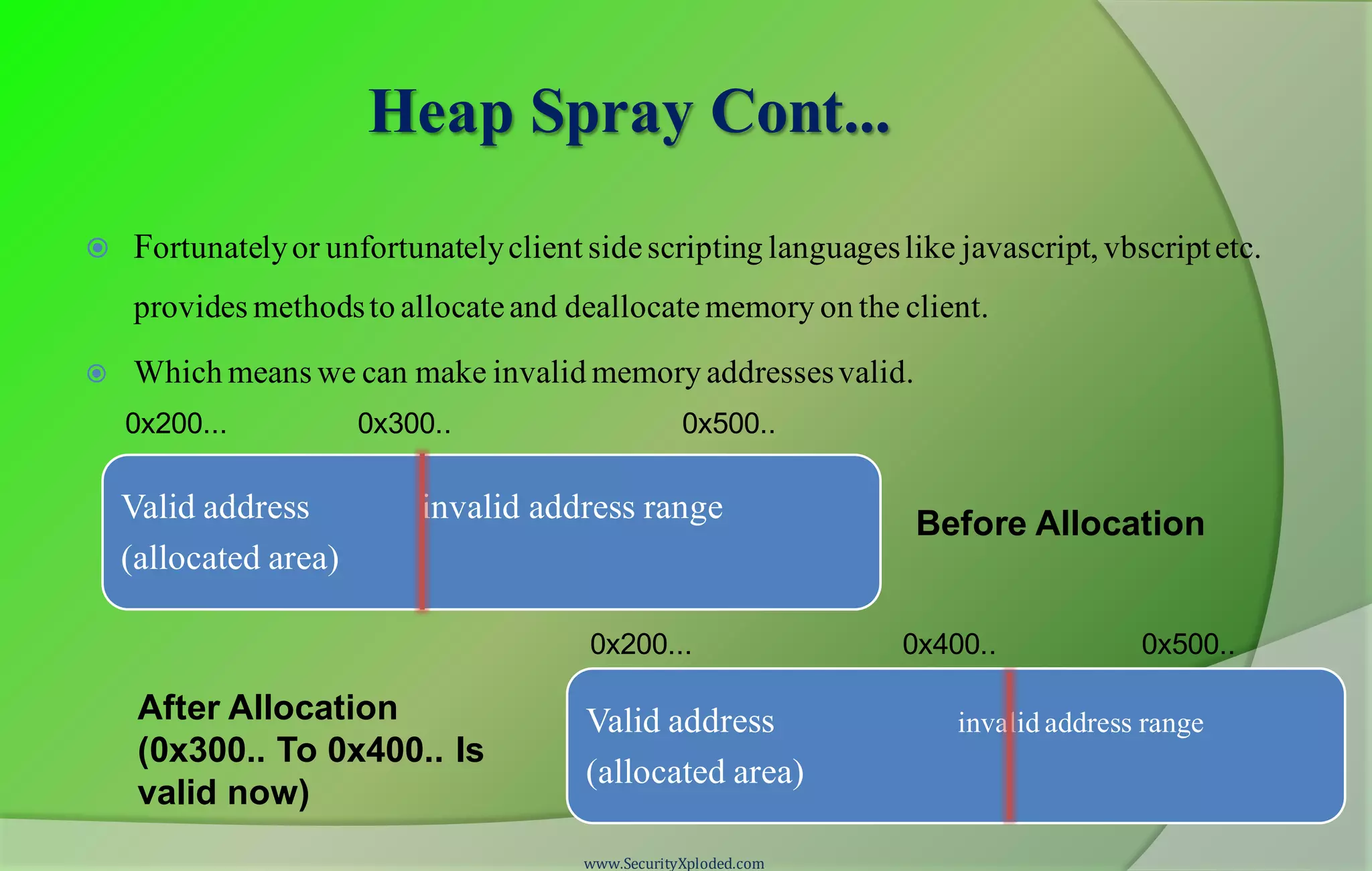
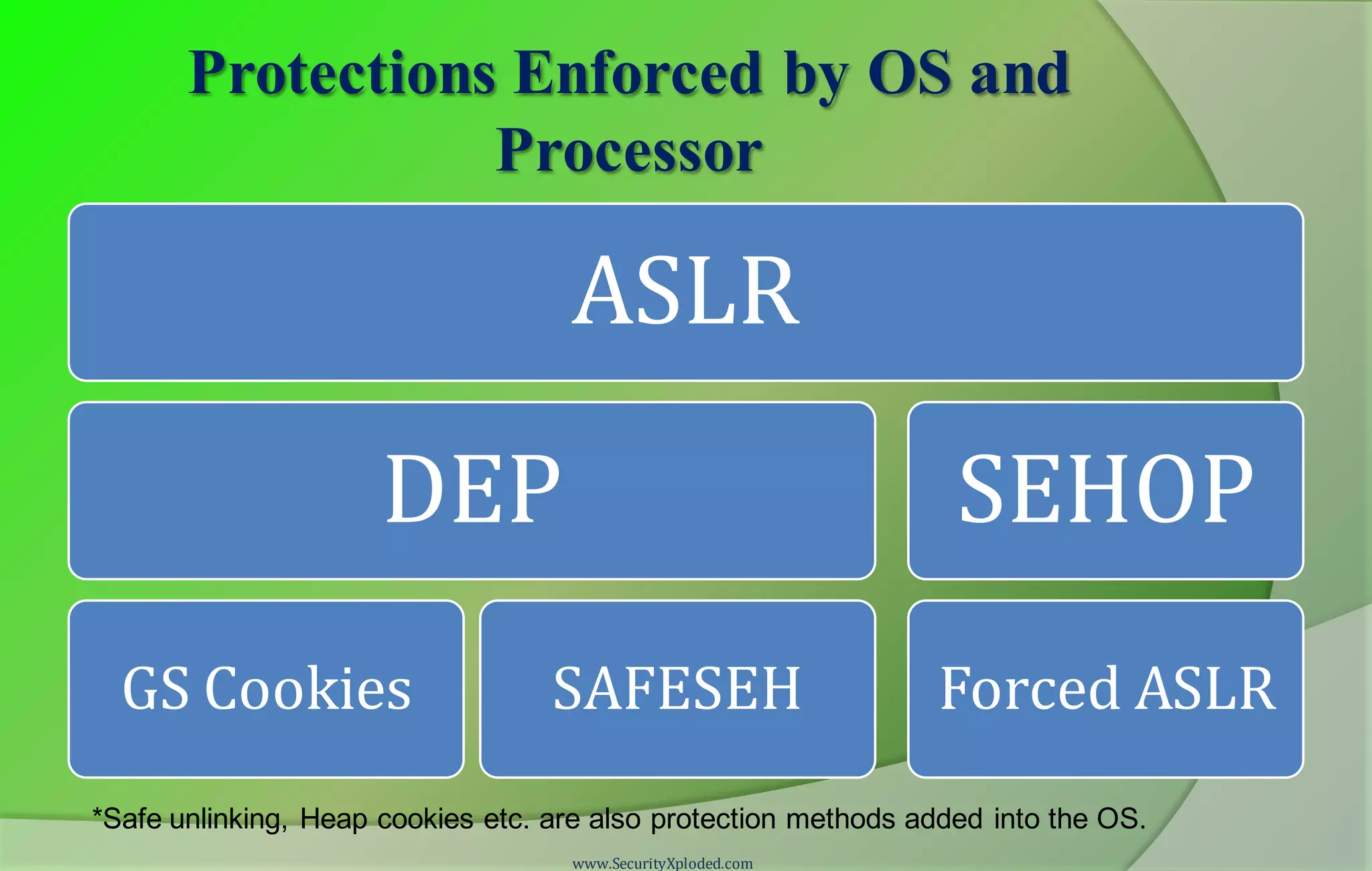
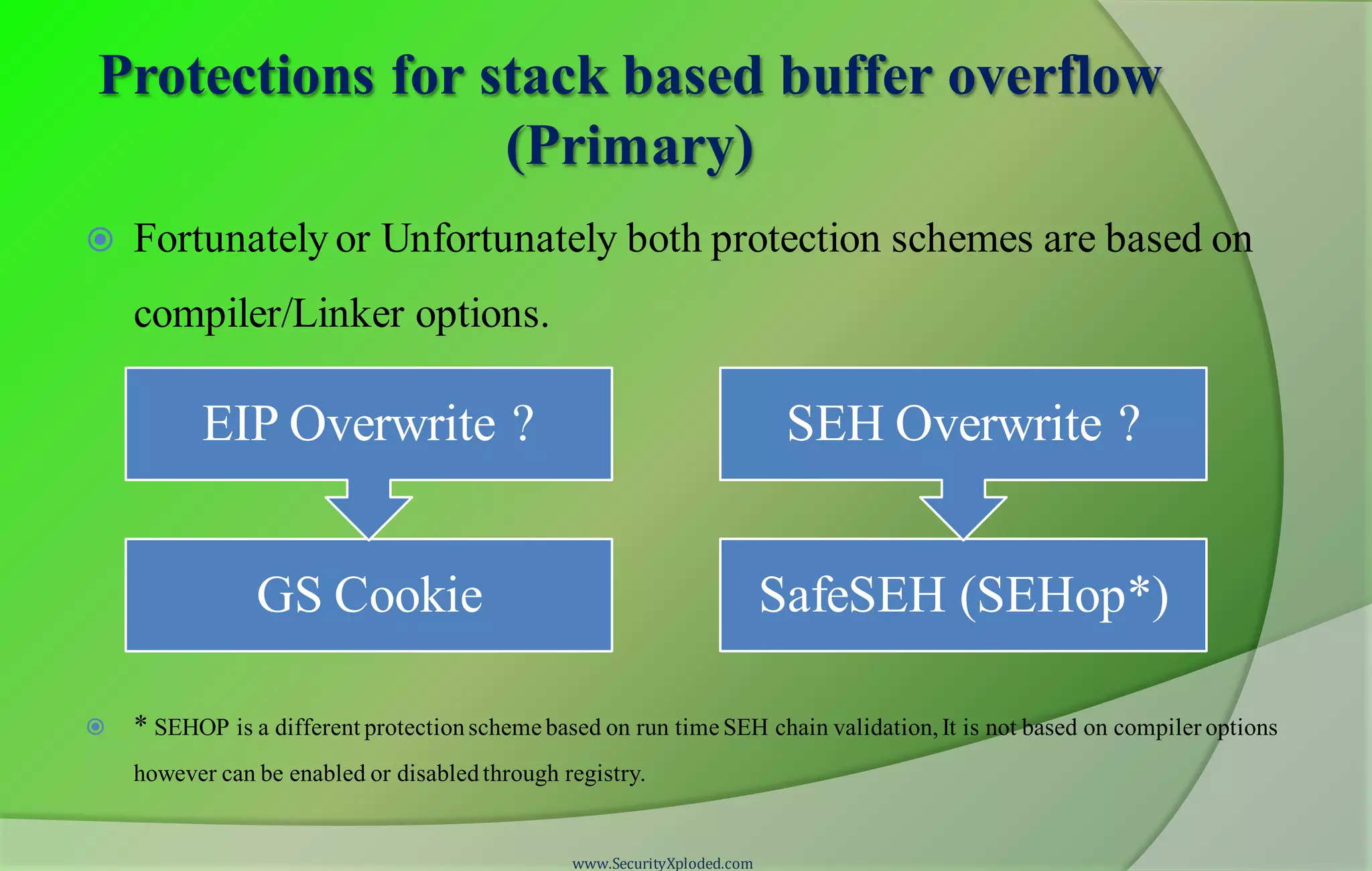
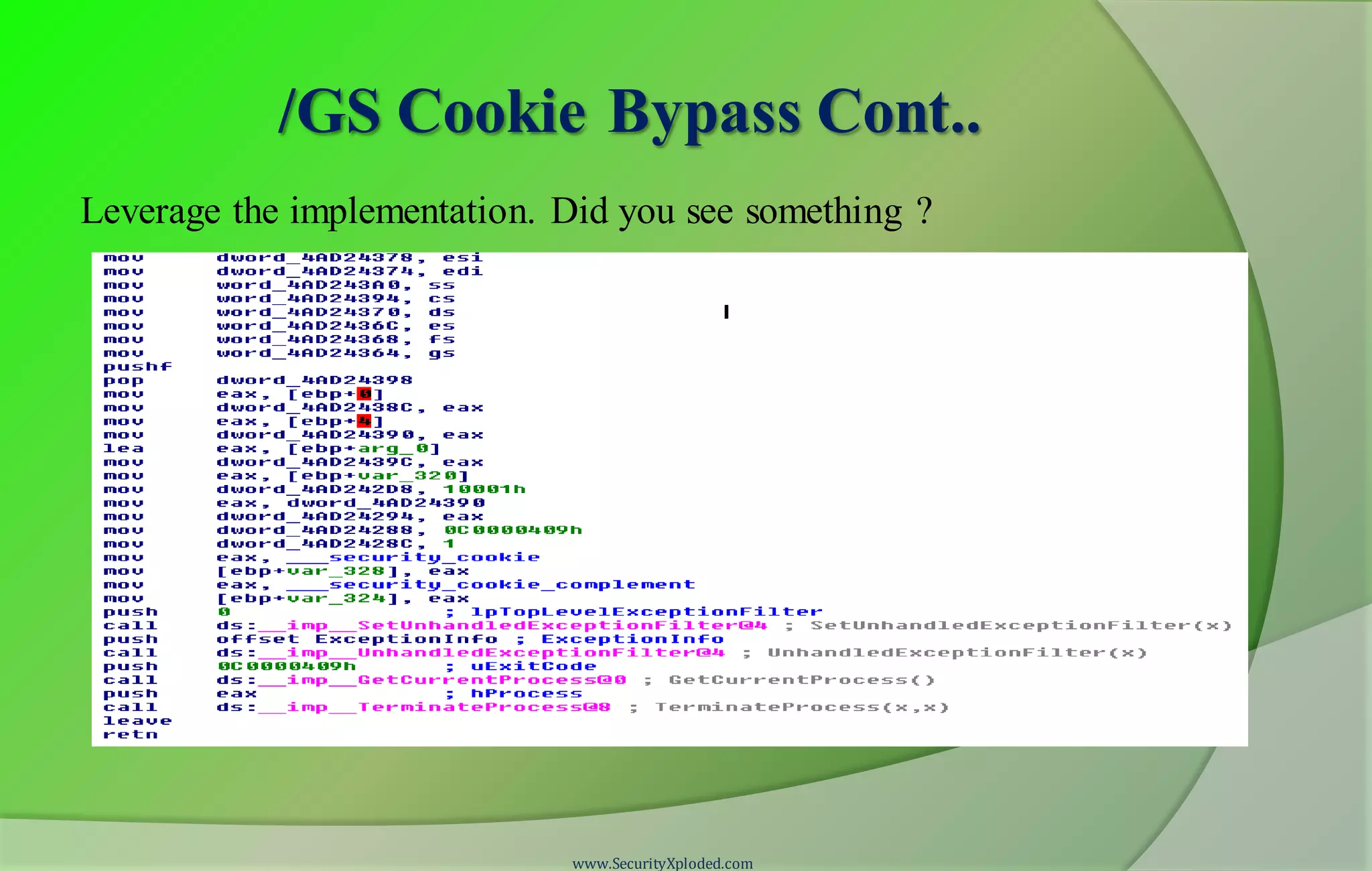
The document provides information about a reversing and malware analysis training program. It includes disclaimers about the content presented, acknowledges those involved in the training, and outlines the agenda. The training will use a "zig-zag approach" and cover topics like stack and heap-based buffer overflows, protections like GS cookies, SafeSEH, DEP, and ASLR, client-side exploits using heap spray techniques, and methods for bypassing protections. Demonstrations will be provided on exploiting vulnerabilities and bypassing DEP. Attendees are encouraged to ask questions and keep up with latest security news.









