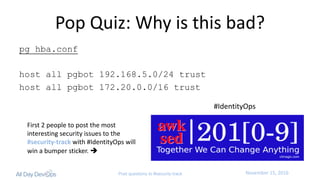
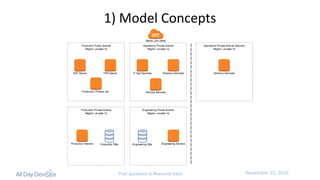
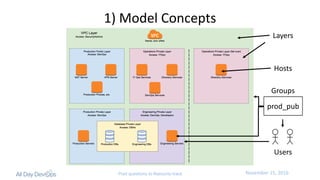
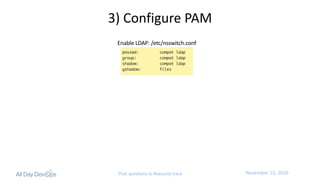
The document discusses the intersection of security, identity, and DevOps, emphasizing the importance of integrating security strategies within DevOps practices. It introduces the concept of 'IdentityOps,' which aims to manage identity and access control through centralized policies and real-time enforcement in IT environments, specifically focusing on use cases like SSH and Docker access. The presentation also highlights the need for better operational efficiency and compliance with business policies while ensuring secure access management.