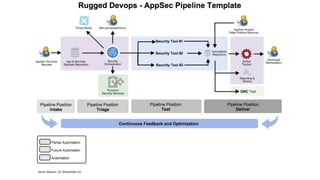
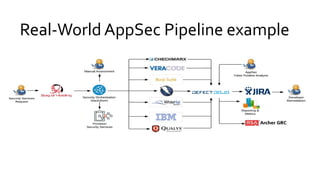
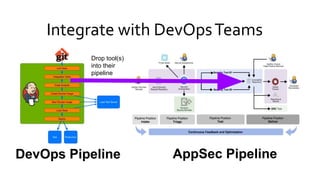
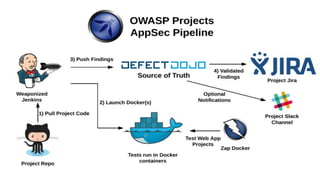
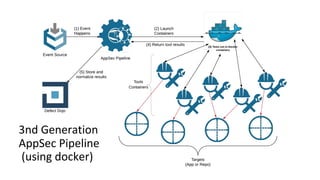
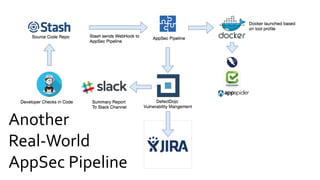
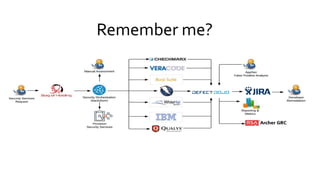
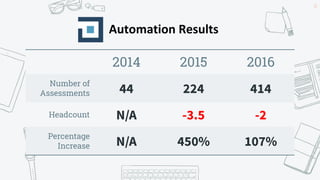
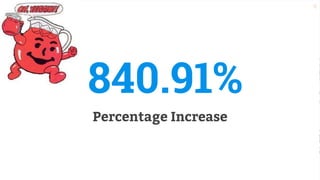
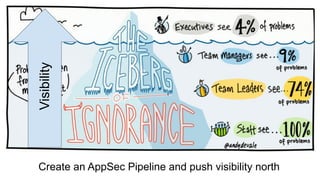
The document discusses the evolution of application security (AppSec) towards automation and integration within DevOps practices, emphasizing the need to improve efficiency and visibility in security processes. It highlights the importance of leveraging tools like OWASP Defectdojo for vulnerability management, automation, and collaboration between AppSec and development teams. The presentation outlines strategies for developing different generations of AppSec pipelines to enhance security coverage, streamline workflows, and support continuous learning and experimentation.