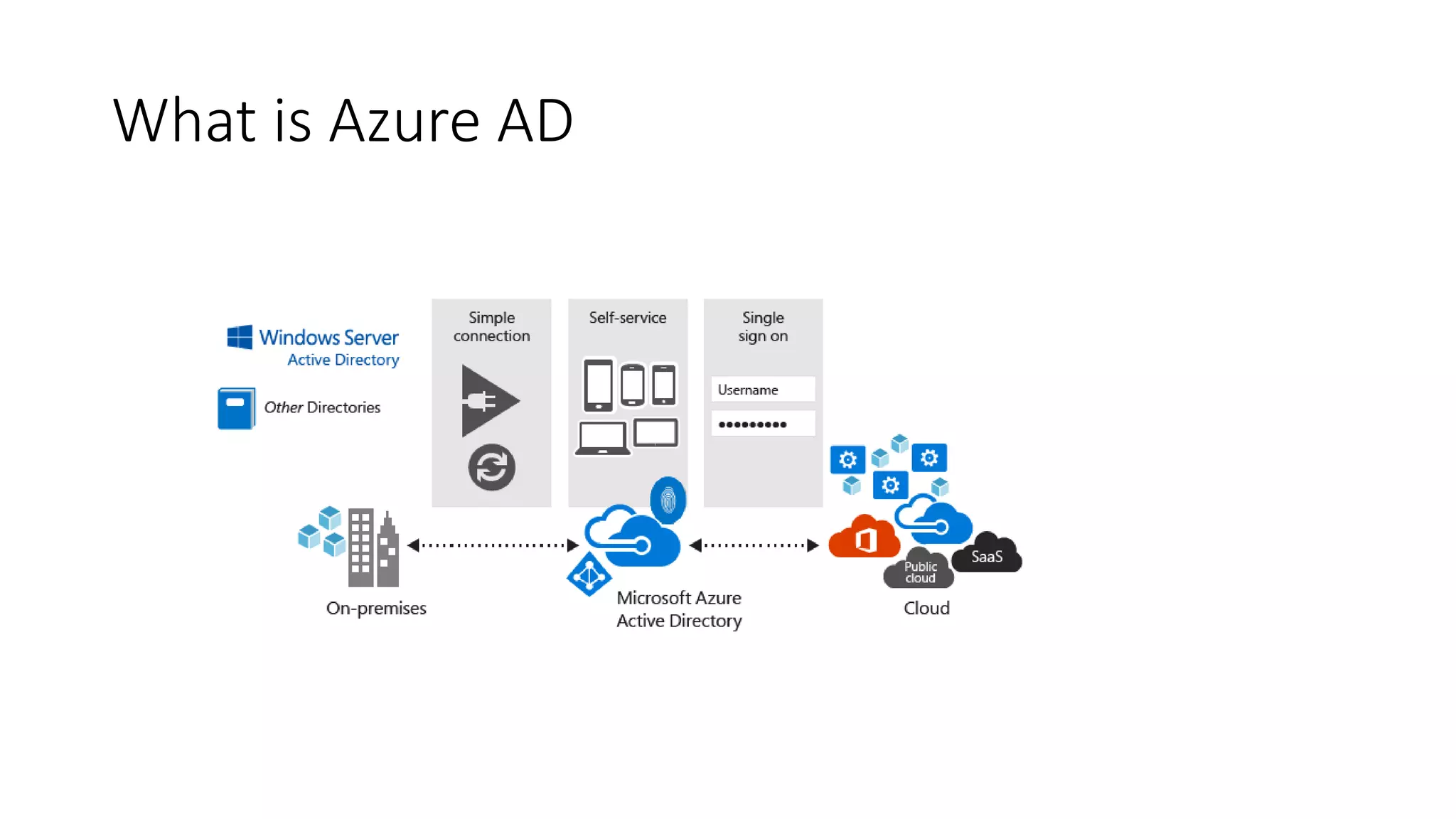
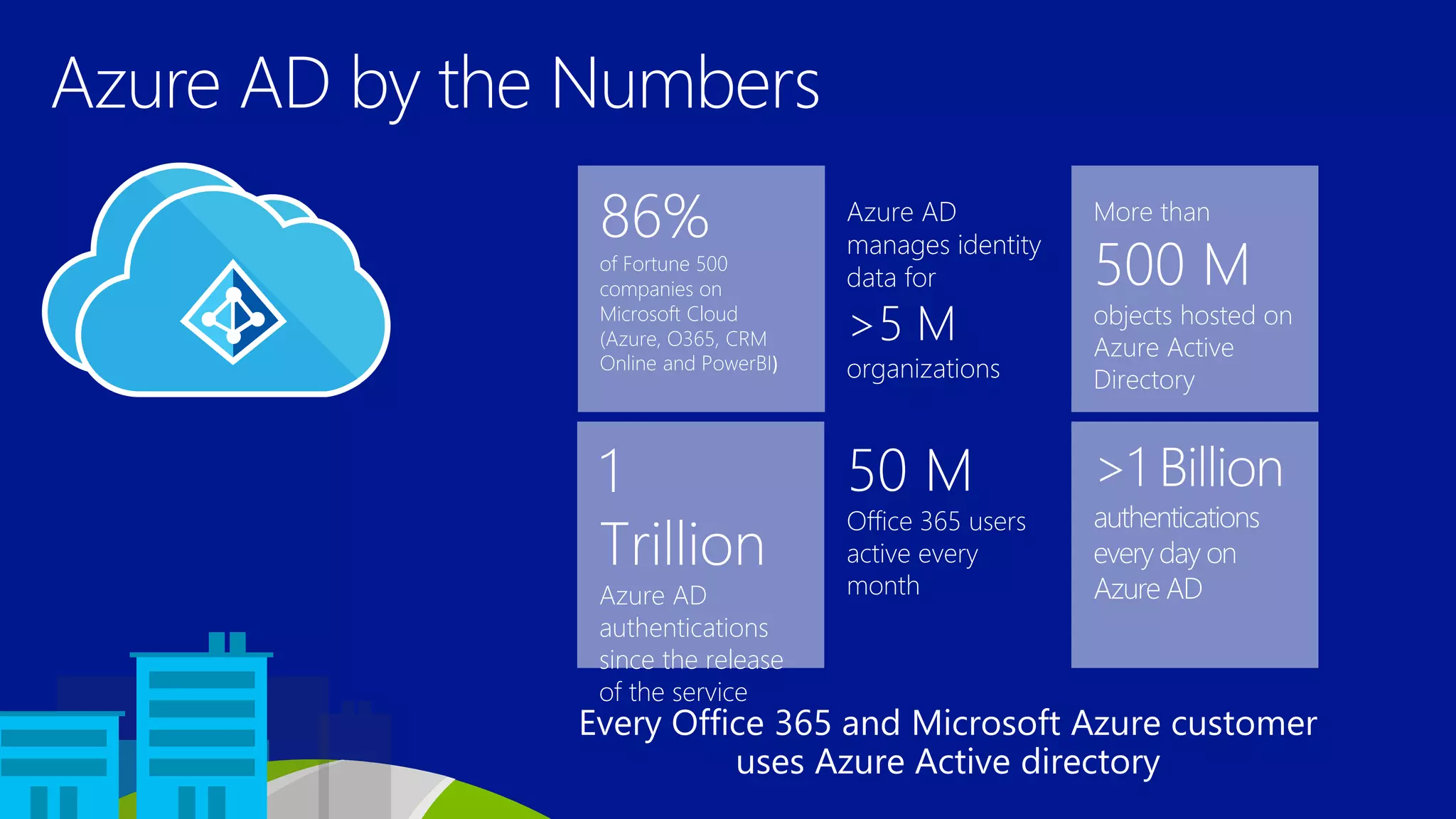
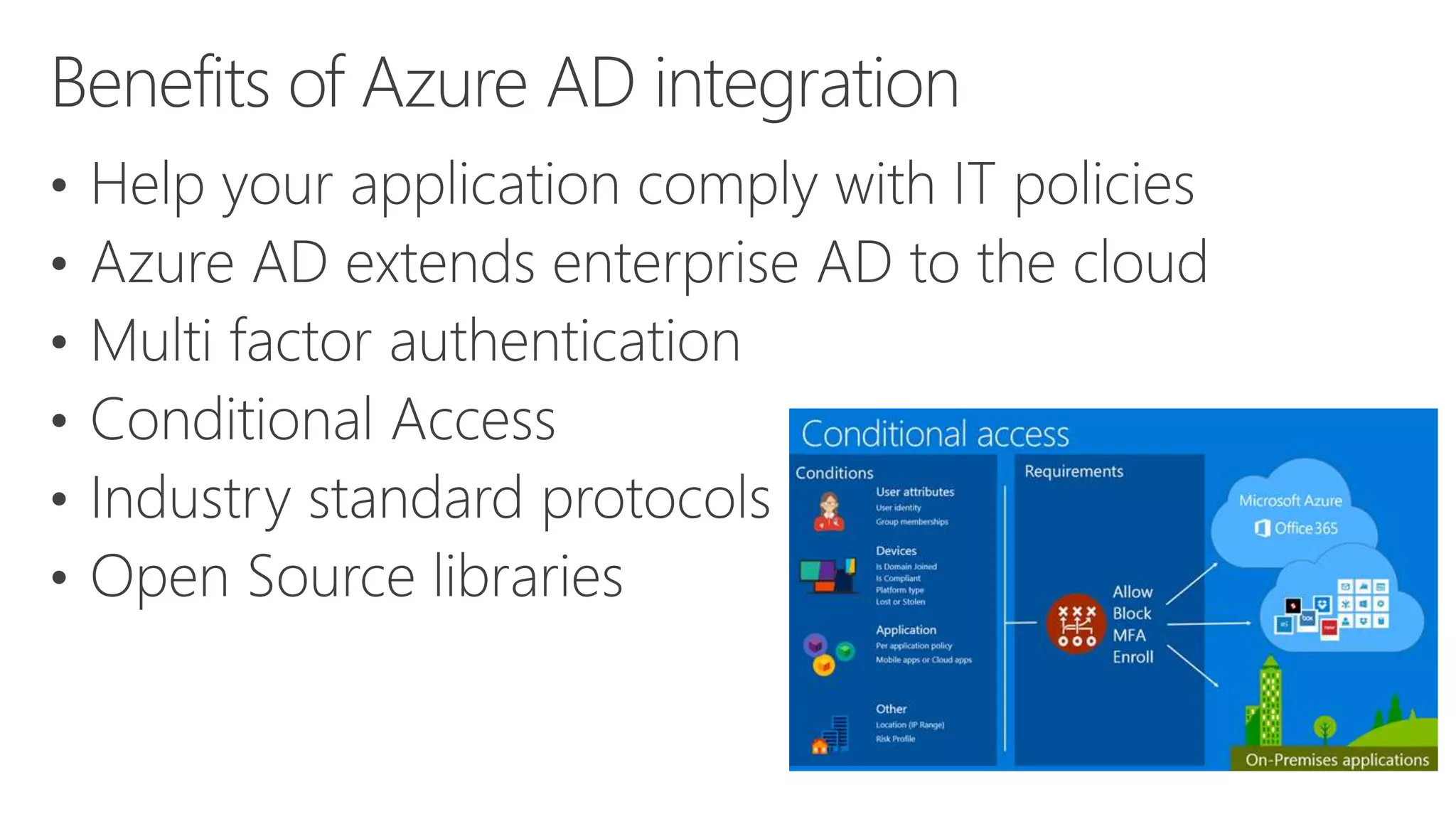
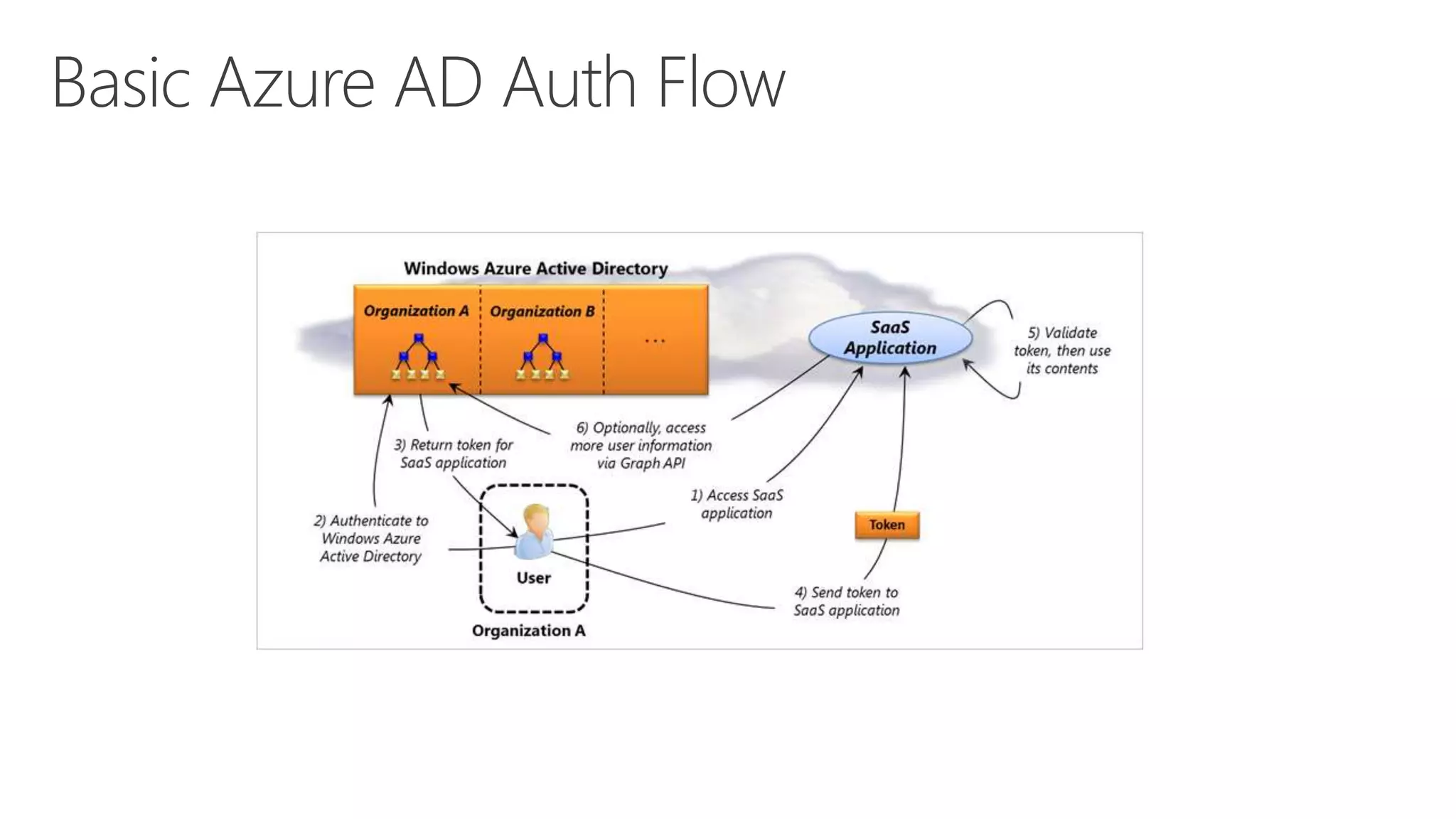
