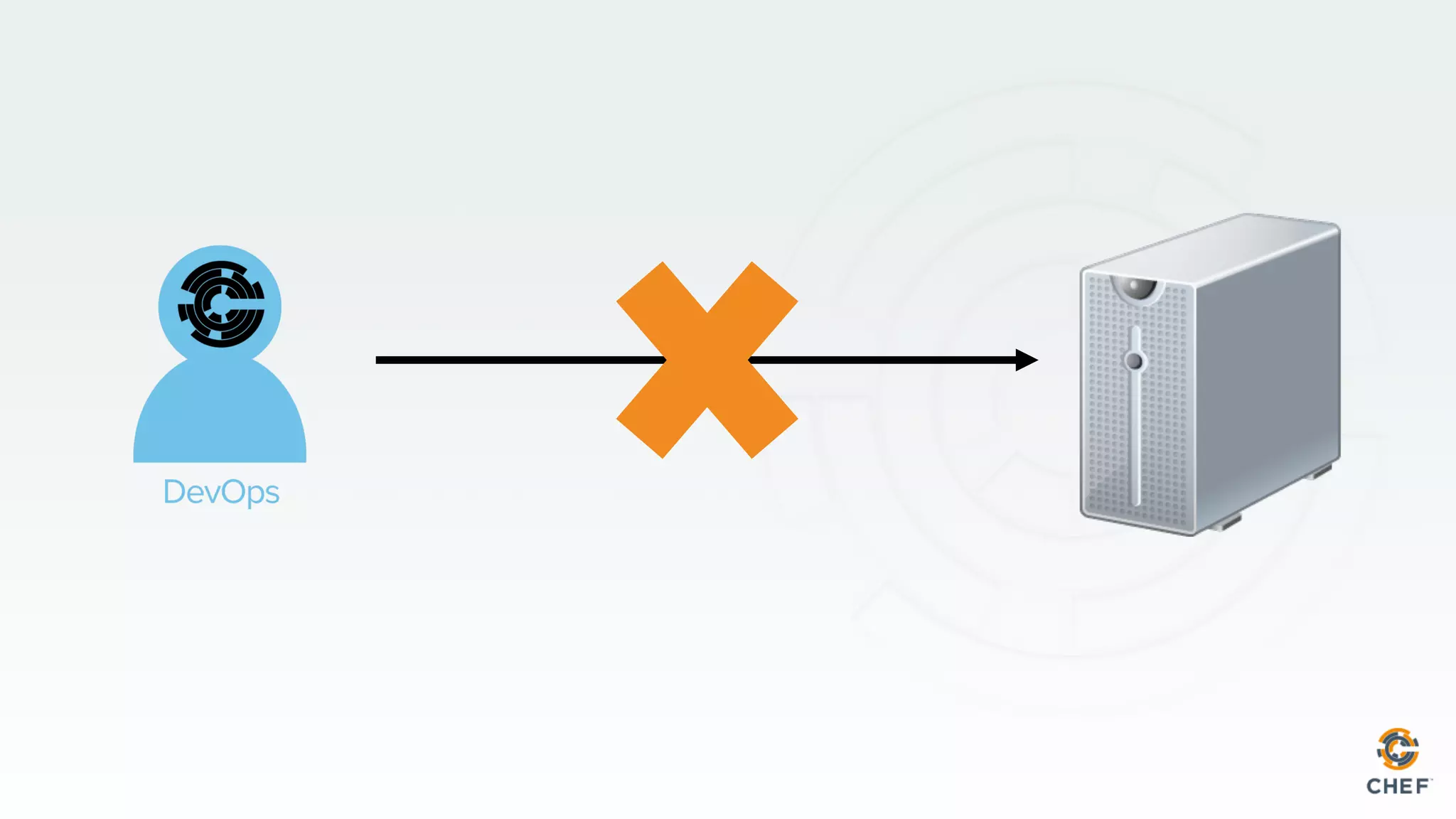
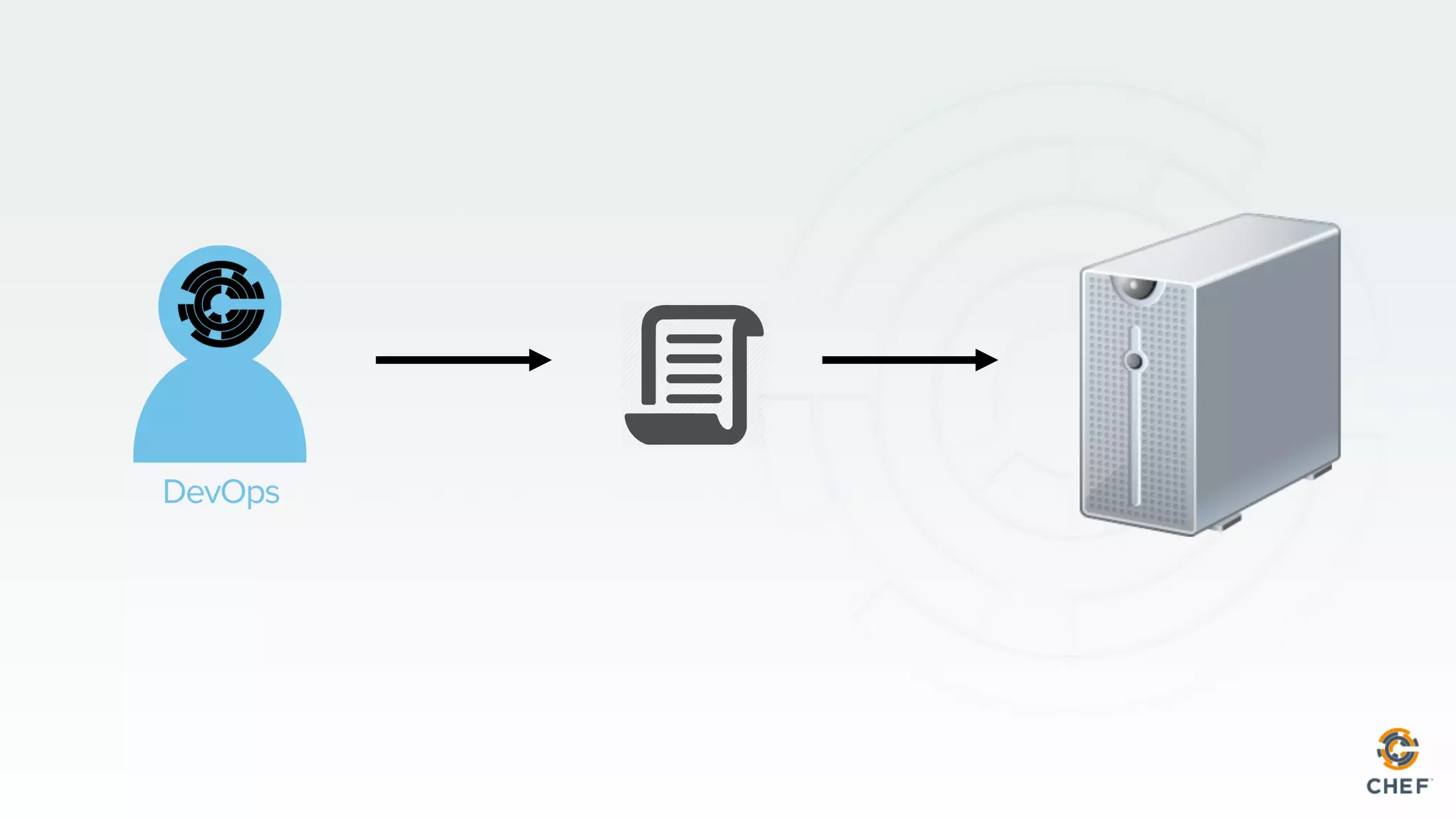
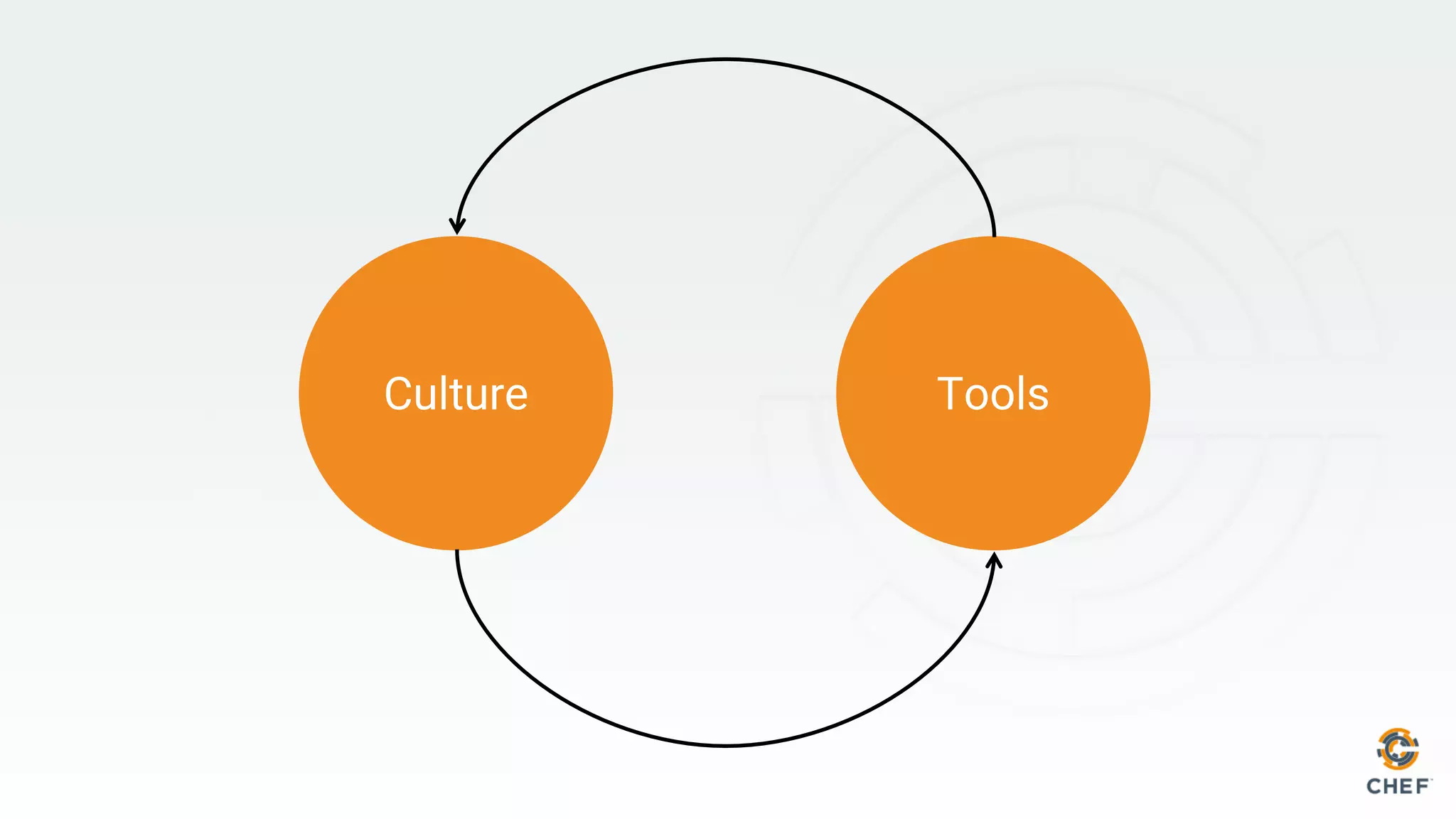
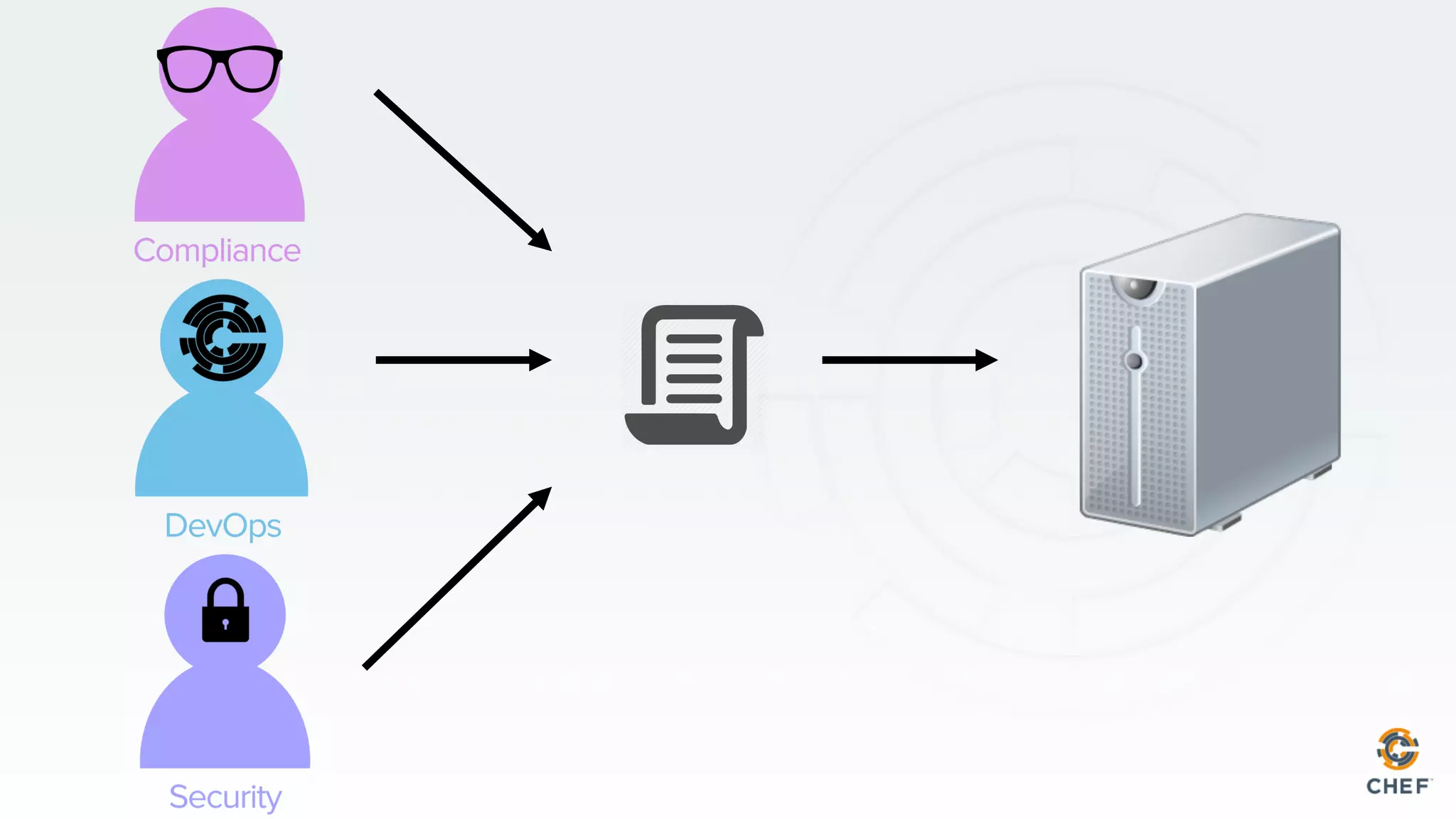
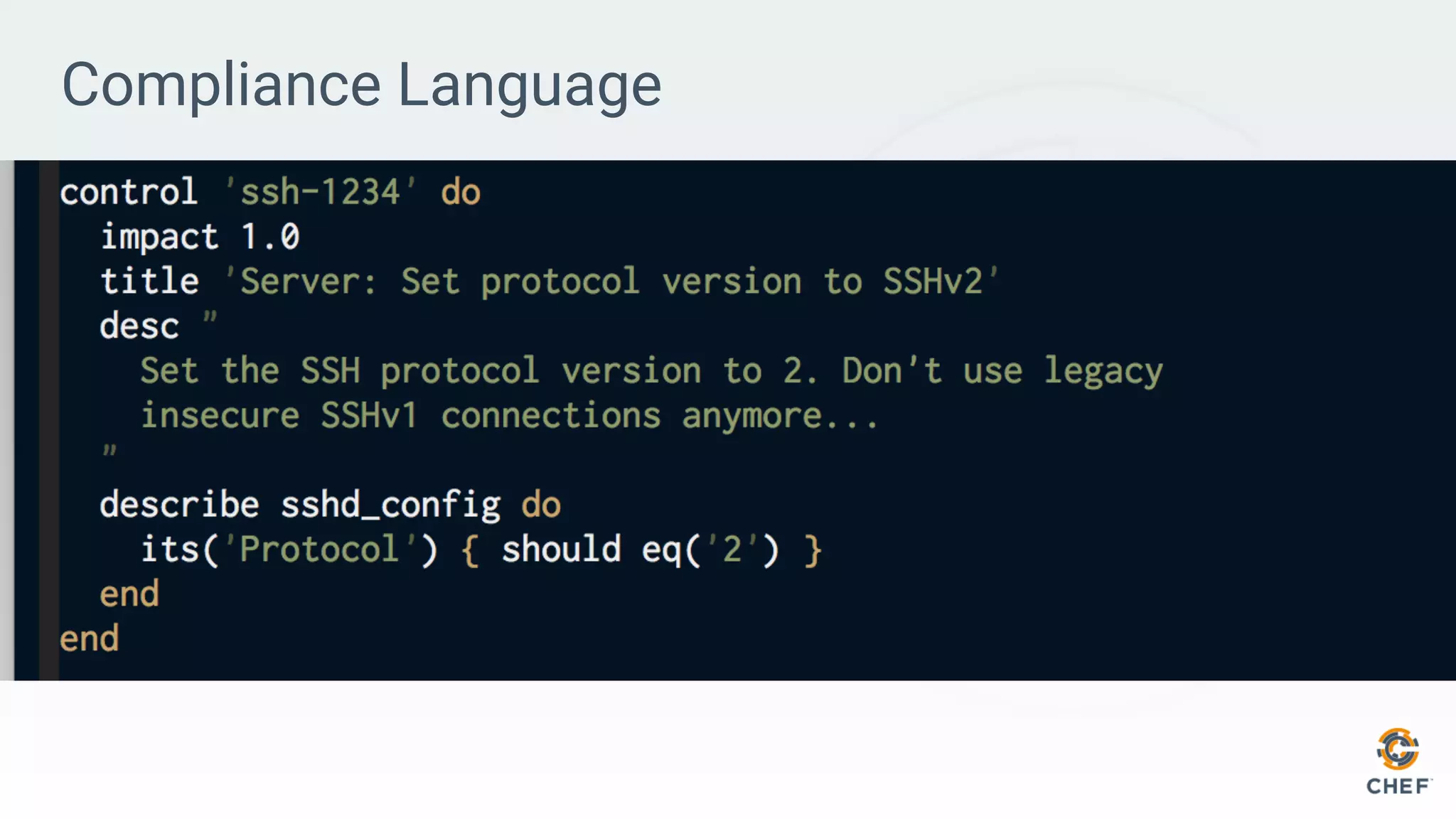
