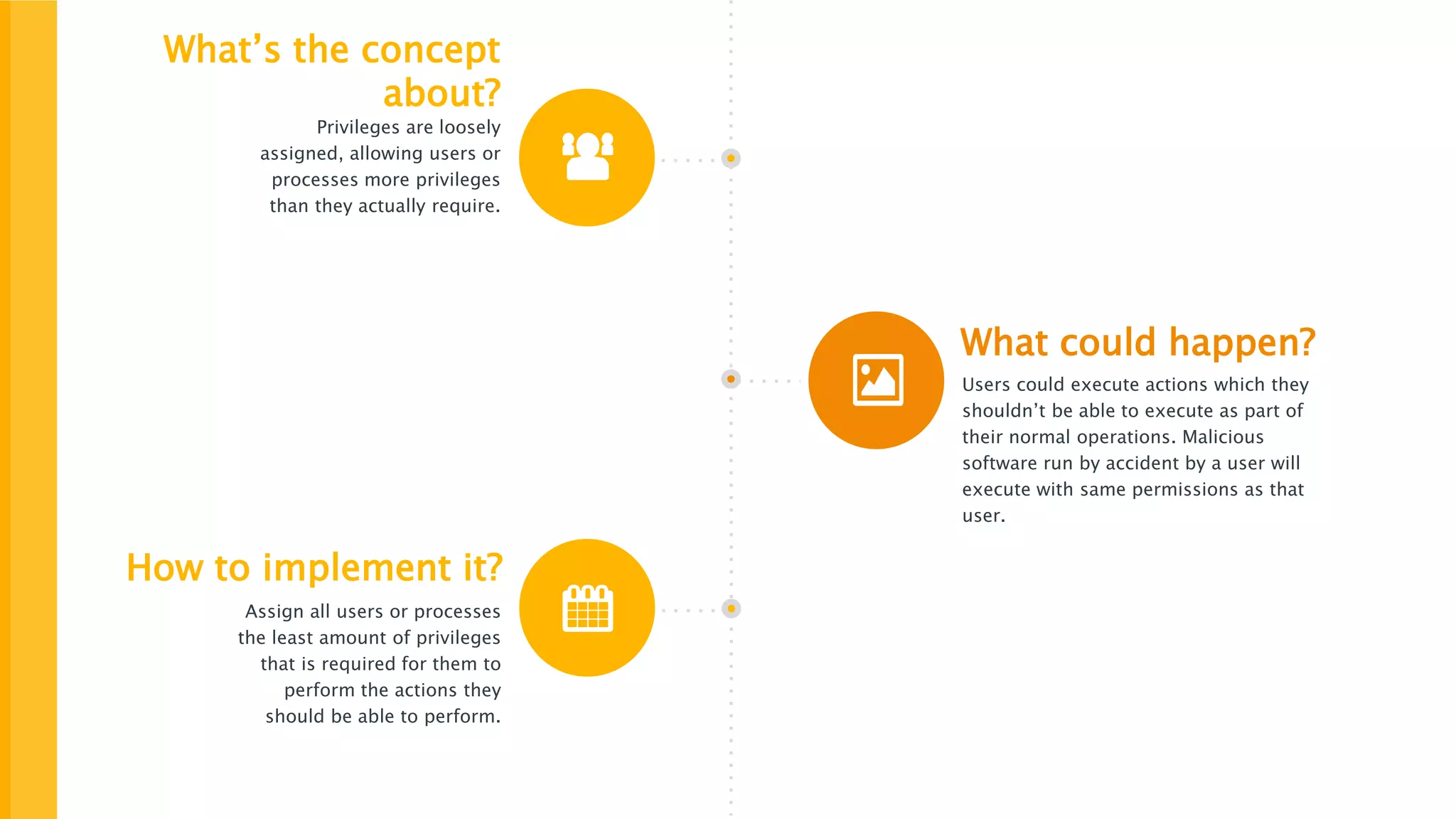
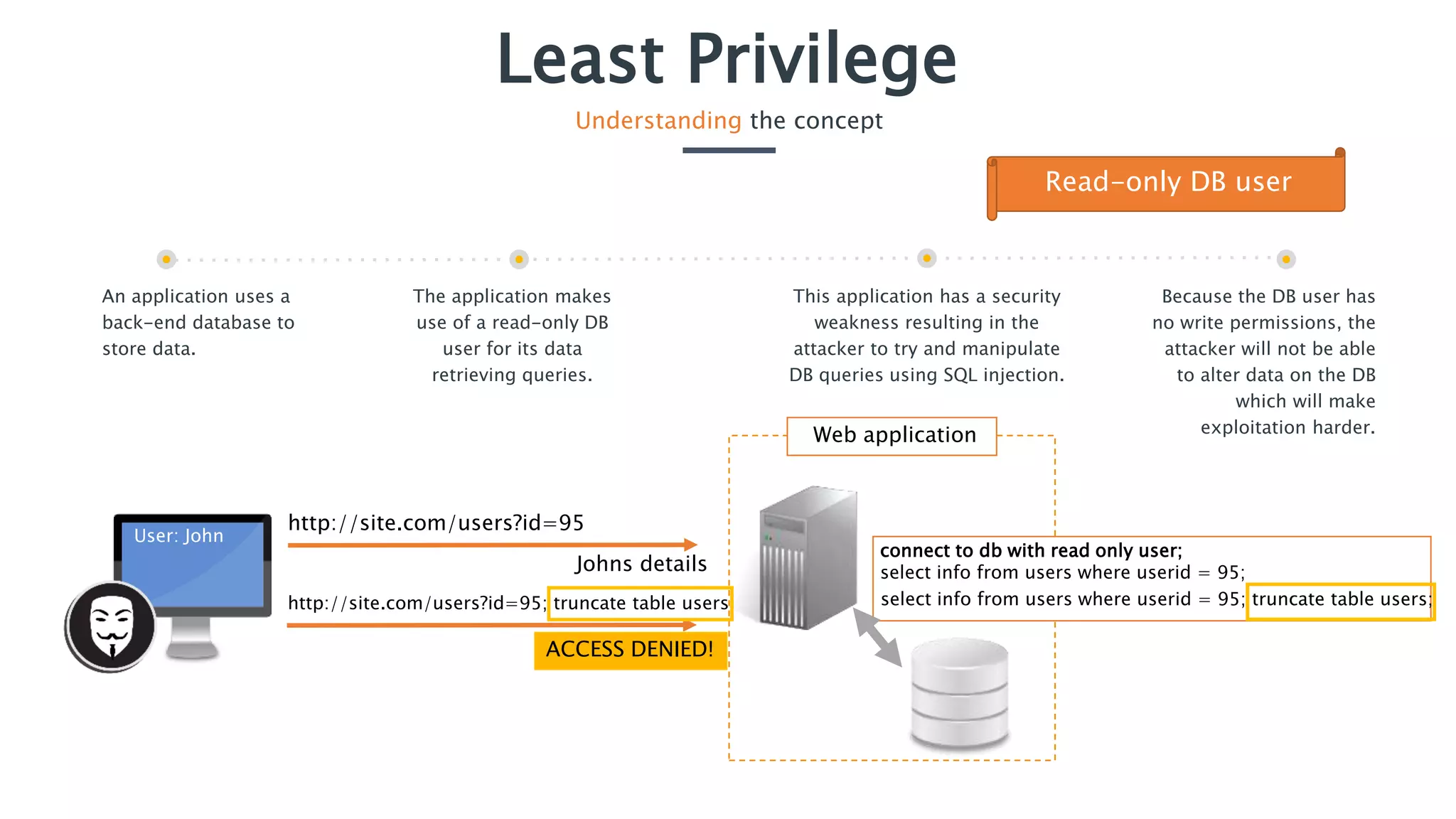
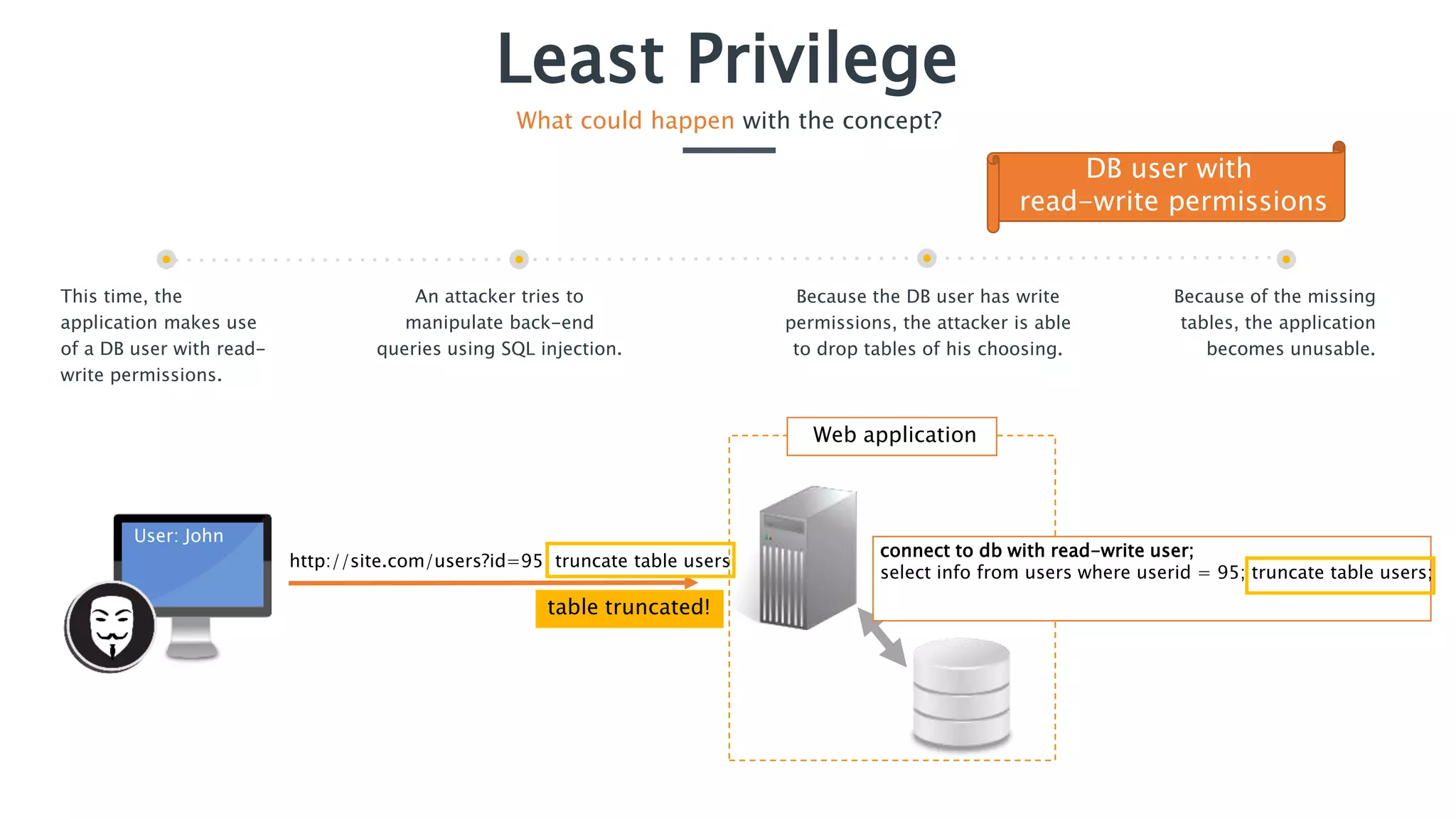
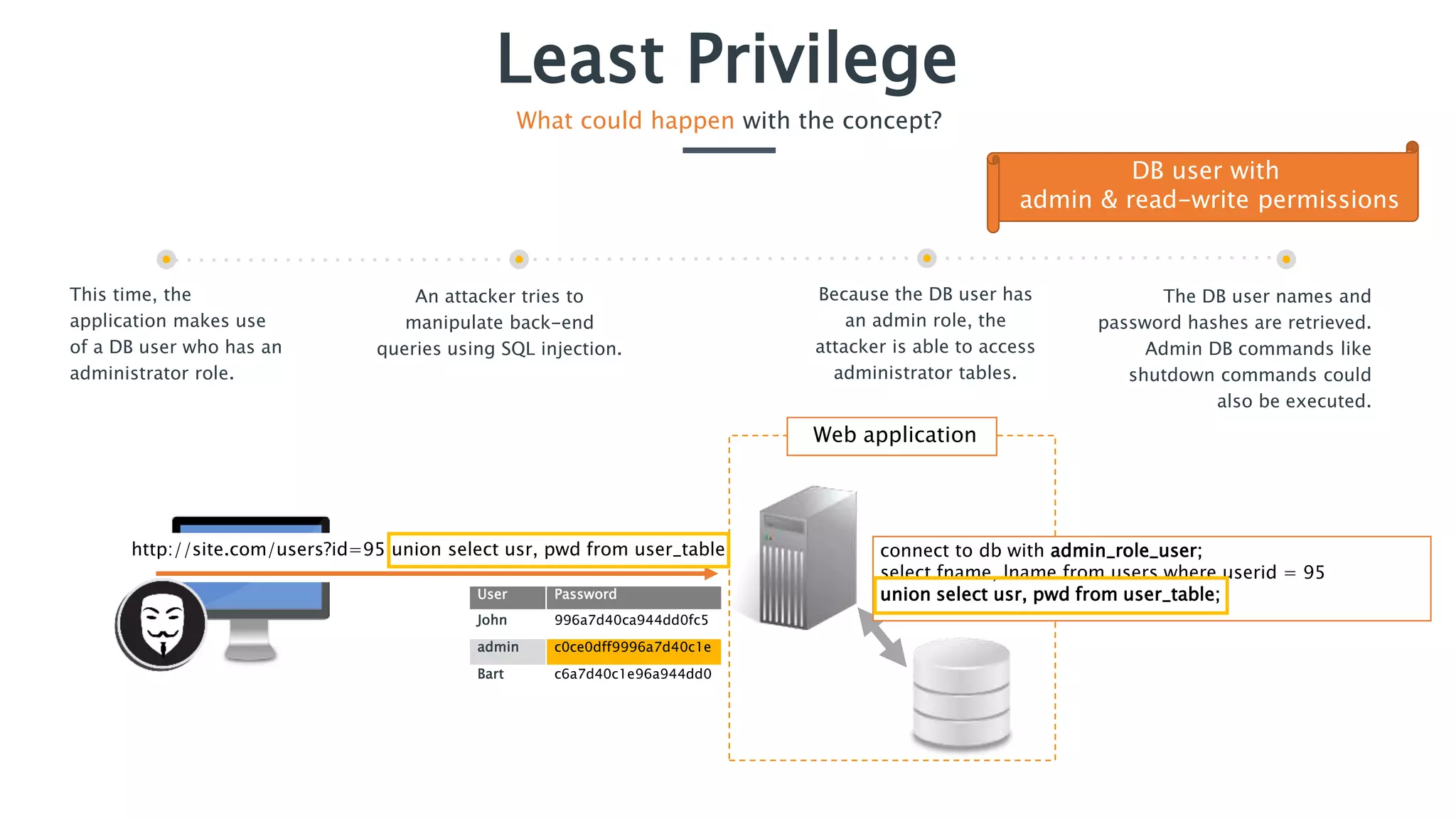
The document discusses the concept of least privilege in application security, emphasizing that users and processes should be granted only the minimum privileges necessary for their tasks to prevent unauthorized actions and exploits like SQL injection. It outlines potential consequences of inadequate privilege assignments, including data manipulation and unauthorized access to sensitive information. Additionally, it provides recommendations for implementation, such as role-based access controls and a deny-by-default policy to enhance security.