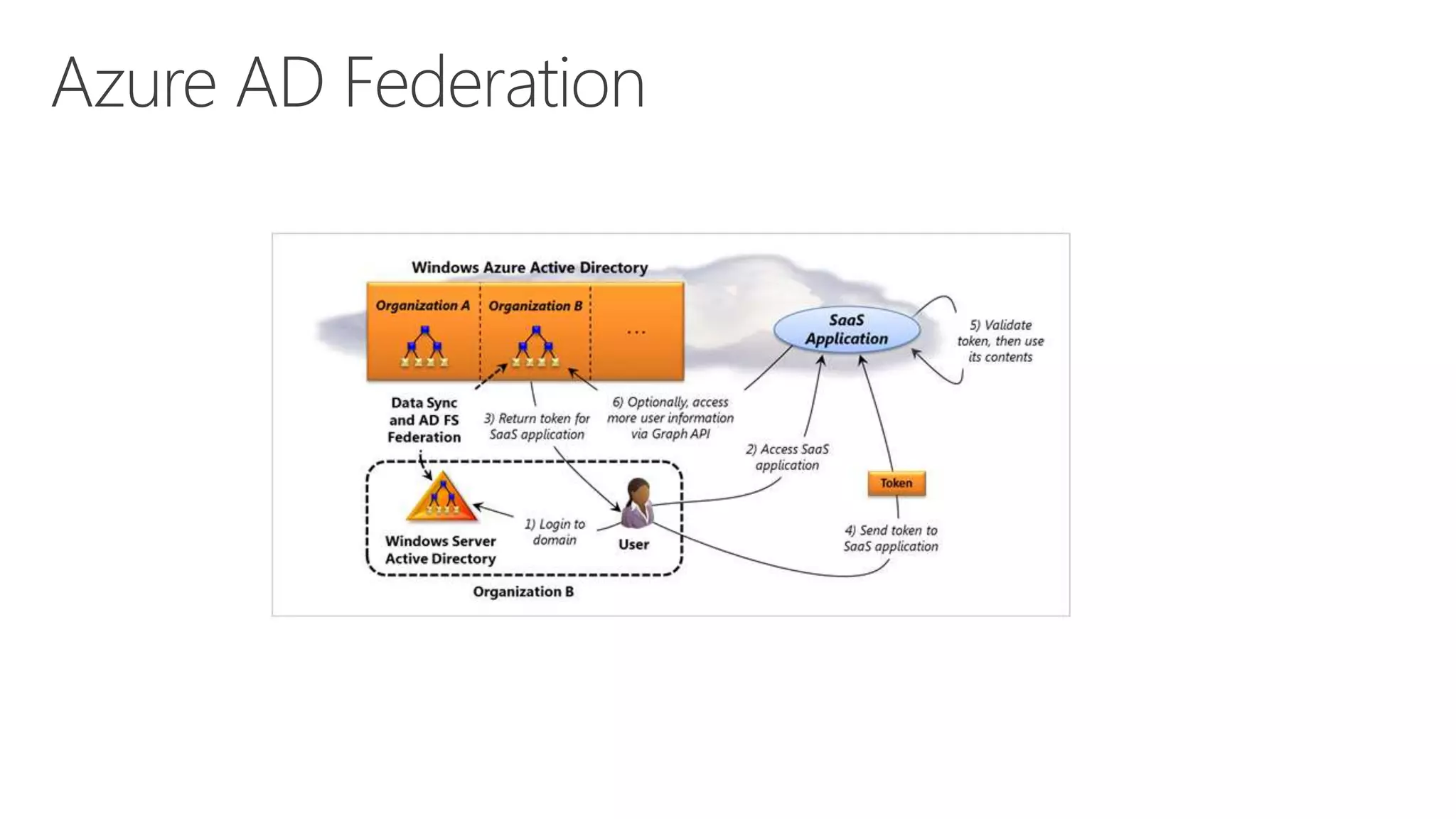
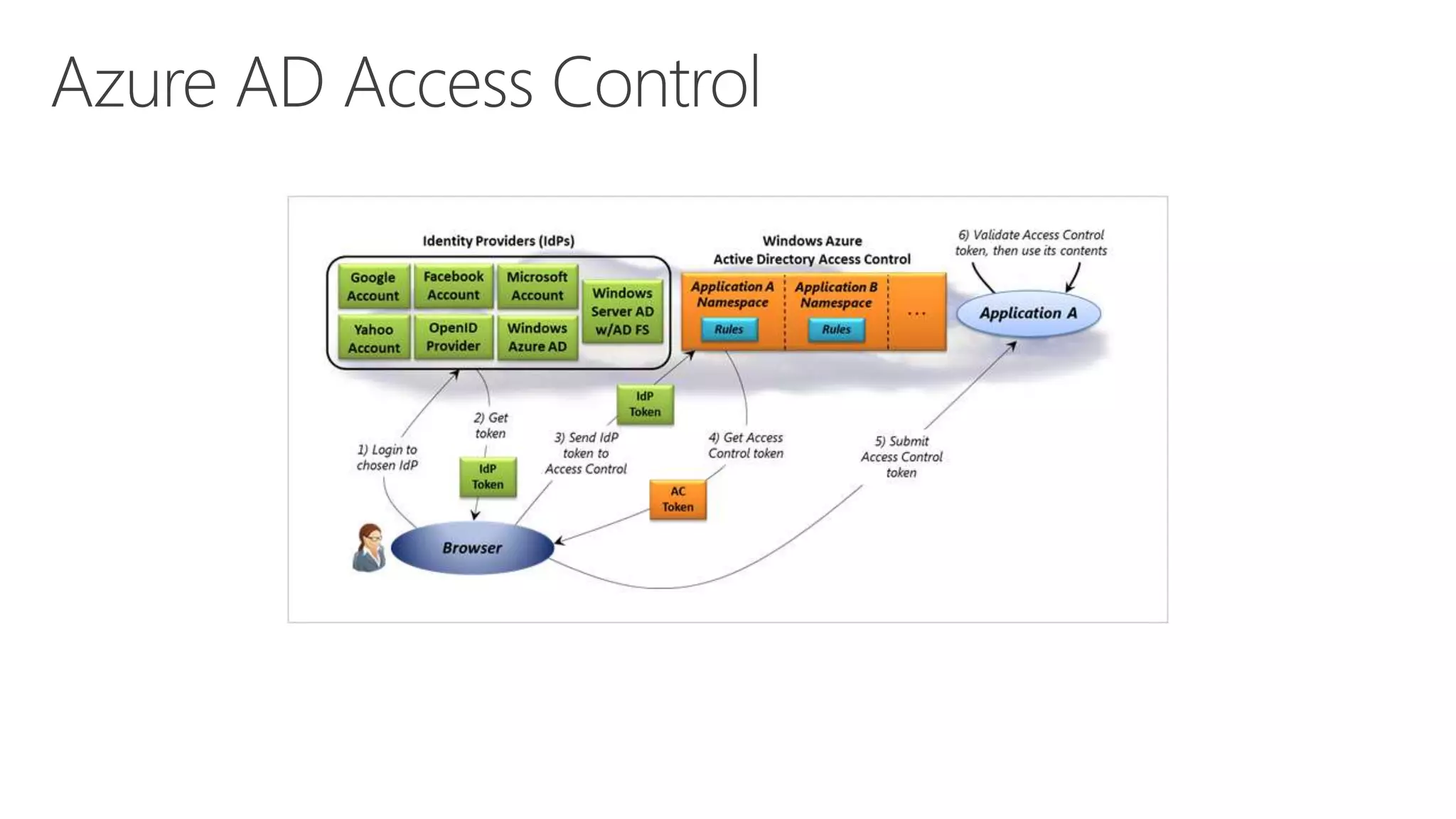
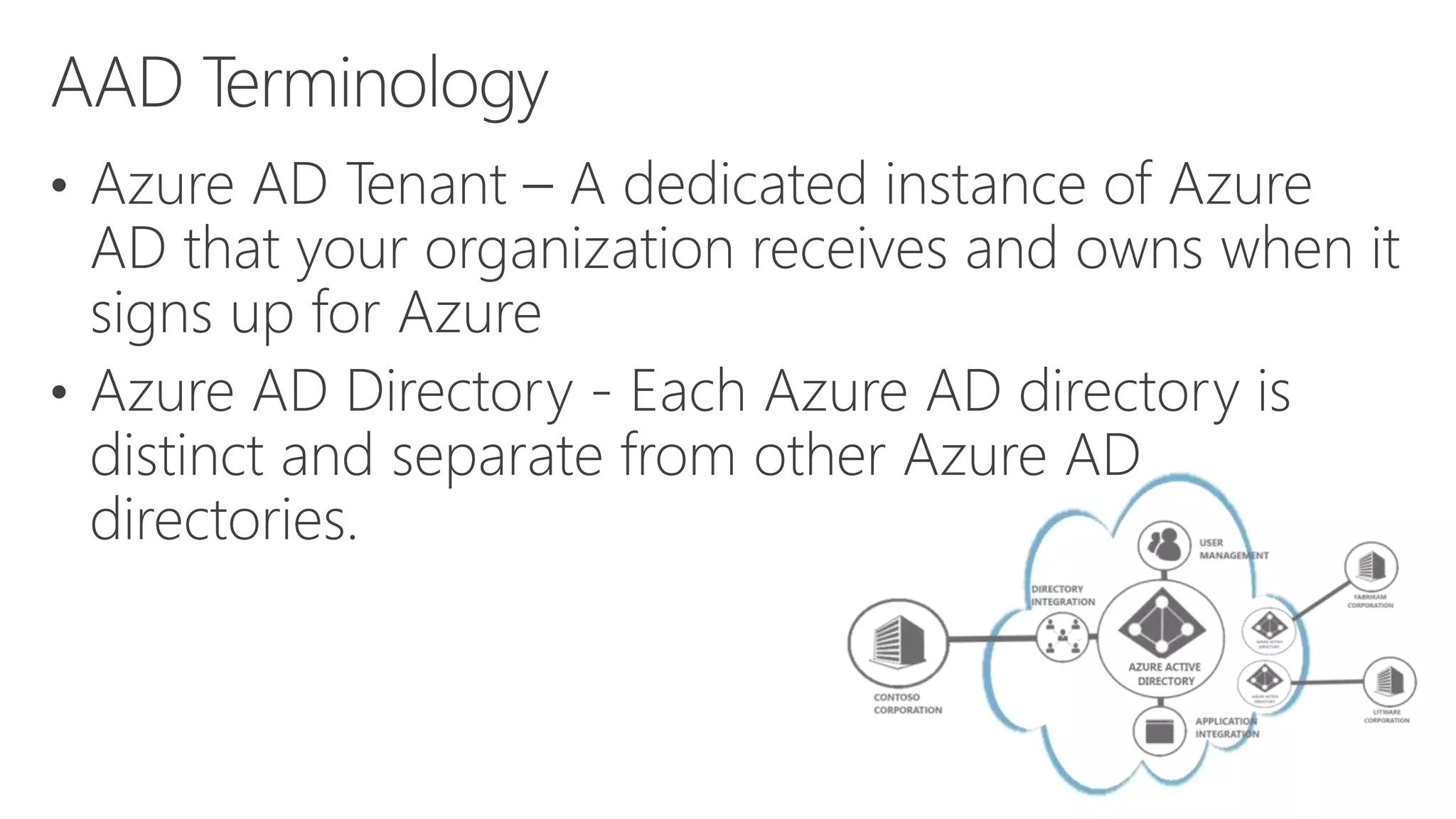
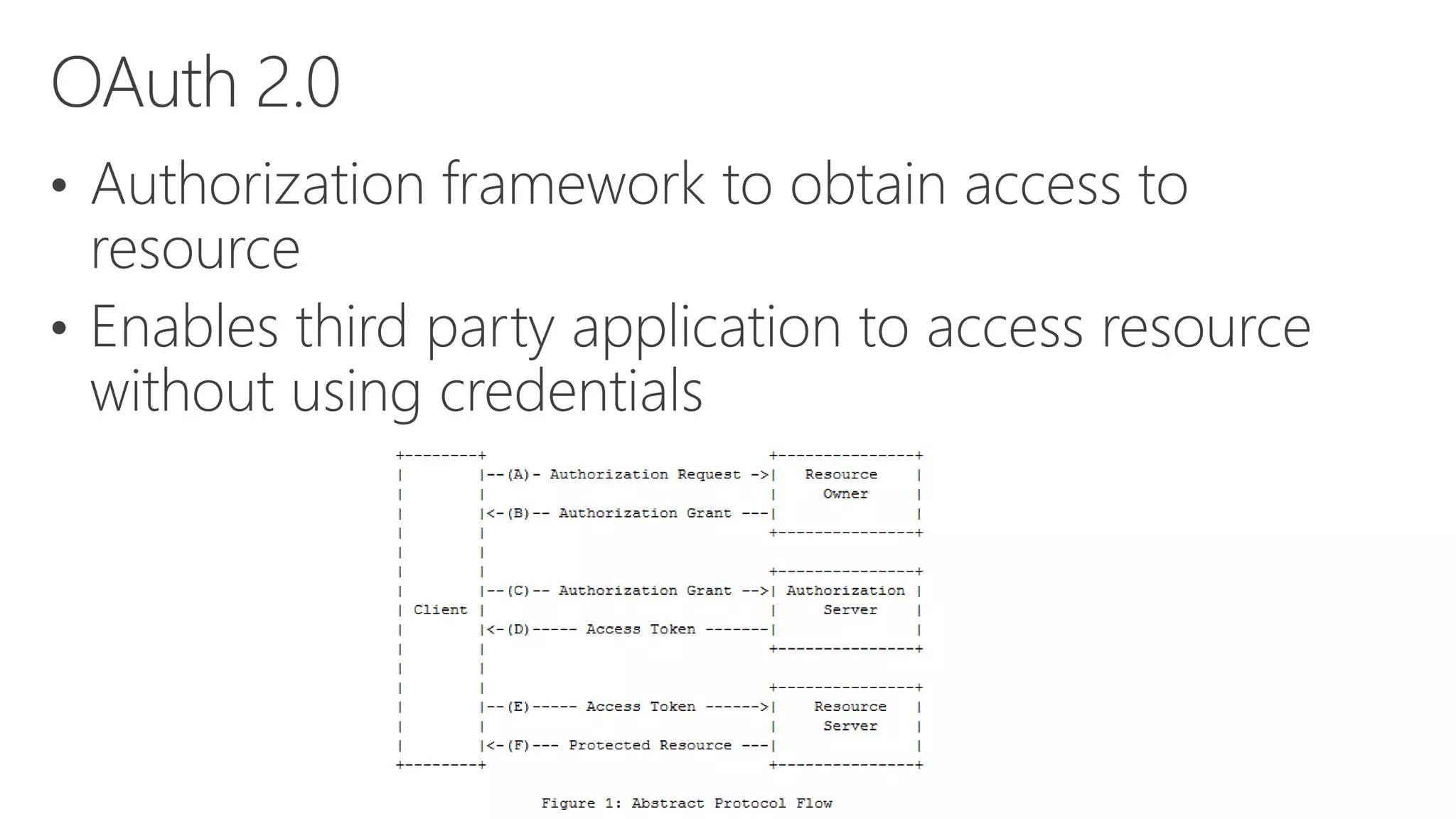
