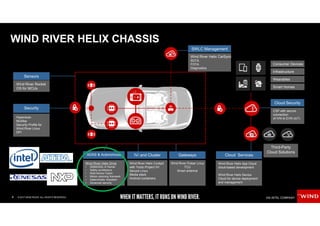
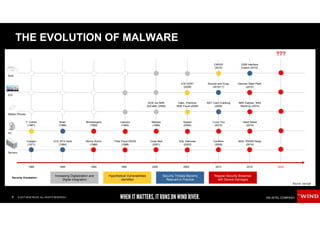
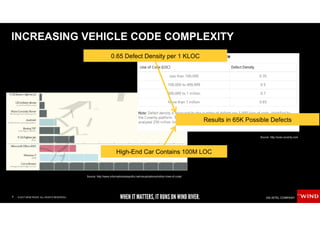
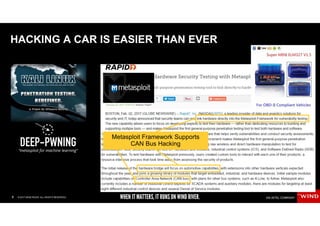
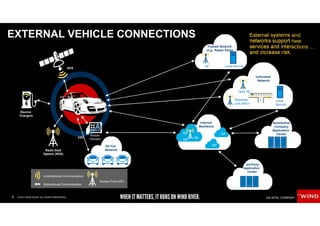
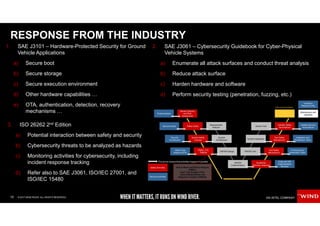
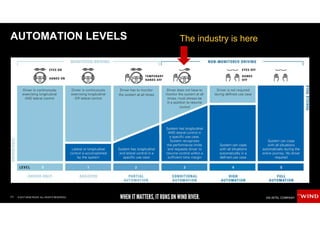
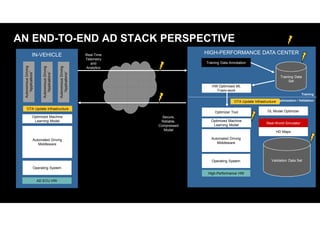
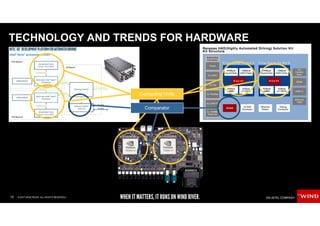
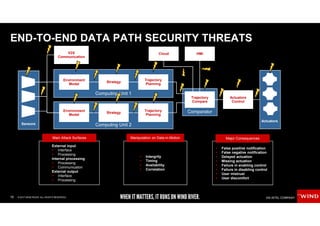
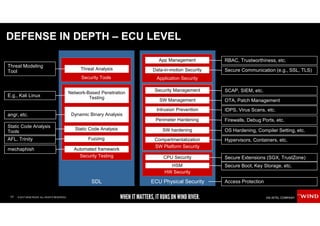
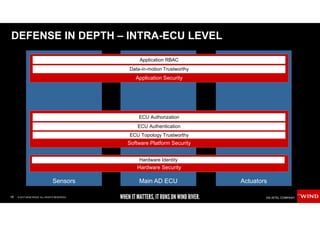
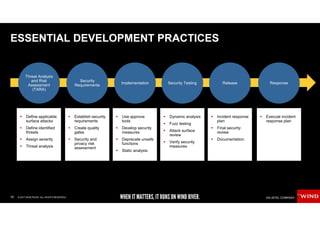
The document discusses the evolving security challenges associated with autonomous driving technology, highlighting the complexity of vehicle software and the increasing risk of cyber threats. It outlines industry responses including new security standards and practices to ensure safety and security in connected and automated vehicles. Key themes include the necessity for an end-to-end security architecture, defense in depth, and the integration of safety and security measures.