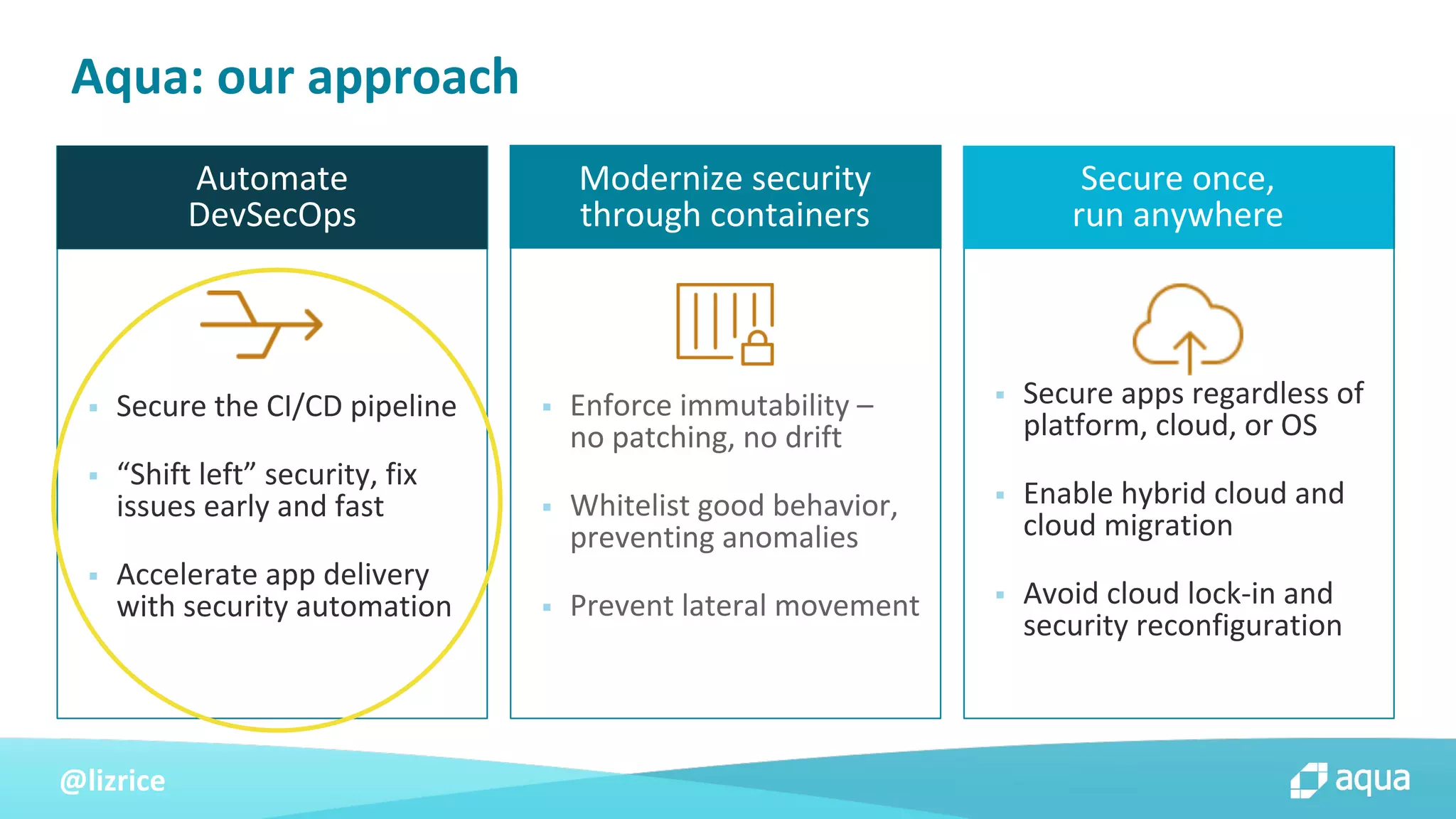
