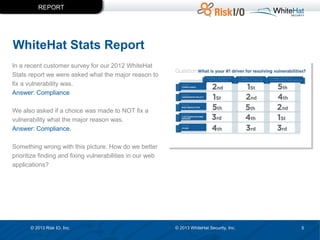
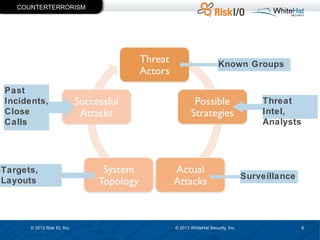
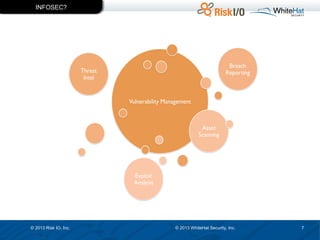
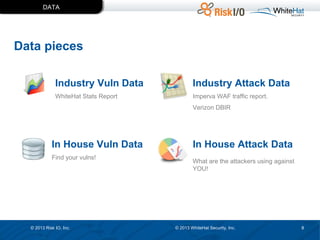
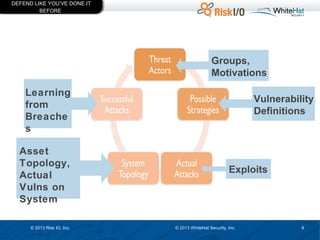
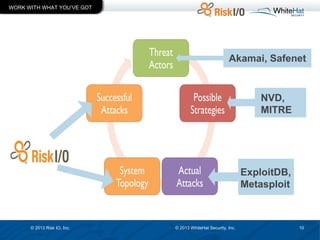
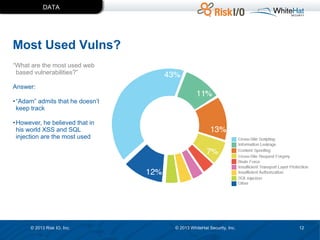
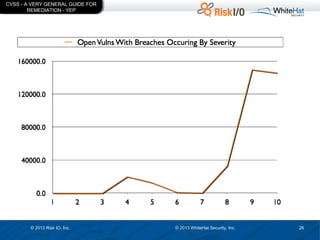
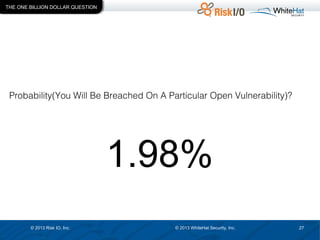
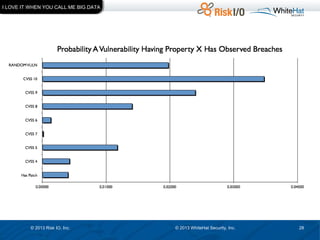
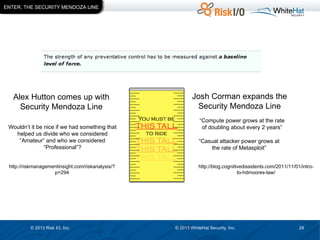
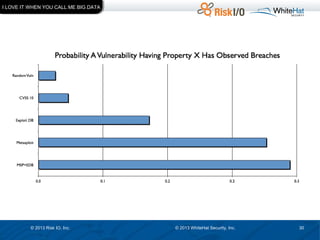
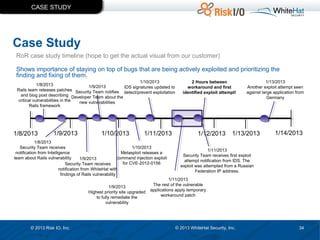
The document discusses the importance of vulnerability management in web security, highlighting the roles of Ed Bellis and Matt Johansen in the industry. It emphasizes the need for prioritizing vulnerability fixes based on compliance and effectiveness, and critiques the limitations of the OWASP Top 10 list. Additionally, it stresses the significance of real-time threat intelligence and the need for organizations to effectively manage and remediate vulnerabilities to prevent attacks.