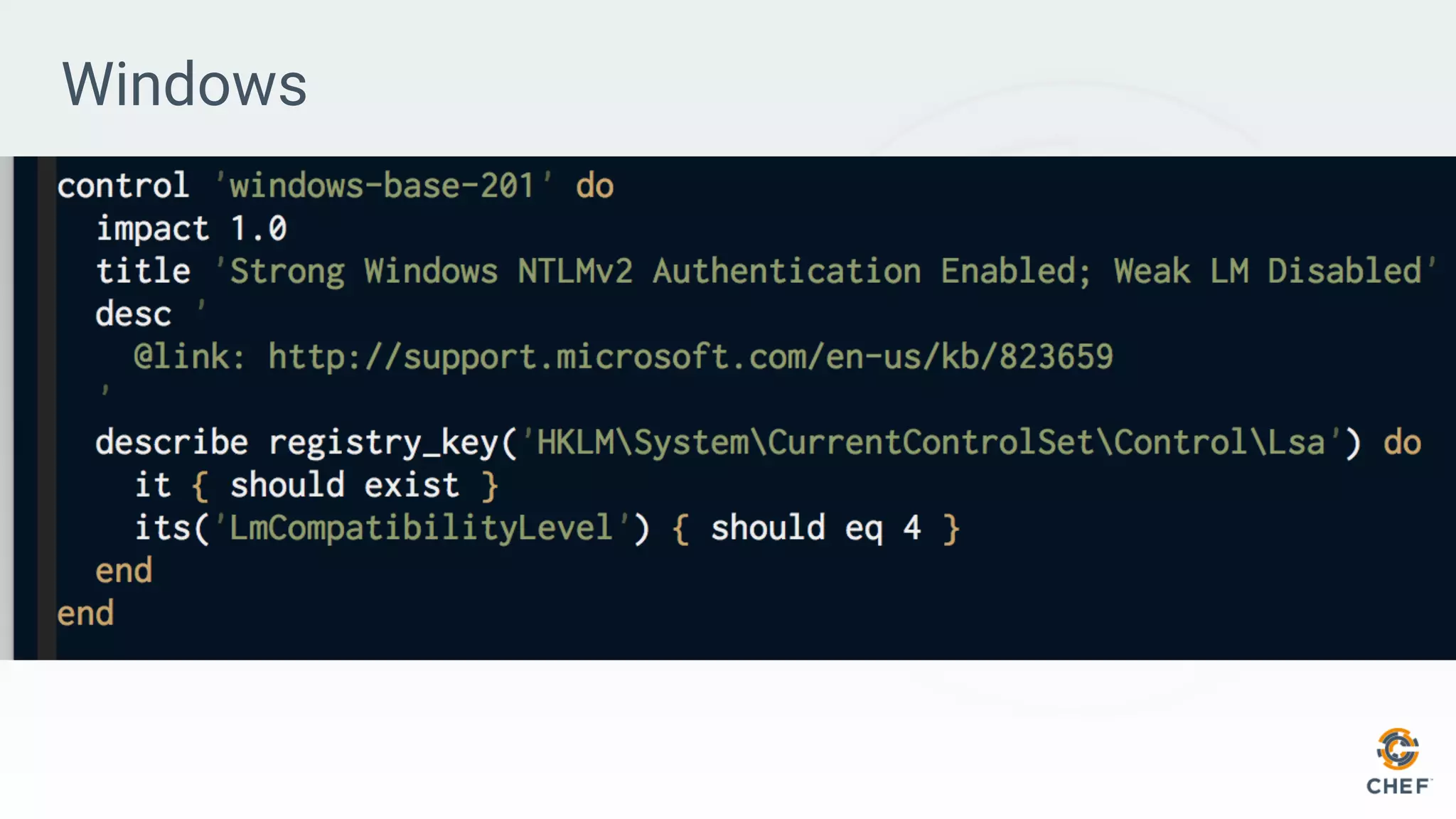
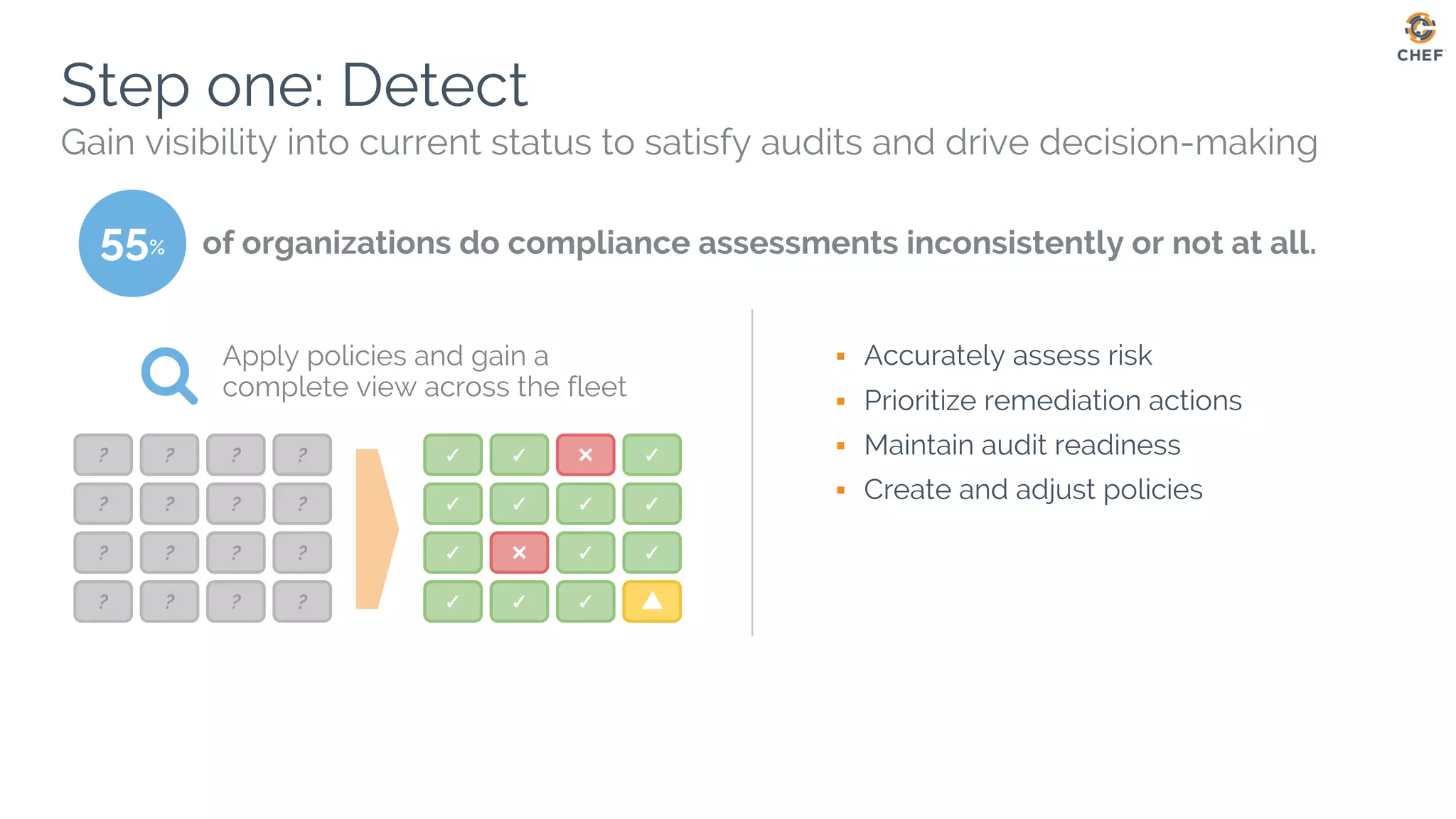
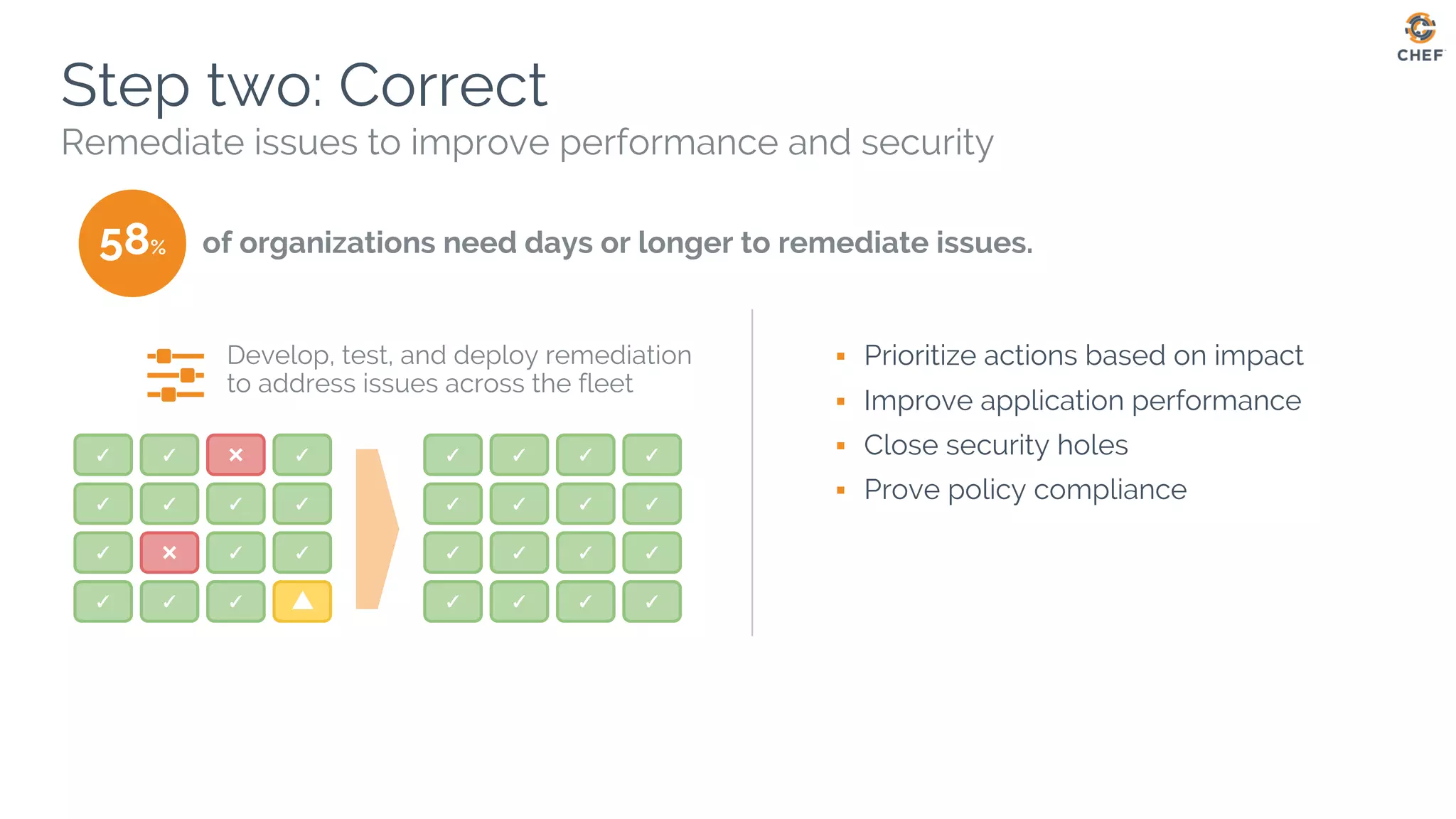
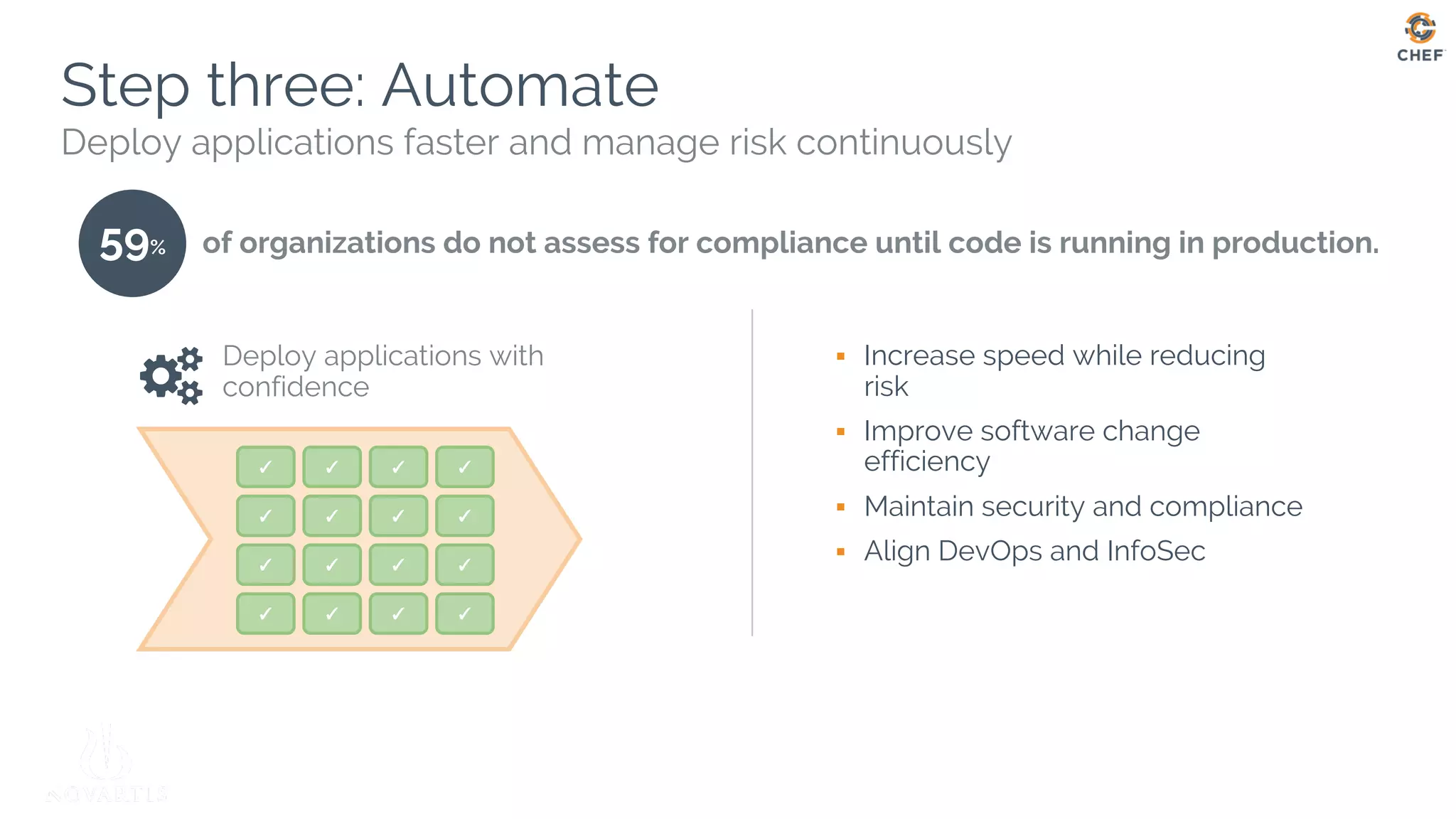