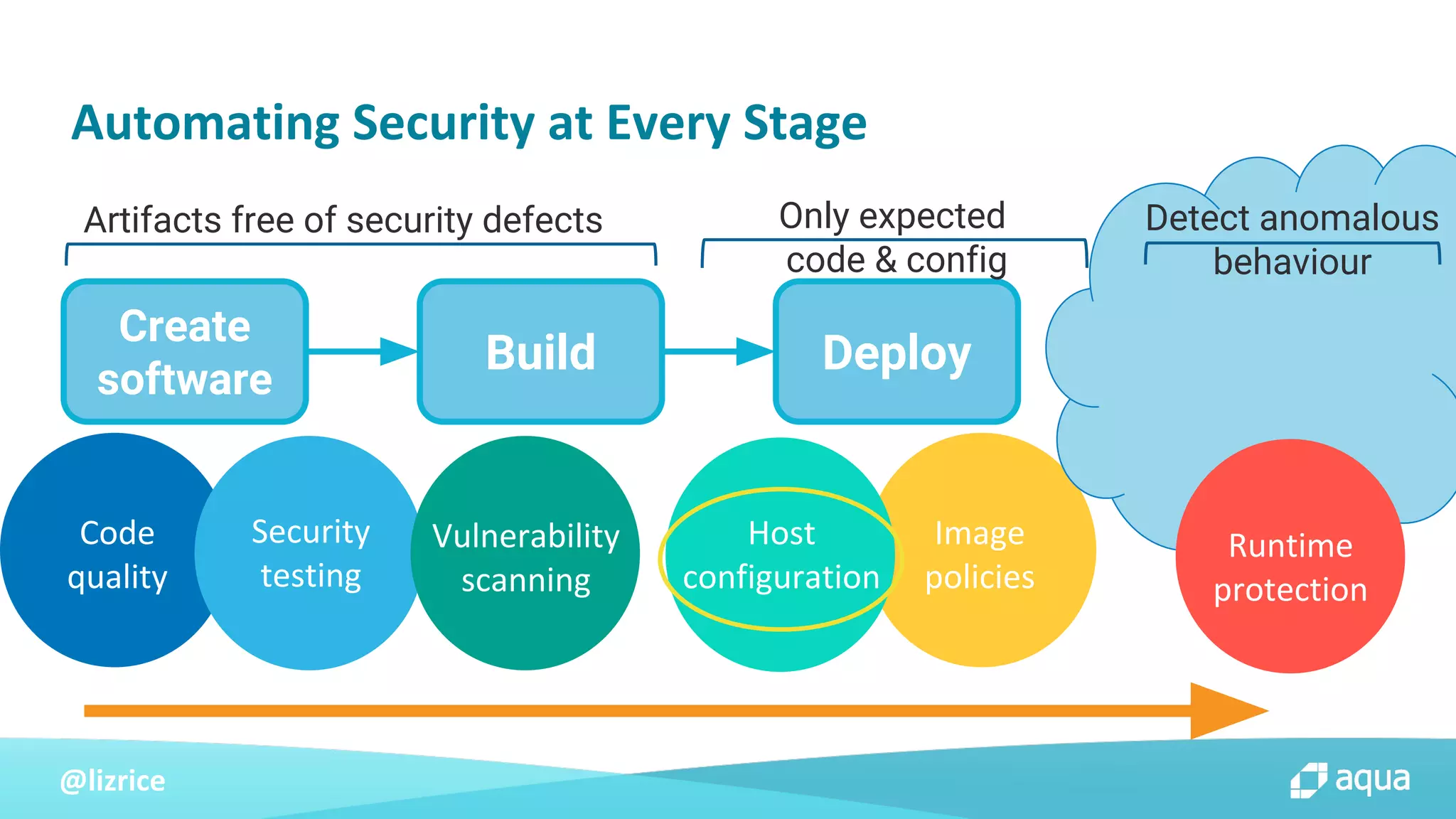