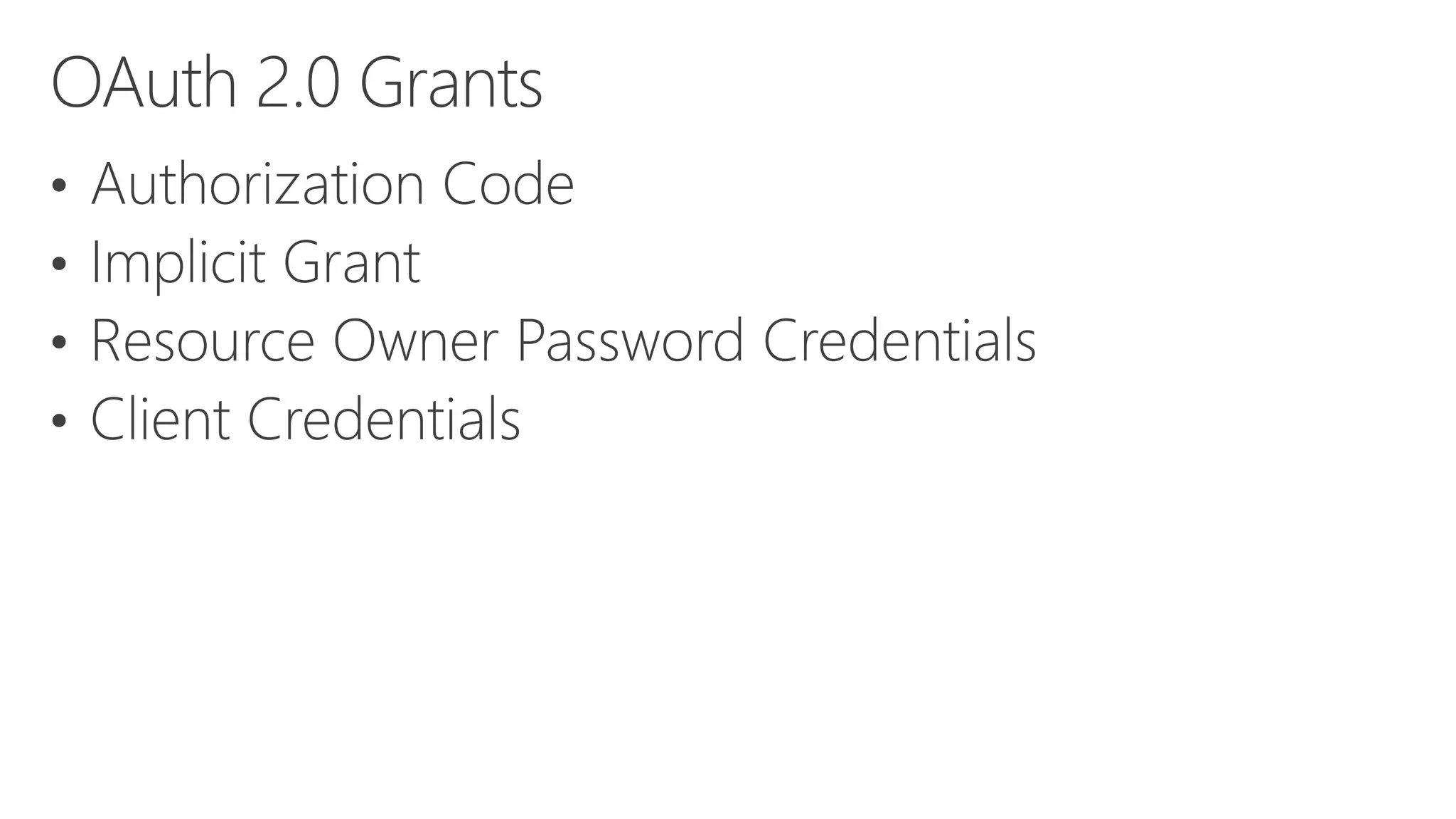
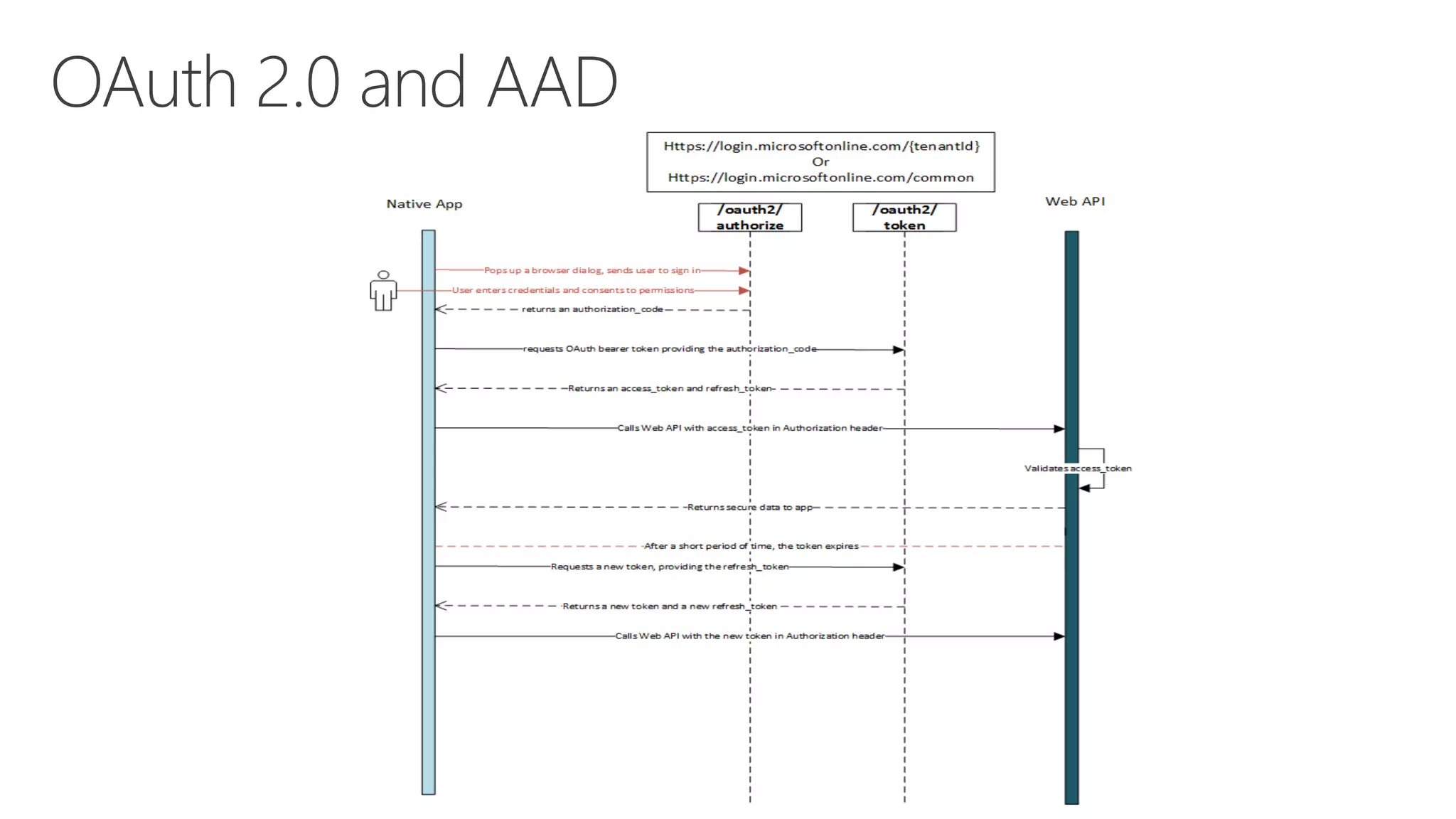
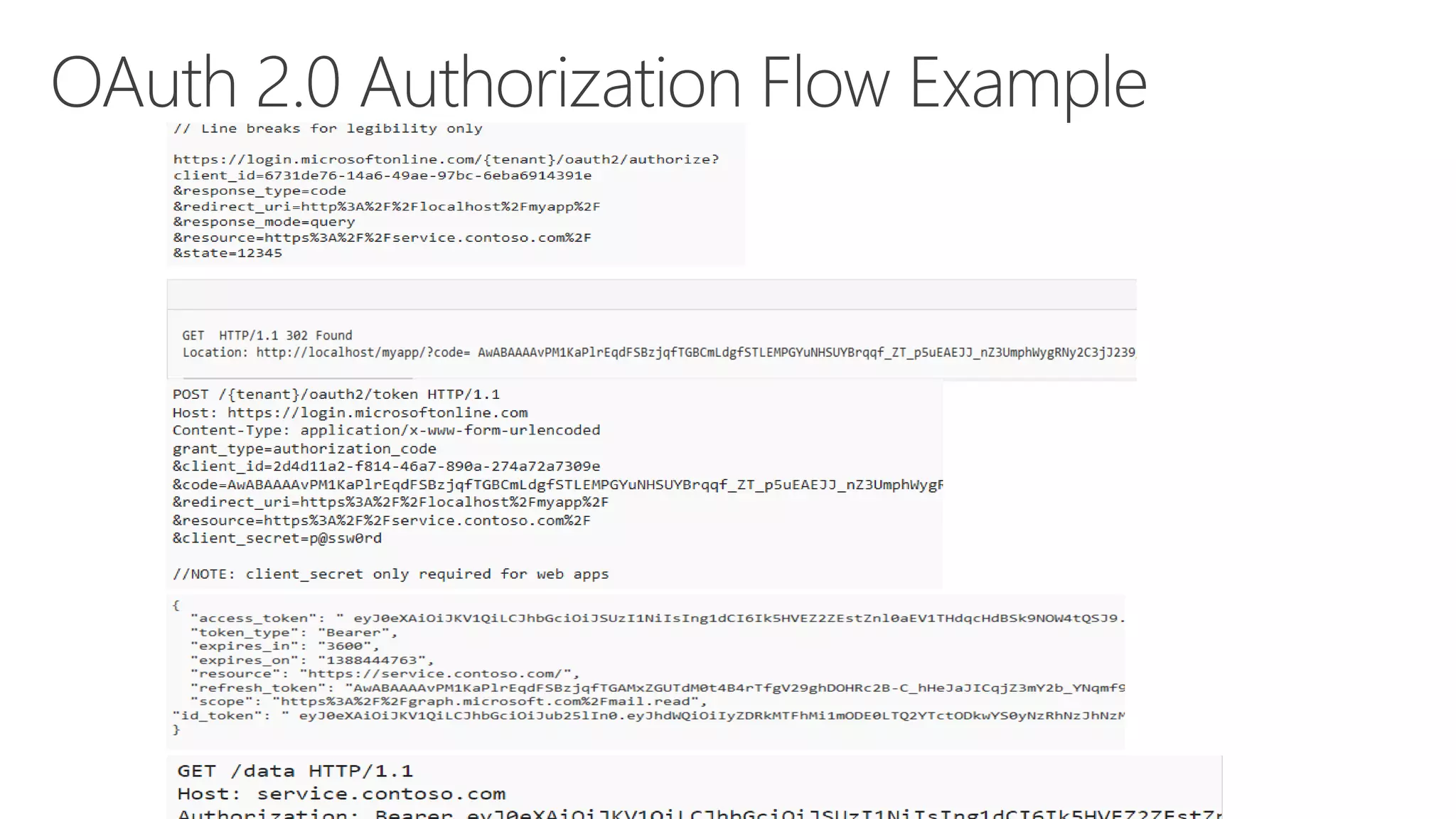
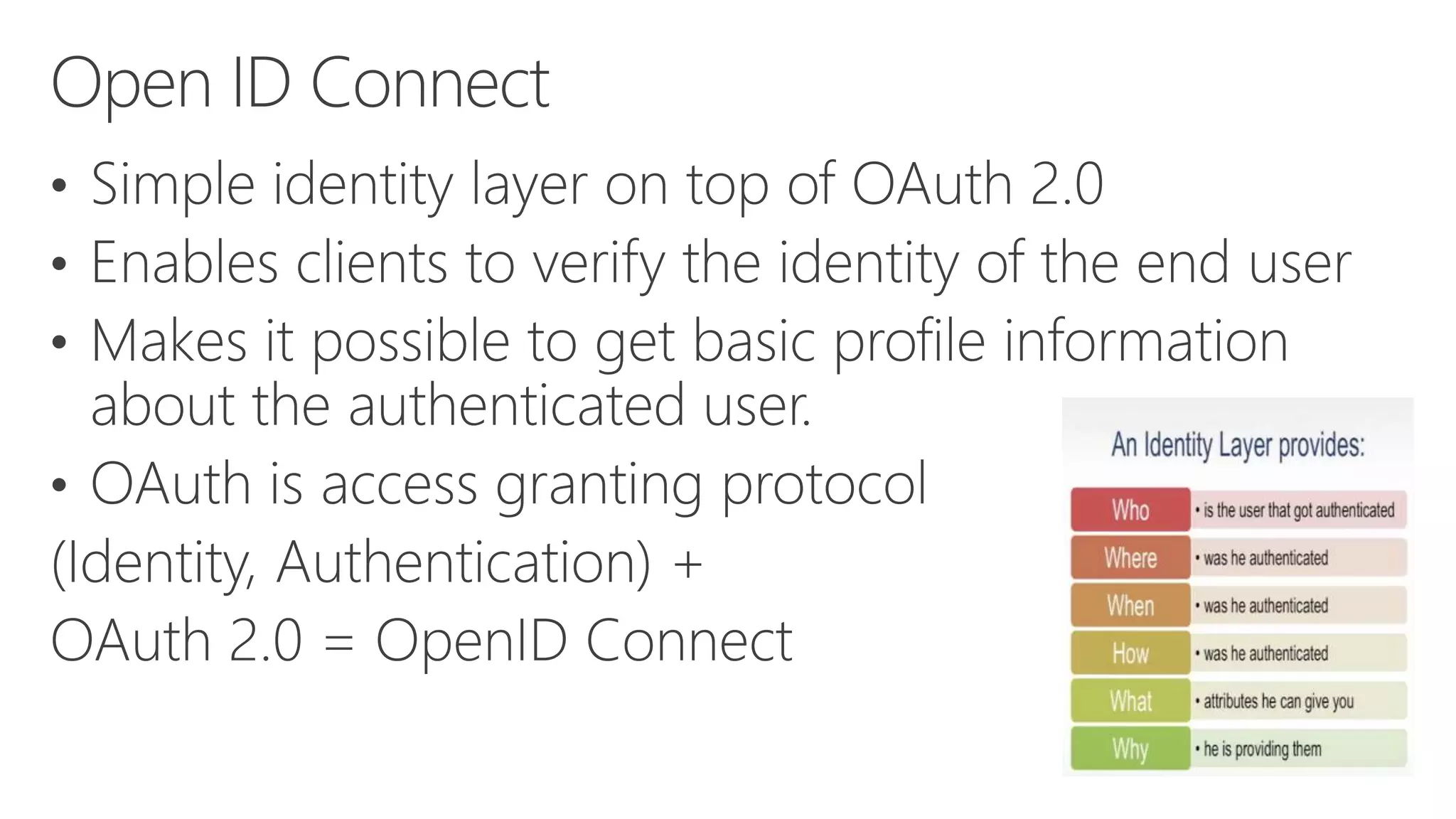
