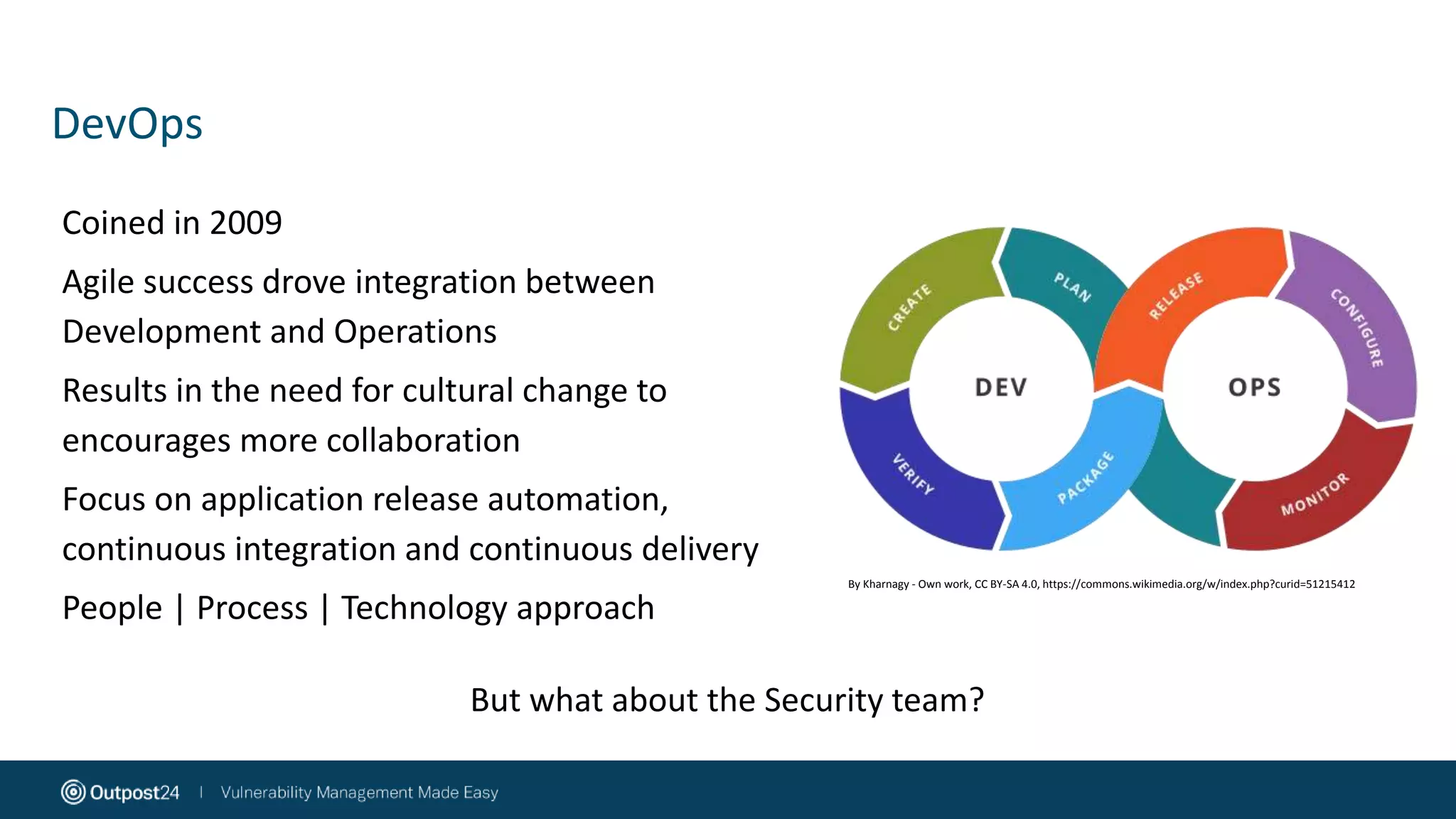
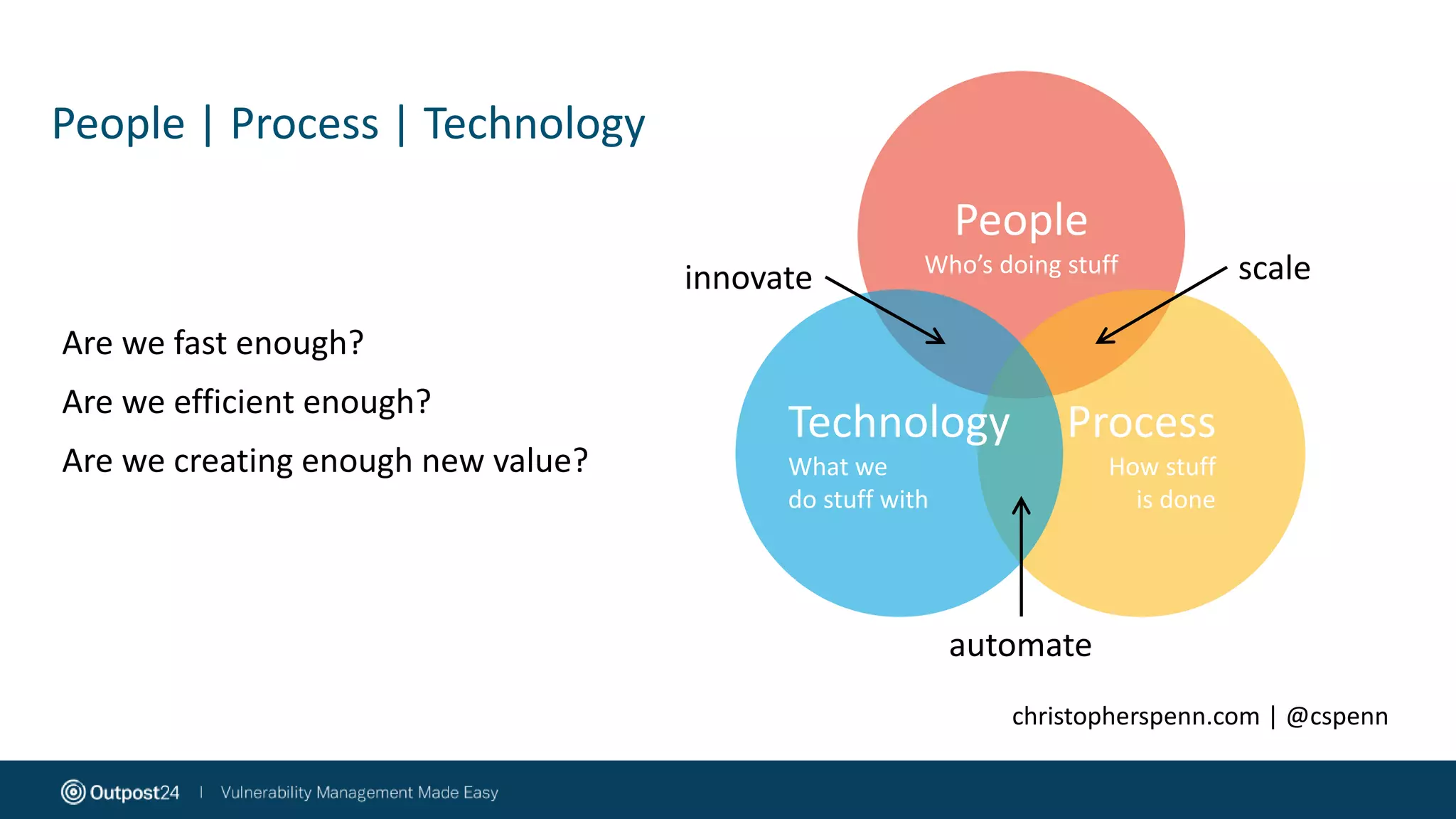
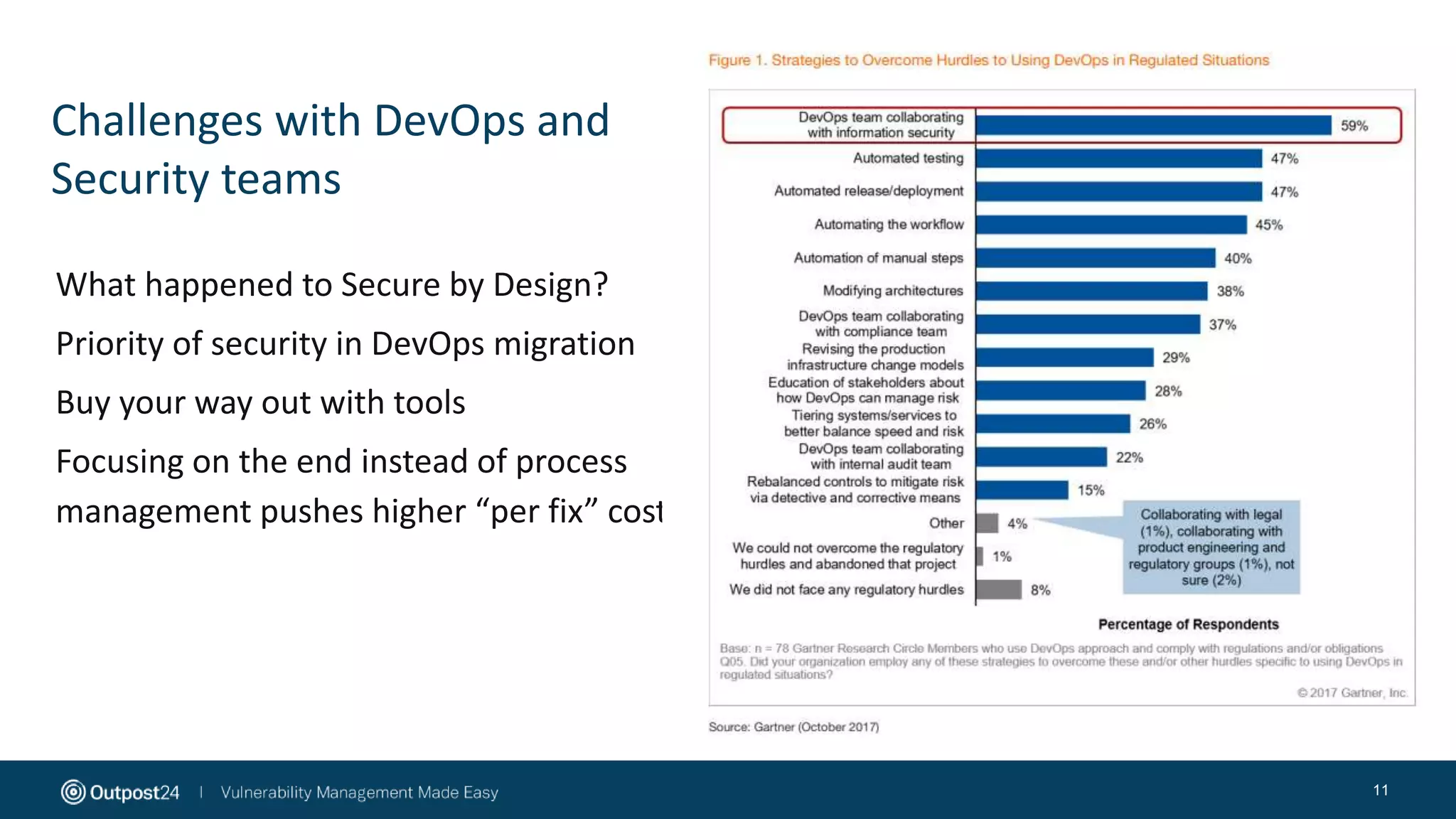