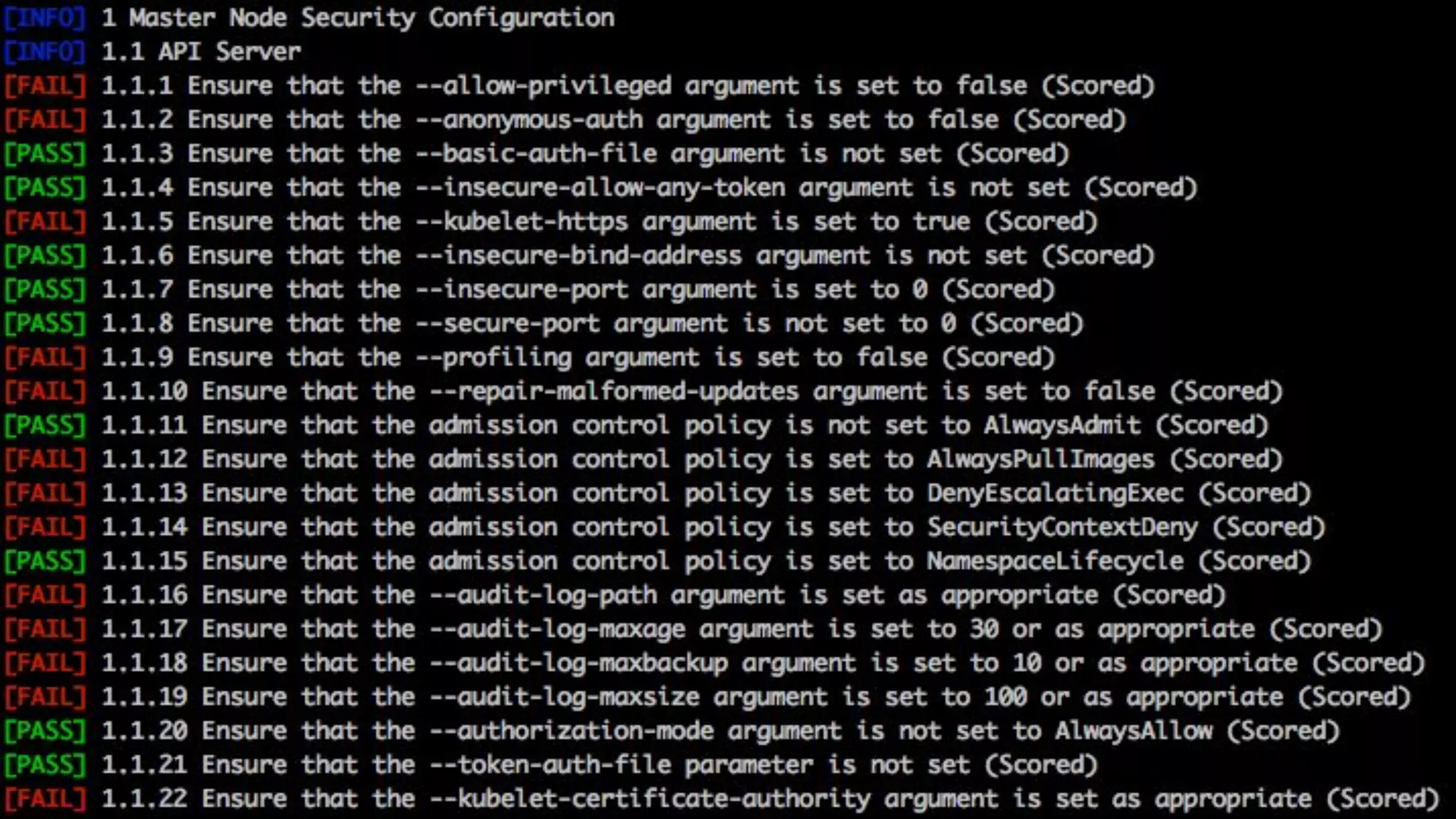