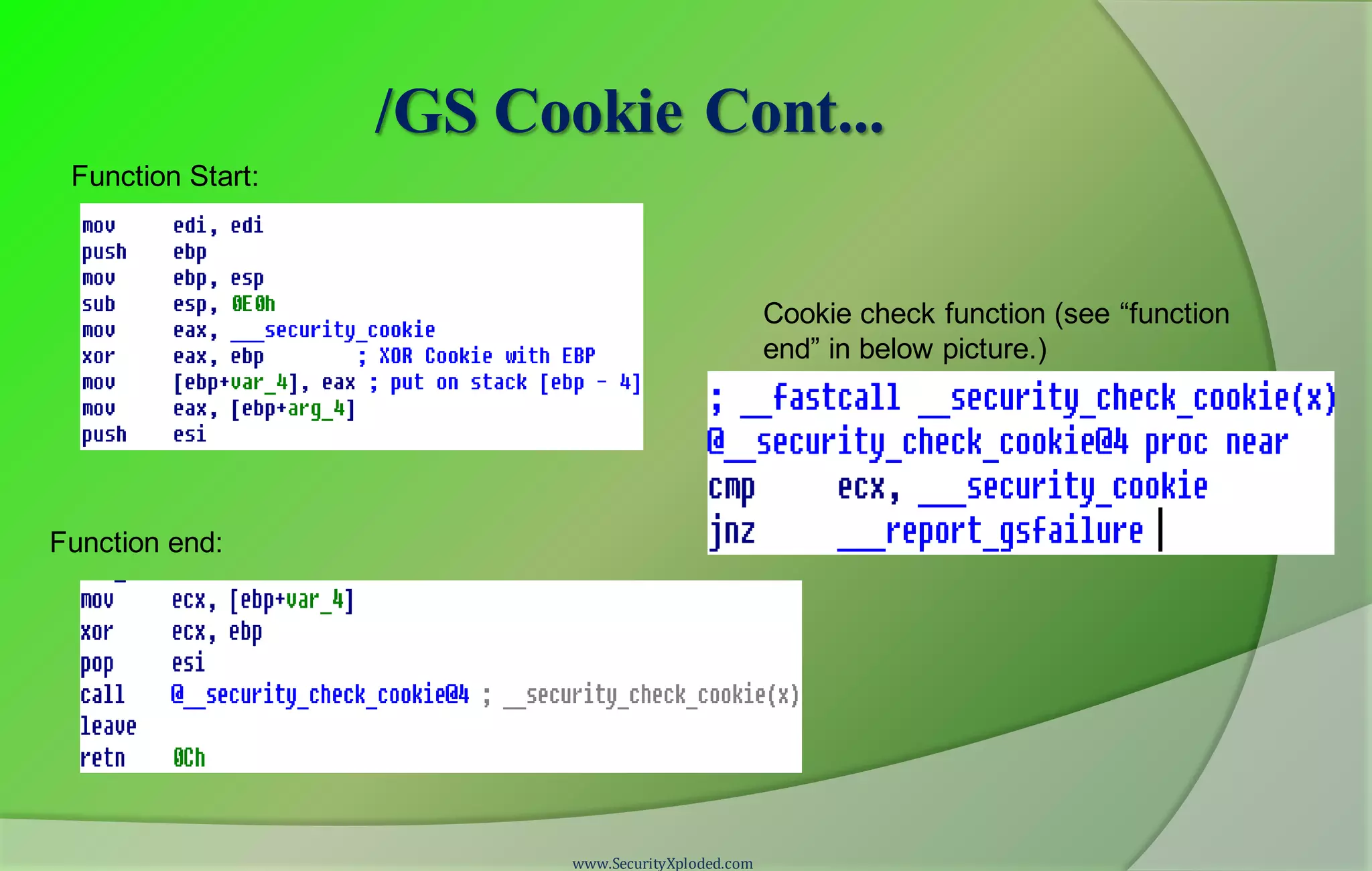

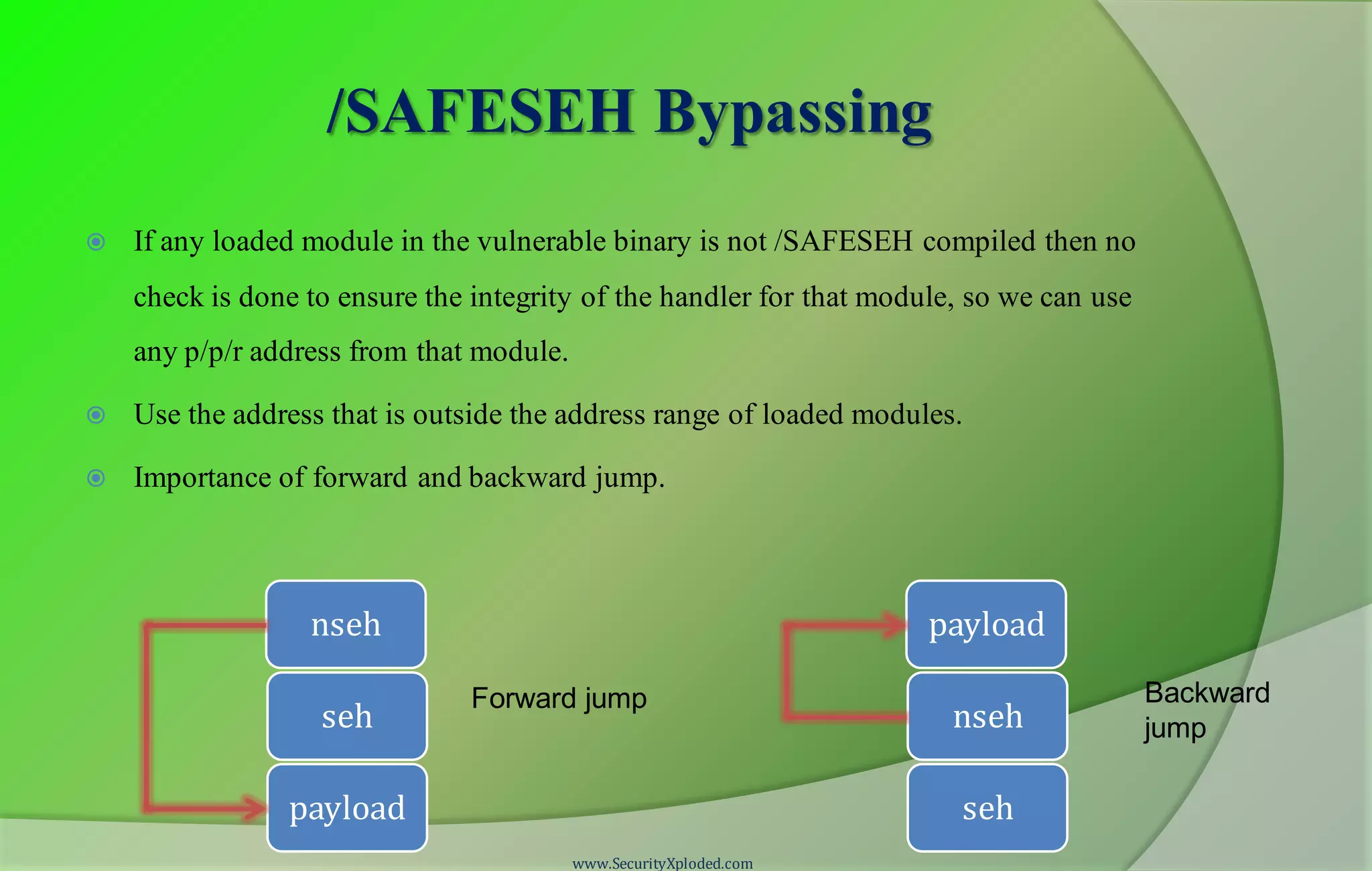
![SafeSEH
Compiler [Linker] /SAFESEH option
Static list of known good exception handlers for the binary.
Checks every time when a handler is called against the static list, if not in the list
then handler is invalid and takes preventive measures.
Load configuration directory stores meta information about safe exception
handlers.
If any module is not compiled with /SAFESEH then no check is done to ensure
the integrity of the handler for that module.
www.SecurityXploded.com](https://image.slidesharecdn.com/reversingmalwareanalysistrainingpart11-exploitdevelopmentadvanced-131009095821-phpapp02/75/Reversing-malware-analysis-training-part-11-exploit-development-advanced-15-2048.jpg)

![Stack Heap Flipping (Stack Pivoting)
I think this deservea dedicated slide
Dependingon the conditionswemay have largeROP payload whilespaceon stack
may be less or may be our entirepayload is on heap.
Flip the heap on to the stack so that we can get larger room.
InstructionslikeXCHG ESP[REG], REG[ESP]can be used.
We can also jump insidethevalid instructionsto changetheir meaning.
Example:jump onebyte inside“setzal” instruction( FromAdobeU3D exploitin
wild)
www.SecurityXploded.com](https://image.slidesharecdn.com/reversingmalwareanalysistrainingpart11-exploitdevelopmentadvanced-131009095821-phpapp02/75/Reversing-malware-analysis-training-part-11-exploit-development-advanced-19-2048.jpg)

![ASLR
Address Space Layout Randomization
Involves randomly positioning the memory areas like base
address of the binary, position of stack and heap.
Compiler[linker] /DYNAMICBASE option
www.SecurityXploded.com](https://image.slidesharecdn.com/reversingmalwareanalysistrainingpart11-exploitdevelopmentadvanced-131009095821-phpapp02/75/Reversing-malware-analysis-training-part-11-exploit-development-advanced-22-2048.jpg)