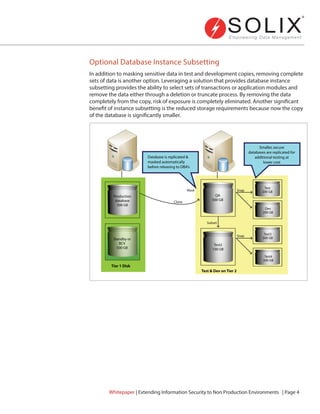
The Solix whitepaper discusses the importance of securing non-production environments to mitigate risks of data theft and tampering, particularly for sensitive information in test and development databases. It emphasizes the need for data masking, encryption, and comprehensive security policies when managing these environments, as traditional protections may not be sufficient once data is replicated outside the production system. The document outlines best practices and tools necessary for implementing effective data security measures in compliance with regulations.