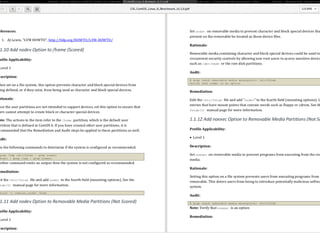
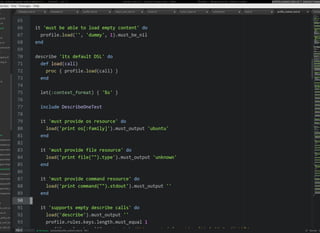
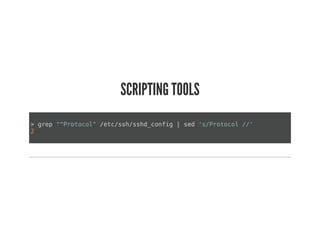
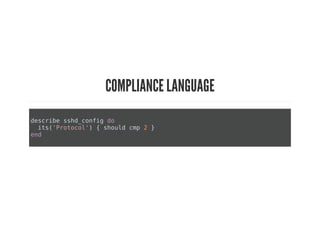
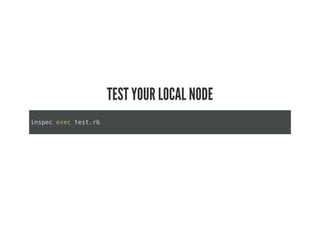
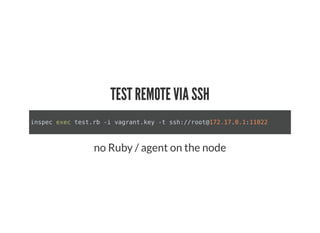
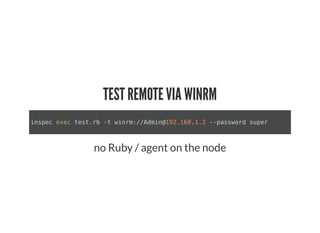
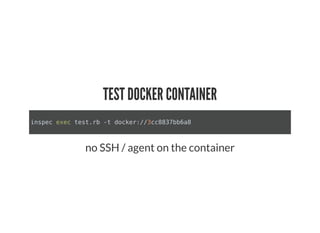
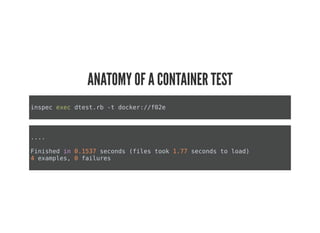
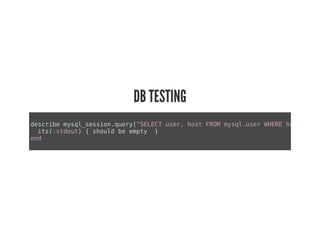
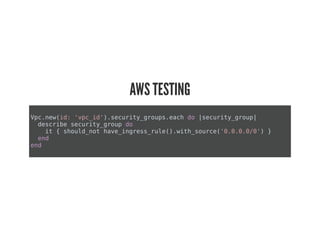
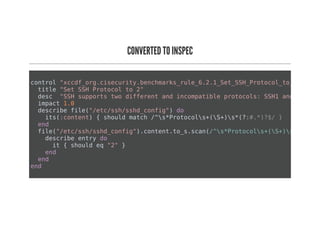
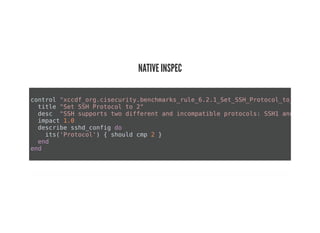
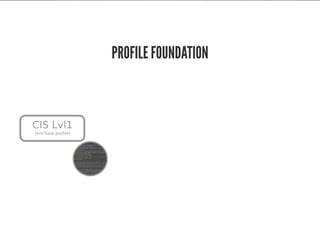
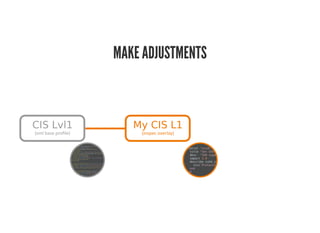
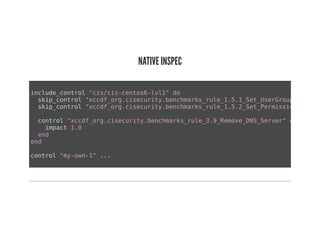
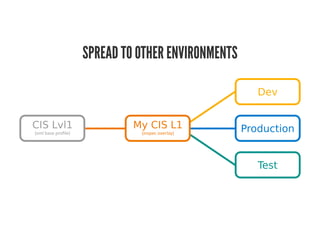
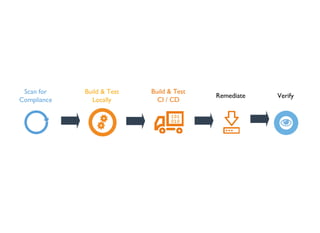
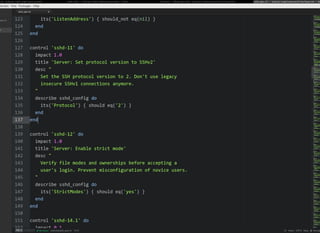
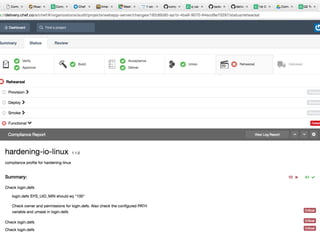
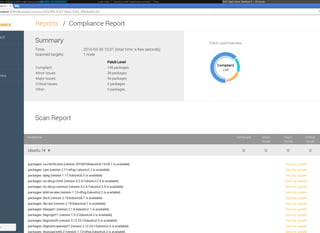
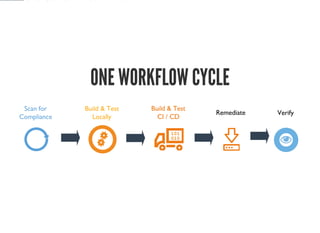
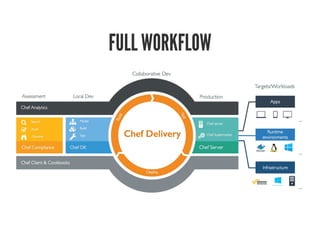
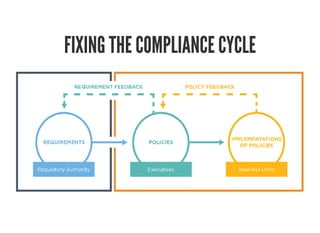
This document discusses Chef Compliance and how it helps with security and DevOps for organizations that move quickly. It introduces InSpec, an open source framework that allows defining infrastructure compliance and security checks as code. With InSpec, compliance checks can be automated and run continuously alongside infrastructure code. Traditional compliance is time-consuming and separate from development workflows, but defining compliance specifications in InSpec code allows integrating compliance into DevOps pipelines for continuous verification.