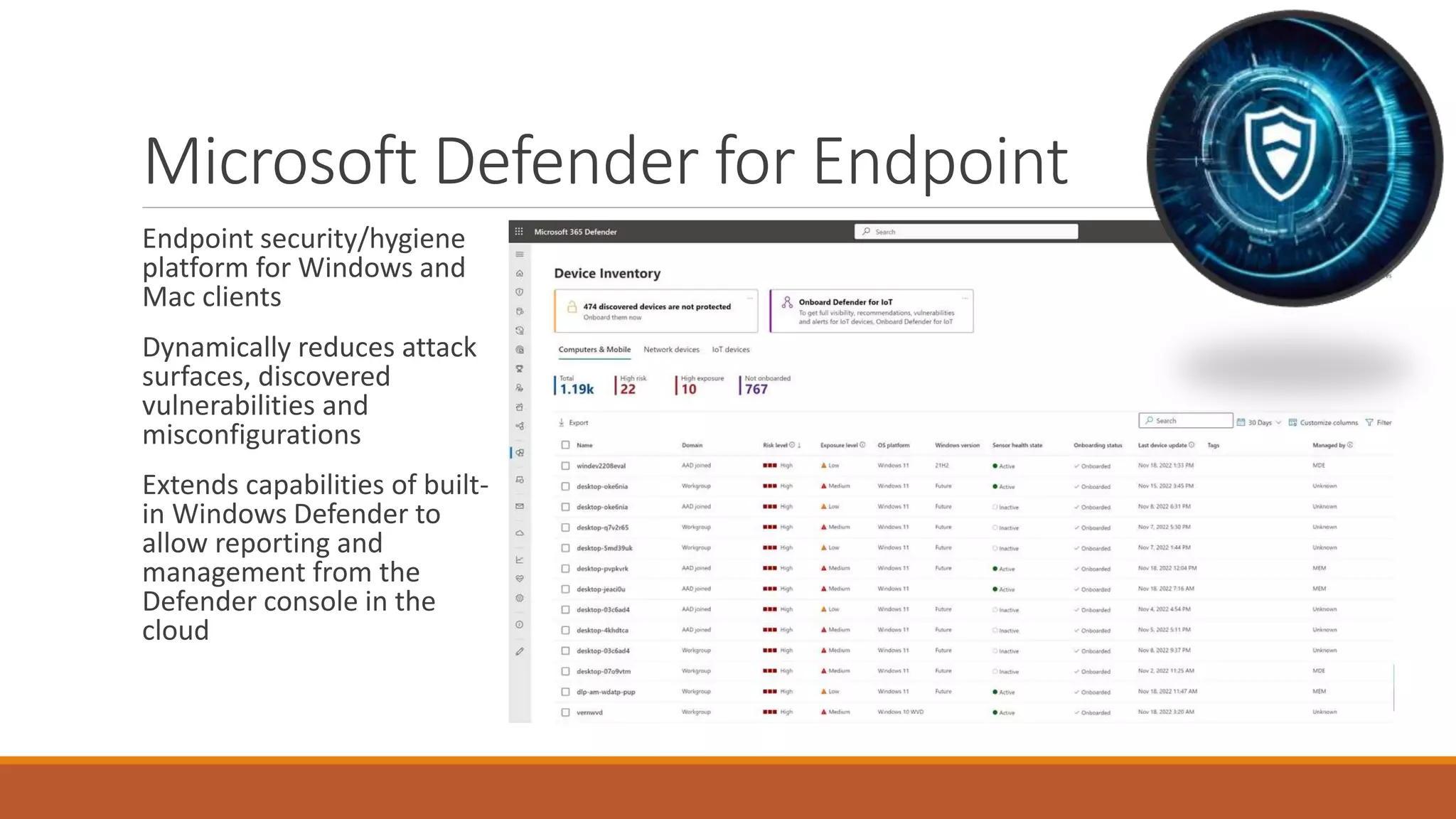
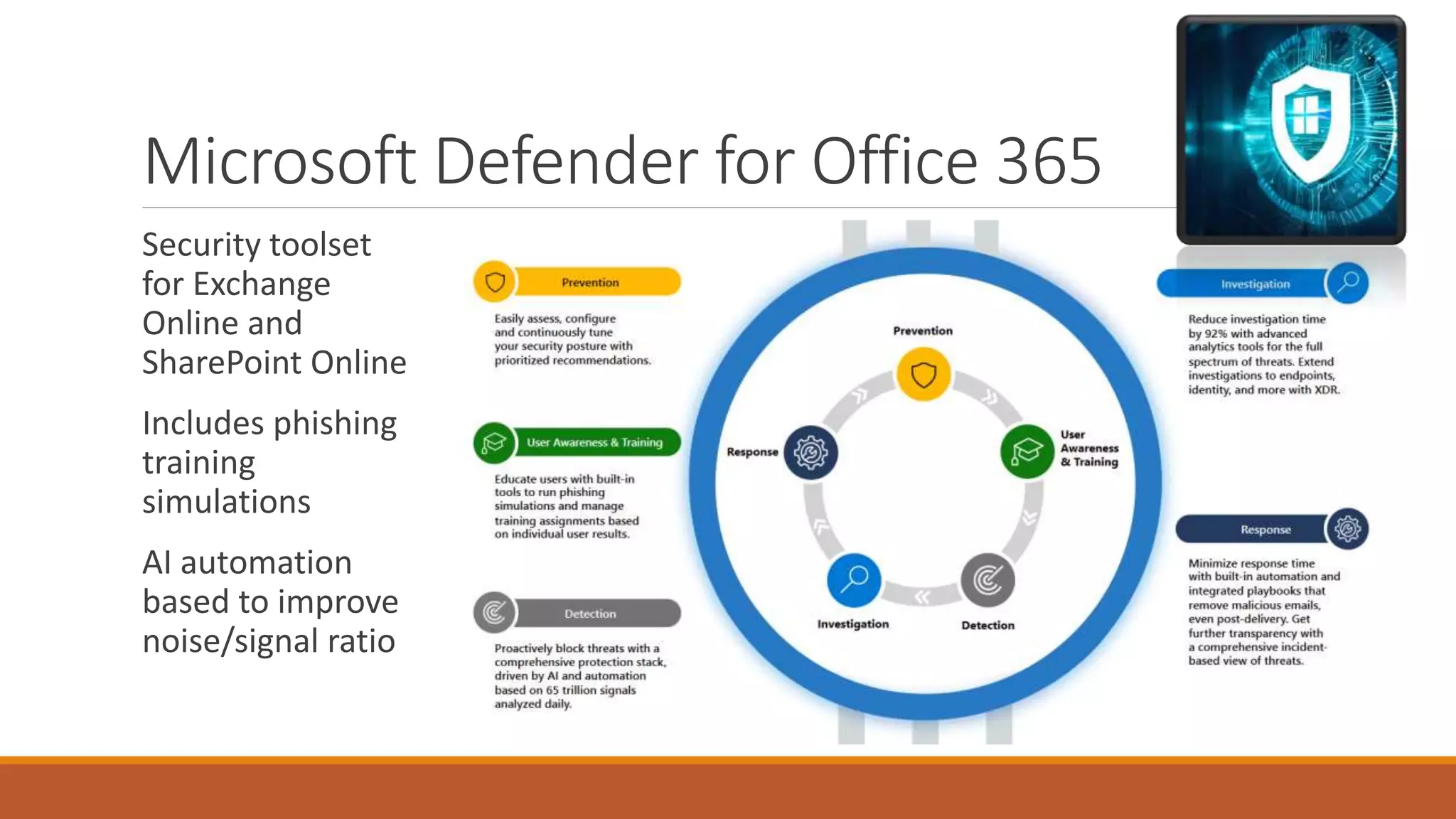
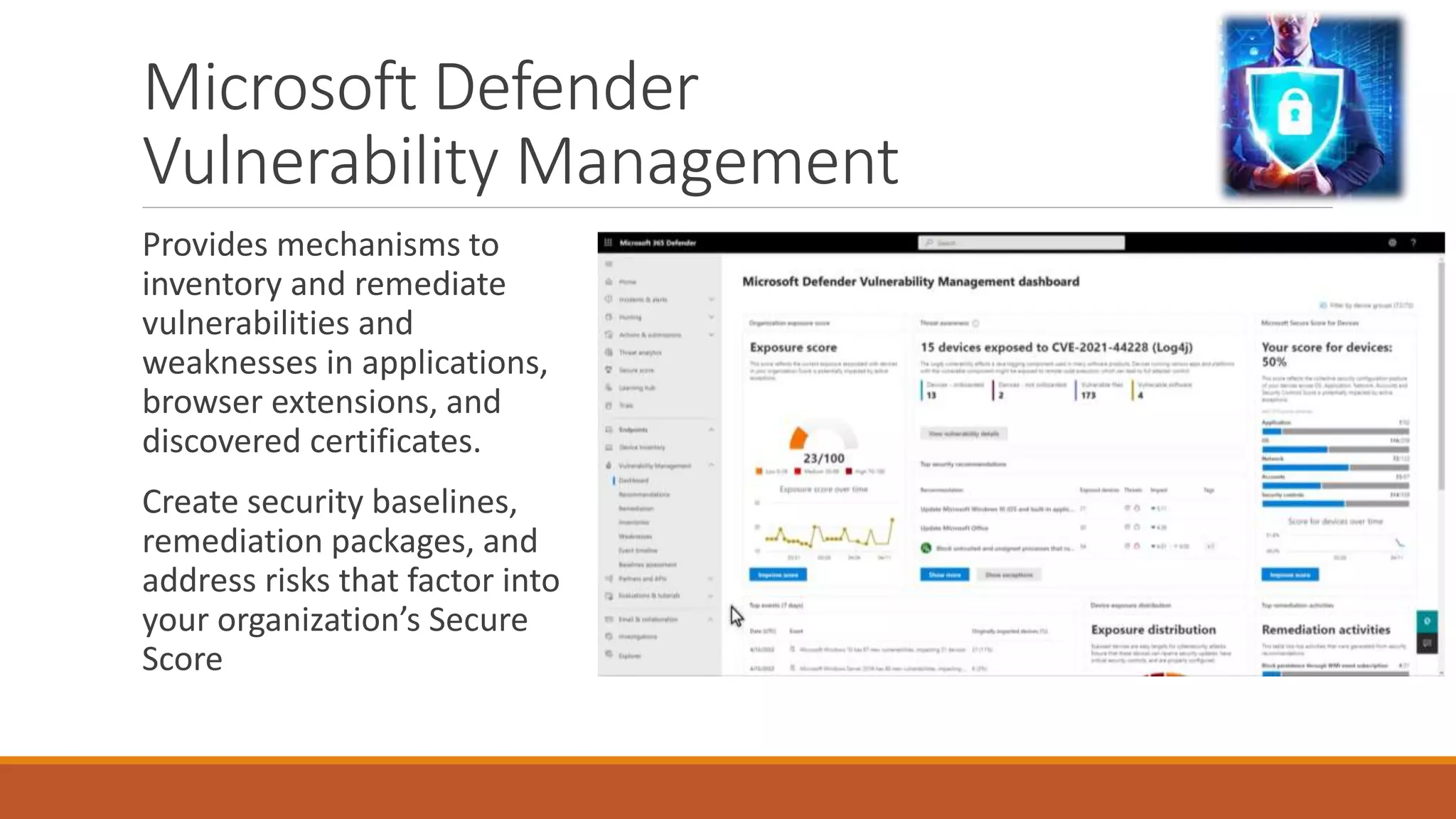
