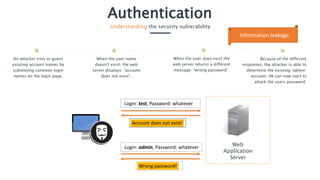
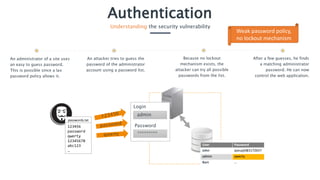
The document discusses the 'authentication' vulnerability in web applications, highlighting risks associated with weak password policies and insecure authentication processes. Common causes include inadequate password practices and information leakage, which can lead to account takeovers, especially of administrative accounts. Preventative measures include implementing strong password policies, securely hashing passwords, and employing account lockout mechanisms to enhance security.