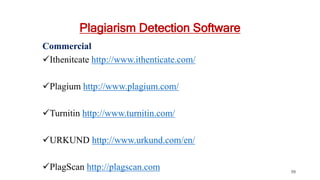
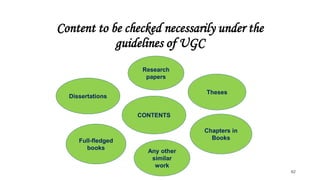
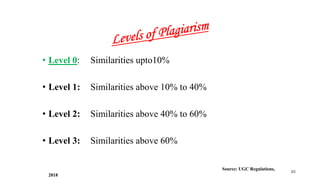
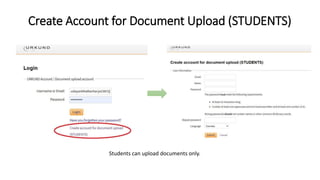
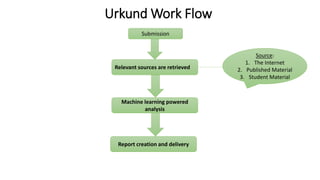
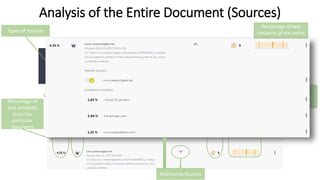
This document discusses various types of academic misconduct, including fabrication, falsification, and plagiarism. It defines fabrication as the construction of data that was never actually observed or measured. Falsification is changing or omitting results to support a claim. Plagiarism involves using others' work and ideas without proper citation. The document provides several examples of academic misconduct, such as conducting research on humans without informed consent, ghost authorship, and image manipulation. It emphasizes the importance of ethical research practices.