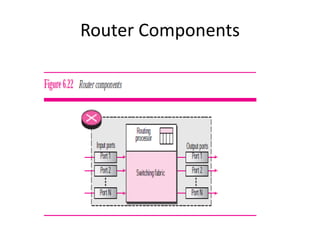
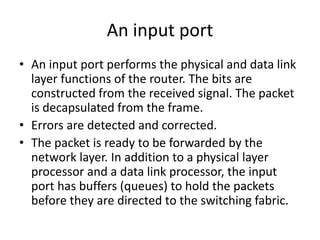
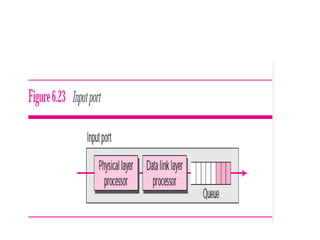
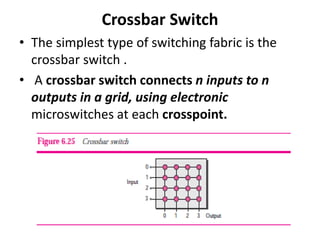
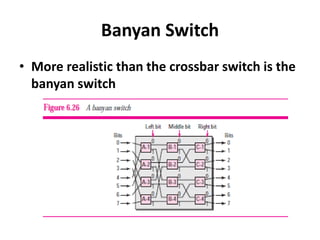
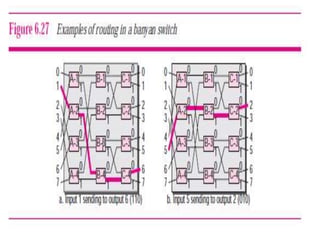
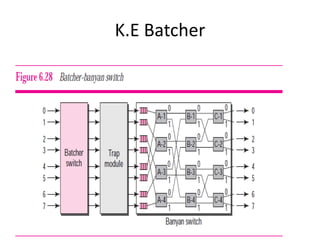
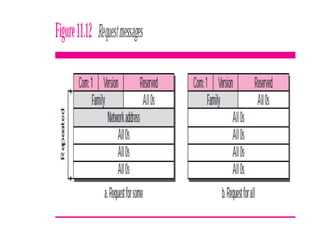
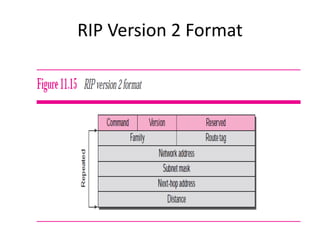
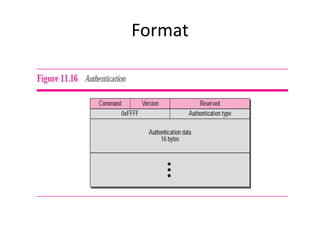
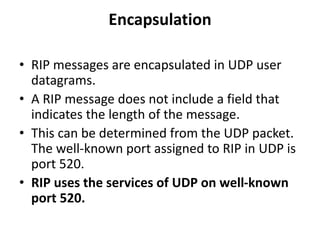
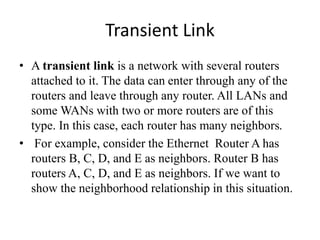
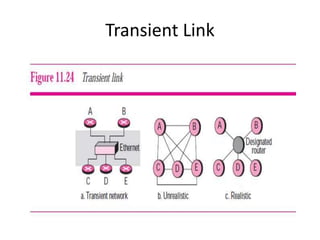
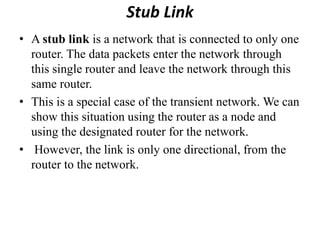
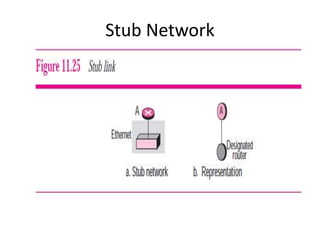
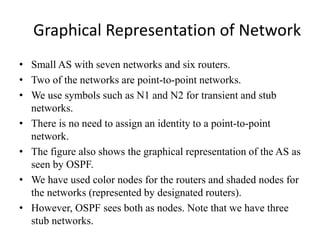
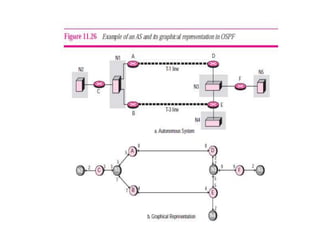
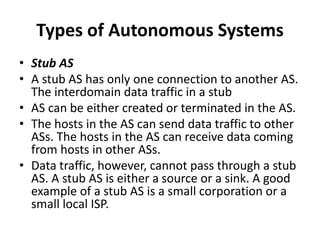
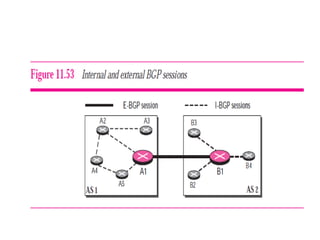
The document discusses different routing methods used in computer networks, including:
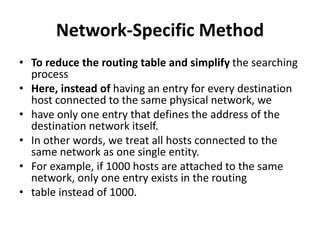
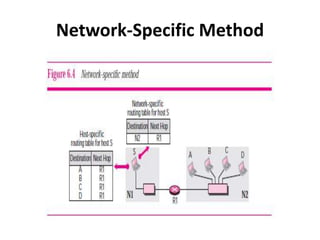
- Network-specific routing which treats all hosts on the same network as a single entity in the routing table.