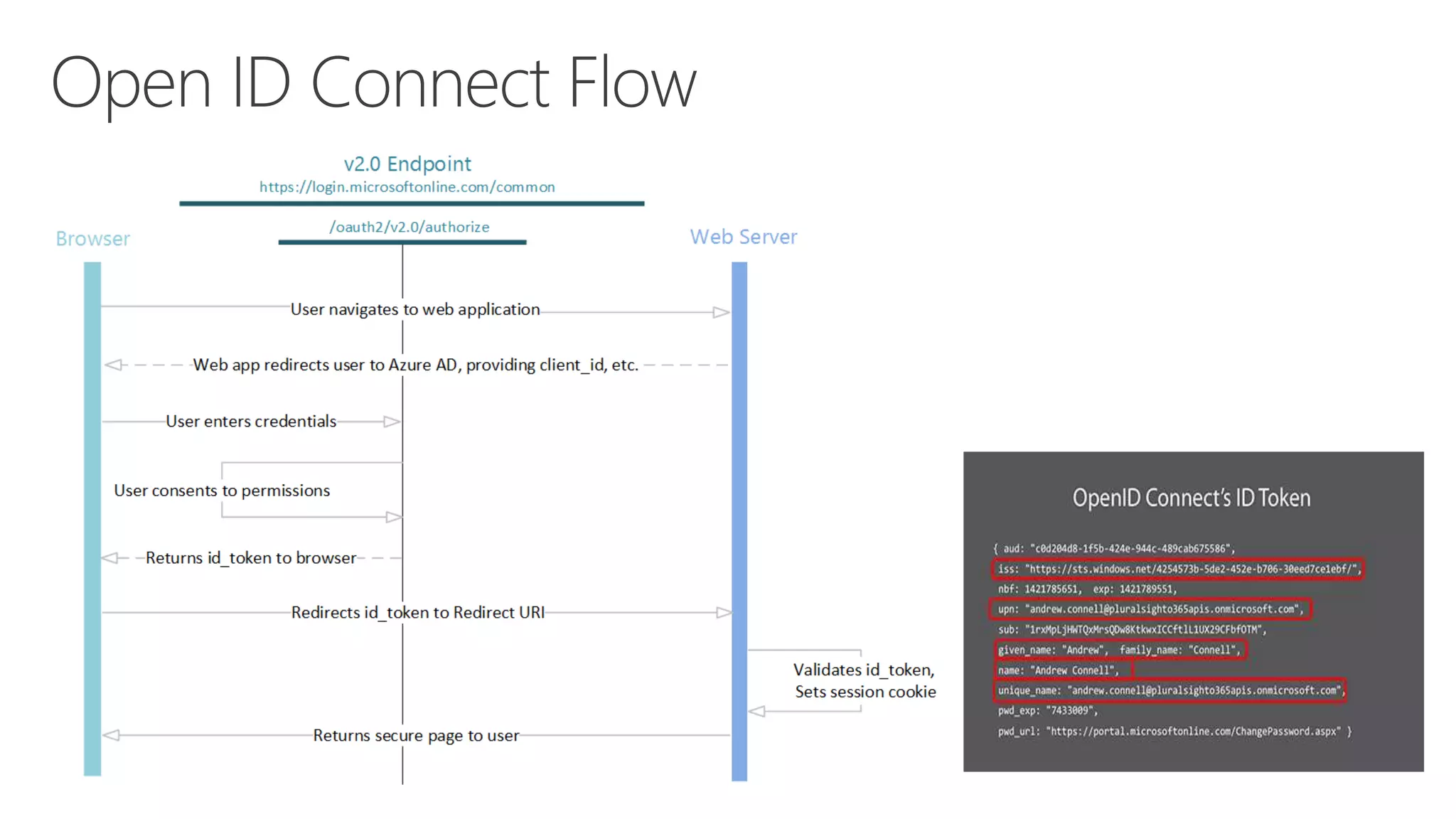
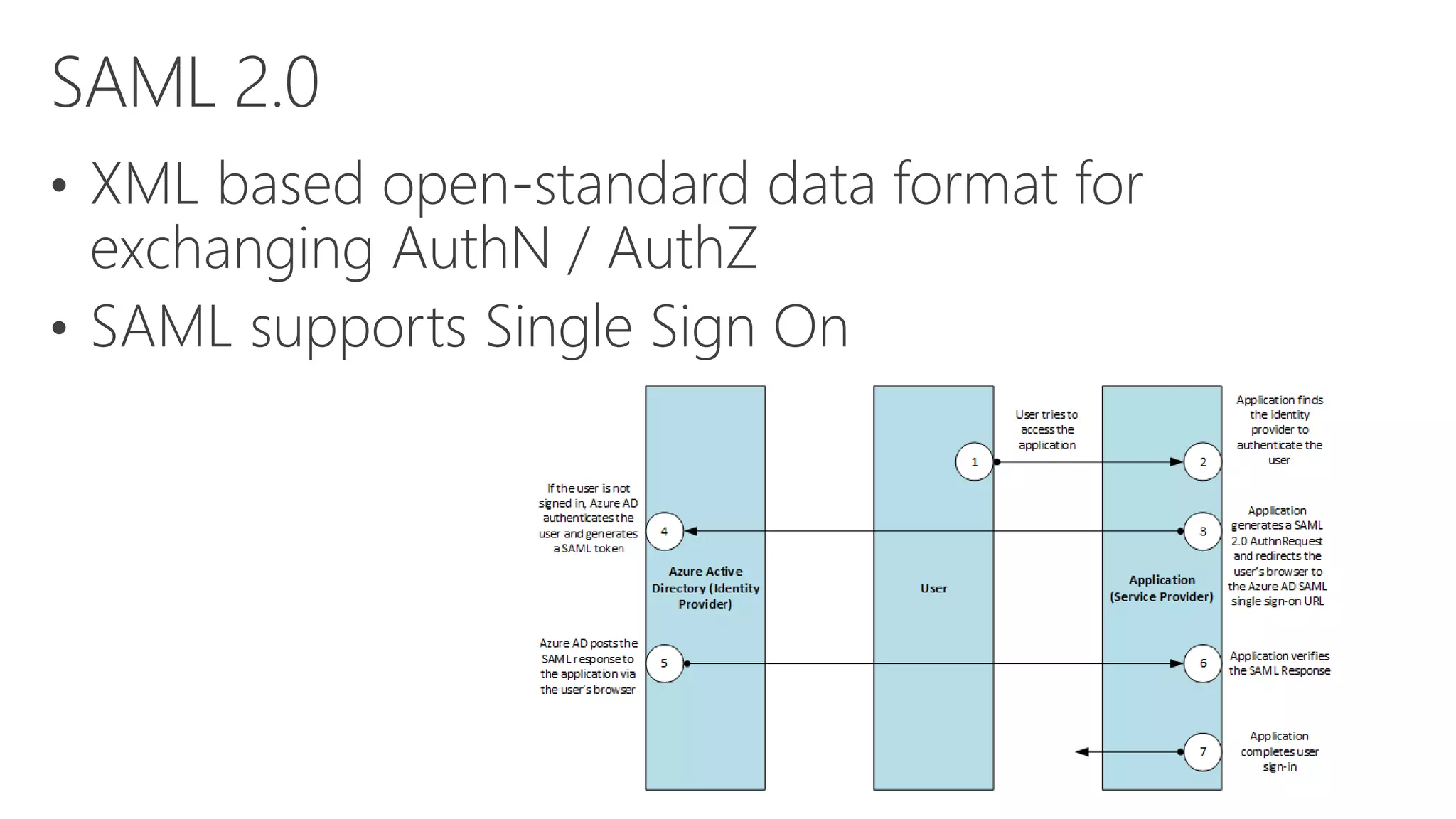
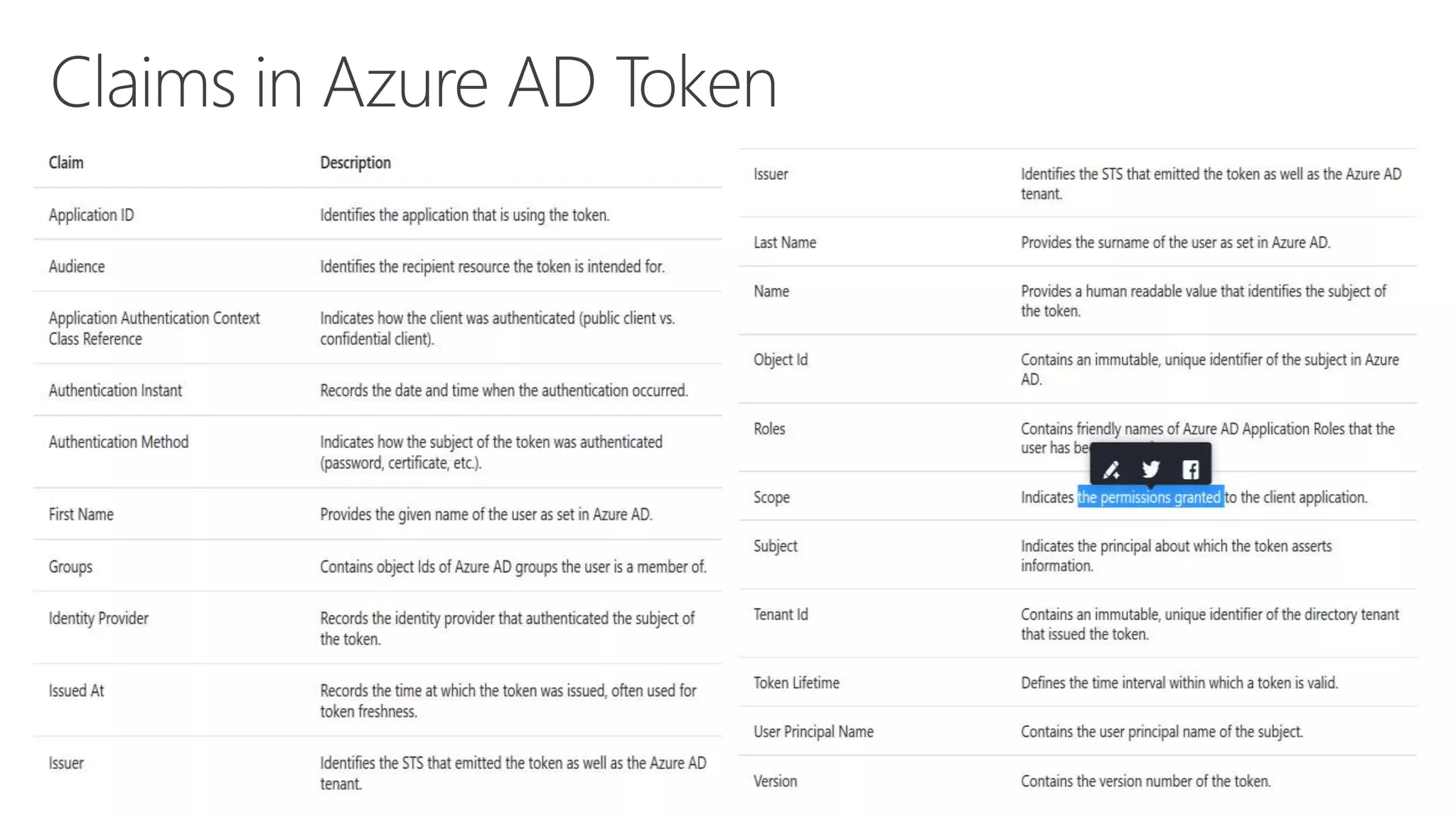
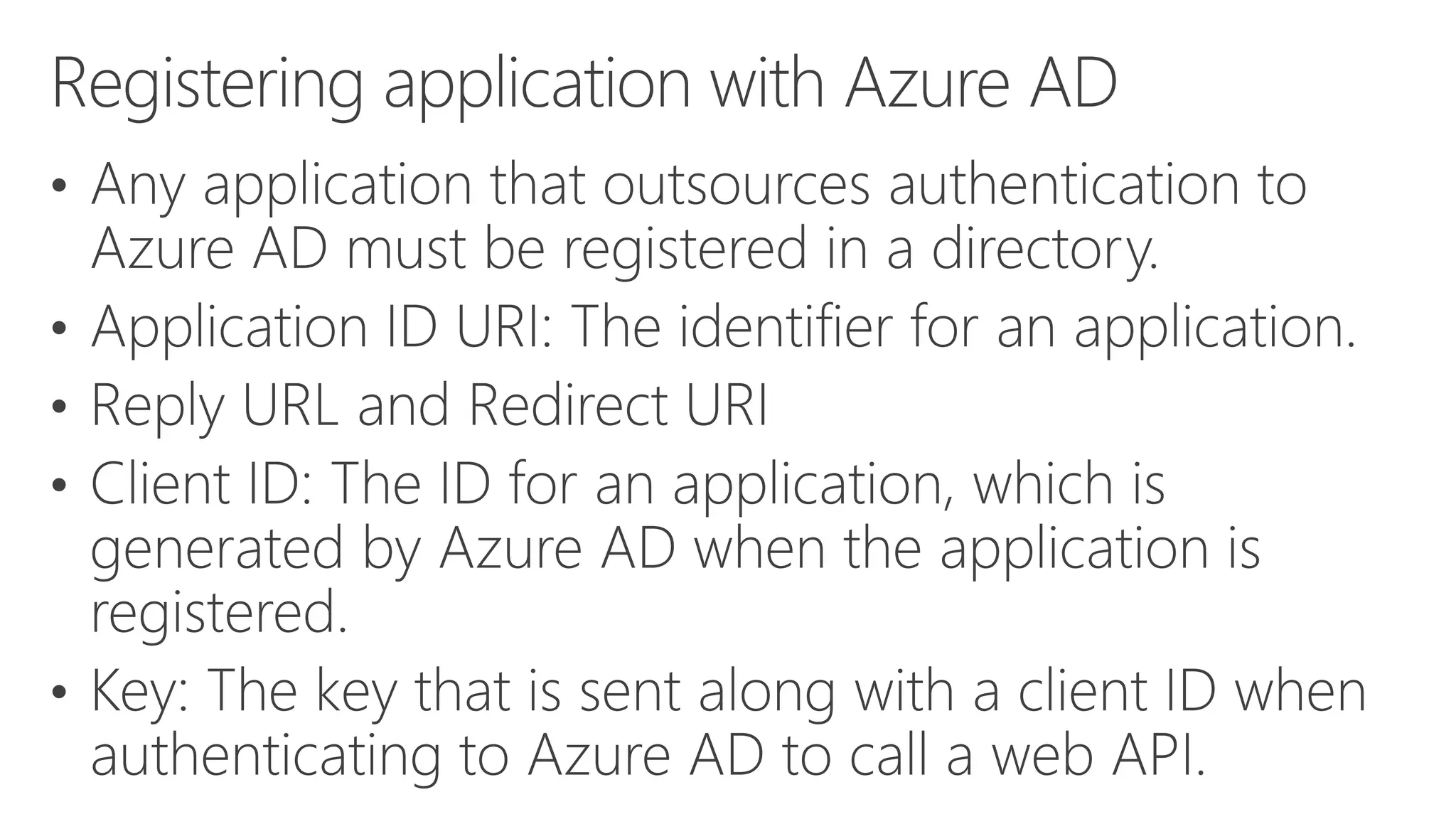
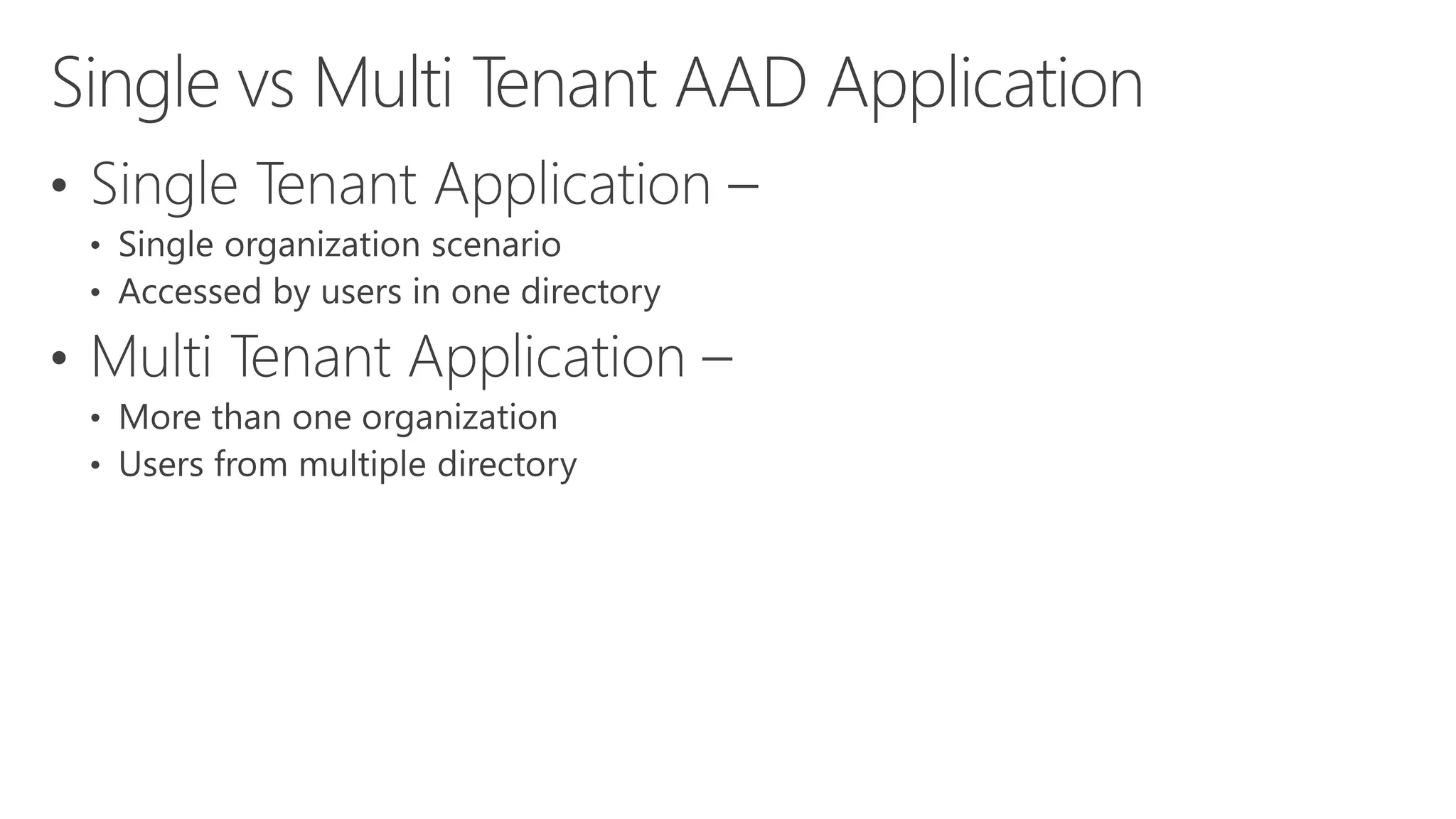