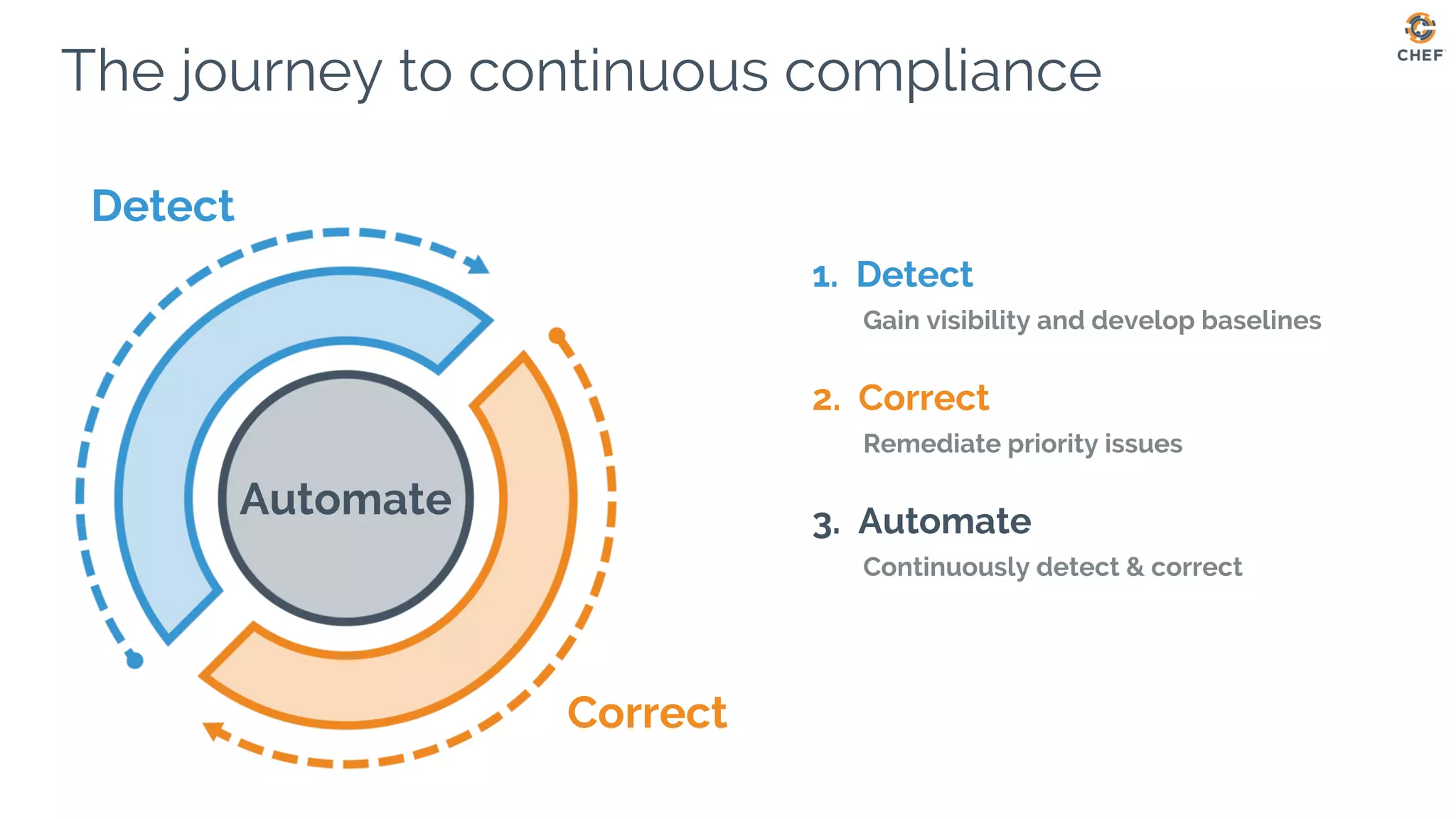
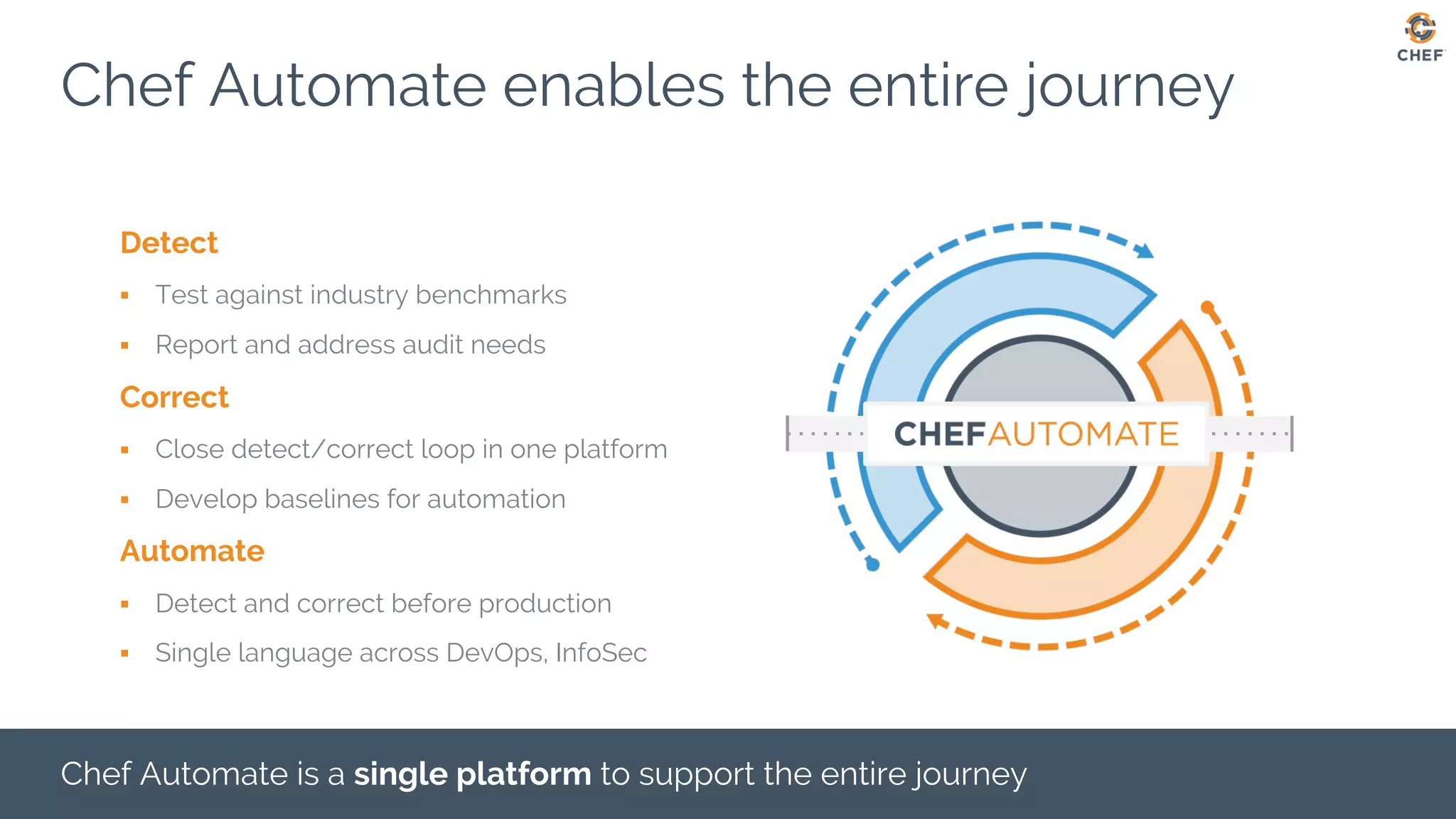
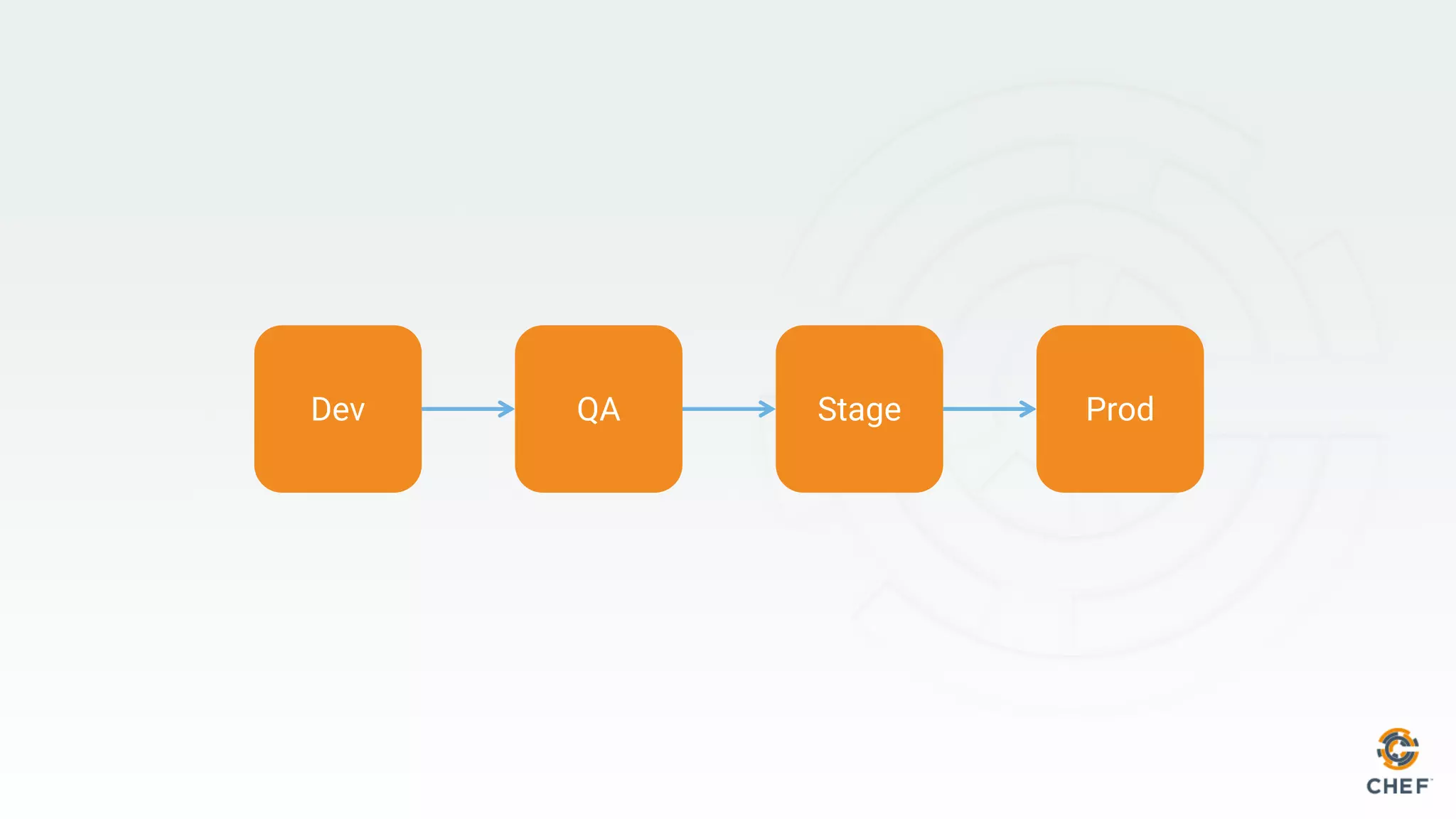
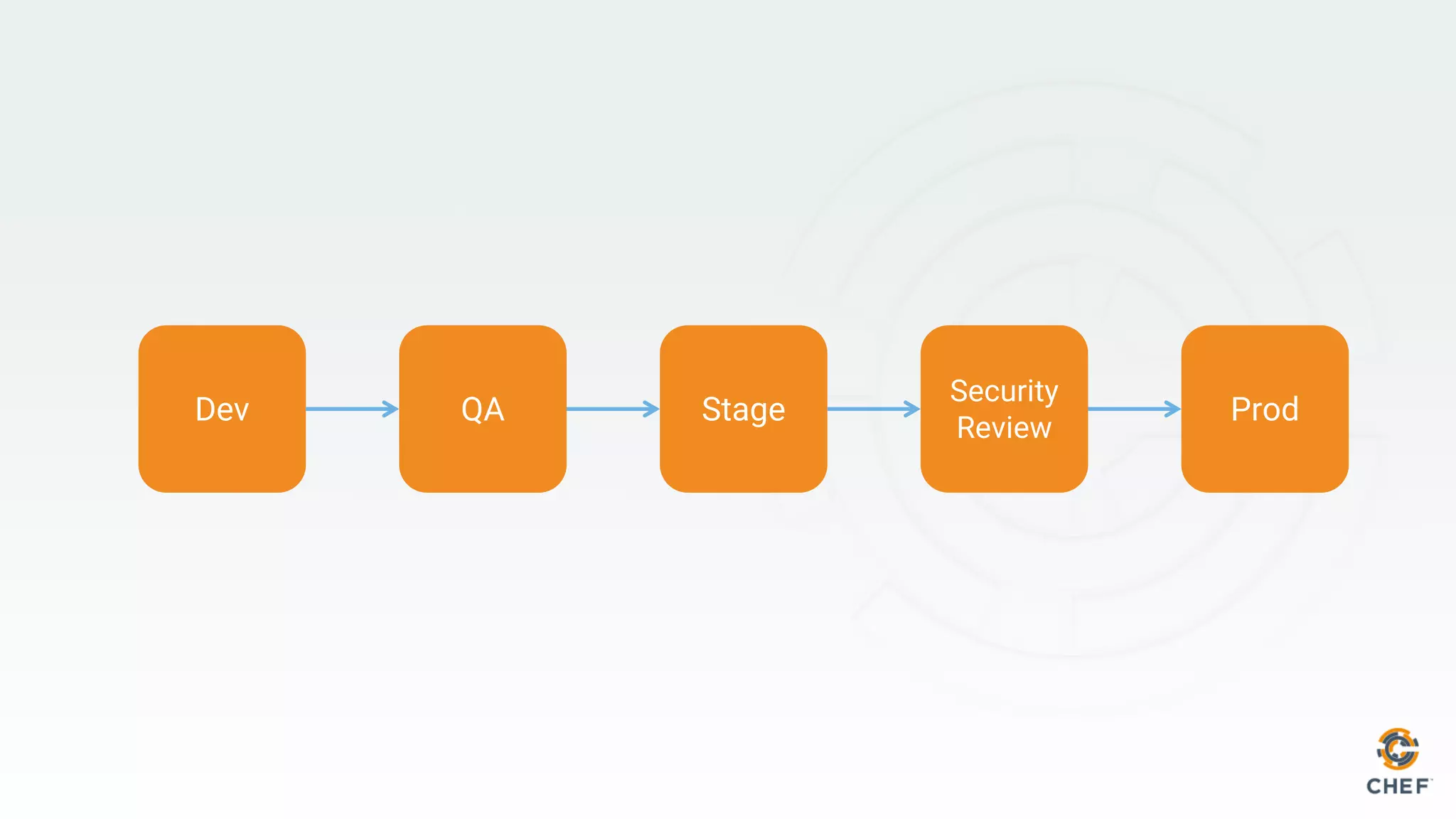
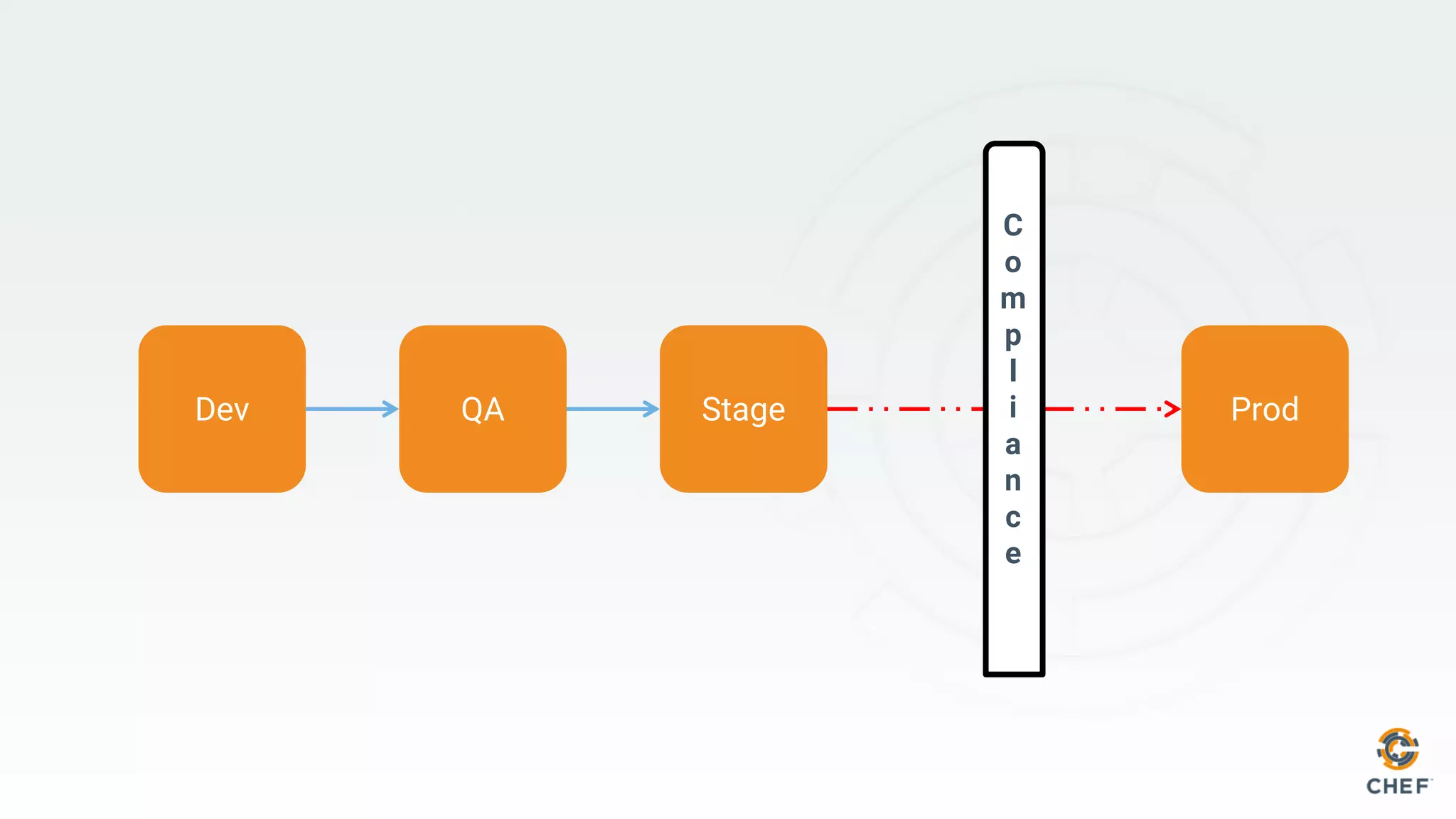
