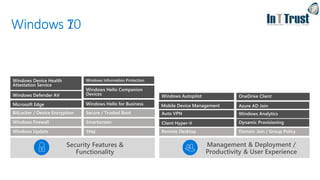
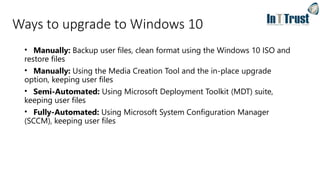
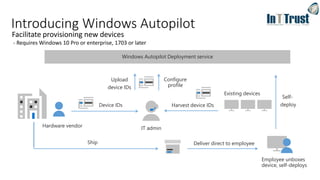
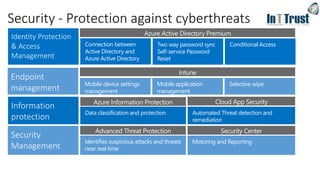
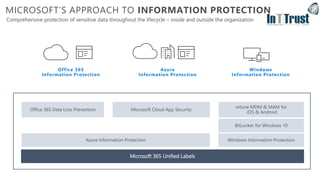
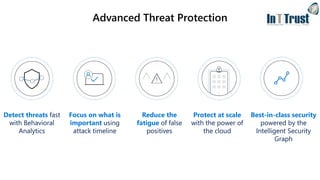
The document discusses the transition from Windows 7 to Windows 10, detailing various upgrade methods and security features to protect against cyber threats. It covers management options including Windows Autopilot, identity access management through Azure Active Directory, and information protection strategies involving Azure Information Protection. Additionally, it highlights Microsoft's comprehensive security measures across its services, including advanced threat protection and endpoint management.


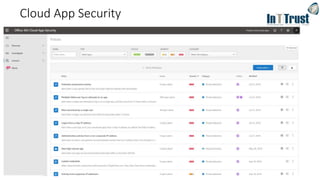
![Paths to Windows 10 Pro
Windows XP,
Vista, etc.
Windows Ent./LTSB
• Upgrade (keep files, apps, and settings)
• Clean-install (install Windows only [keep nothing])
May require manual re-input of OEM license key to activate
In-place upgrade options
• Keep files, apps, and settings
• Keep files only (discard apps and settings)
• Keep nothing (discard files, apps, and settings)
Windows 10
Home
In-place upgrade
OR
Windows 7 Home
Windows 8 Home
Windows 8.1 Home
Windows 7 Pro
Windows 7 Ultimate
Windows 8 Pro
Windows 8.1 Pro
Windows 10 Pro
clean install](https://image.slidesharecdn.com/inttrustm365emsv3-191120105049/85/In-t-trustm365ems_v3-4-320.jpg)





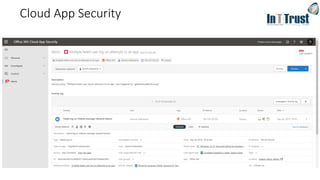

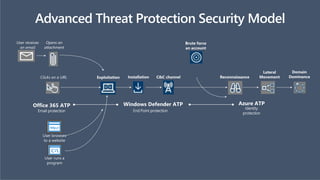


![Features
Office 365
BP
Microsoft 365
Business
Microsoft 365
E3
Microsoft 365
E5
Maximum number of users 300 300 unlimited unlimited
Office Apps Install Office on up to 5 PCs/Macs + 5 tablets + 5 smartphones per user (Word, Excel, PowerPoint, OneNote,
Access), Office Online
Business Business ProPlus ProPlus
Email & Calendar Outlook, Exchange Online 50GB 50GB unlimited unlimited
Hub for Teamwork Chat-based workspace, online meetings, and more in Microsoft Teams
File Storage OneDrive for Business 1 TB/user 1 TB/user unlimited unlimited
Social, Video, Sites Yammer, SharePoint Online, Planner
Stream
Business Apps Scheduling Apps – Bookings1, StaffHub
Business Apps – Outlook Customer Manager, MileIQ1
Threat Protection Microsoft Advanced Threat Analytics, Device Guard, Credential Guard, App Locker, Enterprise Data Protection,
Office 365 Advanced Threat Protection
Windows Defender Advanced Threat Protection
Office 365 Threat Intelligence
Identity Management Self-service password reset for hybrid Azure Active Directory accounts, Azure MFA, Conditional Access
Azure AD: Cloud App Discovery, AAD Connect Health, SSO for more than 10 Apps
Azure Active Directory Plan 2
Device & App
Management
Microsoft Intune, Windows AutoPilot
Shared Computer Activation
Microsoft Desktop Optimization Package, VDA
Information
Protection
Office 365 Data Loss Prevention, Azure Information Protection Plan 1
Azure Information Protection Plan 2, Microsoft Cloud App Security, O365 Cloud App Security
On-Prem CAL Rights ECAL Suite (Exchange, SharePoint, Skype, Windows, SCCM, Win. Rights Management)
Compliance Unlimited email archiving2
Advanced eDiscovery, Customer Lockbox, Advanced Data Governance
Analytics Power BI Pro, MyAnalytics
Voice PSTN Conferencing, Cloud PBX
ComparisonacrossBusinessPremiumandMicrosoft365SKU’s
[1] Available in US, UK, Canada | [2] Unlimited archiving when auto-expansion is turned on](https://image.slidesharecdn.com/inttrustm365emsv3-191120105049/85/In-t-trustm365ems_v3-27-320.jpg)