Embed presentation
Download as PDF, PPTX





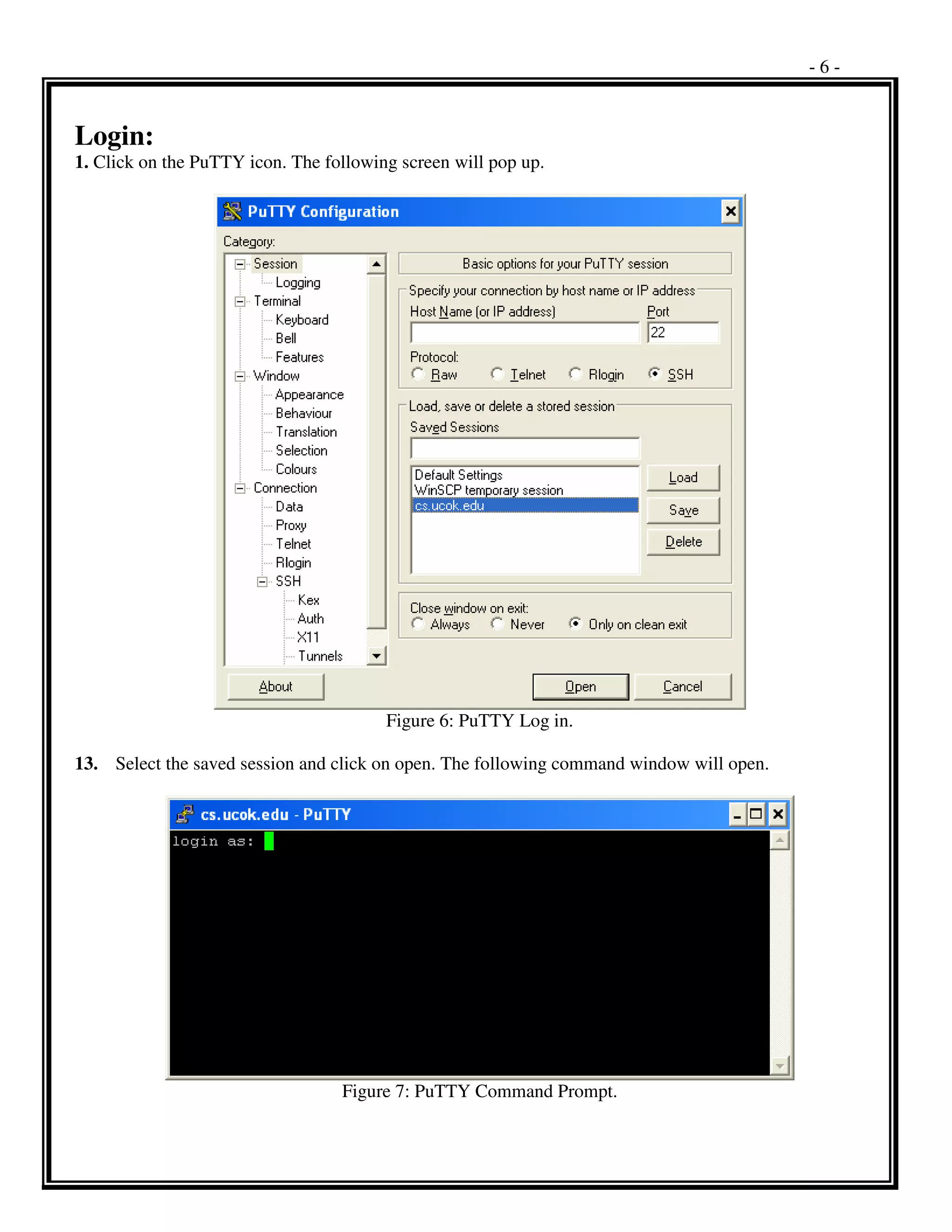








PuTTY is a free and open-source terminal emulator and SSH client. It allows users to connect to other systems running SSH, Telnet, or Rlogin servers over the network. PuTTY can be downloaded and installed easily without any configuration required. It can be configured by specifying connection settings like the host name, protocol, encryption, and saved for future use. Basic UNIX commands in PuTTY allow users to navigate directories, view and edit files, install and run programs. Common commands include ls, cd, cat, vi, more, grep, find, man and others. PuTTY provides secure remote access and administration of UNIX servers through its simple terminal interface.













