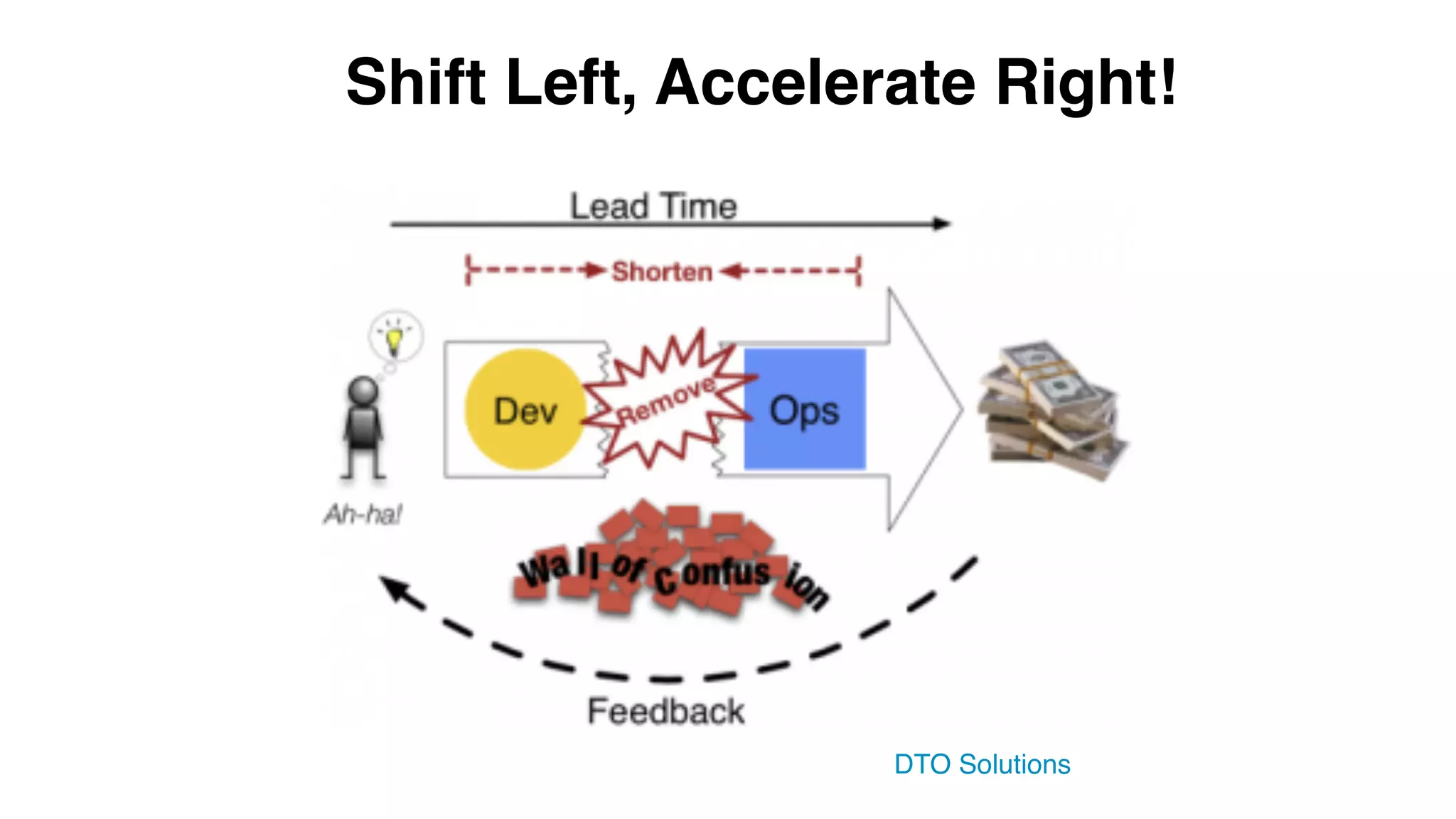
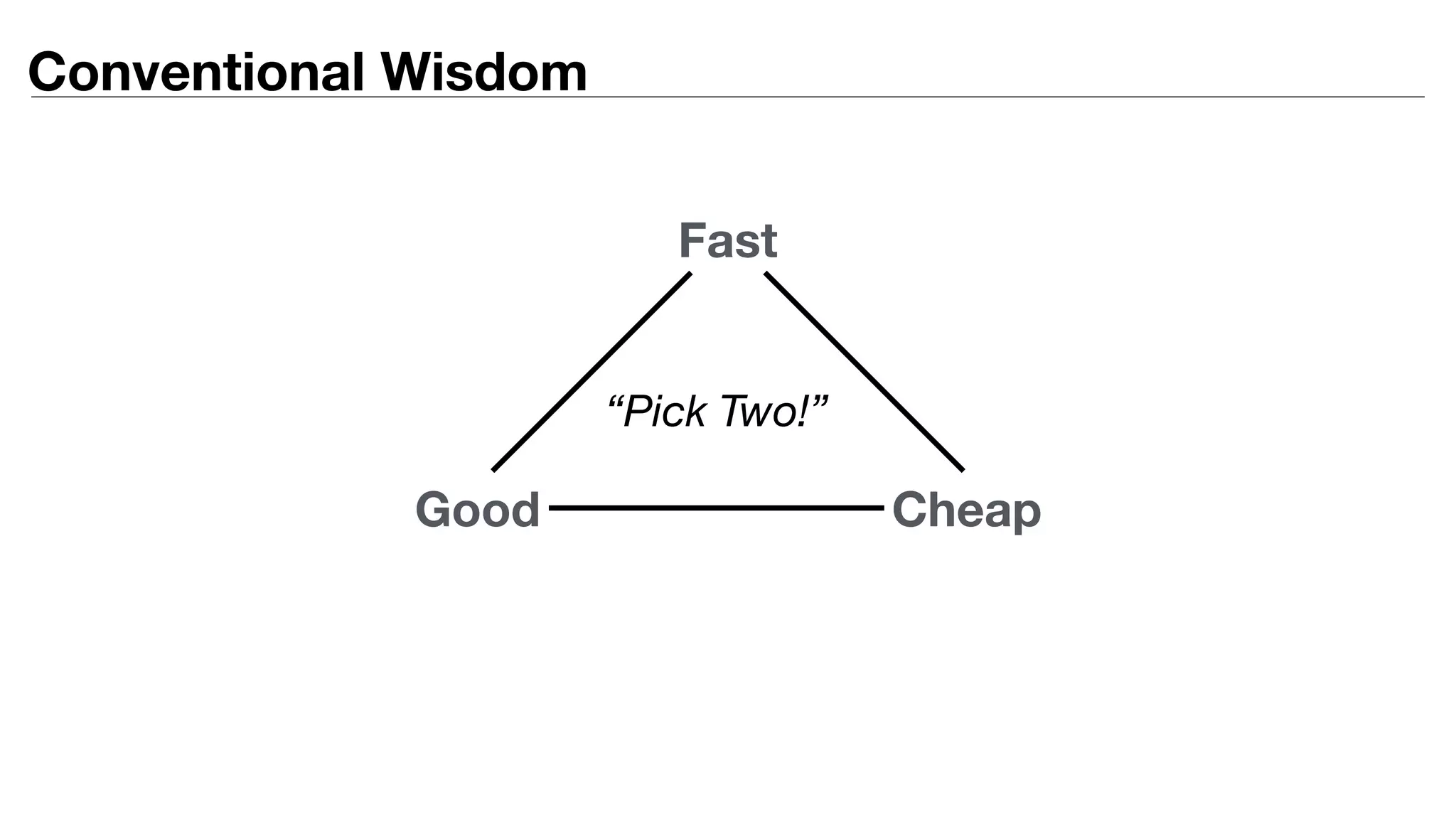
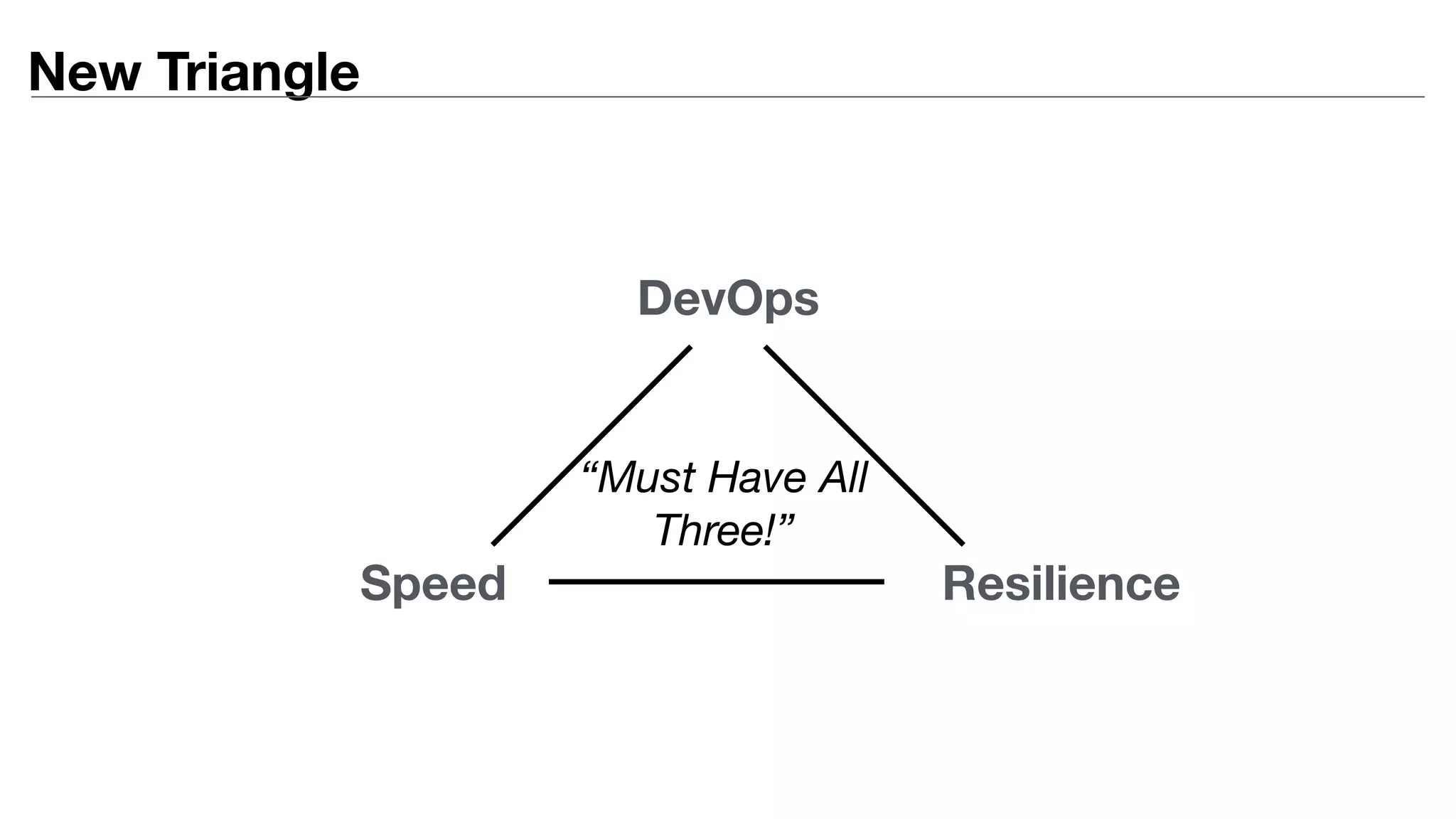
