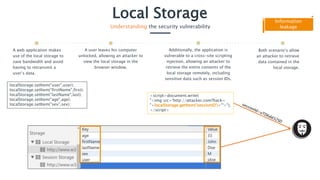
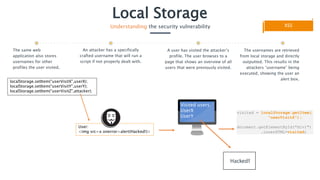
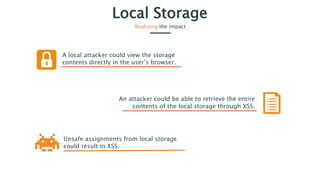
Local storage in web applications allows client-side storage of key/value pairs, but it poses security risks such as exposure to cross-site scripting (XSS) attacks, potentially revealing sensitive data like session identifiers. To prevent these vulnerabilities, sensitive information should not be stored in local storage, and developers should implement filters or sanitization for any data retrieved from it. Users should also be cautious about the contents of local storage, as an unlocked computer can expose data to malicious actors.