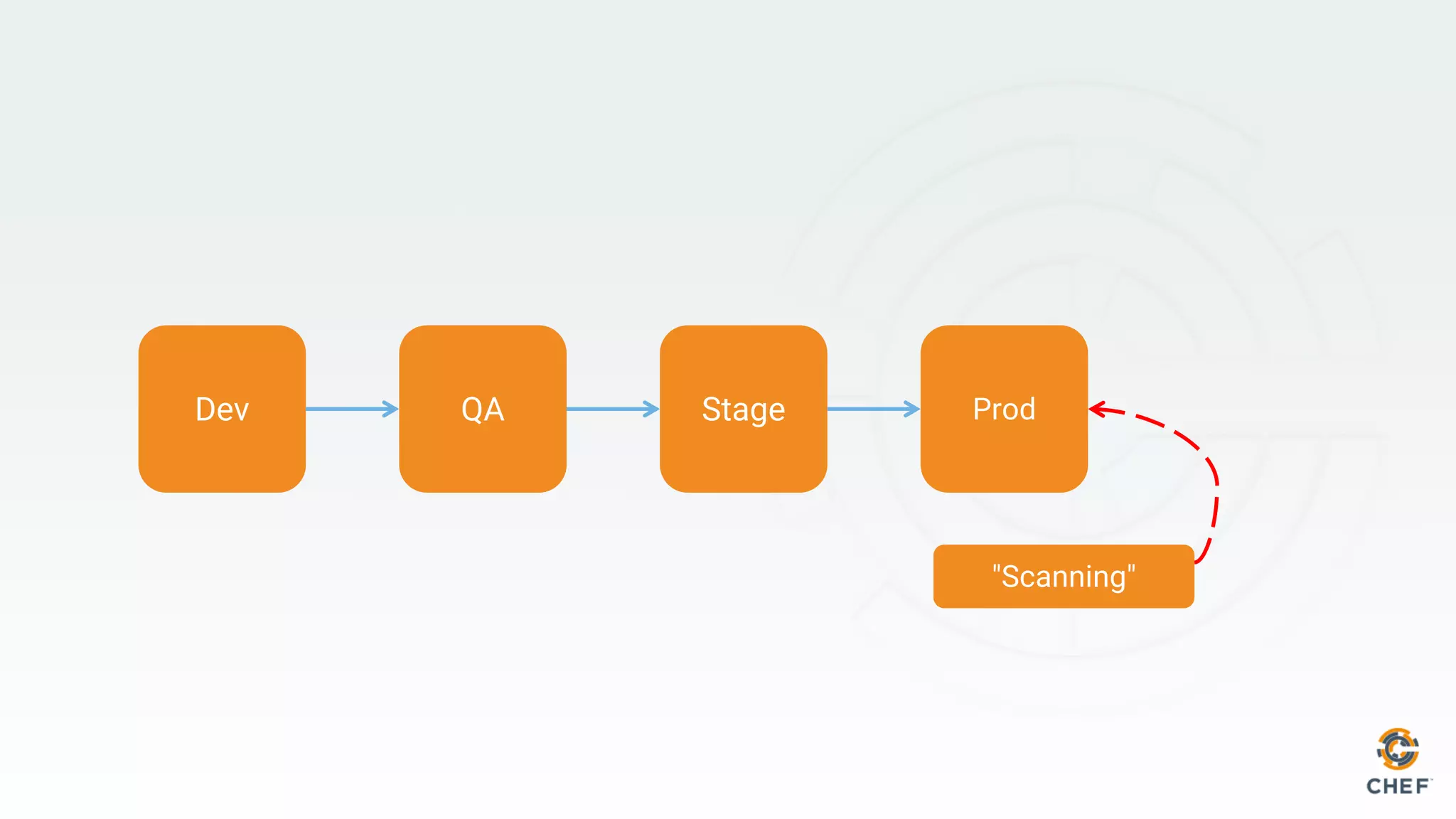
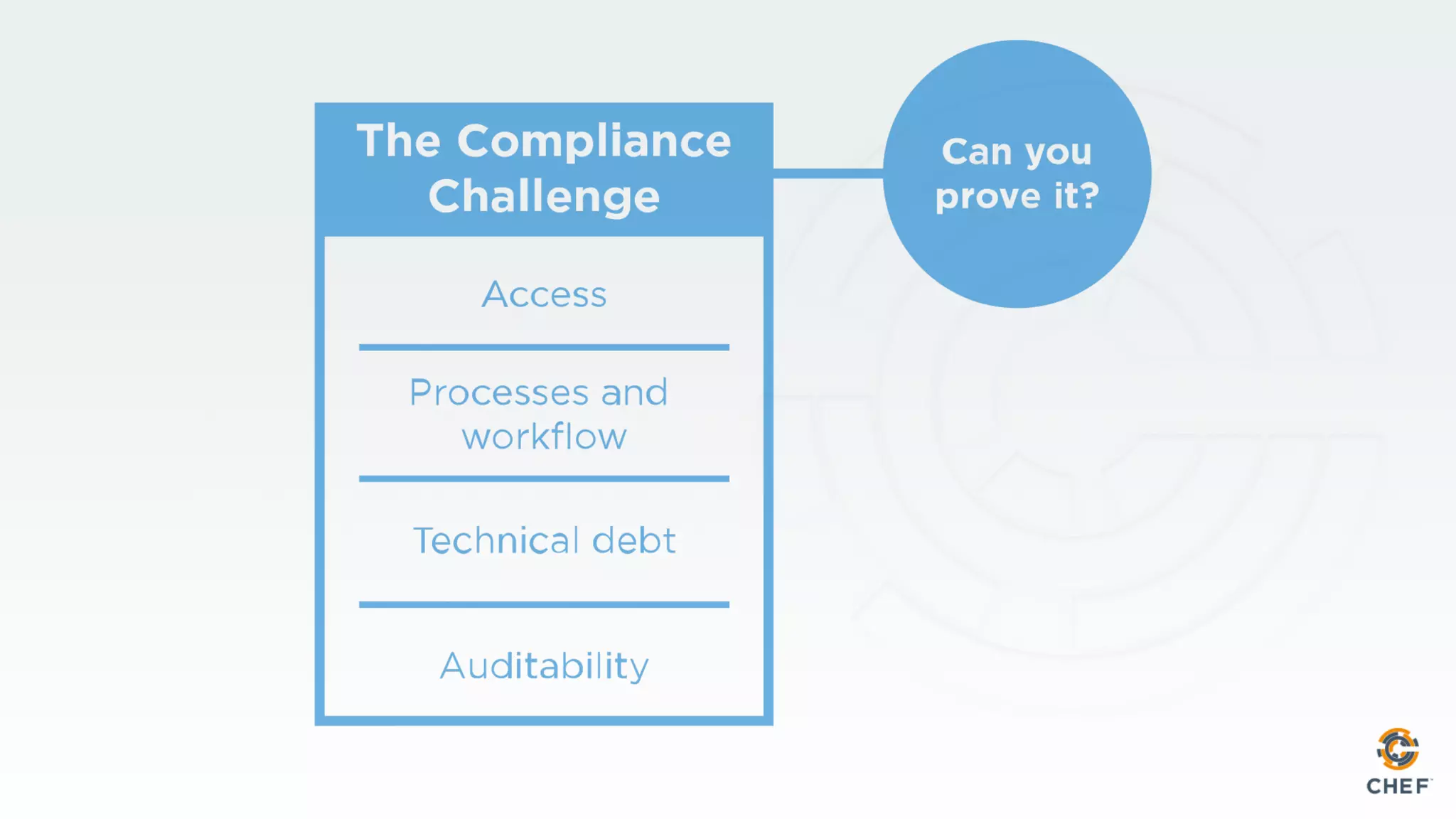
This document discusses using Chef Automate to enable continuous compliance through a three step