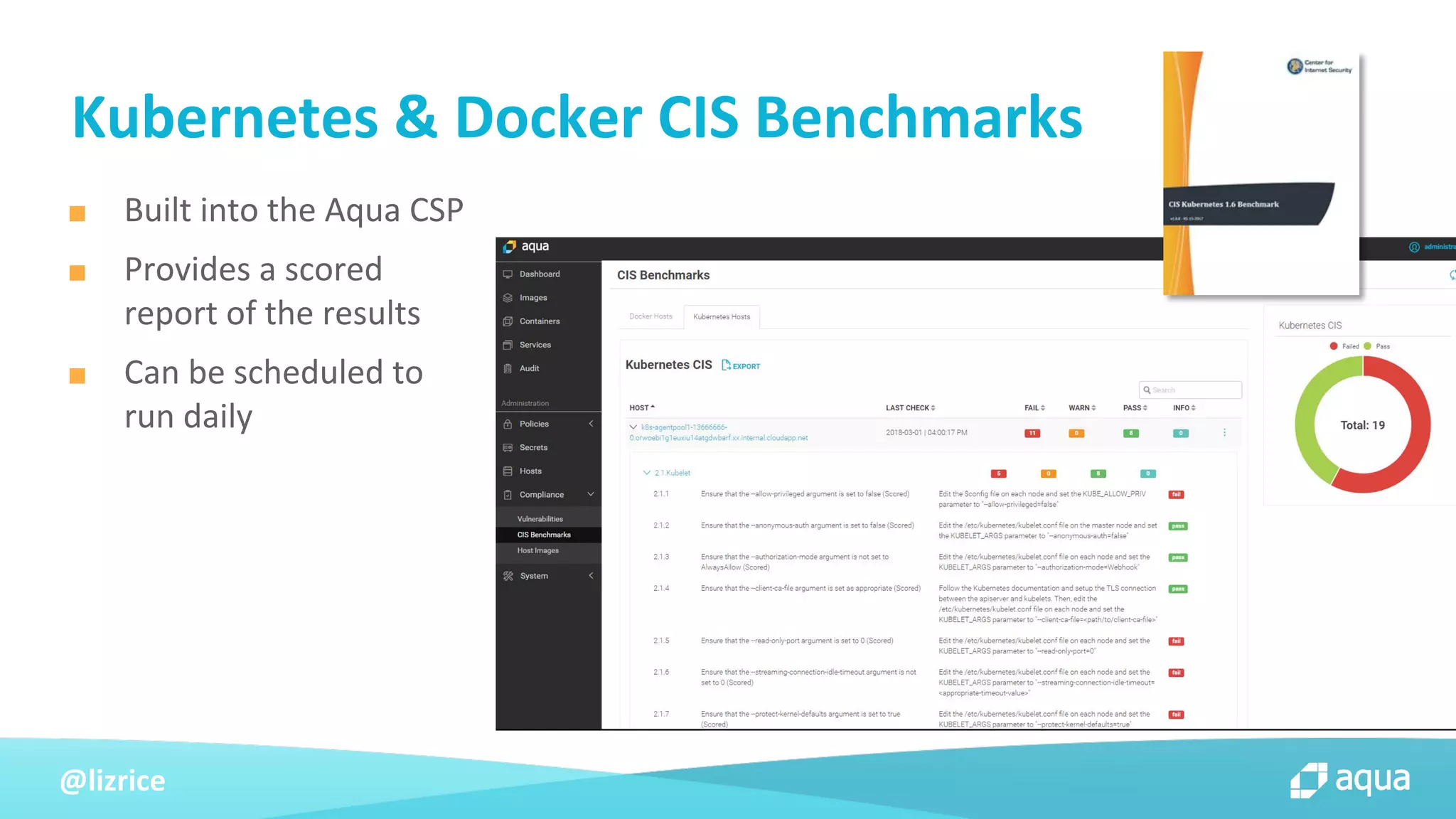