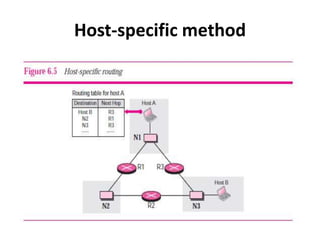
- Host-specific routing which explicitly defines routes to individual host addresses in the routing table.
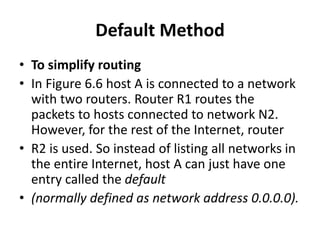
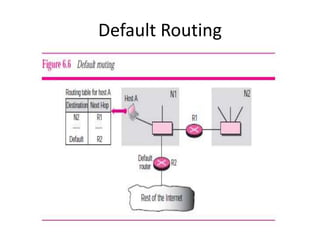
- Default routing which uses a single default route for all unknown destinations.
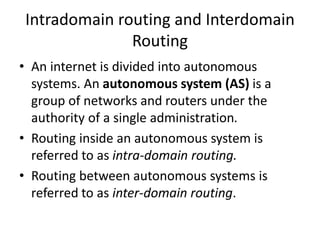
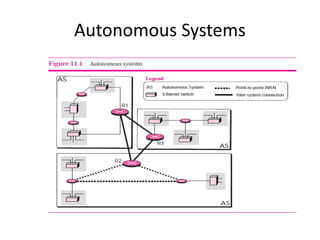
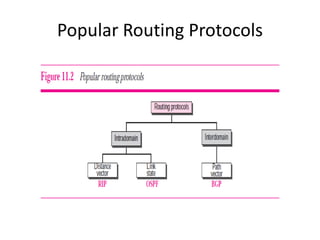
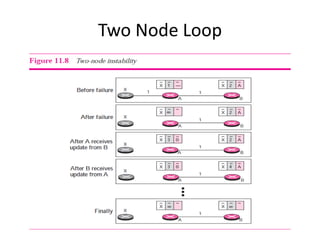
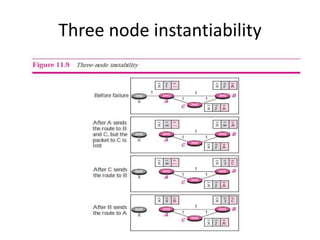
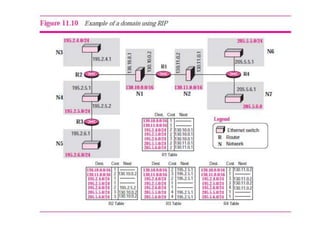
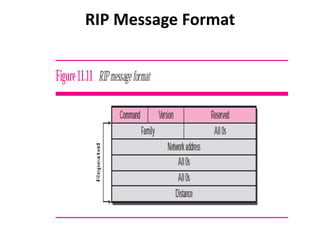
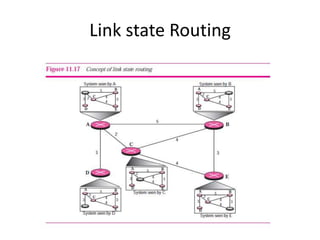
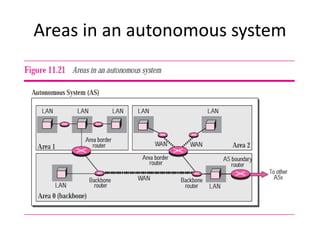
It also covers routing protocols like RIP and OSPF, explaining how they establish and maintain routing tables dynamically as the network changes. Distance vector protocols like RIP propagate full routing tables between routers, while link-state protocols like OSPF flood link state information to build independent views of the network topology.