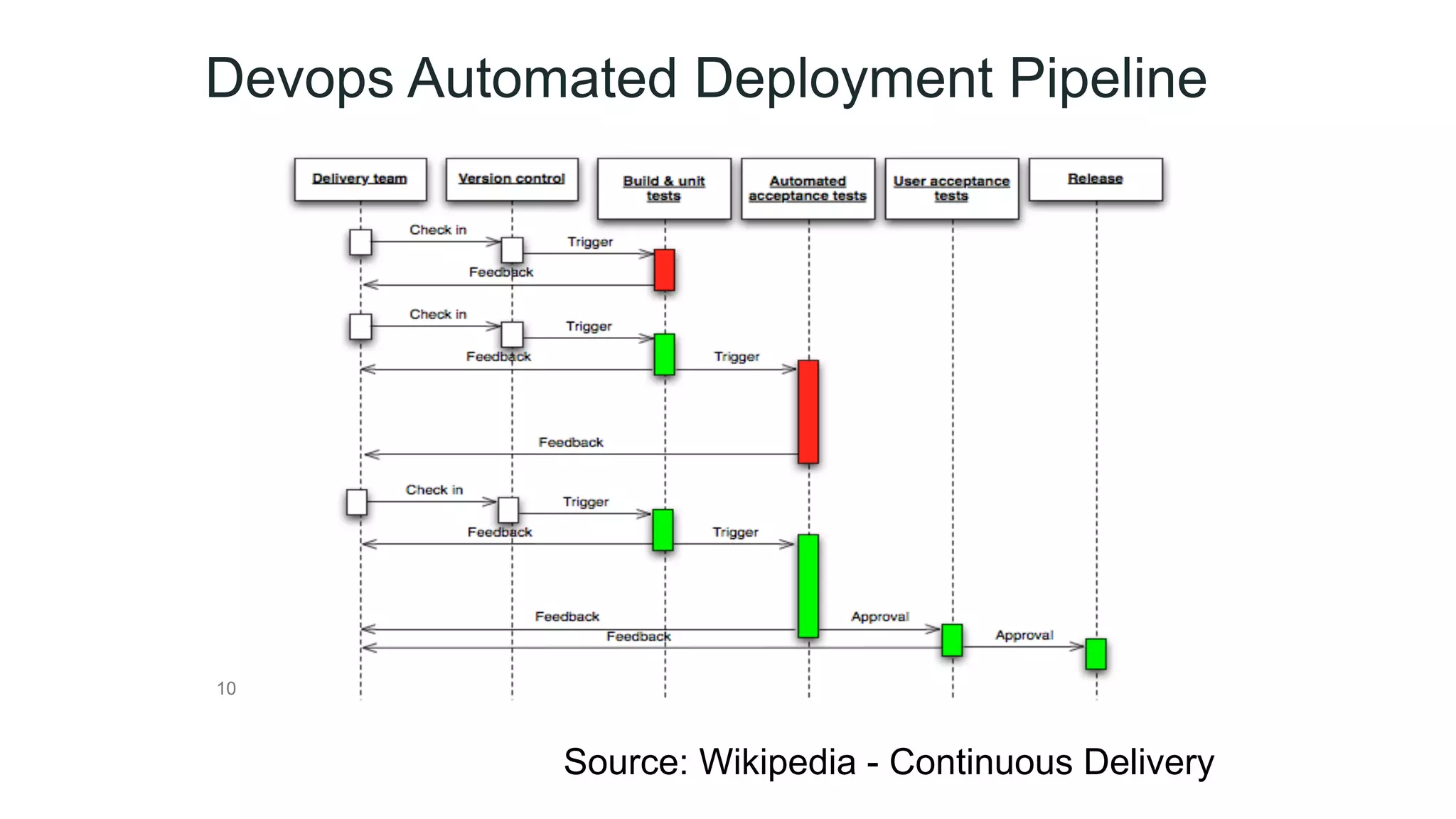
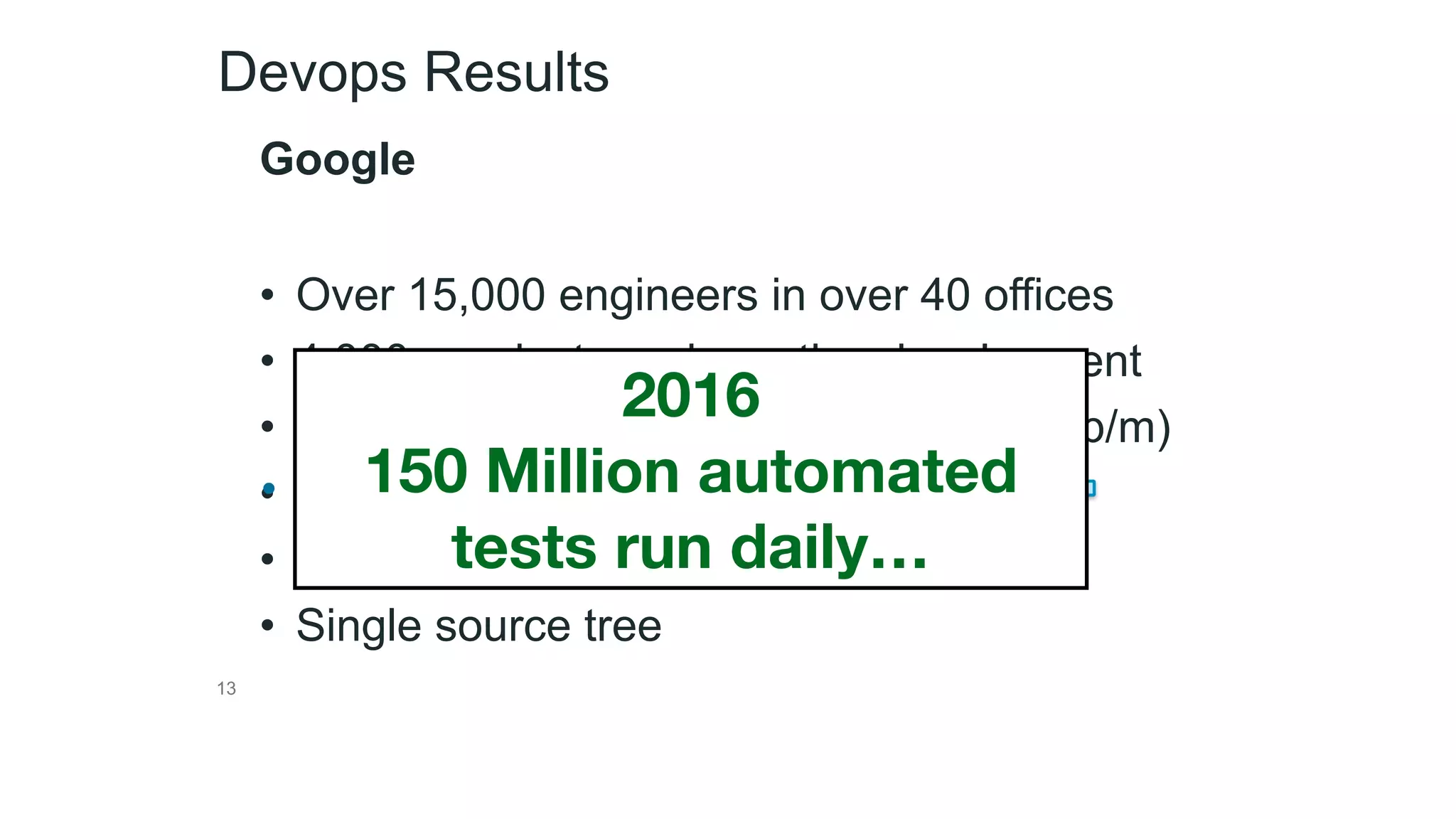
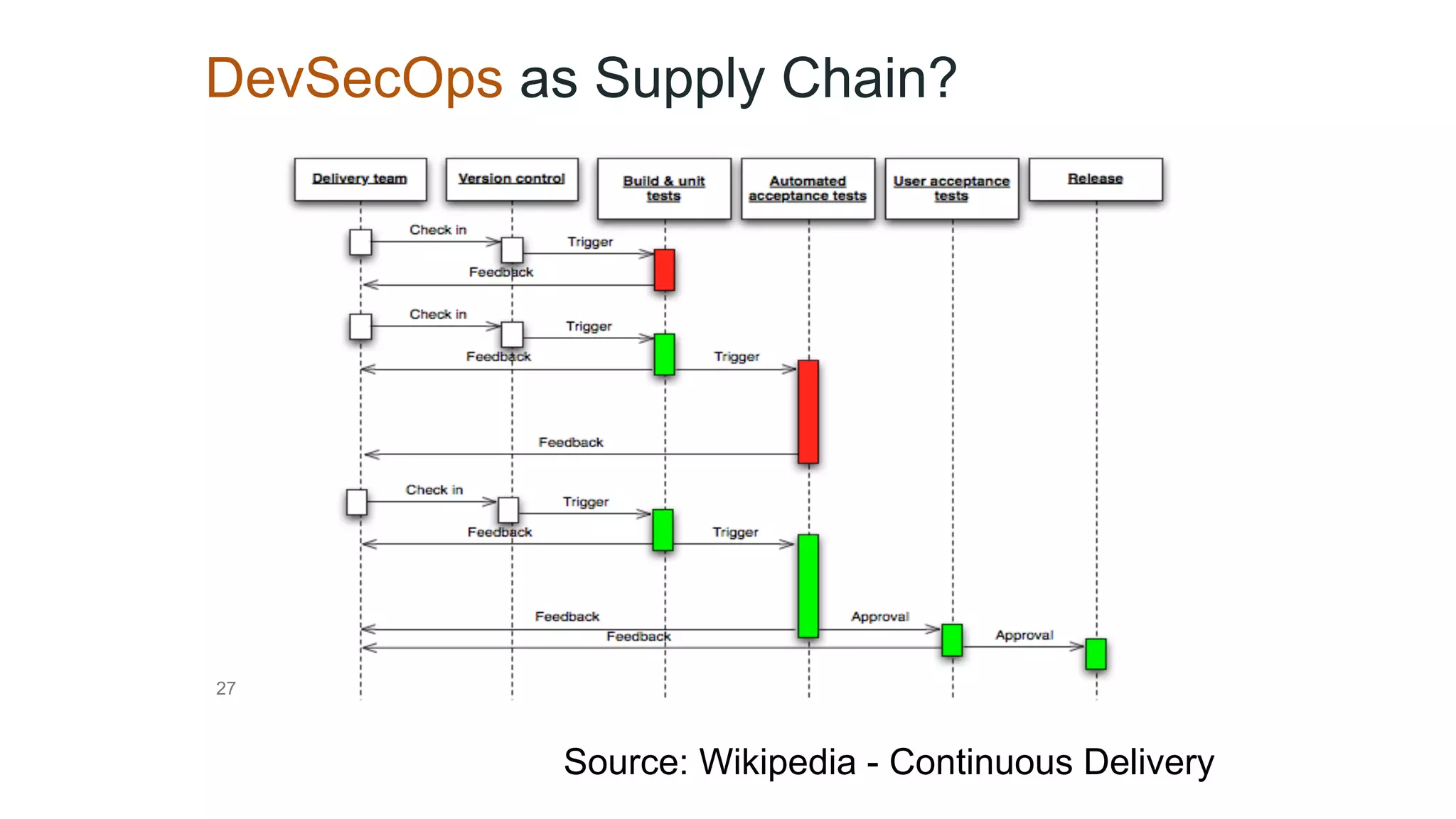
