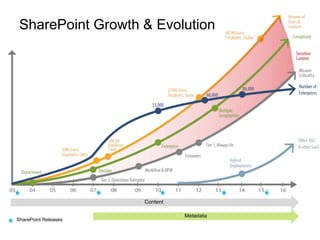
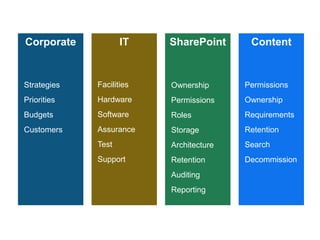
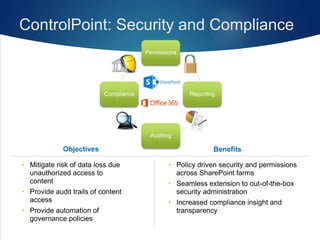
The document outlines five essential security practices for SharePoint, emphasizing the importance of governance and compliance in managing sensitive information. It notes that many organizations lack robust security policies, highlighting the significant risks posed by inadequate permissions and failure to conduct regular audits. The recommendations include defining security policies, implementing permission best practices, and utilizing tools like ControlPoint to enhance oversight and compliance.