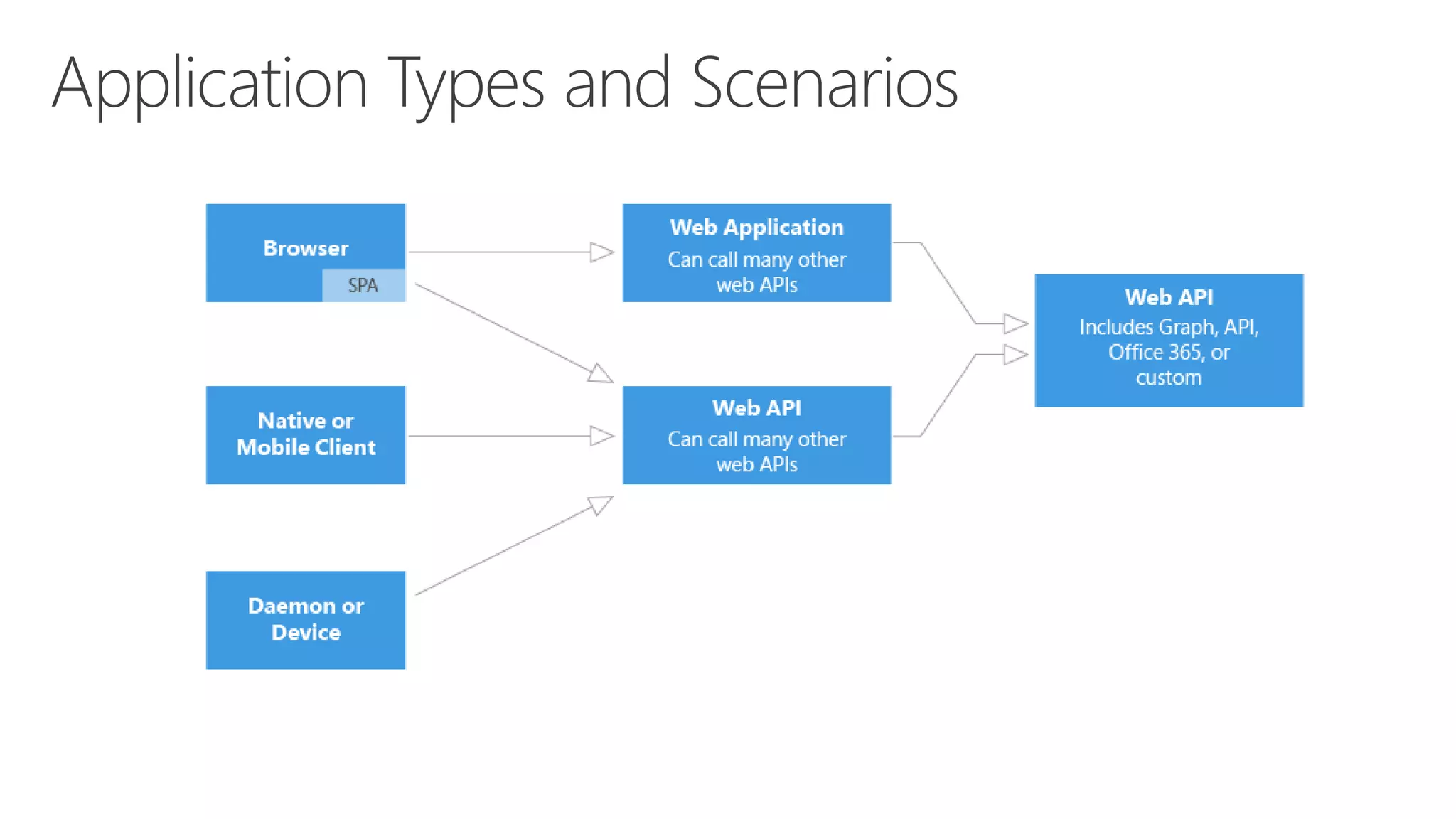
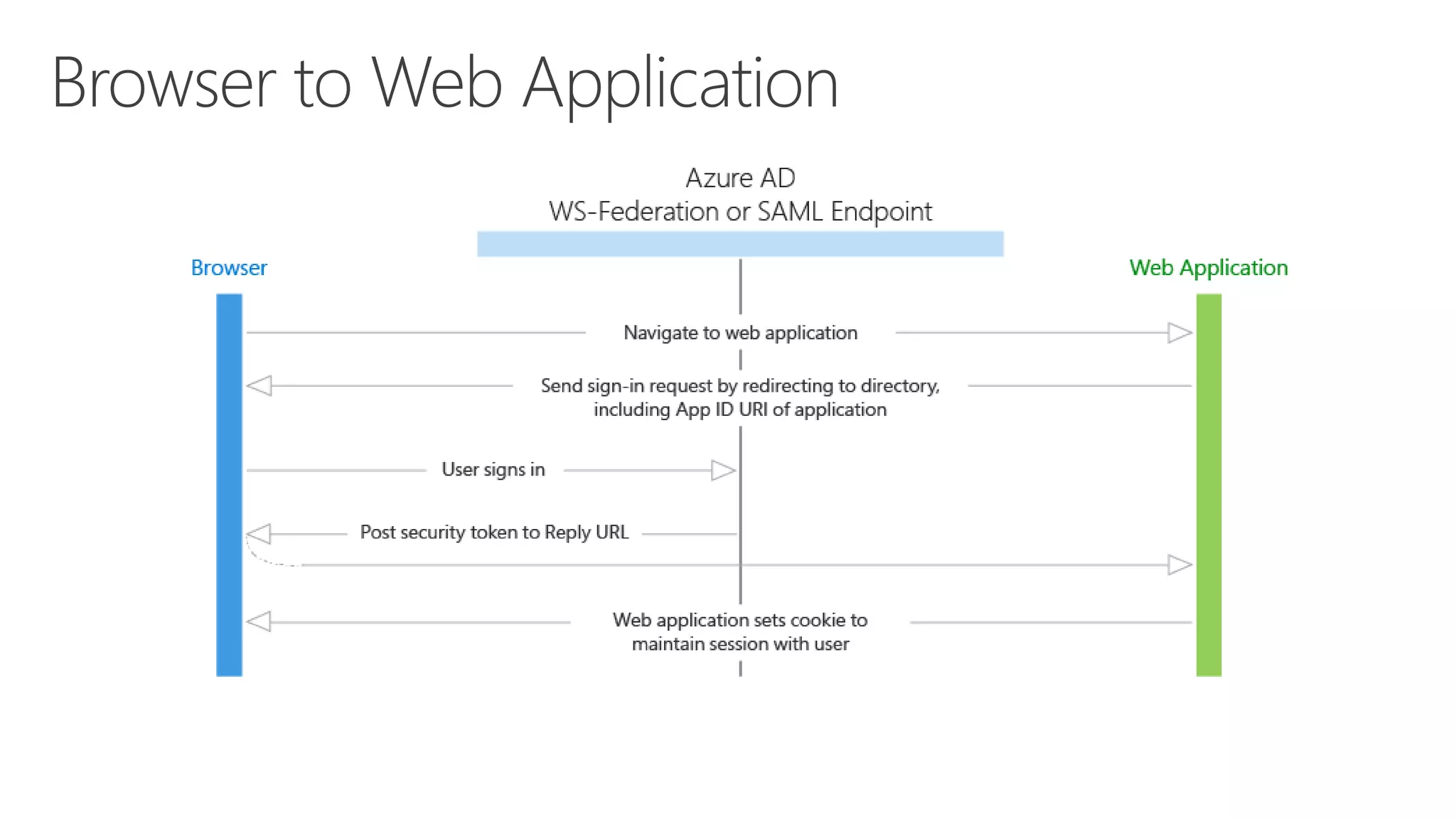
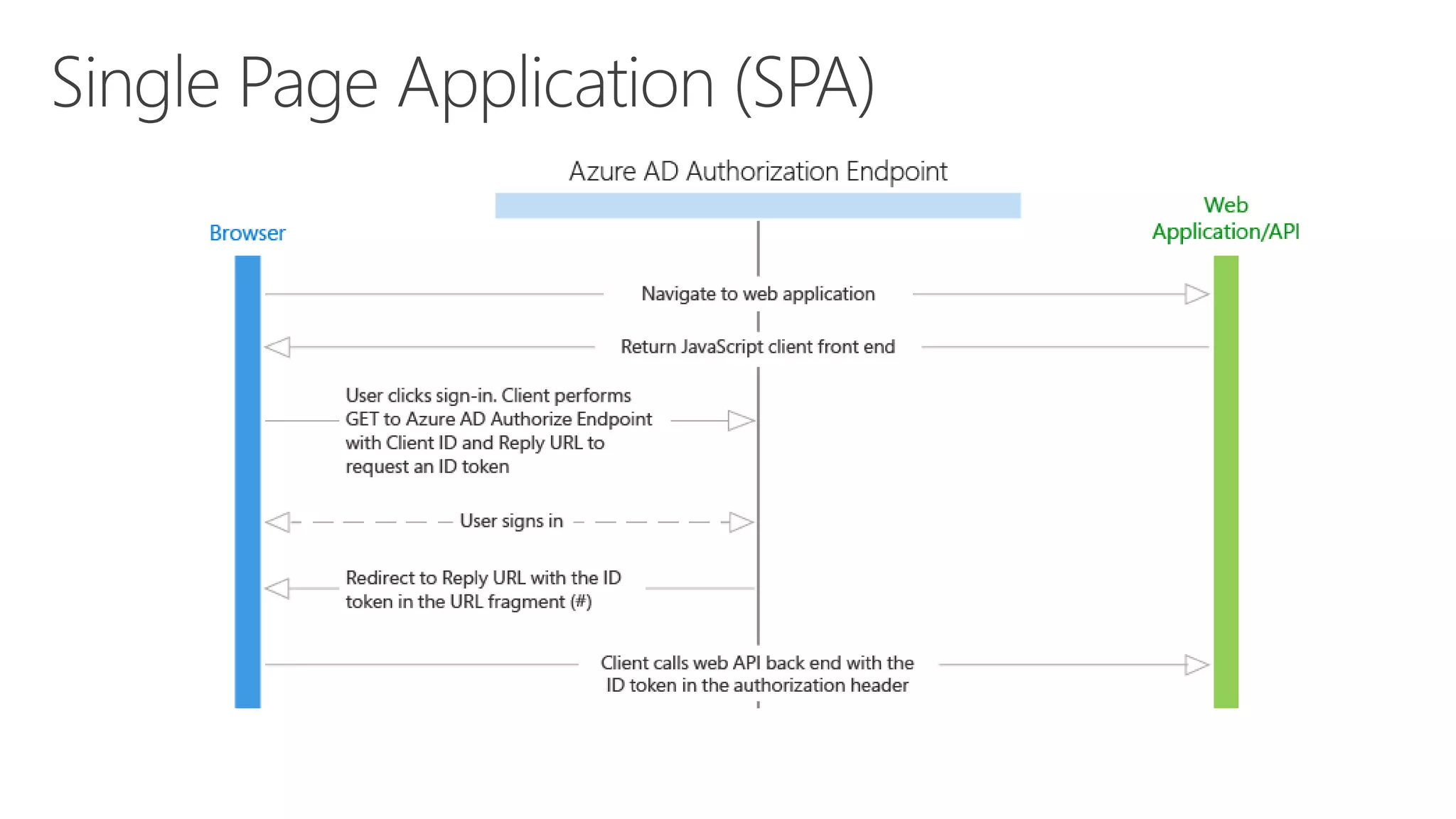
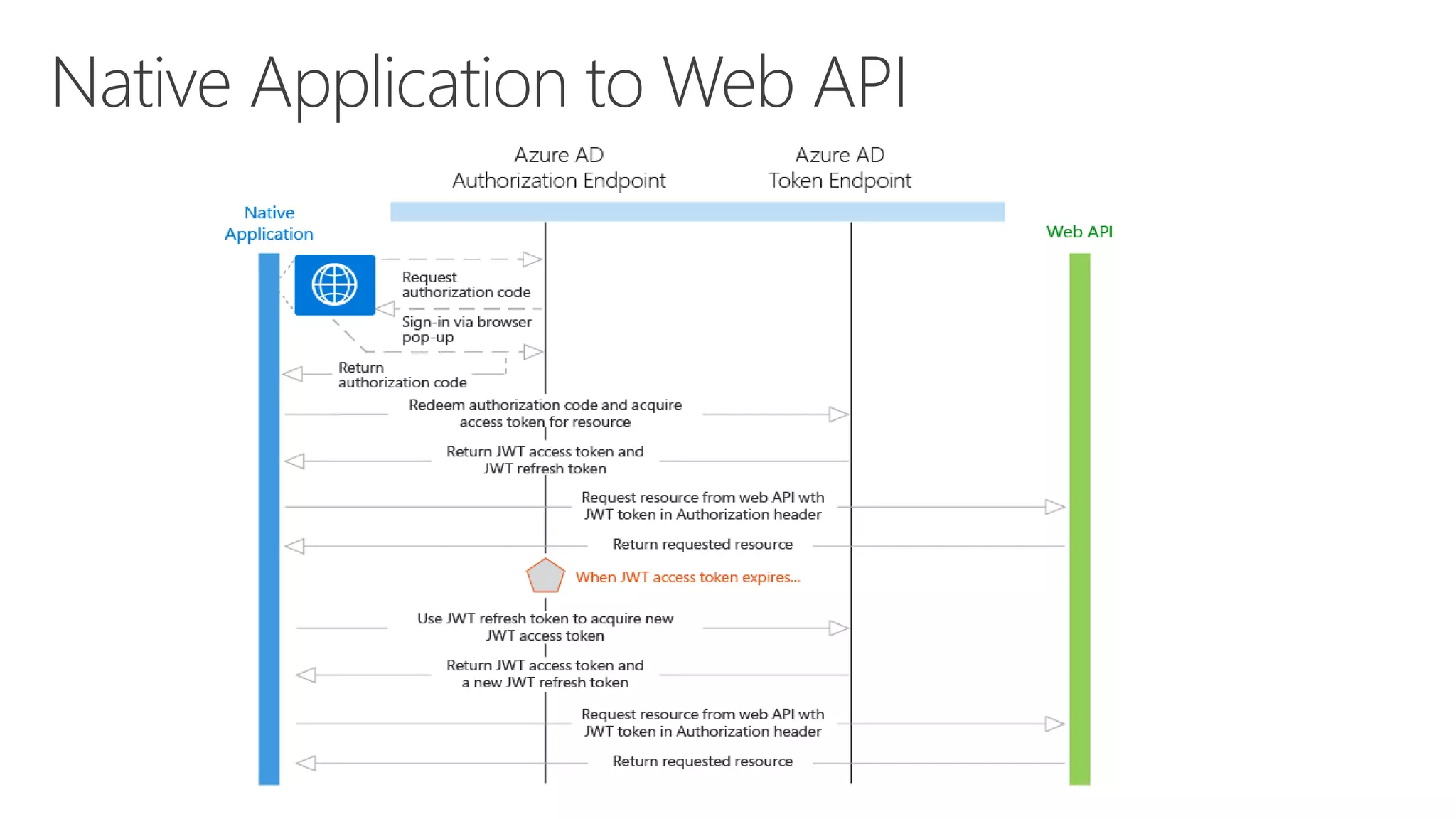
