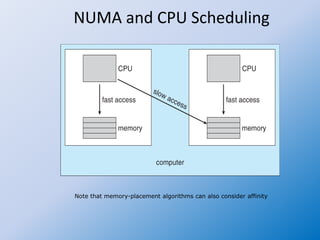
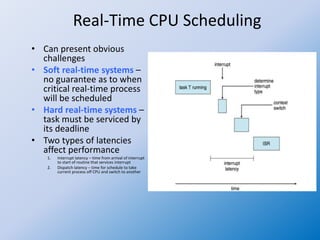
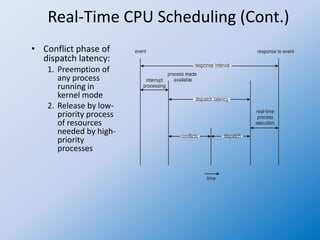
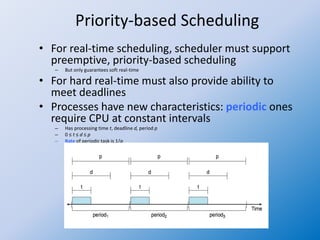
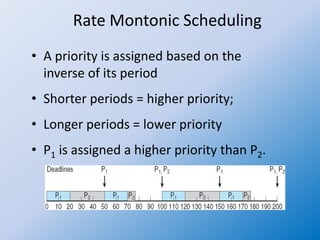
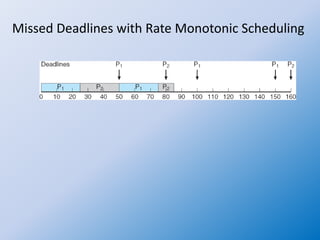
The document discusses multiple-processor scheduling in operating systems, outlining key concepts such as symmetric and asymmetric multiprocessing, processor affinity, and load balancing strategies. It also covers real-time CPU scheduling criteria, including soft and hard real-time systems, along with various scheduling algorithms like rate monotonic and earliest deadline first scheduling. Additionally, it highlights the impact of virtualization on scheduling efficiency and response times.