Embed presentation
Downloaded 76 times










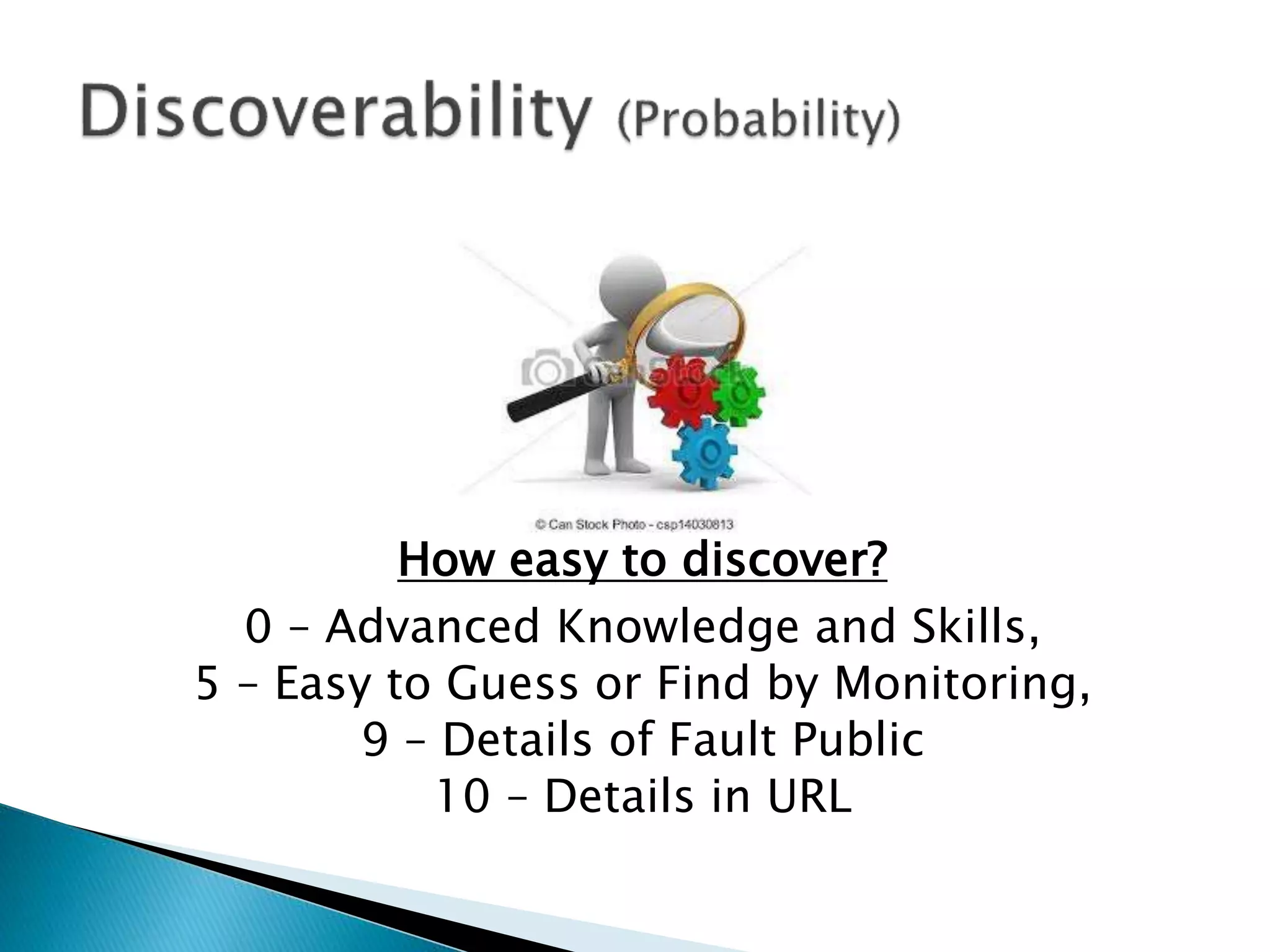




The document features a presentation by Brad Andrews at the North Texas Cyber Security Conference 2015, detailing his extensive experience in technology and information security. It outlines key parts of threat modeling, specifically applying STRIDE and DREAD frameworks for evaluating risks based on various criteria such as damage, reproducibility, and discoverability. Andrews emphasizes collaboration and participation in discussions on risk evaluation.