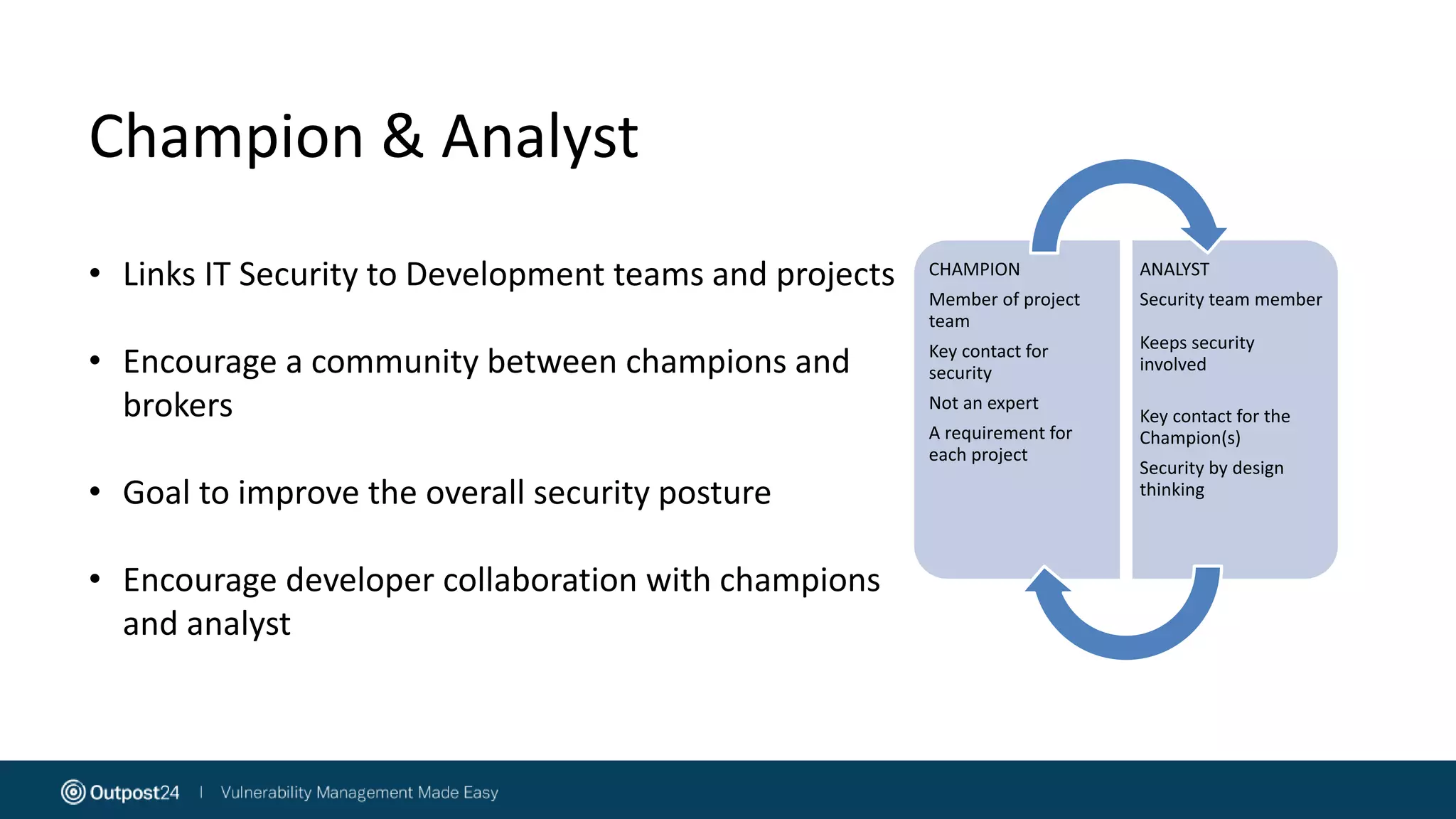
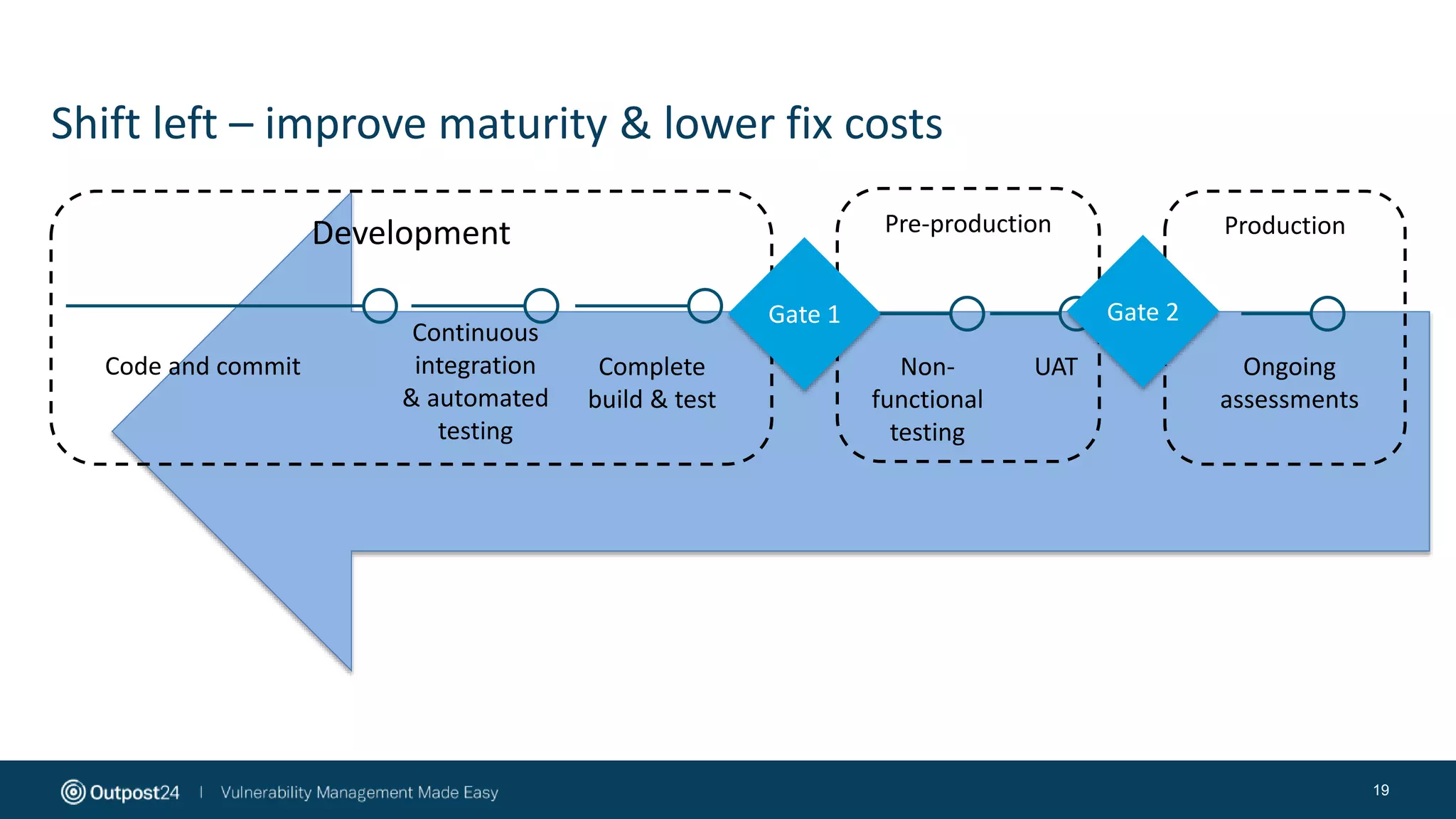
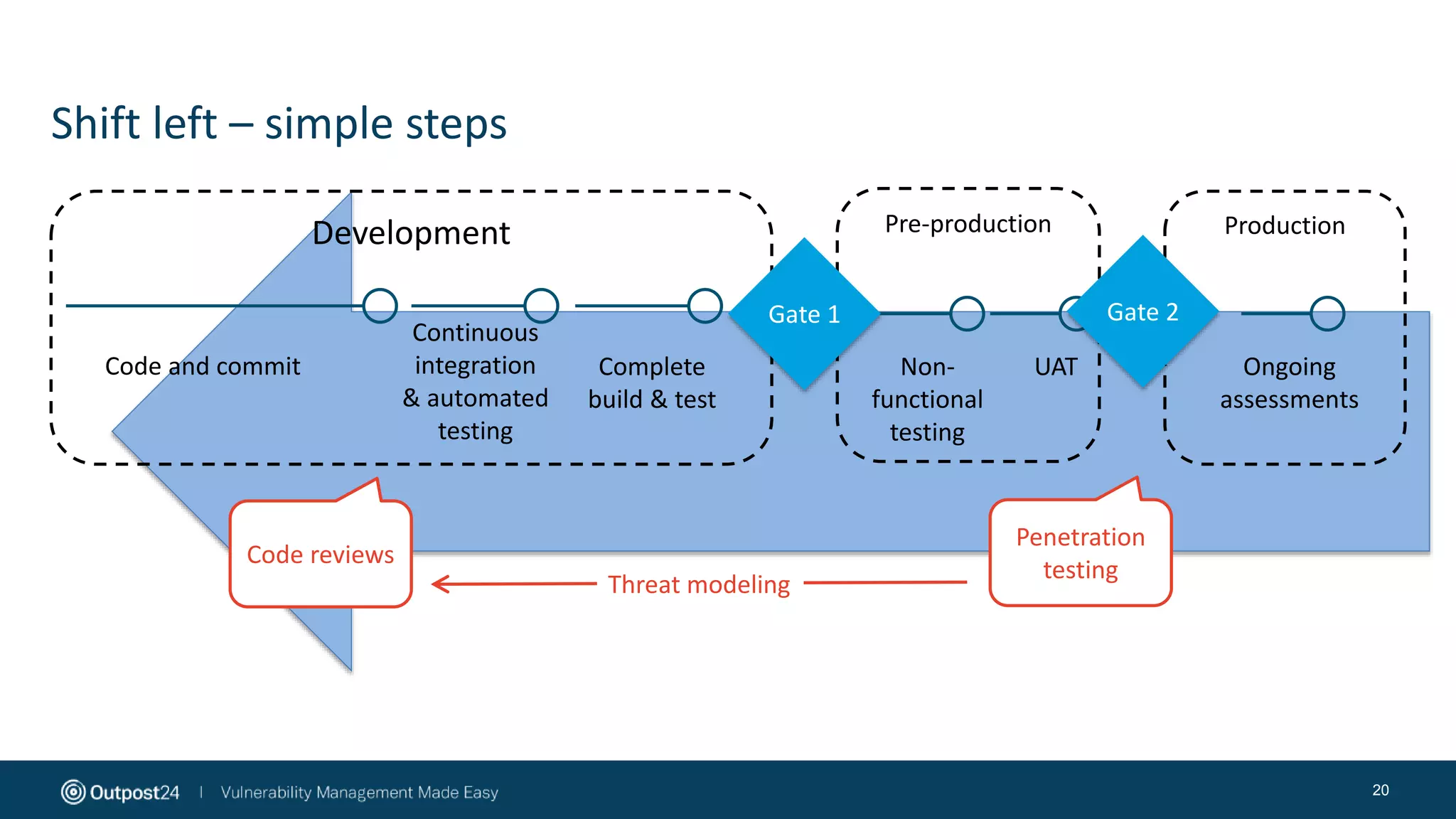
