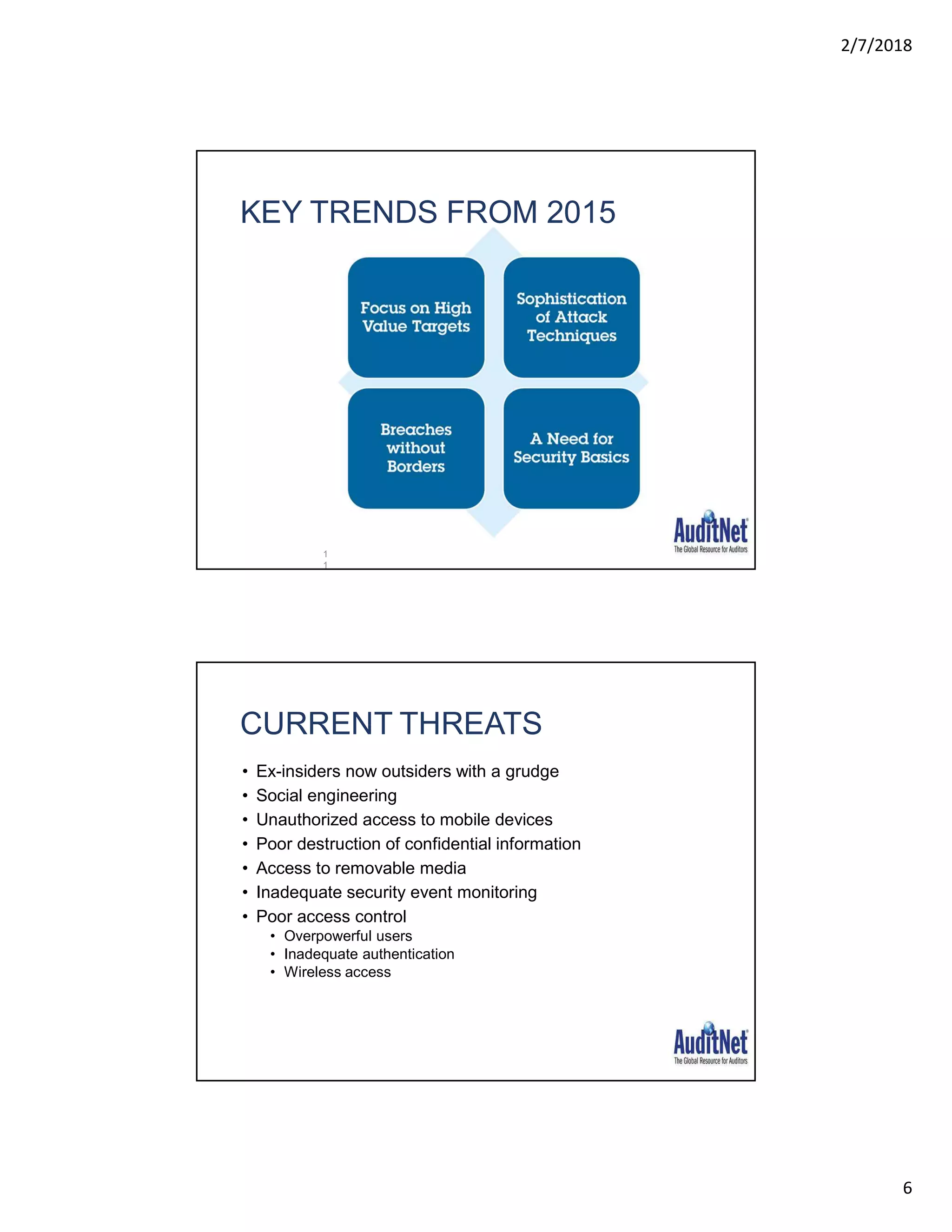
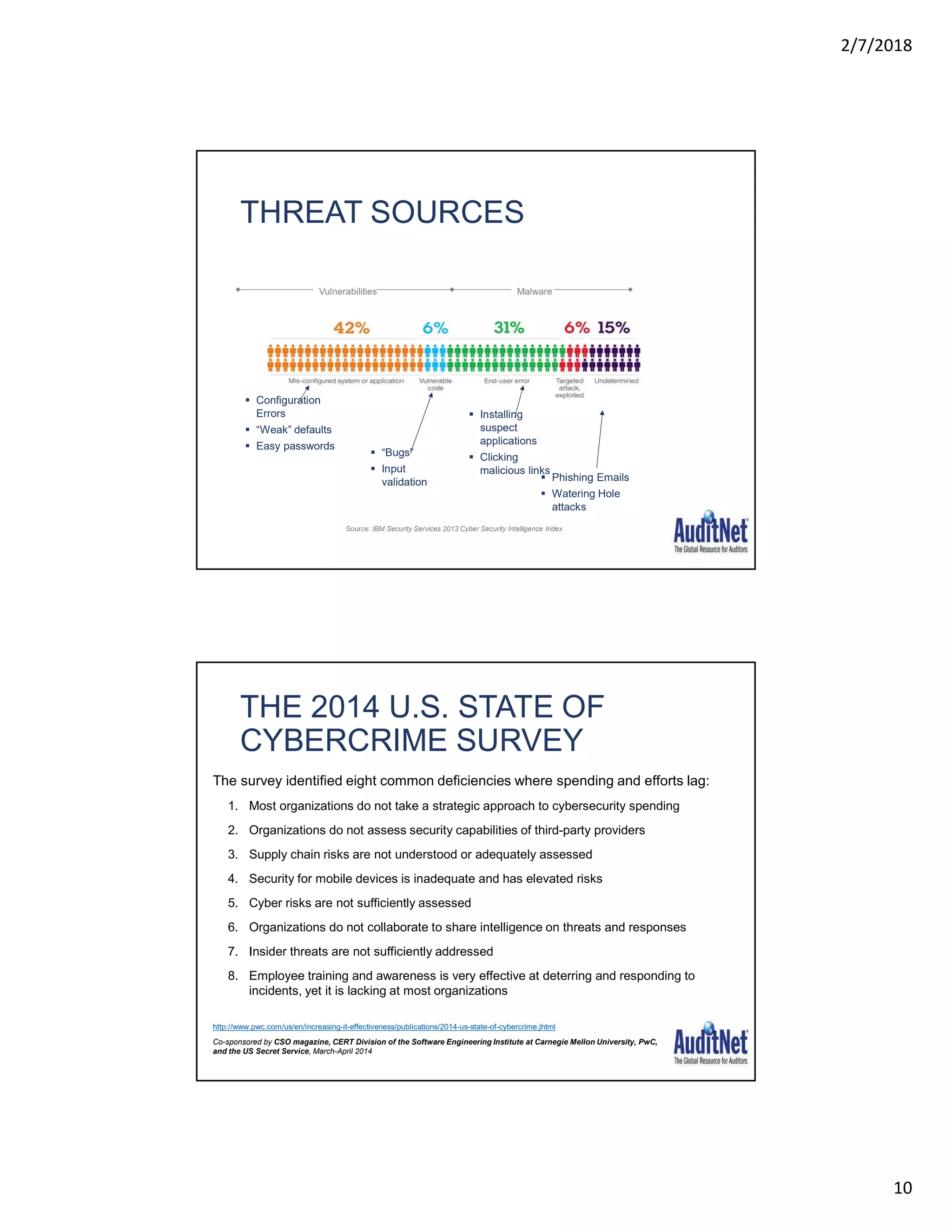
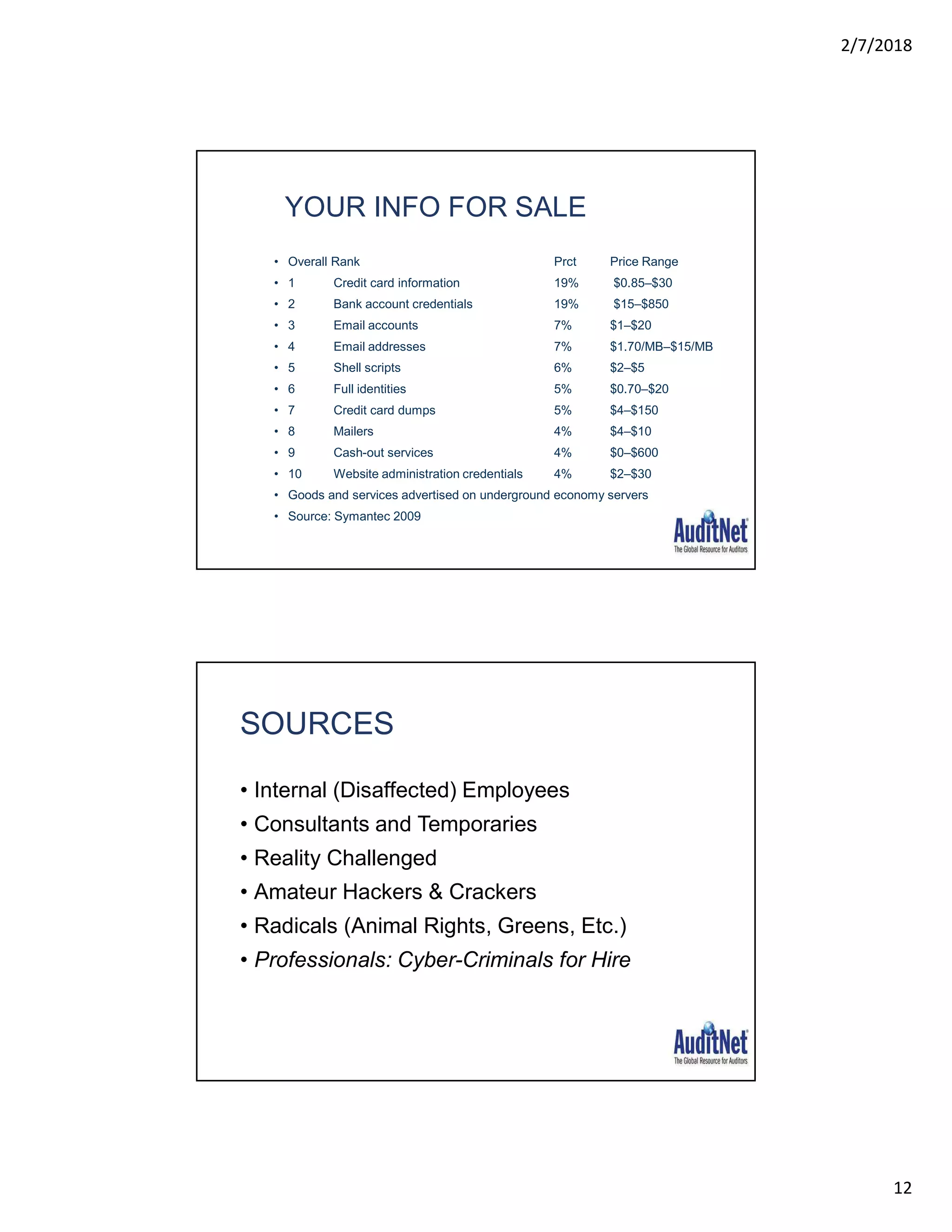