process of detecting issues, correcting problems, and automating compliance. It notes that many organizations currently assess compliance inconsistently or after deploying code to production. Chef Automate allows detecting and correcting issues across infrastructure in a single platform using the same language for both DevOps and InfoSec teams. This enables deploying applications with confidence while maintaining security and compliance.












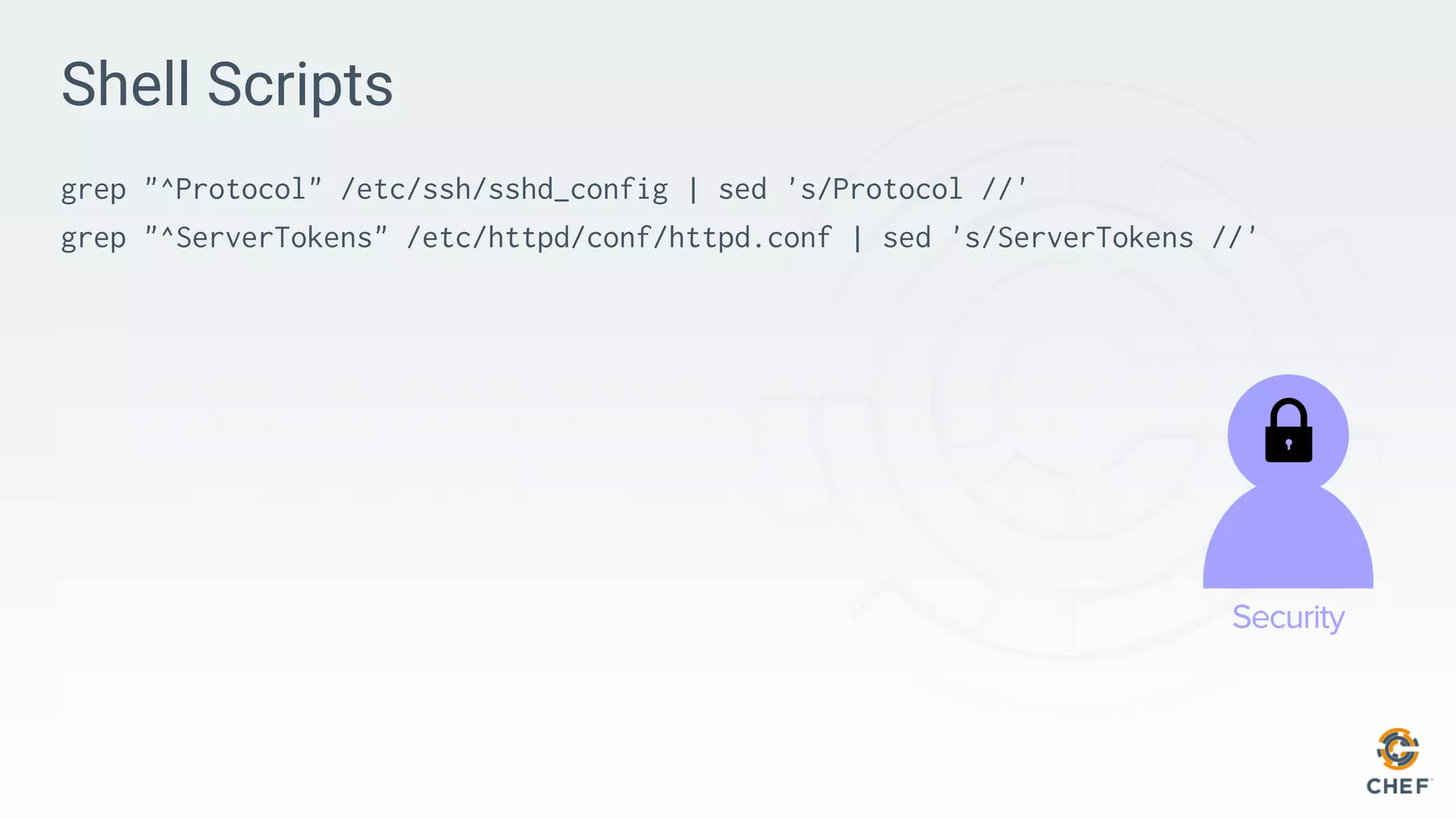
![Infrastructure Code
package 'httpd' do
action :install
end
service 'httpd' do
action [ :start, :enable ]
end](https://image.slidesharecdn.com/20171026-dodsingapore-inspec-171027034554/75/DevOpsDays-Singapore-Continuous-Auditing-with-Compliance-as-Code-26-2048.jpg)