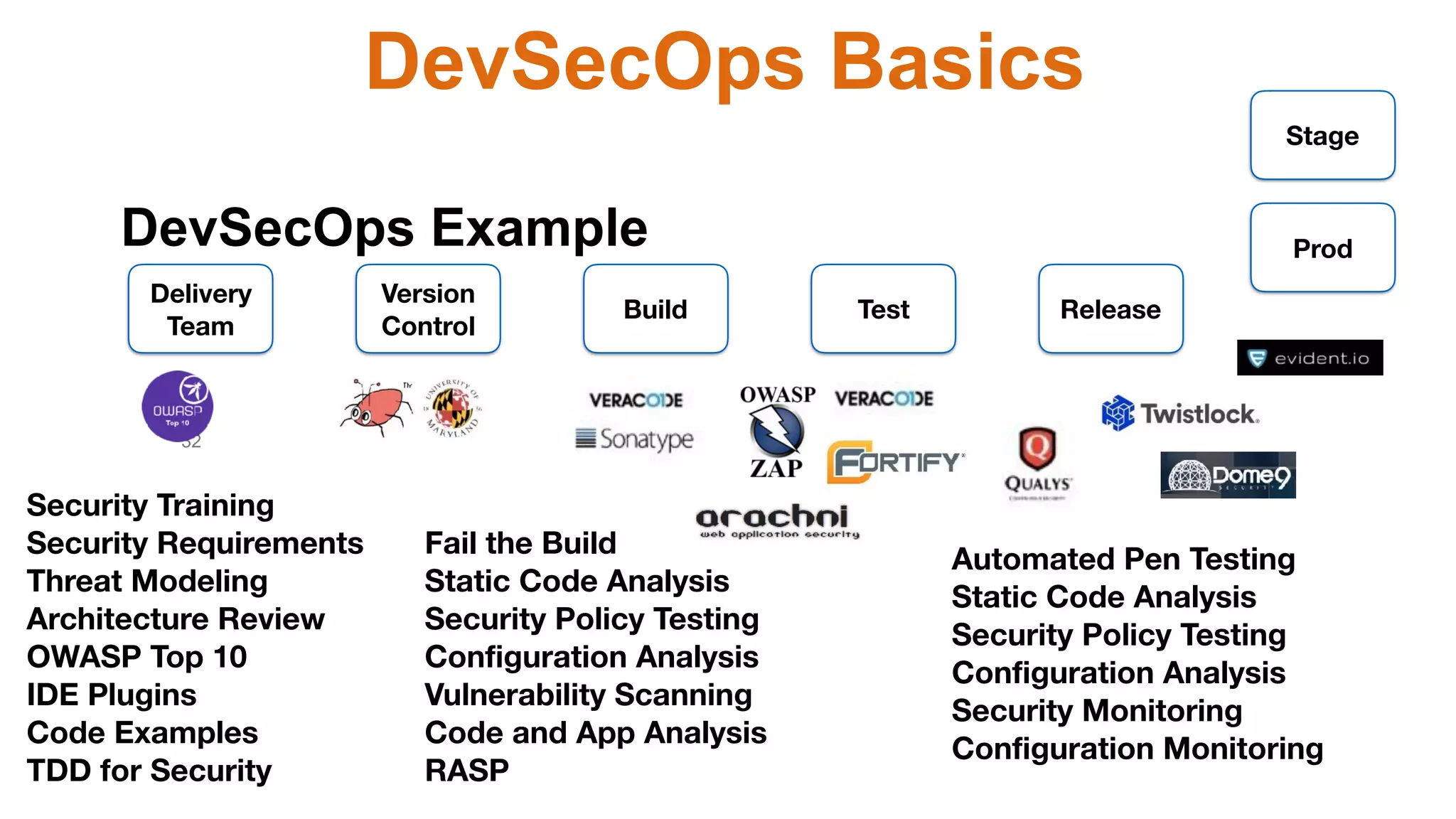
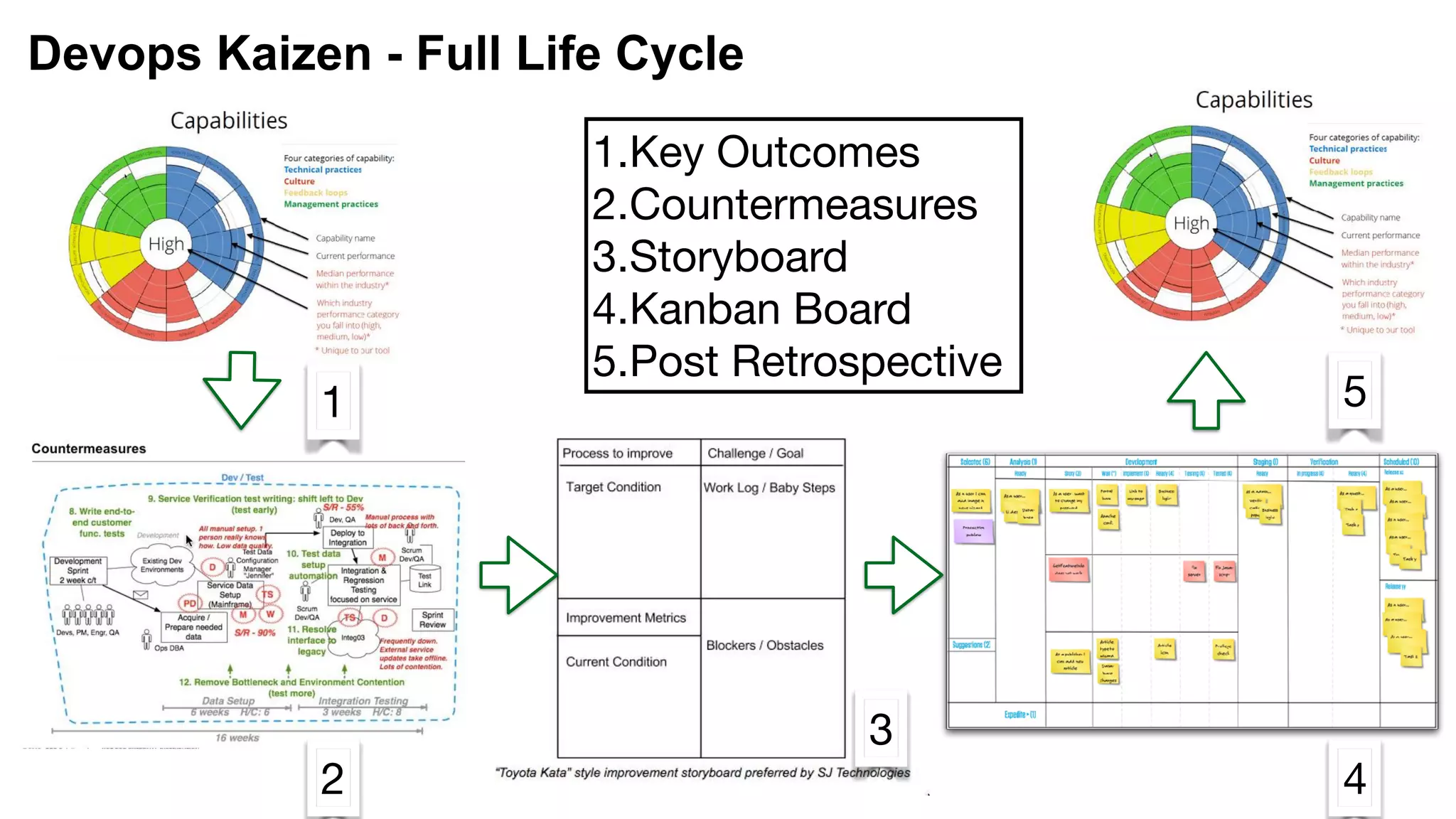
This document provides an introduction to DevSecOps practices. It discusses how DevOps aims to accelerate software delivery through practices like continuous delivery, automation, and removing silos. It notes that security has become the new bottleneck in software delivery. DevSecOps aims to integrate security practices and tools into the software development pipeline to shift security left. This allows security to be addressed continuously throughout development and deployment rather than as a separate phase. The document outlines some DevSecOps basics like security training, threat modeling, and integrating static code analysis and vulnerability scanning into the CI/CD pipeline.