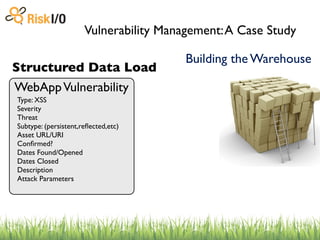
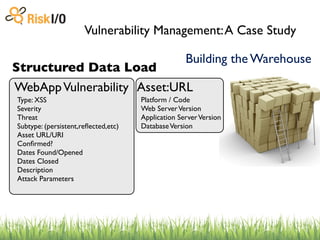
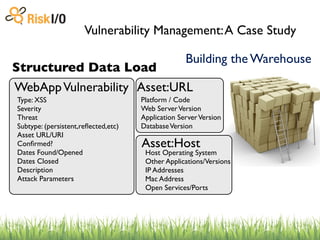
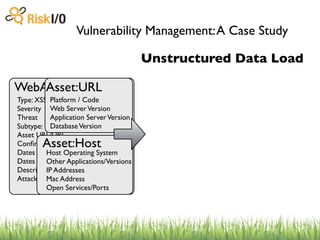
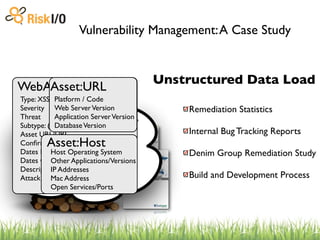
The document discusses the challenges of managing vulnerabilities across many websites without structured data and processes. It describes building a centralized "warehouse" to store vulnerability data in a structured format, including details about the vulnerabilities as well as metadata about the assets and organizations. This allows vulnerabilities to be tracked over time and correlated with internal and external threat data to help prioritize risks.