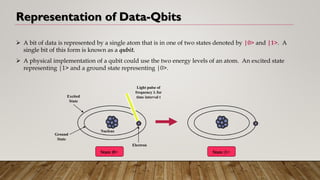
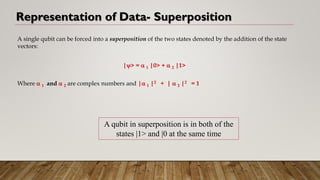
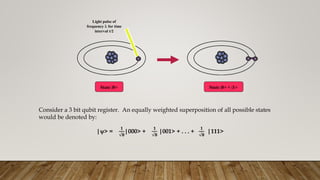
Quantum computing is a new method of computing based on quantum mechanics that offers greater computational power than classical computers. Quantum computers use quantum bits or qubits that can exist in superpositions of states allowing massive parallelism. Several approaches like ion traps, quantum dots and NMR have demonstrated quantum computing. However, challenges remain around errors from decoherence and a lack of reliable reading mechanisms. If these obstacles can be overcome, quantum computers may solve problems in artificial intelligence, cybersecurity, drug design and more exponentially faster than classical computers.