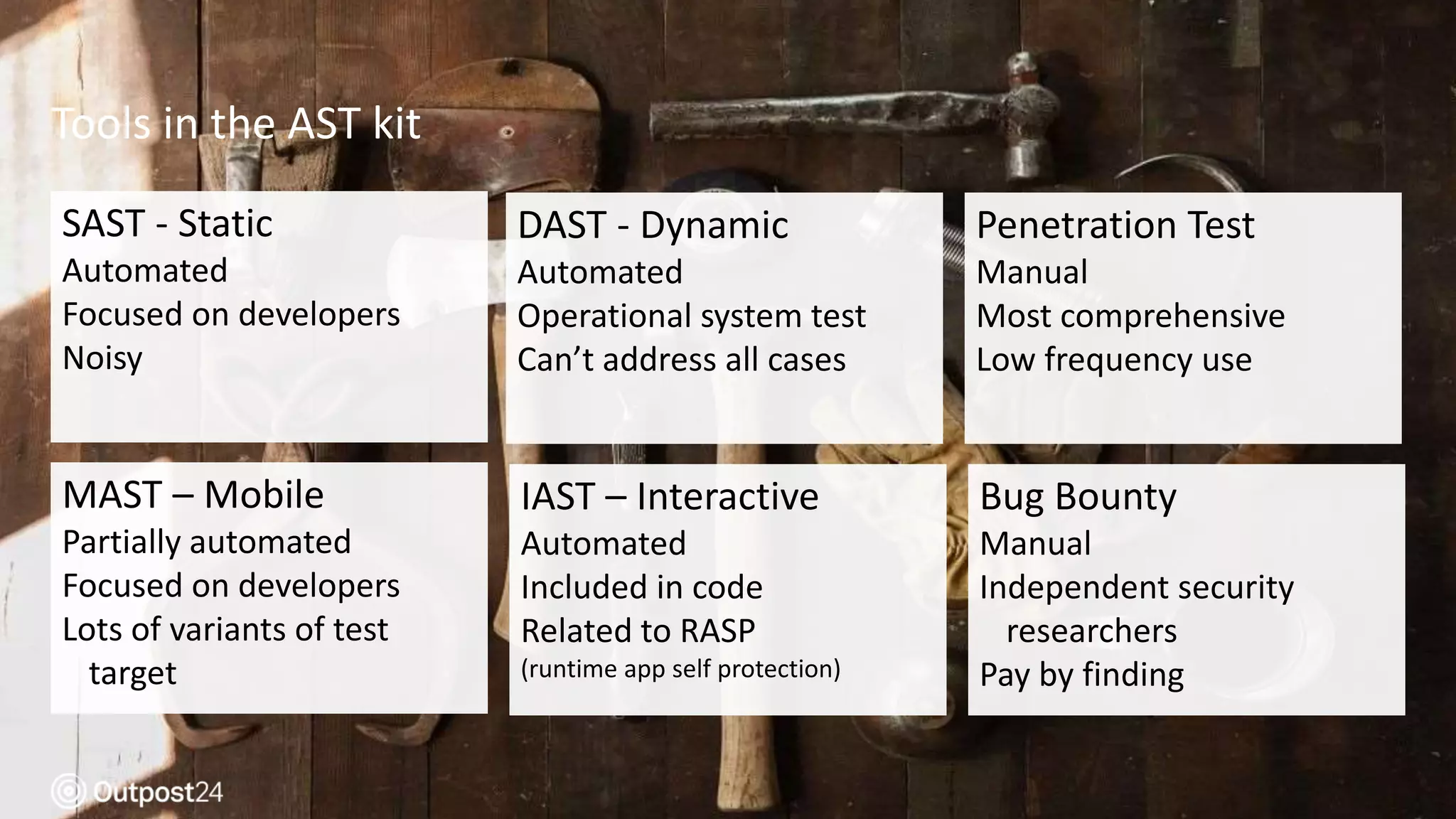
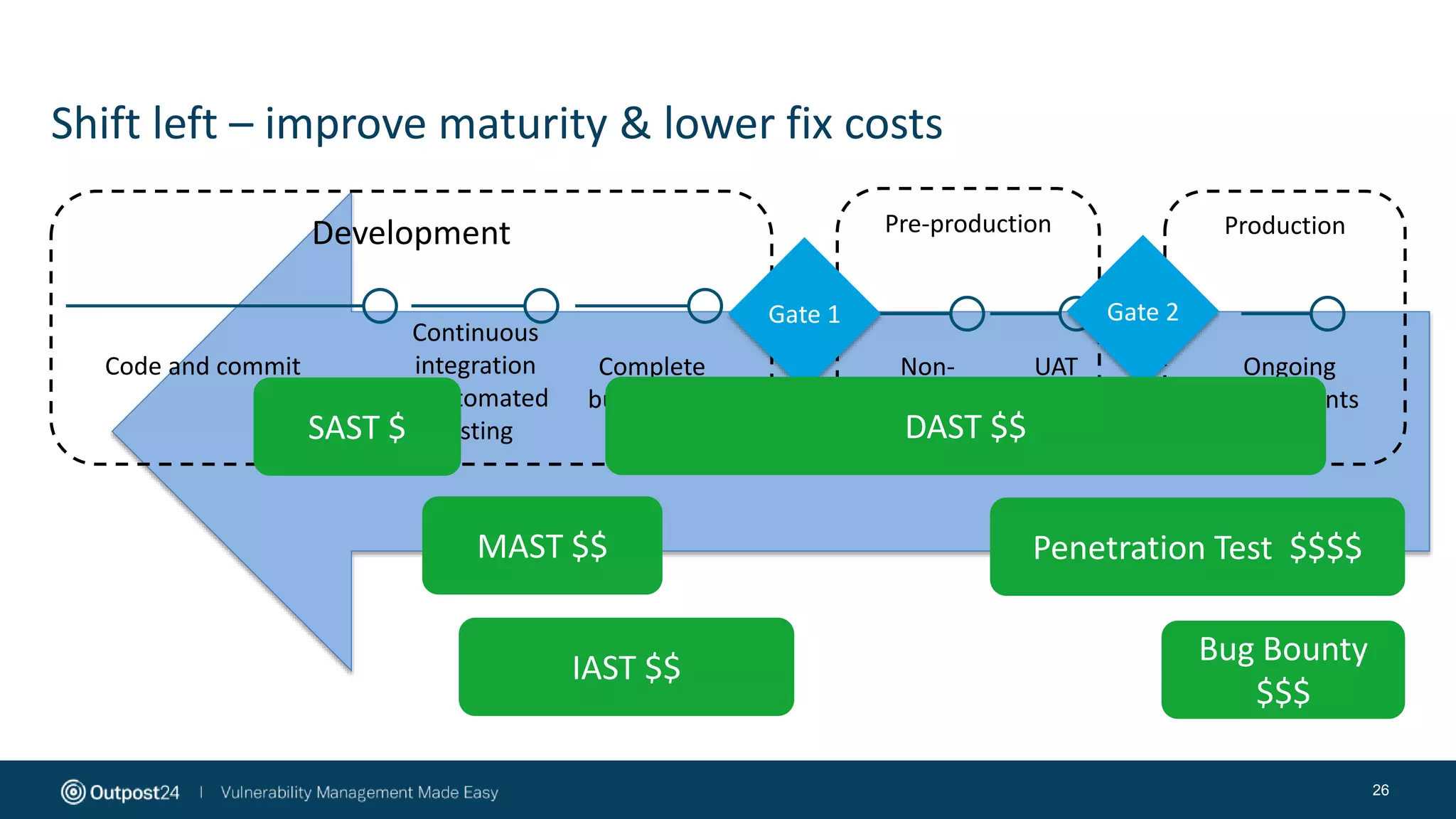
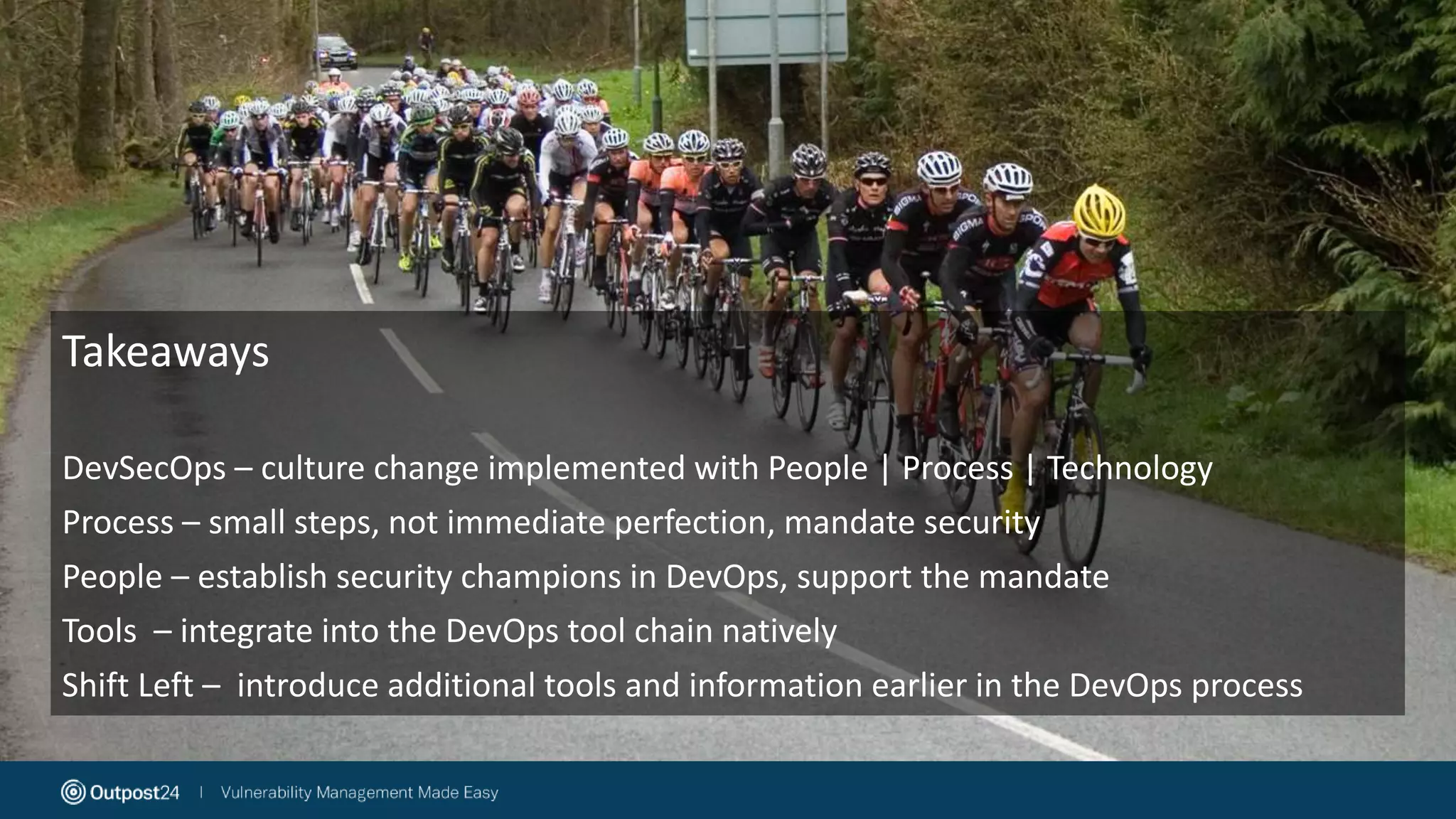
The document discusses the evolution of application security within the DevOps framework, emphasizing the need for integrating security into development processes through the concept of DevSecOps. It highlights the importance of collaboration among development, operations, and security teams, while advocating for the establishment of security champions to bridge gaps in security awareness. The key takeaways stress a cultural shift towards incorporating security earlier in the development cycle, focusing on people, processes, and the right tools to improve overall security posture.