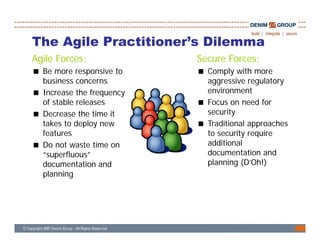
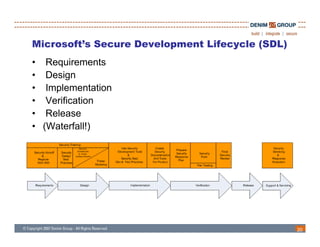
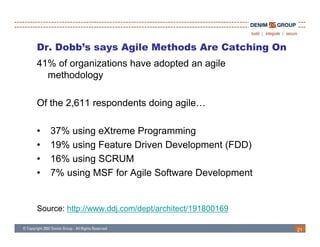
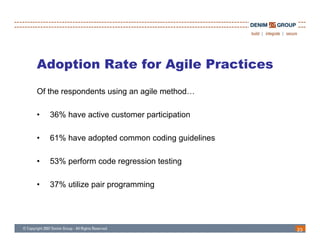
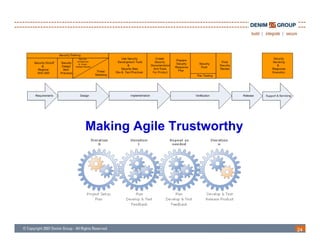
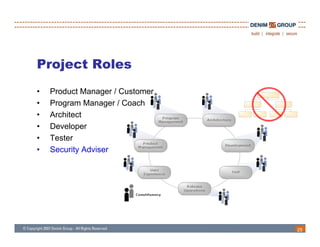
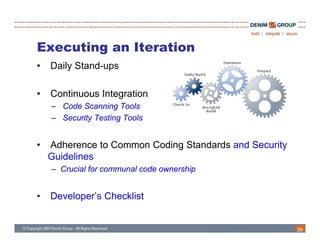
The document discusses the challenges and methodologies of integrating agile development with software security, highlighting the evolution of software development from traditional models to agile practices. It emphasizes the need for a secure development process that incorporates security throughout the software lifecycle, balancing the demands for speed and flexibility with the necessity for robust security measures. Various practices and principles are proposed to ensure that agile teams can maintain security without sacrificing responsiveness or efficiency.