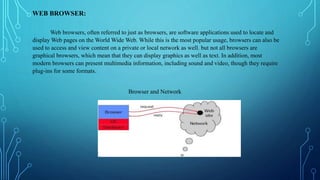
The document discusses browser security. It begins by explaining how initial web protocols assumed cooperation but security became important as usage increased. It then discusses how browsers work, including how they access web pages using HTTP and display content. The document outlines some threats to browser security like zero-day exploits, cross-site scripting, and phishing. It also discusses the security versus usability tradeoff in browser design.