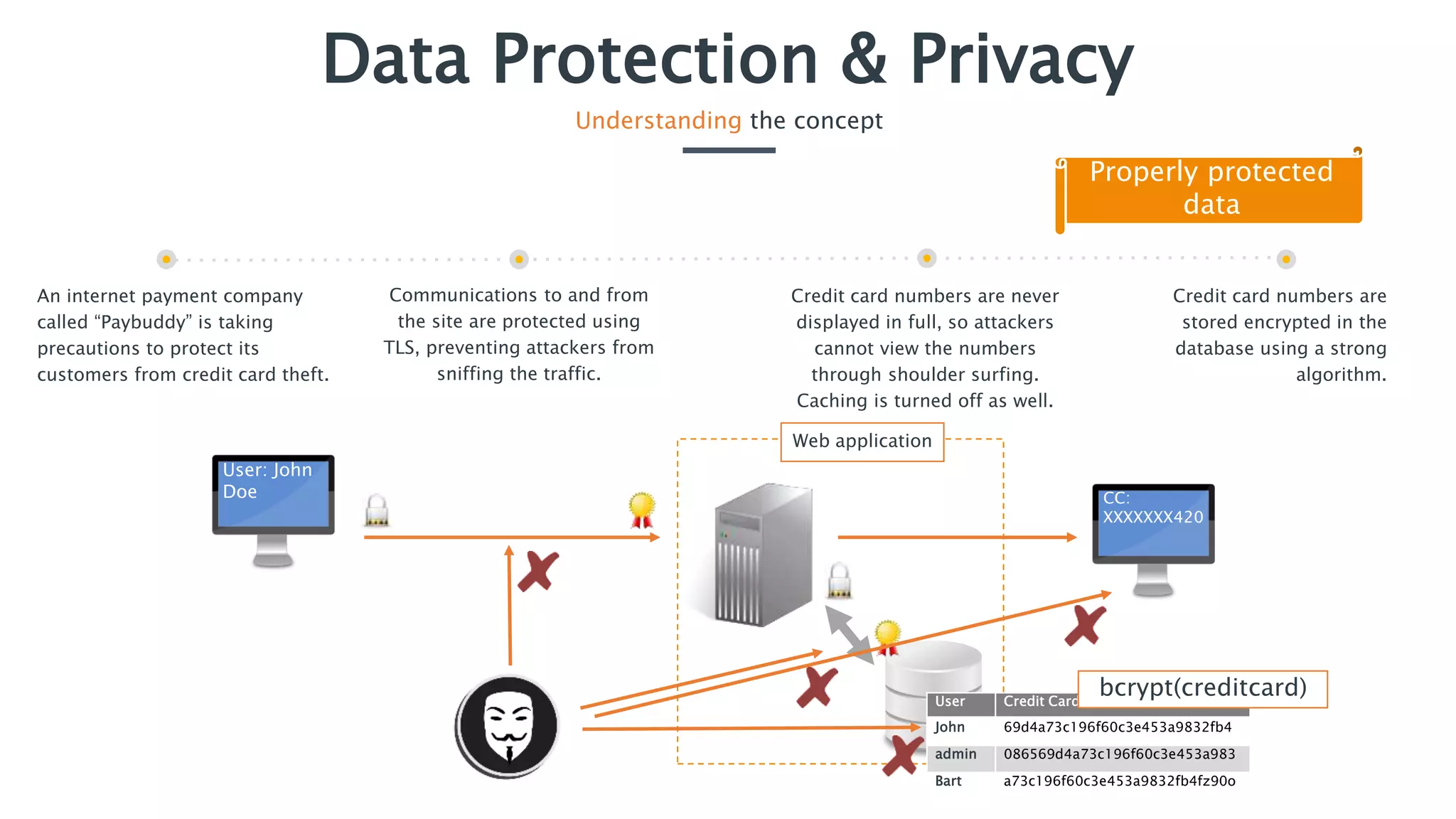
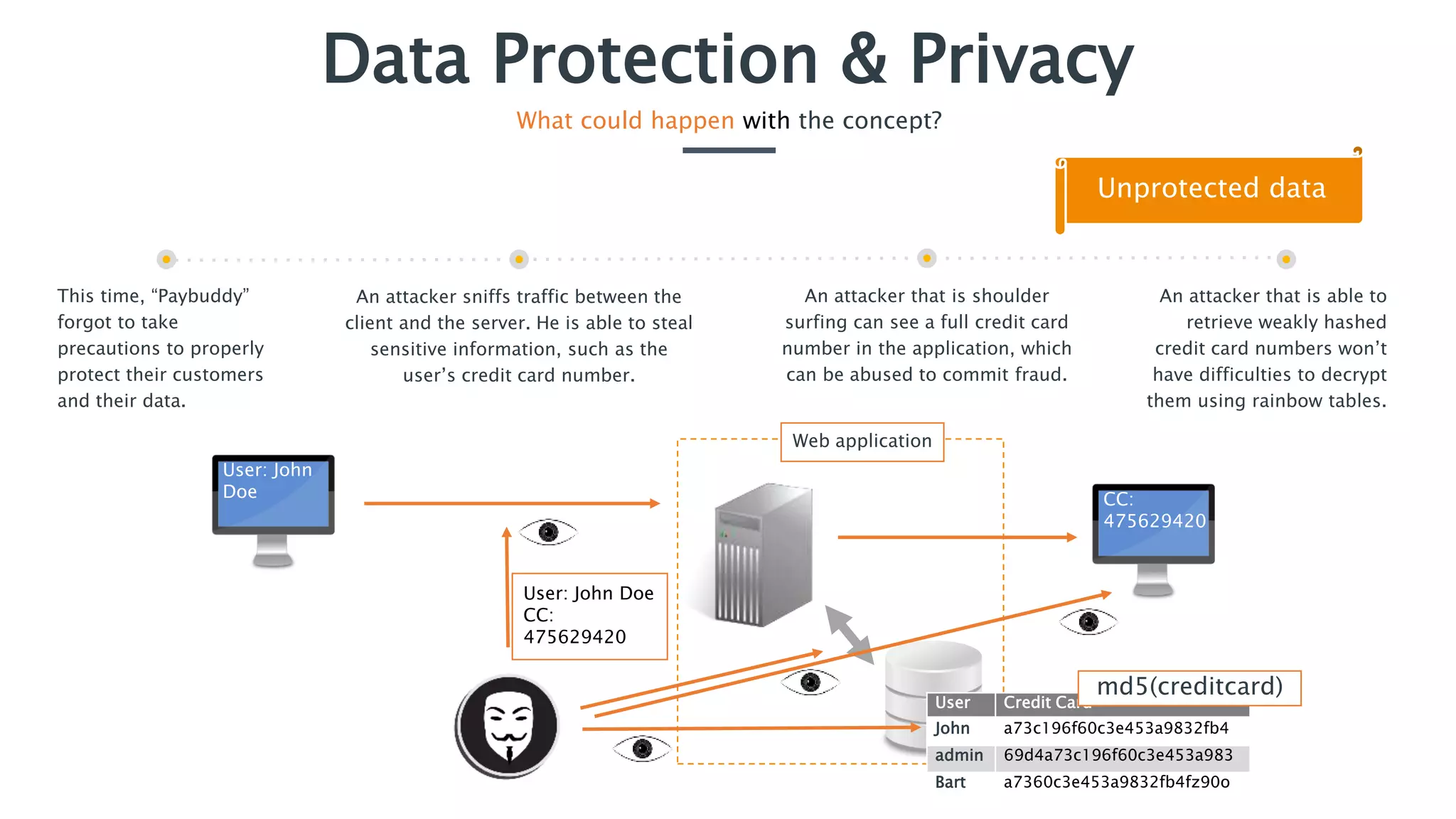
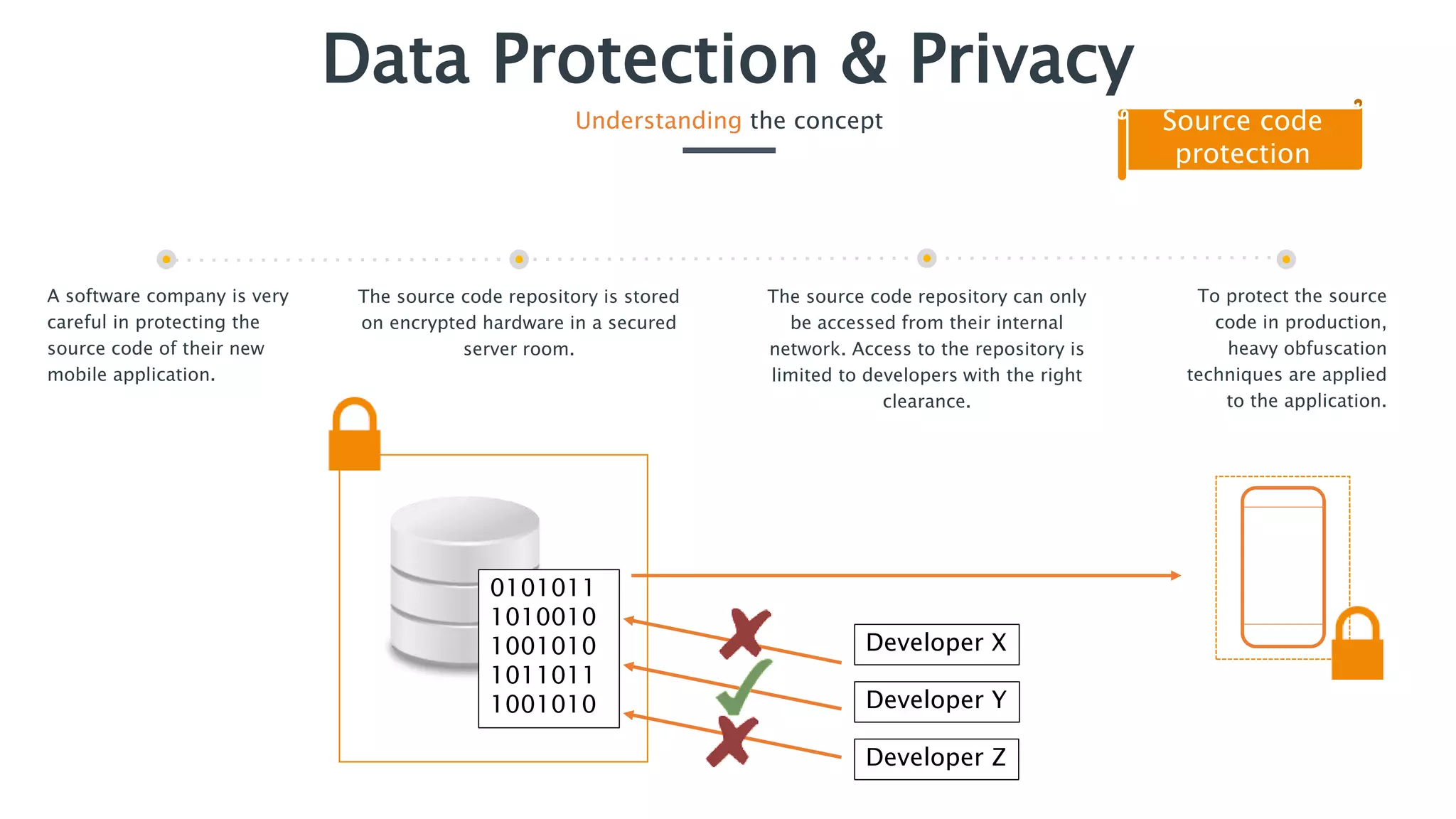