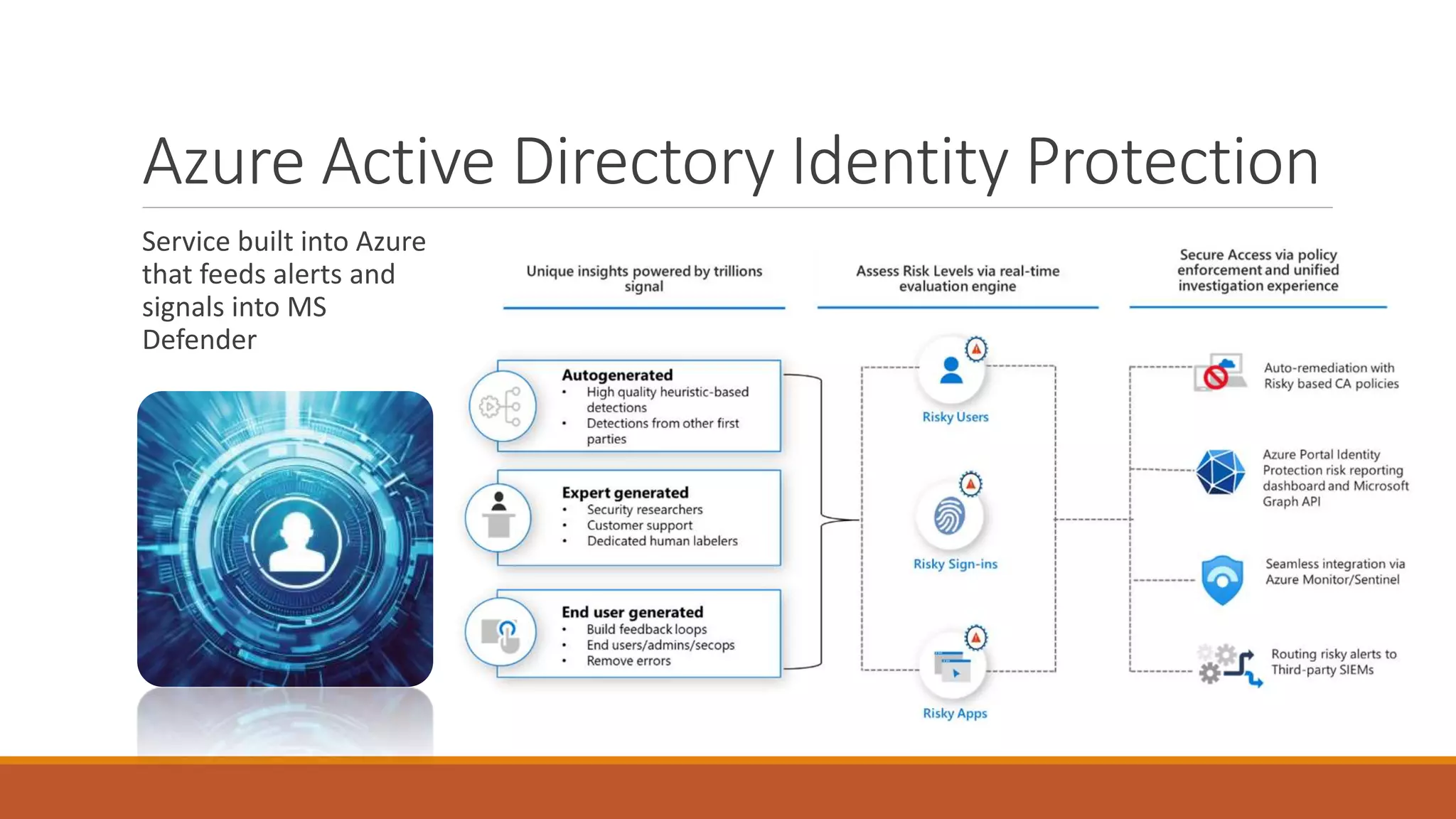
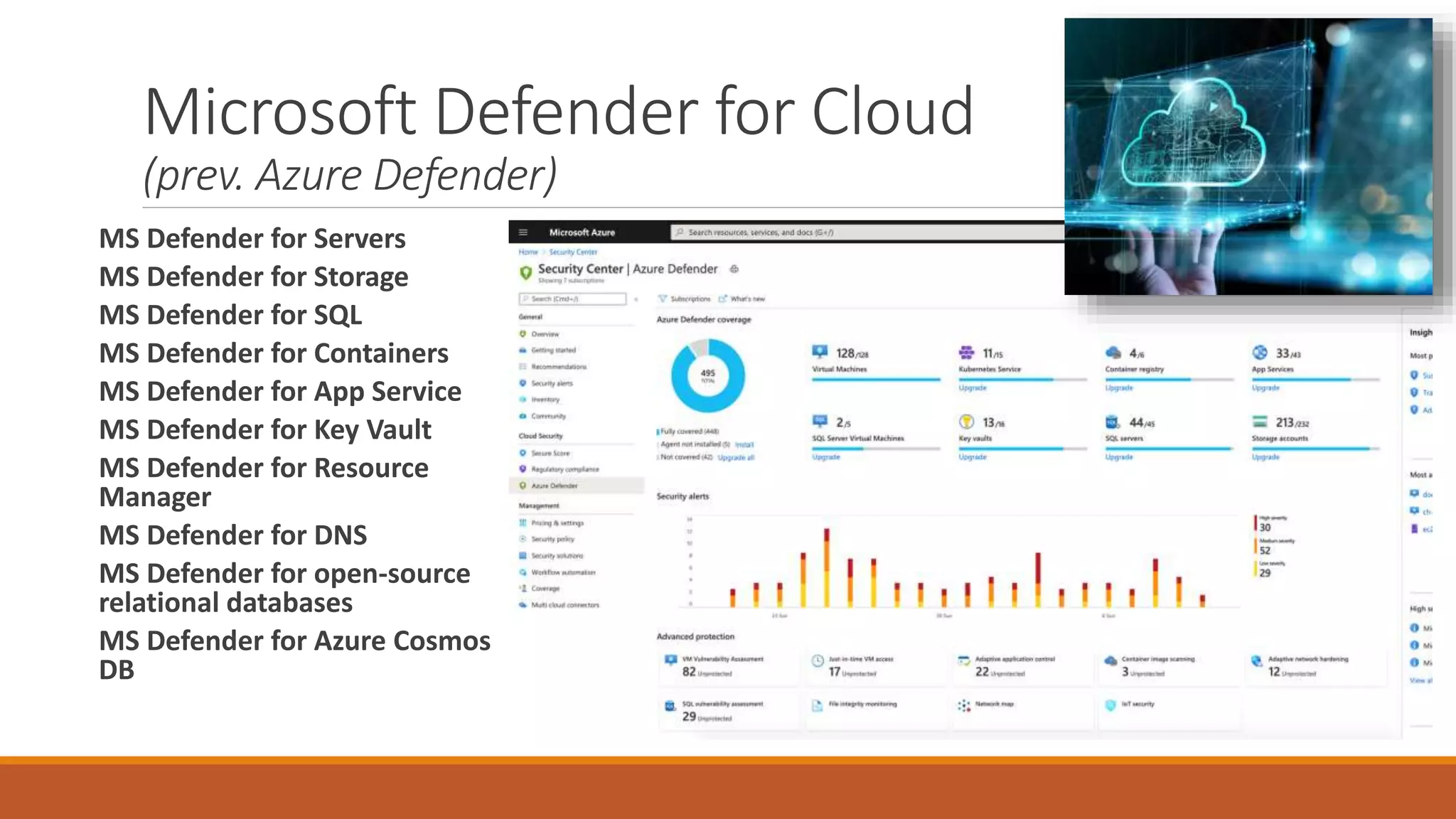
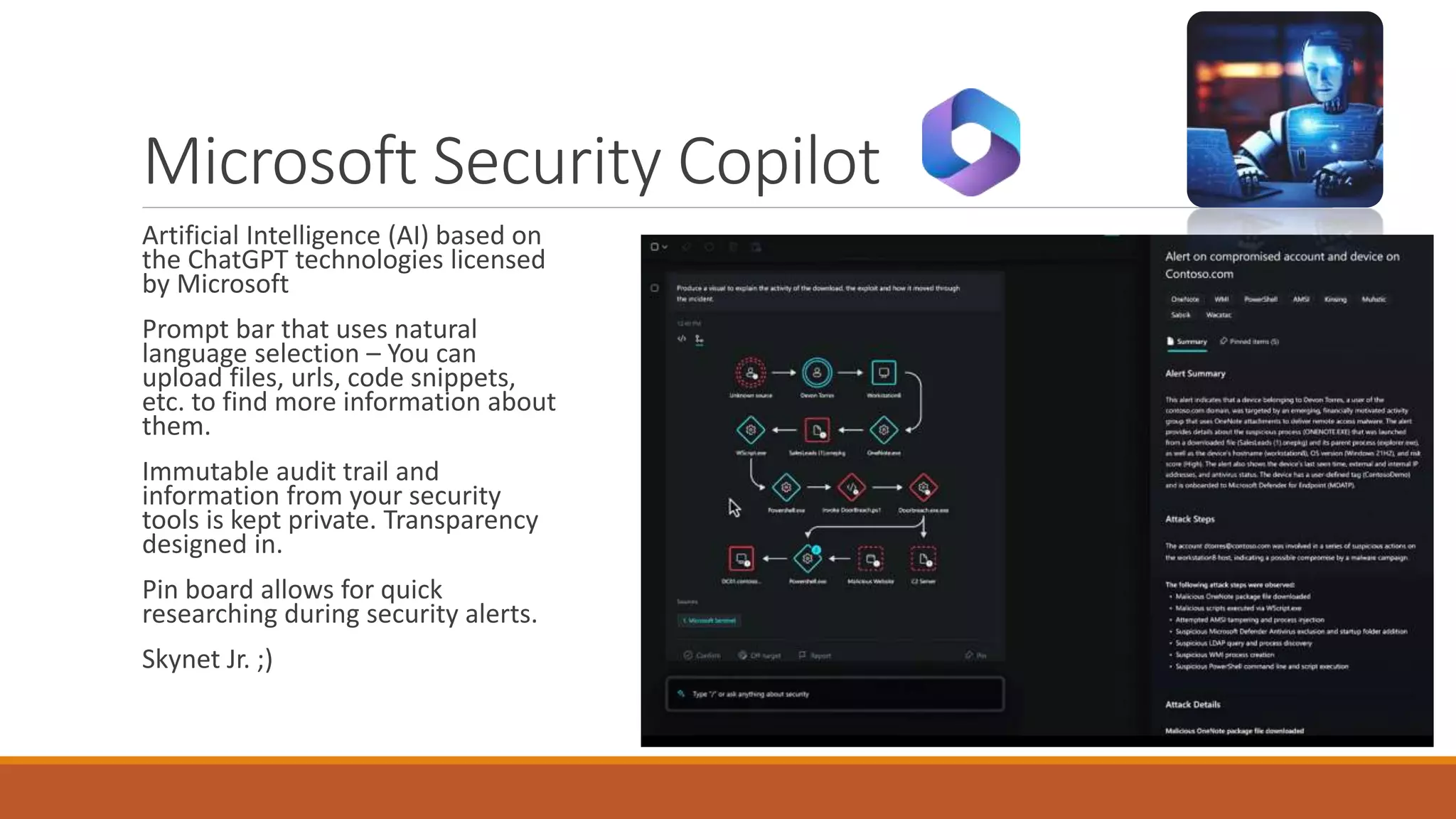
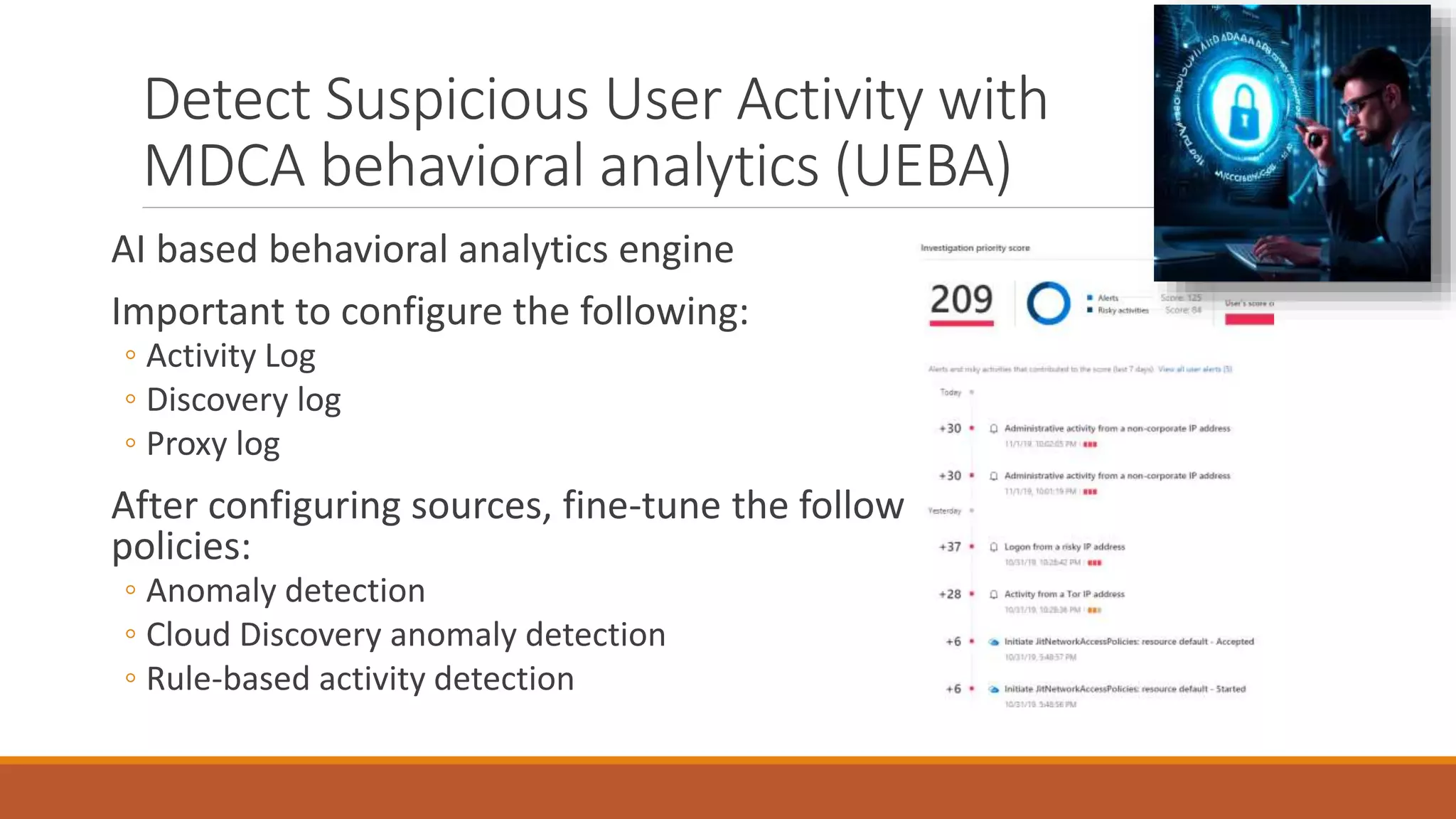
