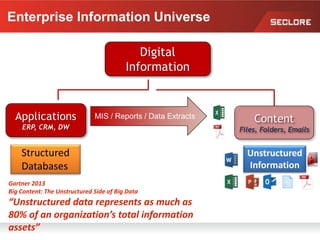
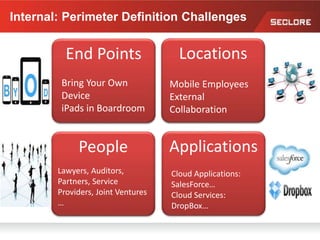
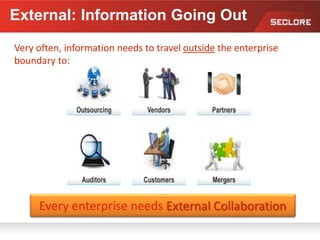
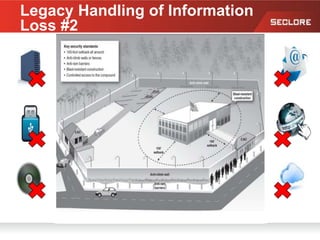
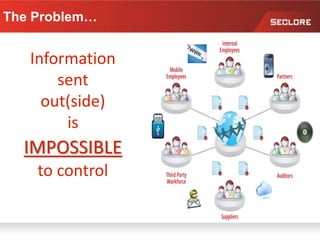
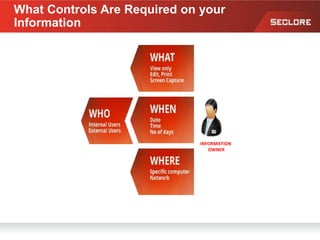
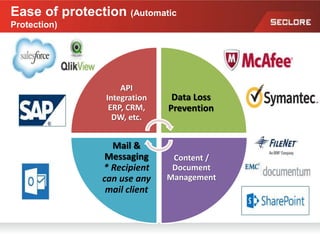
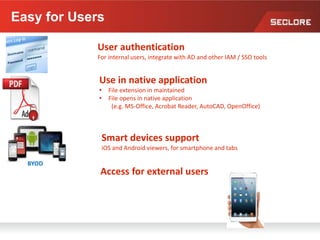
This document discusses information rights management (IRM) concepts and implementation challenges. It notes that unstructured data makes up 80% of organizational information assets and faces challenges from external collaboration and mobile devices. Legacy approaches to information loss control like NDAs are insufficient. IRM aims to allow information owners to control how information is used by applying persistent access policies even as it moves outside the organization. Key requirements for successful IRM implementation include automated policy assignment, usability for users, and support from senior management.