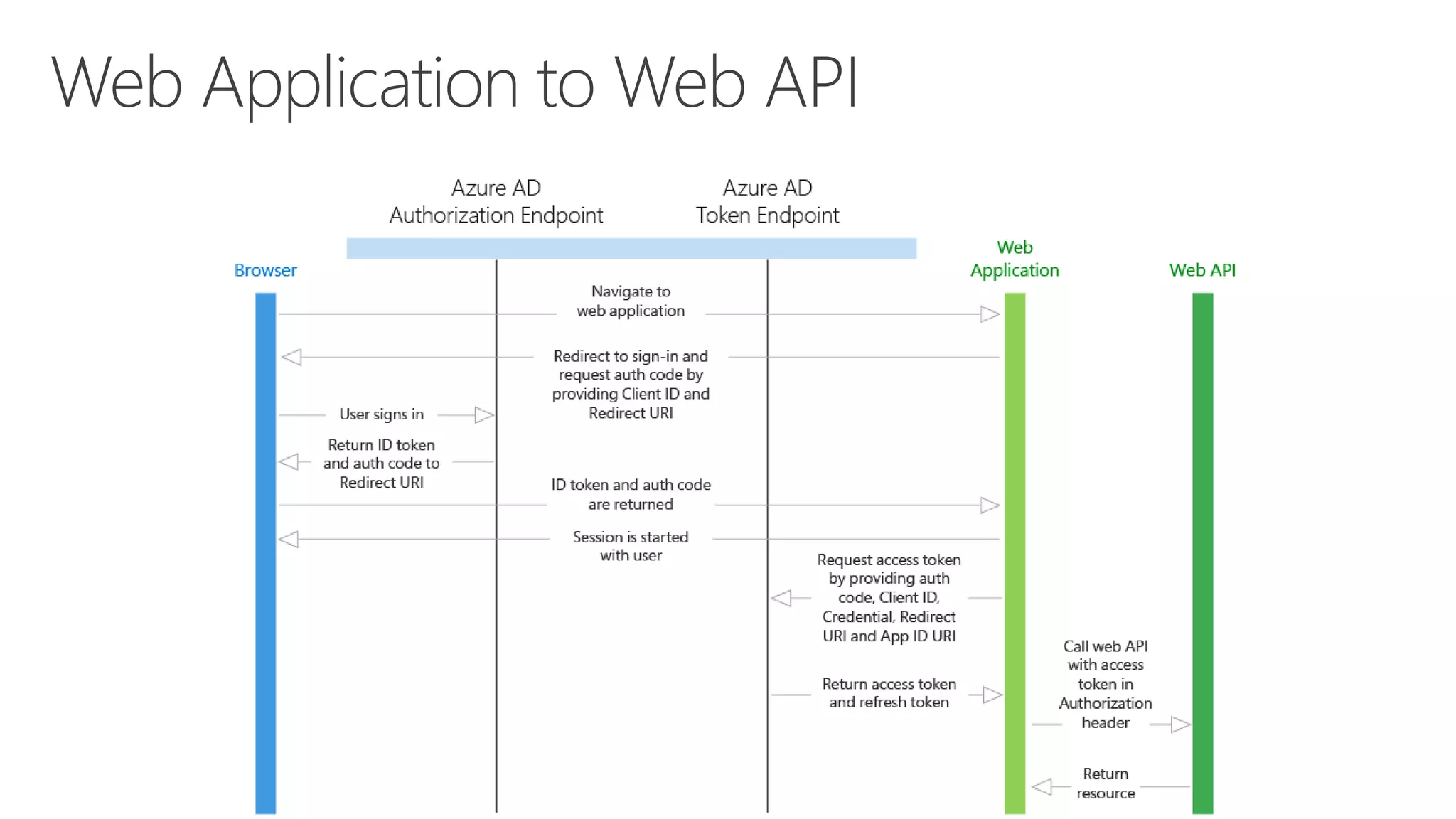
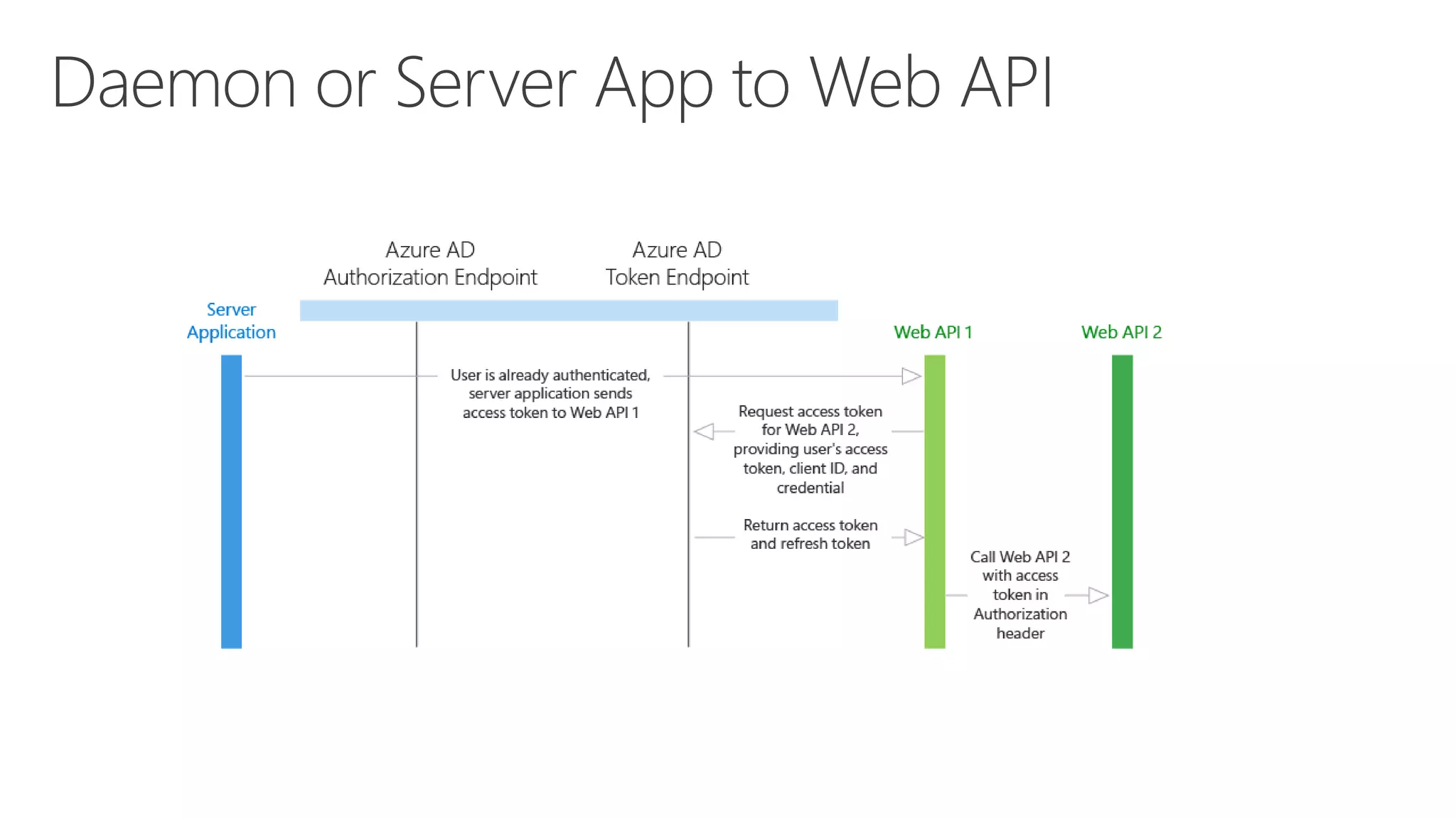
Azure Active Directory (Azure AD) is Microsoft's cloud-based identity and access management service. It authenticates over 1 trillion times since release and manages identity data for over 5 million organizations, including 86% of Fortune 500 companies using Microsoft Cloud services. Azure AD provides single sign-on, multi-factor authentication, and application access management across devices and platforms.