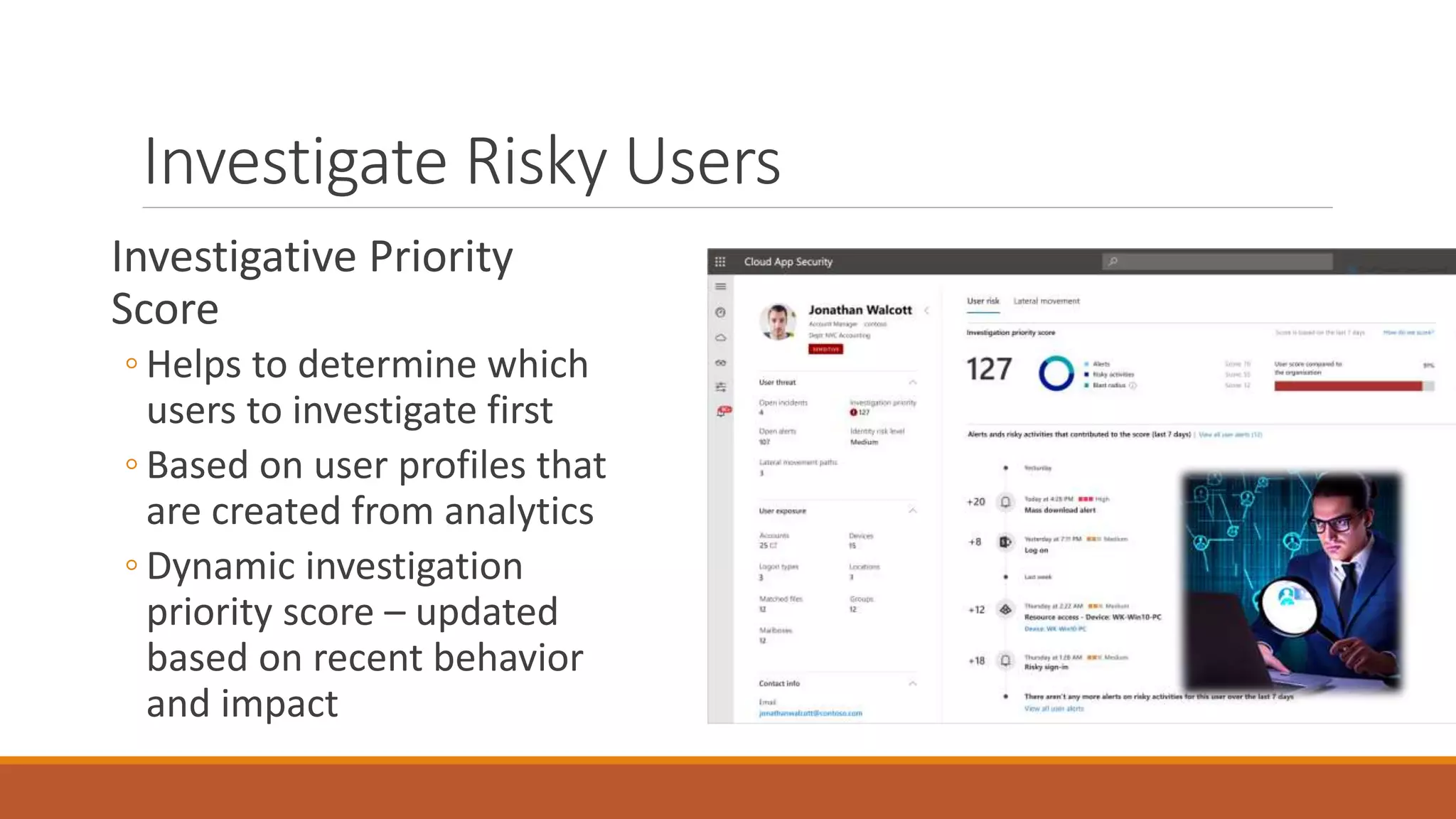
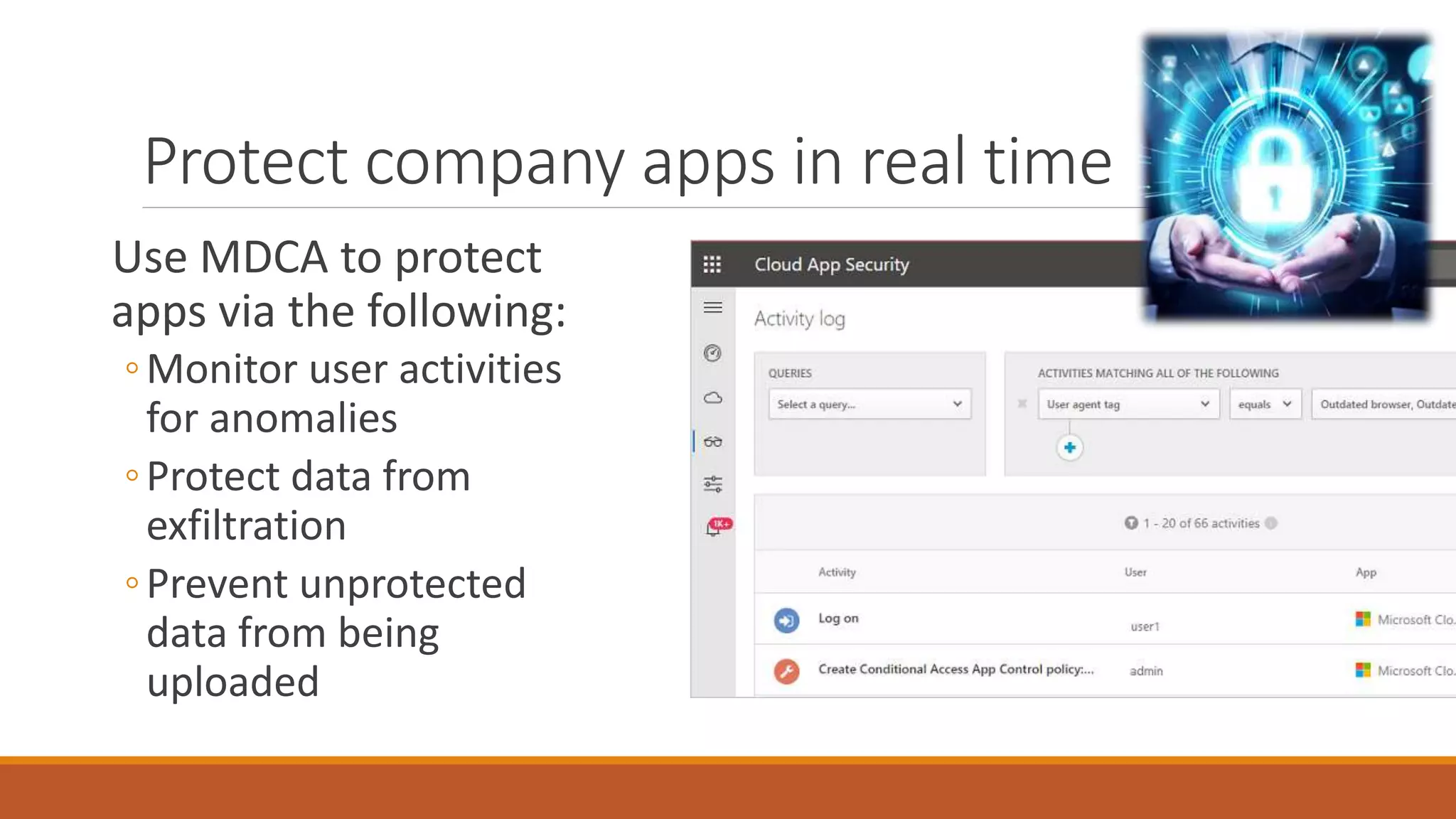
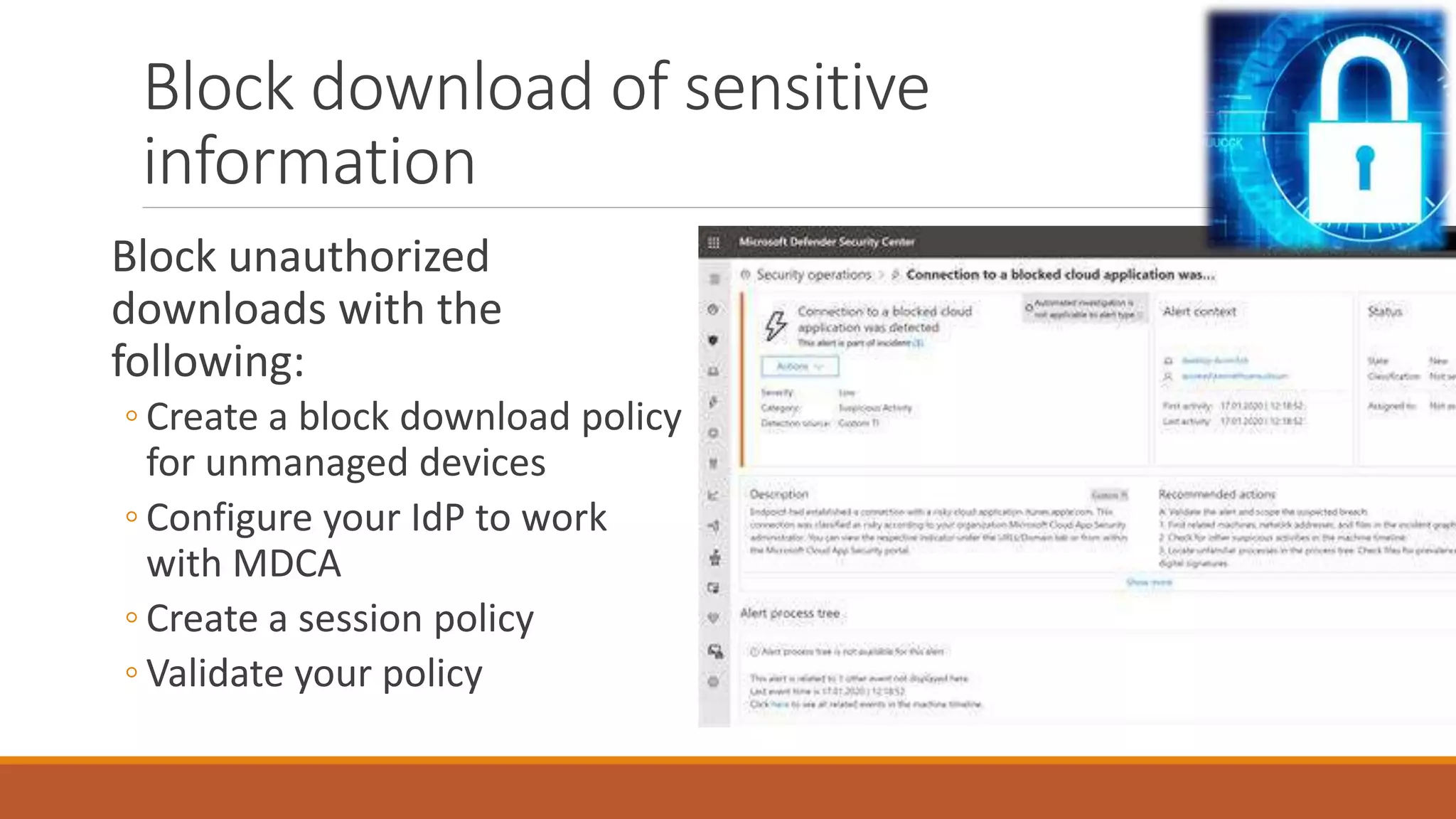
