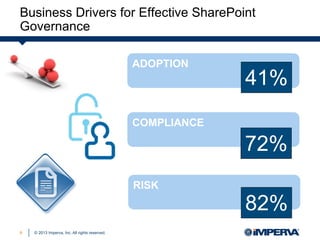
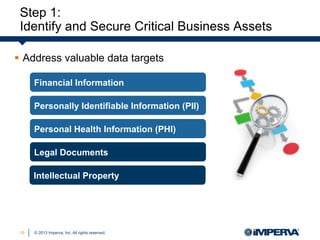
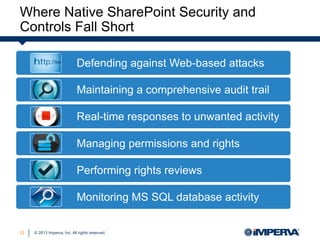
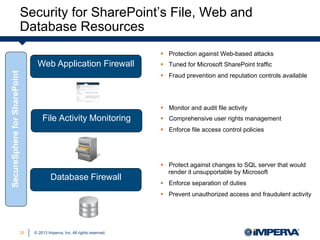
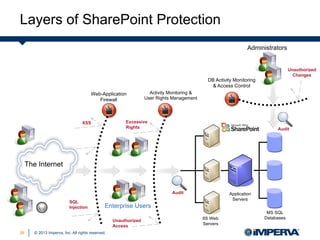
Carrie McDaniel of Imperva presents guidelines for effective SharePoint governance and security. She outlines 4 steps: 1) identify and secure critical business assets, 2) establish a user rights management framework, 3) defend applications from web attacks and code exploits, and 4) monitor user behavior with auditing and analytics. Native SharePoint security controls are insufficient for these tasks, requiring additional defenses like a web application firewall, file activity monitoring, and database firewall.