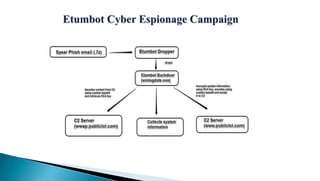
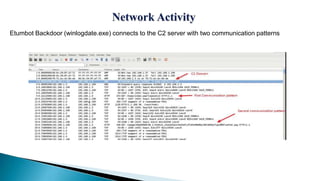
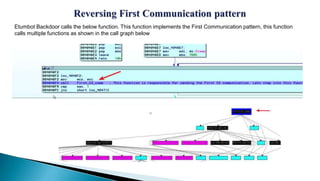
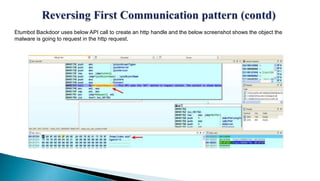
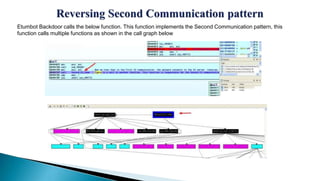
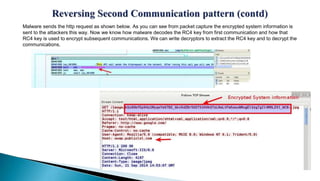
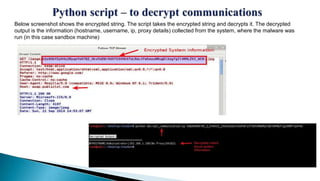
This document provides an overview of the Etumbot malware, including its use in cyber espionage attacks, how it works, and how to analyze and decrypt its communications. Etumbot is dropped via spearphishing emails and establishes persistence on Windows systems by adding a registry entry. It communicates with command and control servers using an initial handshake to receive an RC4 key, which it then uses to encrypt additional communications like sending stolen system information. The document demonstrates analyzing the malware's behavior and decrypting its network traffic.