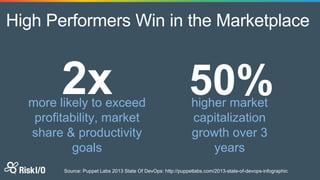
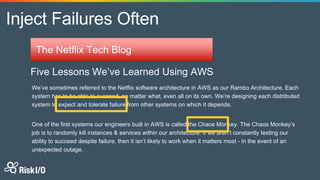
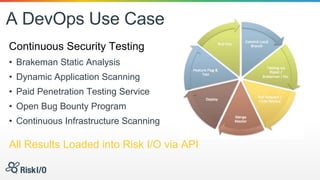
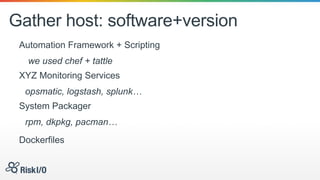
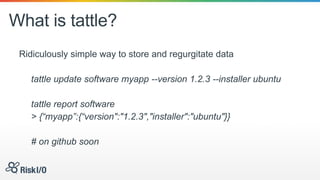
Jason Rohwedder and Ed Bellis presented on security automation at Risk I/O. They discussed how automating security processes through DevOps principles allows for more frequent code deployments and faster response times. Risk I/O utilizes Chef for infrastructure automation and runs continuous security testing and monitoring through APIs to identify vulnerabilities. Their non-intrusive host vulnerability detection approach gathers software/version data and checks it against vulnerability definitions without requiring scanning.

















![Mix It TogetherParse Some XML
$ cat nvdcve-2.0-2014.xml | ruby -e 'require "ox"; p
Ox.parse(ARGF.read).nvd.locate("entry").select {|x|
x.locate("*/vuln:product/*").member? "cpe:/a:oracle:mysql:5.5.26"
}.map(&:id)’
["CVE-2014-0384", "CVE-2014-0386", "CVE-AWW-YEAH",...]
What was that?
• We have mysql 5.5.26 installed
• Searching for it’s most specific CPE locator
• We found that there are a bunch of Vulnerabilities for it from
2014](https://image.slidesharecdn.com/securityascode-cloudsecurityworld-150527032920-lva1-app6891/85/Security-as-Code-31-320.jpg)