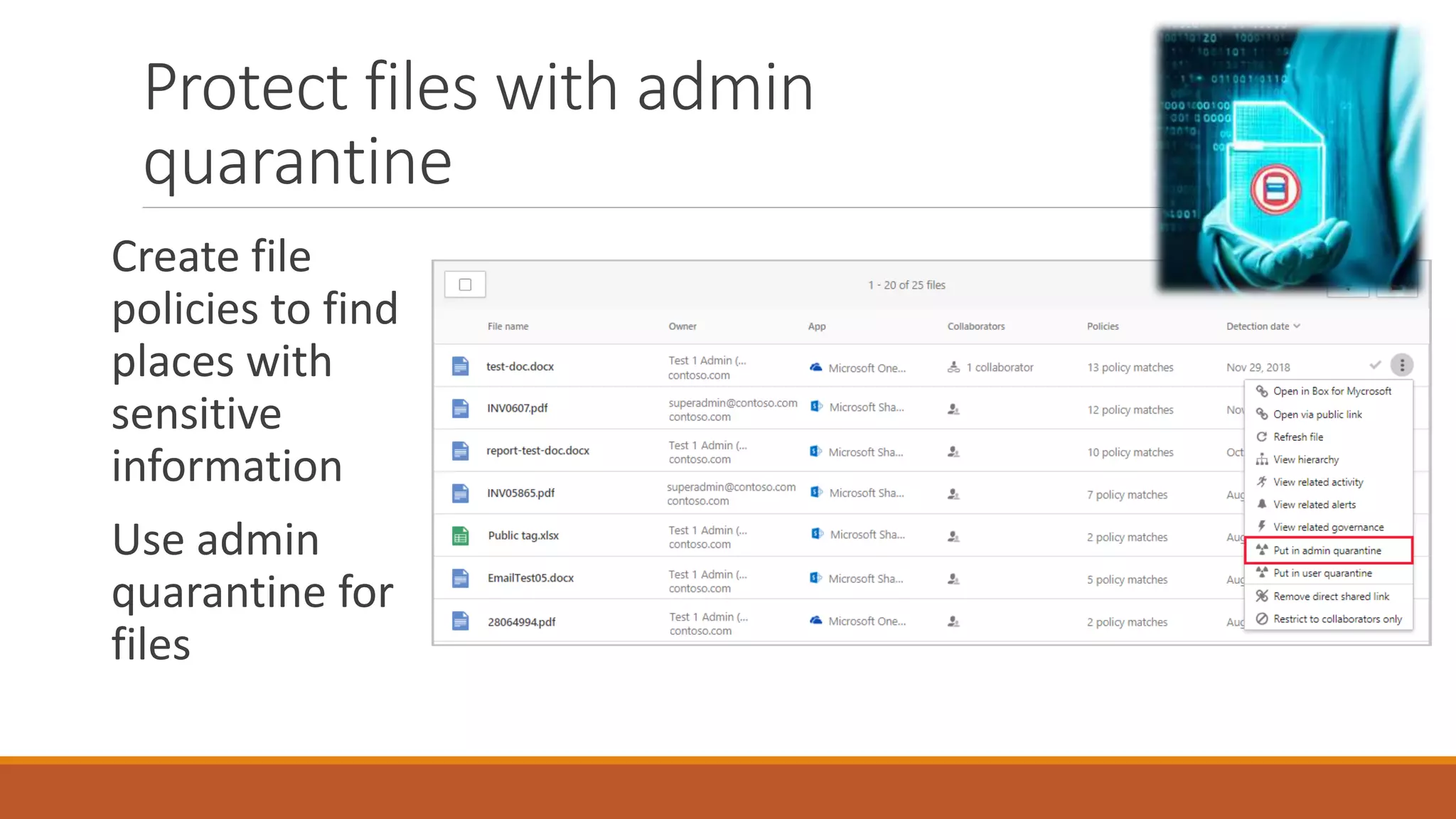
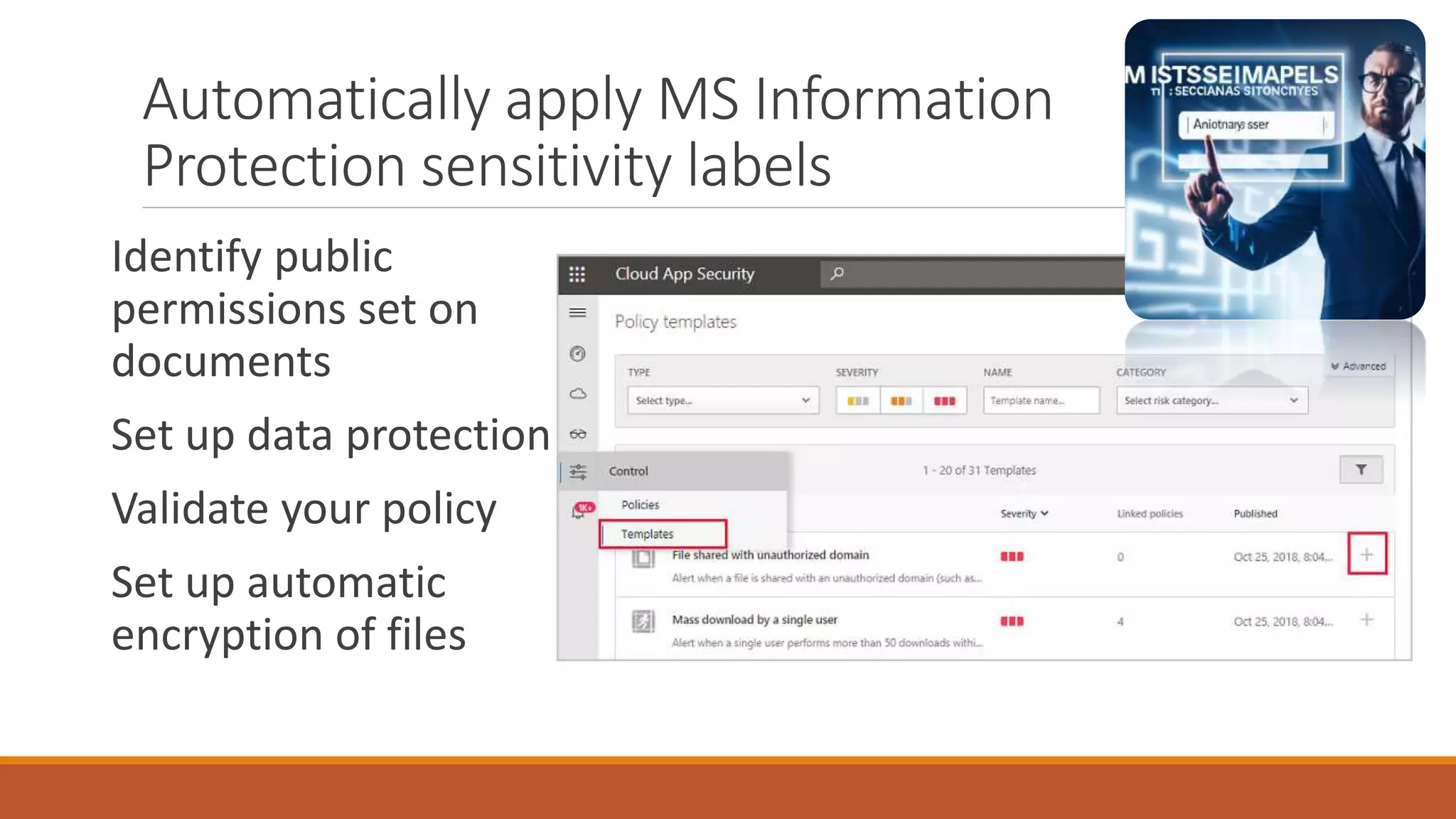
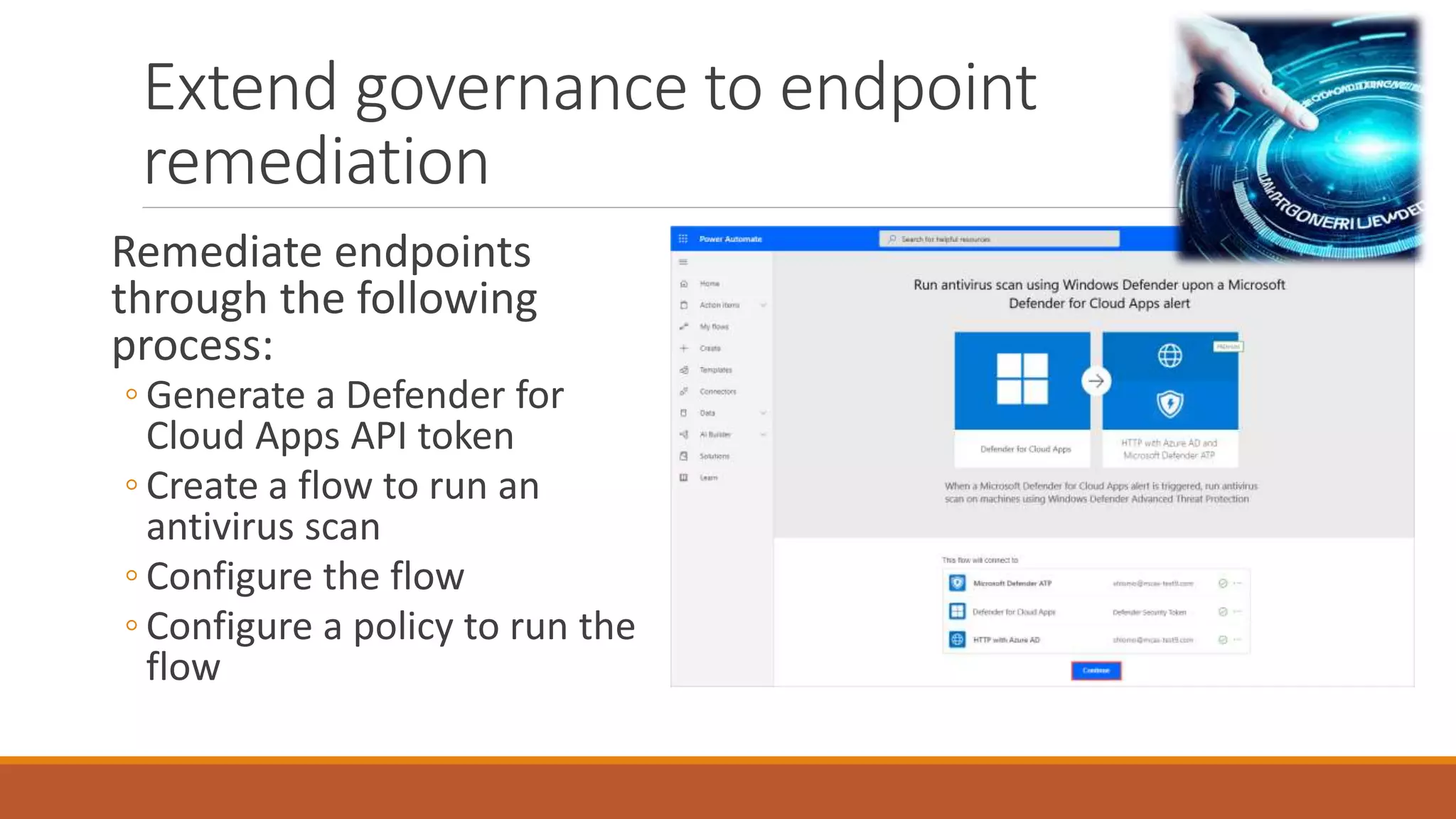
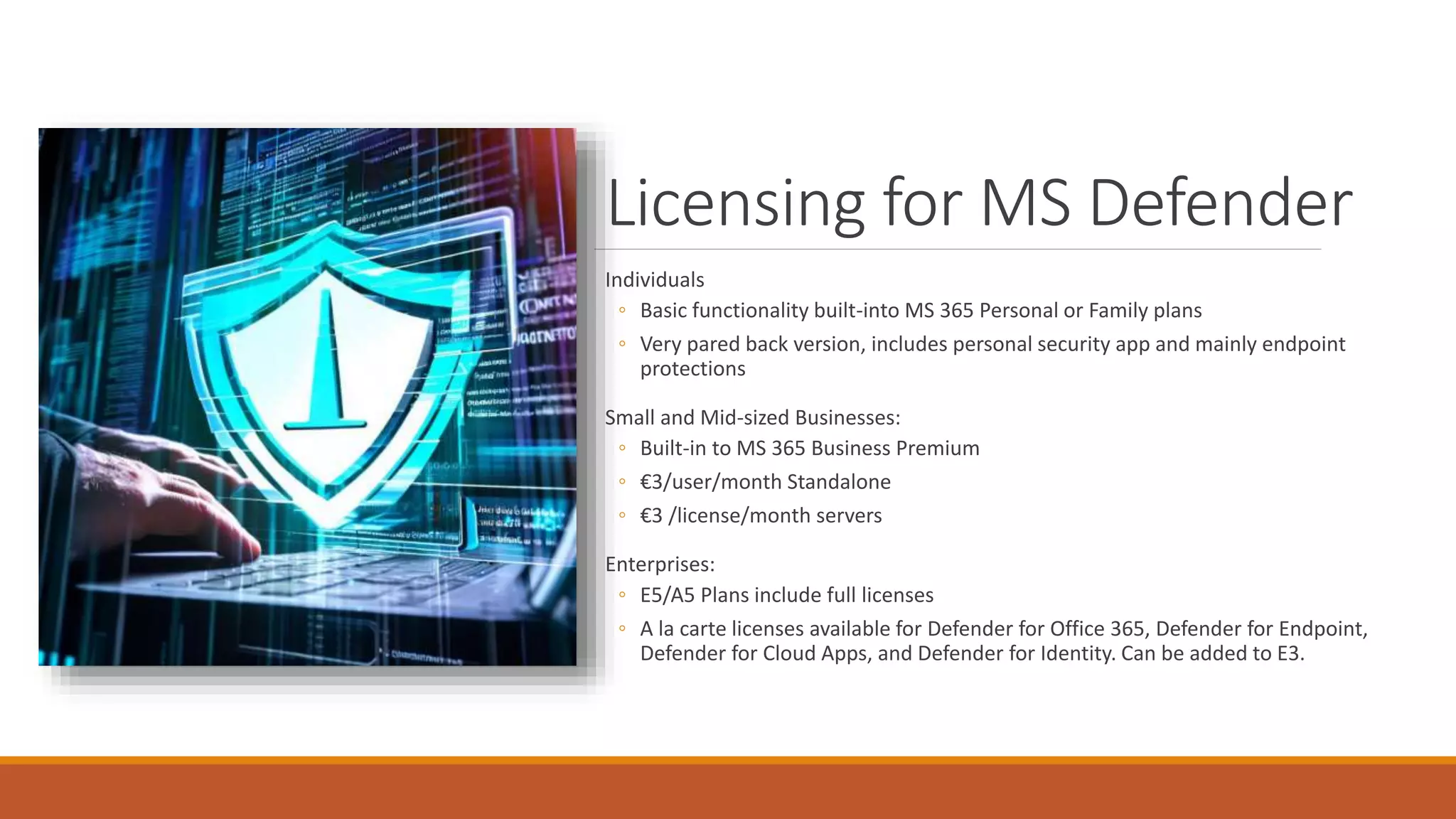
Michael Noel's presentation on combating cyberthreats with Microsoft 365 Defender outlines a range of Microsoft security products, including Microsoft Sentinel, Intune, and various Defender tools designed for endpoint and cloud security. The presentation emphasizes the integration of AI and analytics to enhance threat detection and response, as well as highlighting features like data loss prevention and compliance management. Additionally, it discusses licensing options for individuals and enterprises to implement these security solutions effectively.