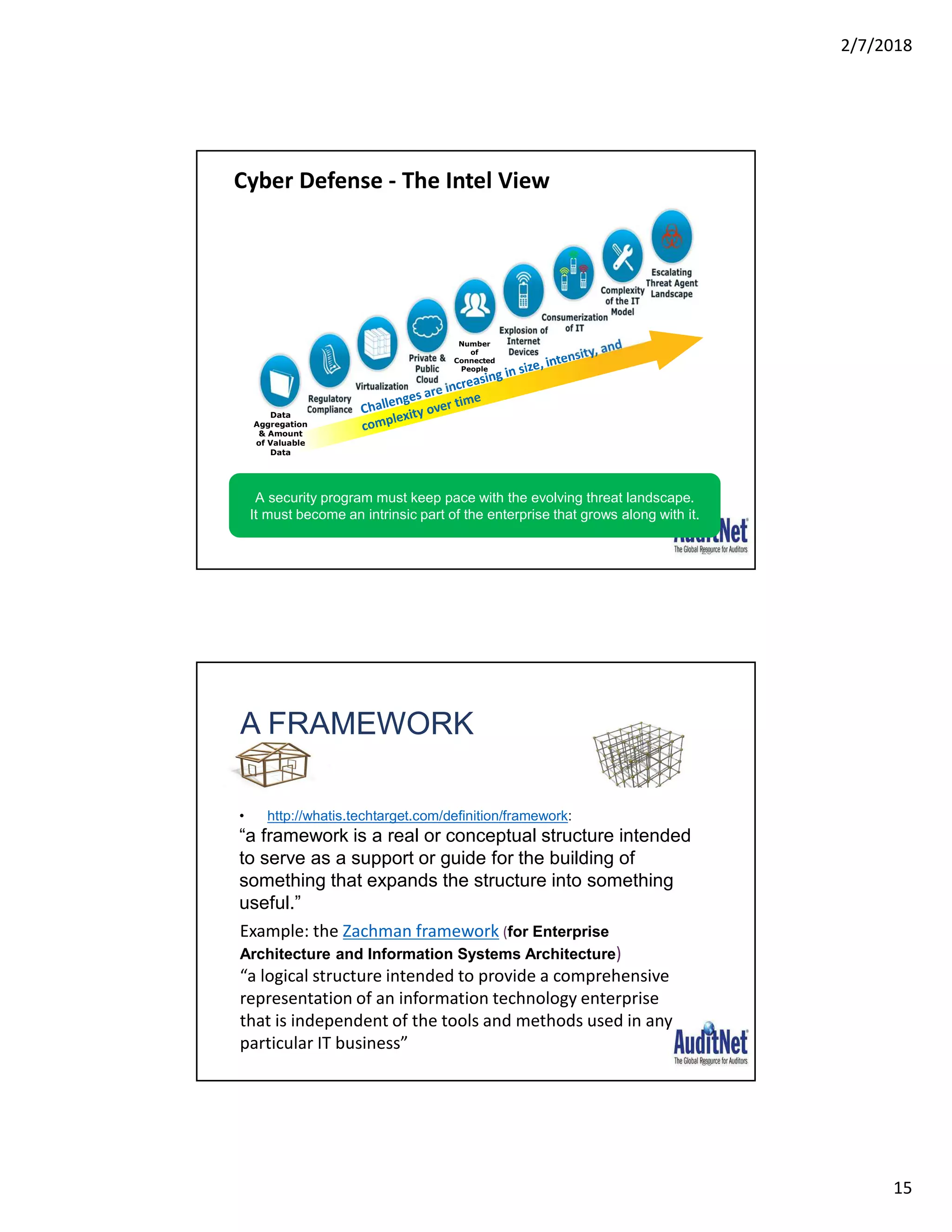
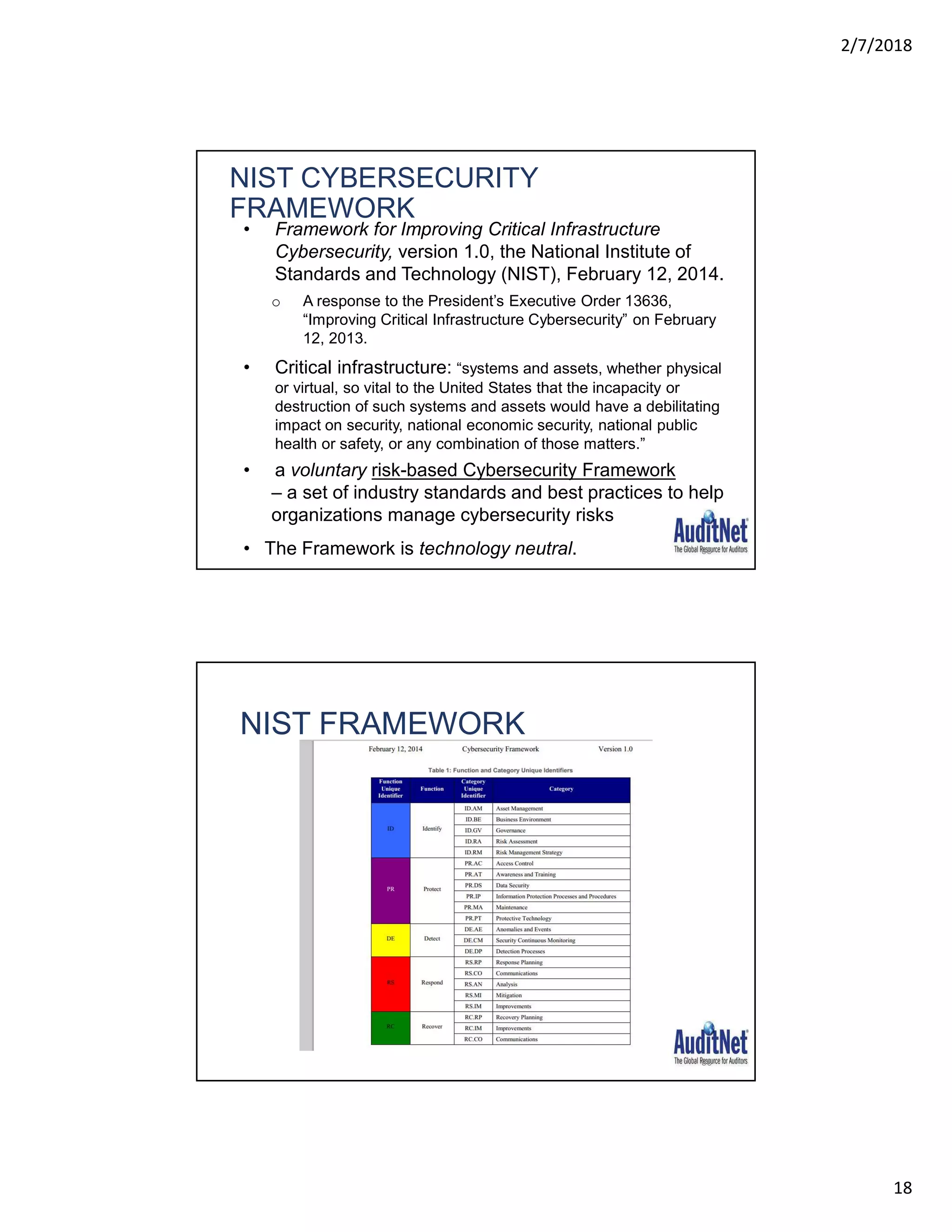
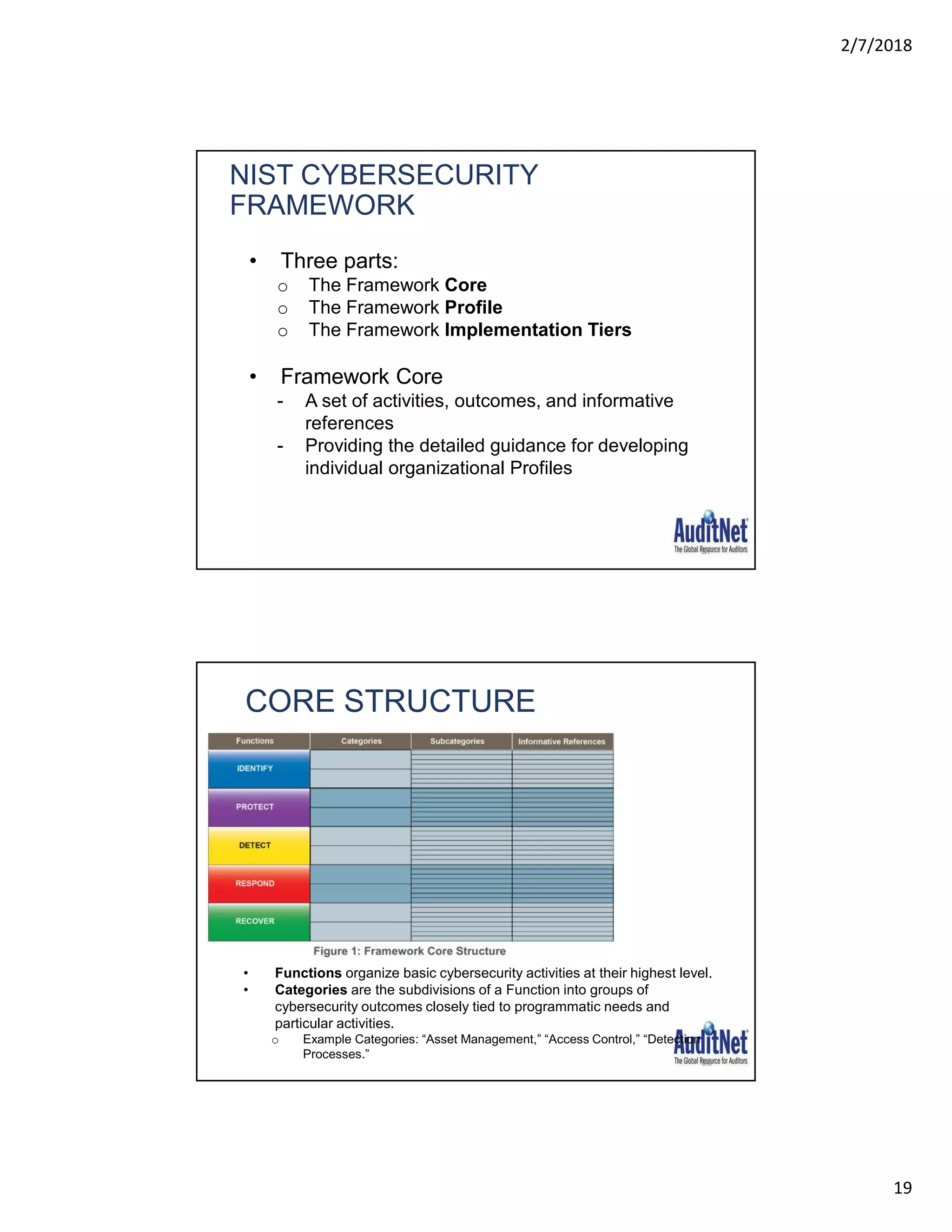
