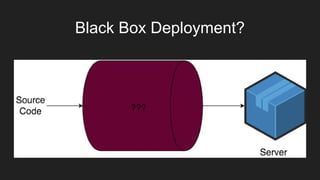
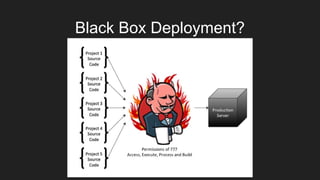
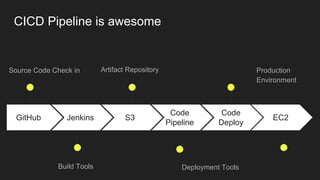
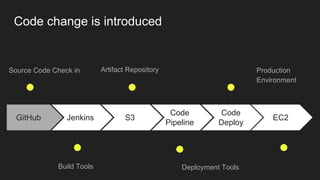
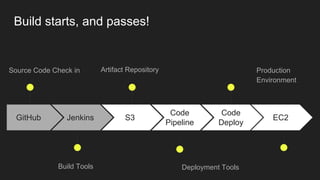
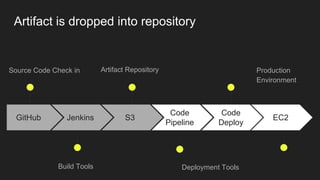
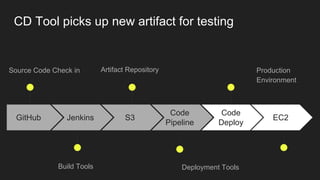
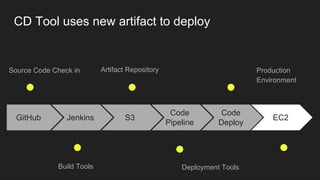
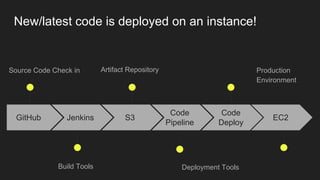
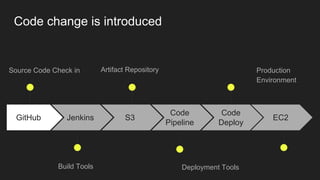
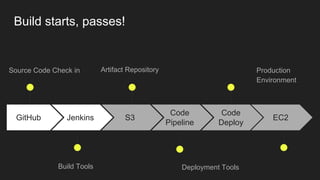
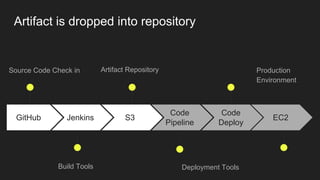
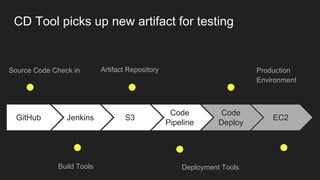
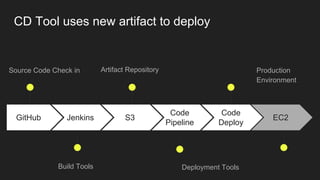
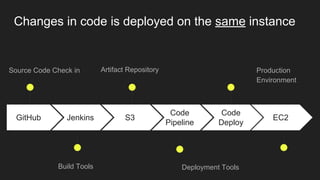
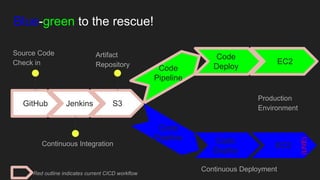
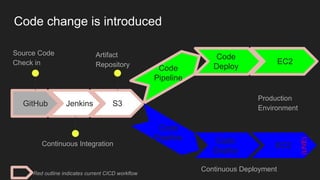
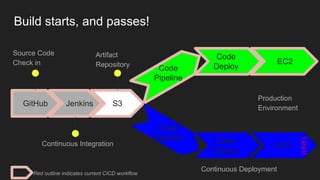
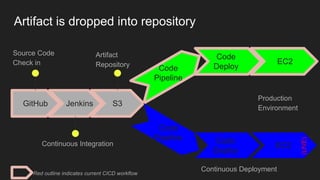
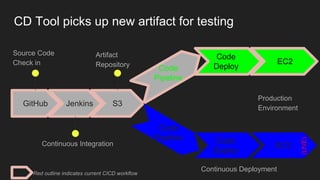
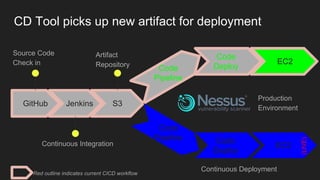
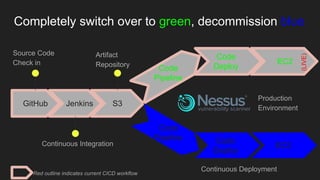
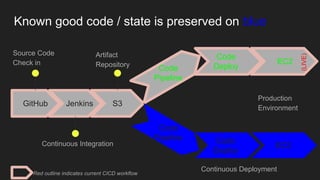
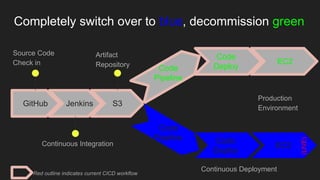
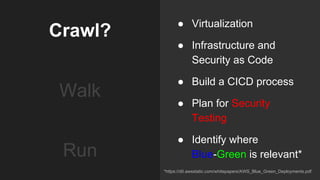
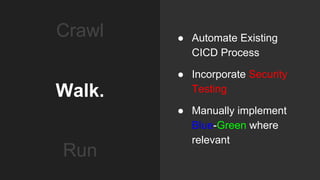
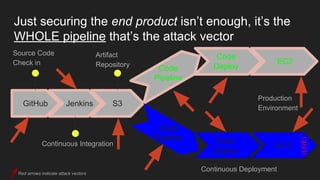
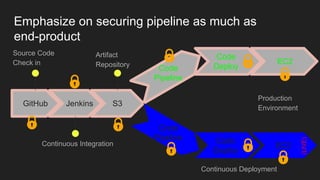
The document describes an automated continuous integration and continuous deployment (CICD) pipeline using a blue-green deployment strategy. It begins by showing a basic CICD pipeline and then introduces blue-green deployment to reduce downtime when deploying new changes. It demonstrates how blue-green deployment works step-by-step and discusses how it helps minimize downtime, preserve the last known good deployment, enable robust infrastructure, and allow for parallel pipelines. The document then provides recommendations for implementing blue-green deployment, including using virtualization, automating the process, and incorporating security testing. It emphasizes securing the entire CICD pipeline, not just the final application.