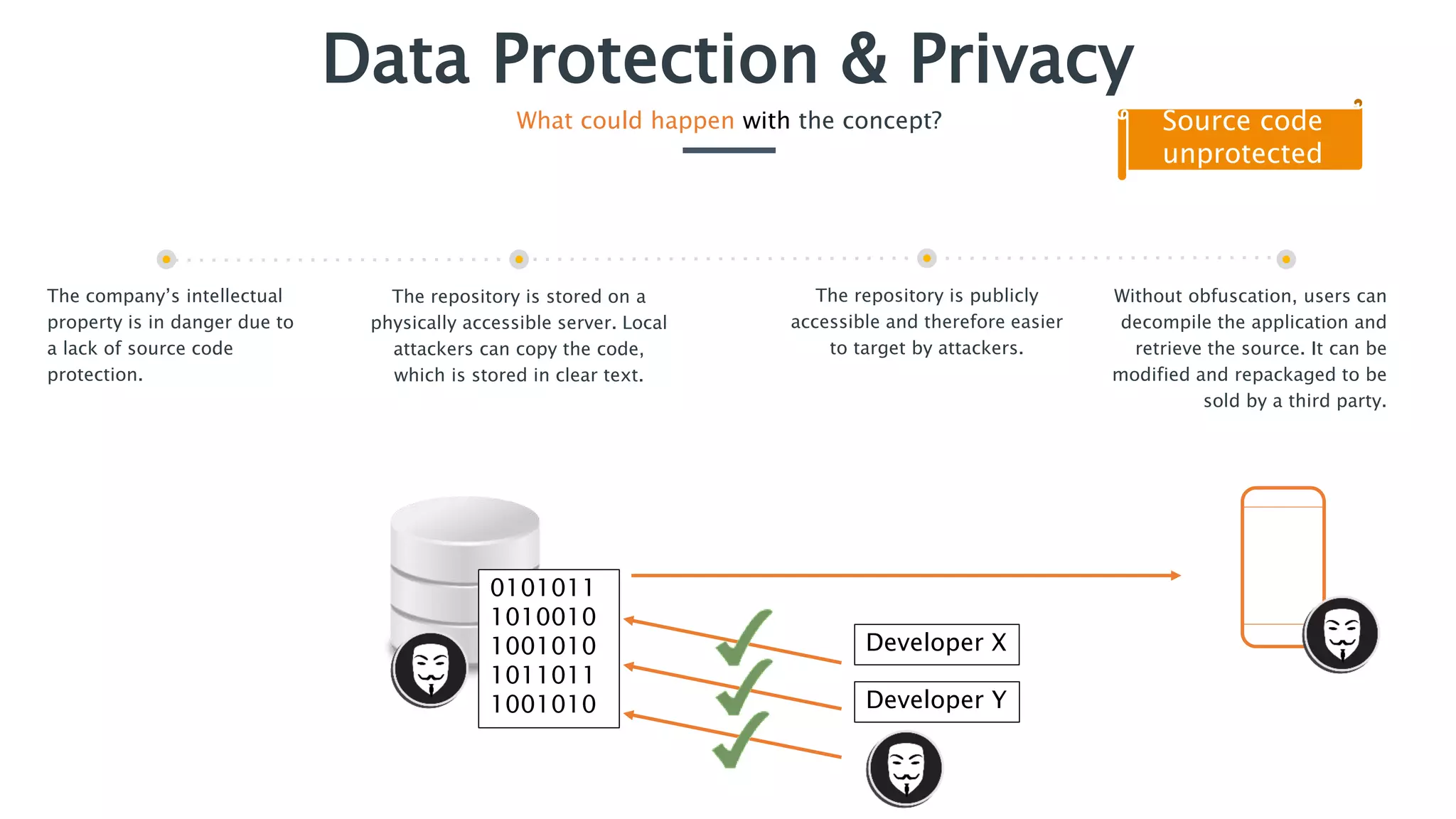
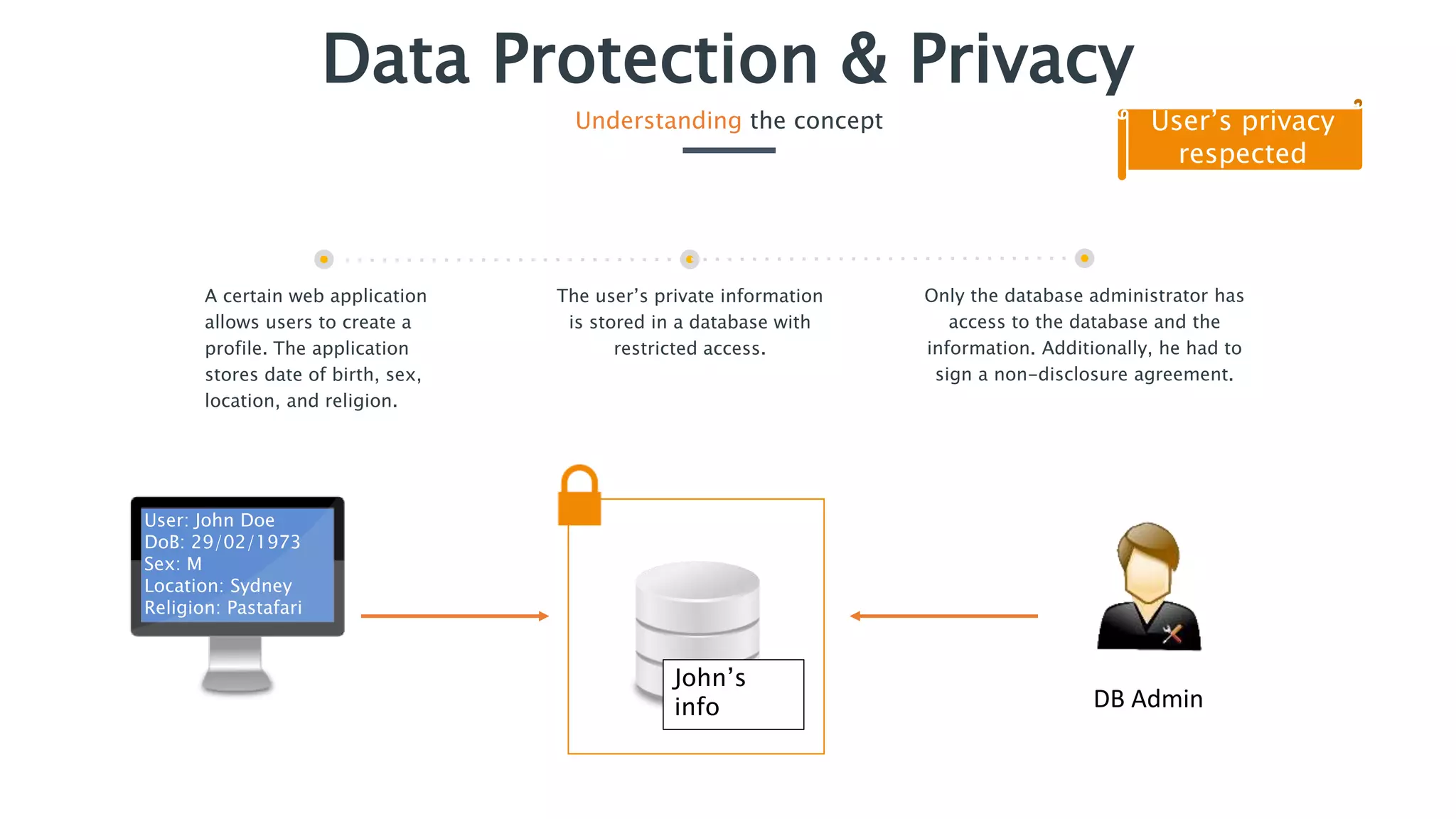
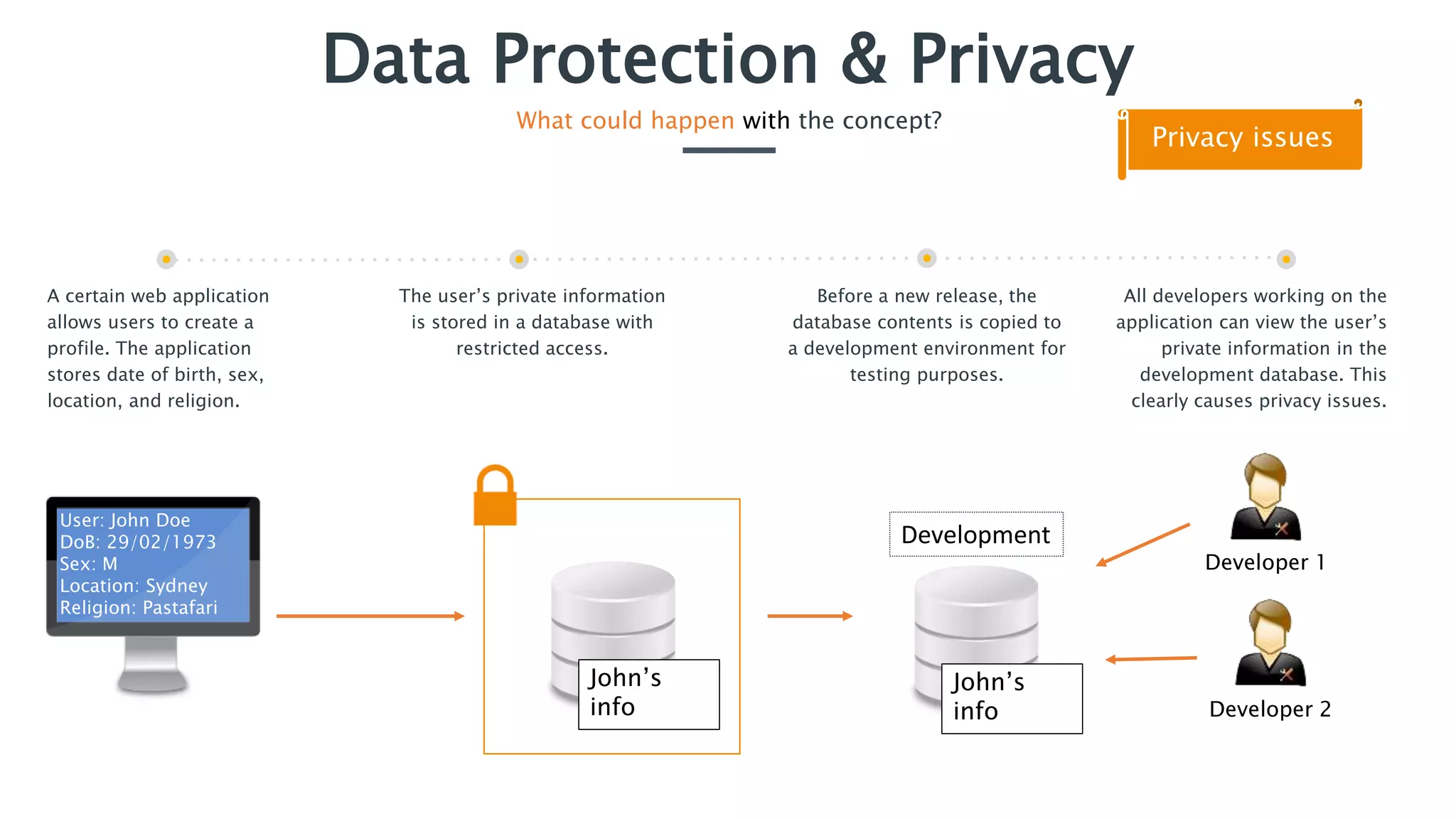
The document outlines essential security practices for application development, emphasizing the need for protection of sensitive information from attacks such as data sniffing and unauthorized access. It provides examples, including the internet payment company 'paybuddy,' which failed to secure credit card information leading to potential fraud. Additionally, it stresses proper data handling protocols, such as only storing necessary information and utilizing encryption, to mitigate privacy issues and protect user data.