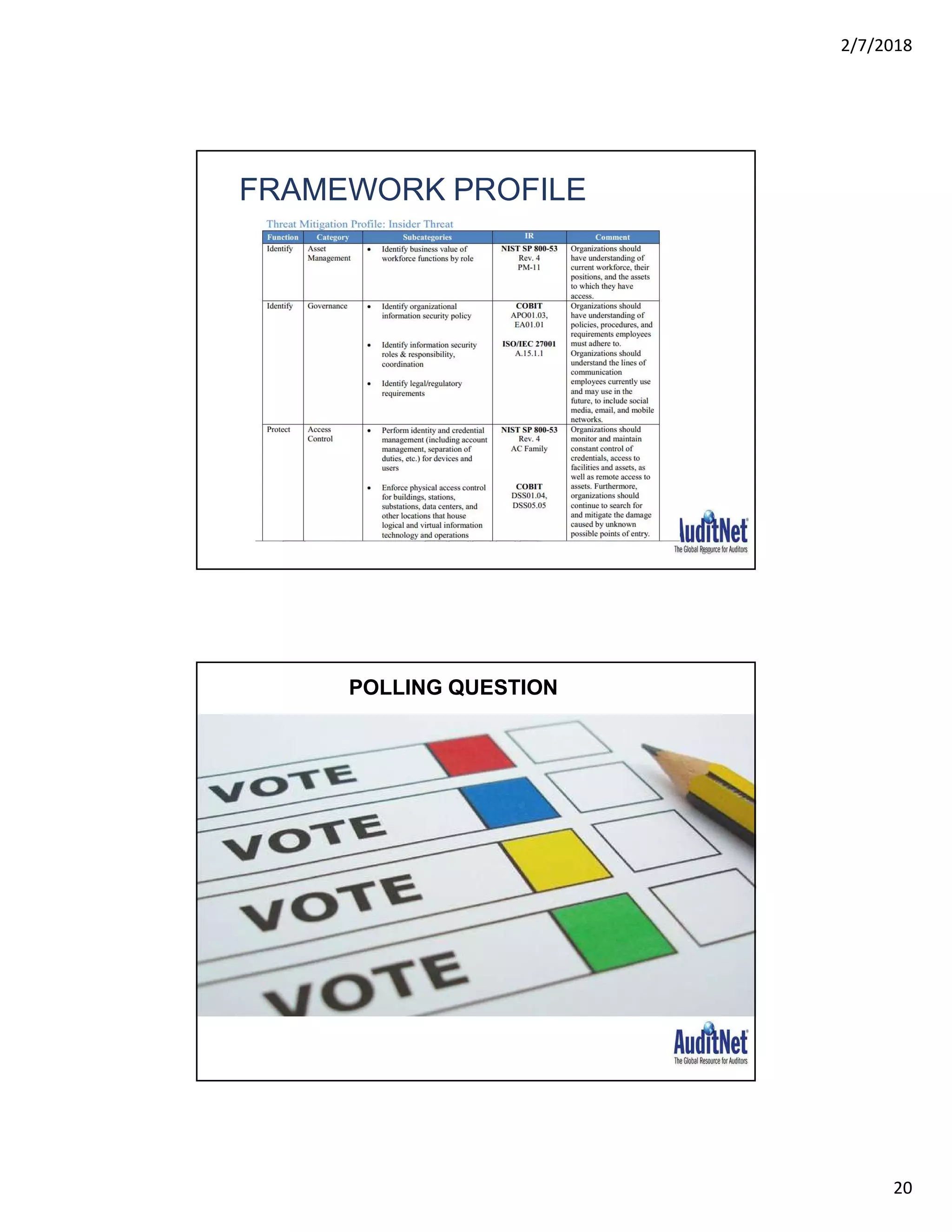
The document outlines a webinar hosted by AuditNet® featuring experts Richard Cascarino and Jim Kaplan discussing cybersecurity threats and preventive measures. Key topics include the current landscape of cyber threats, essential frameworks for cybersecurity, and critical vulnerabilities to web applications. The material emphasizes the importance of security awareness and the implementation of best practices to combat increasing cybercrime risks.