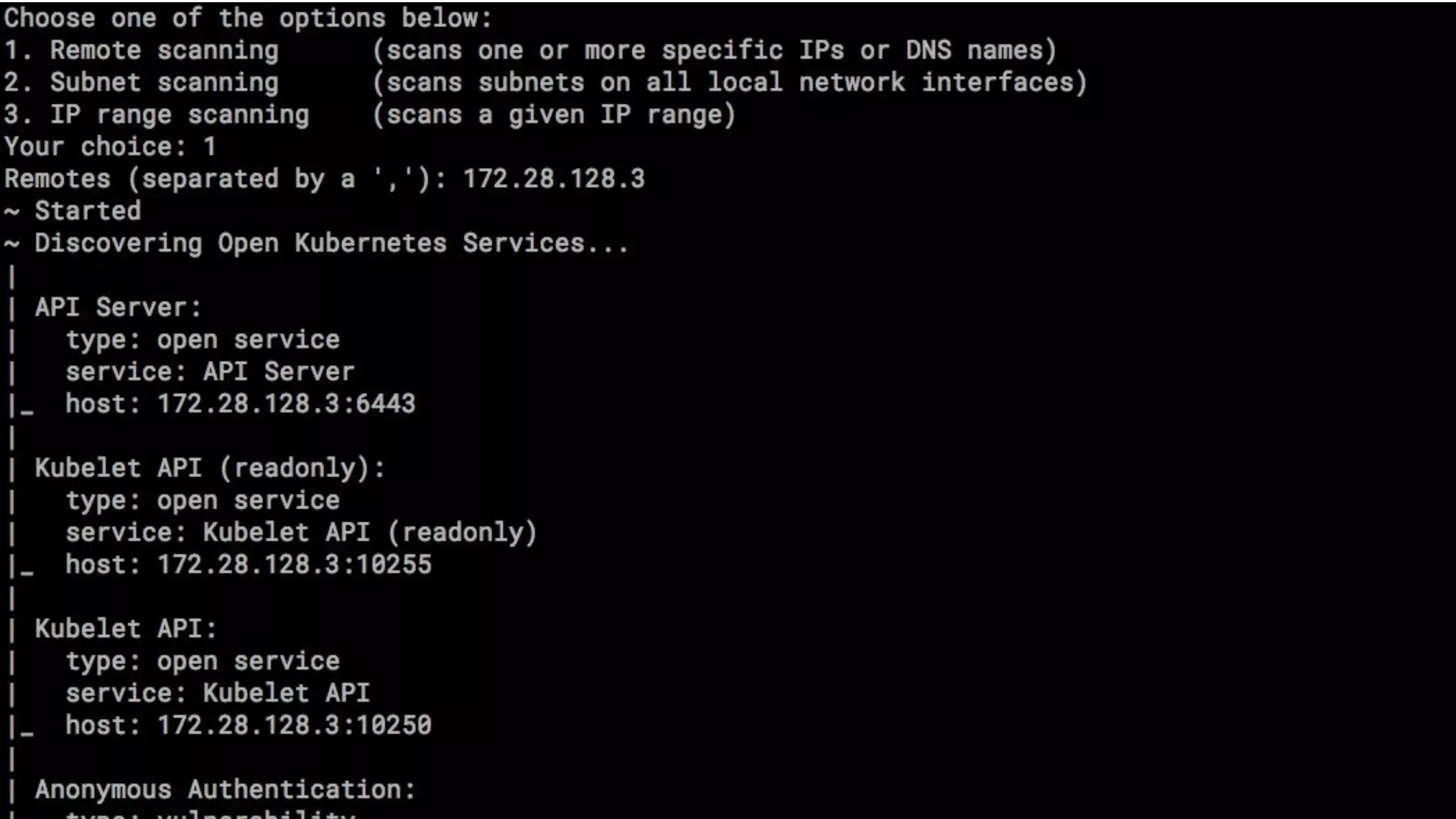
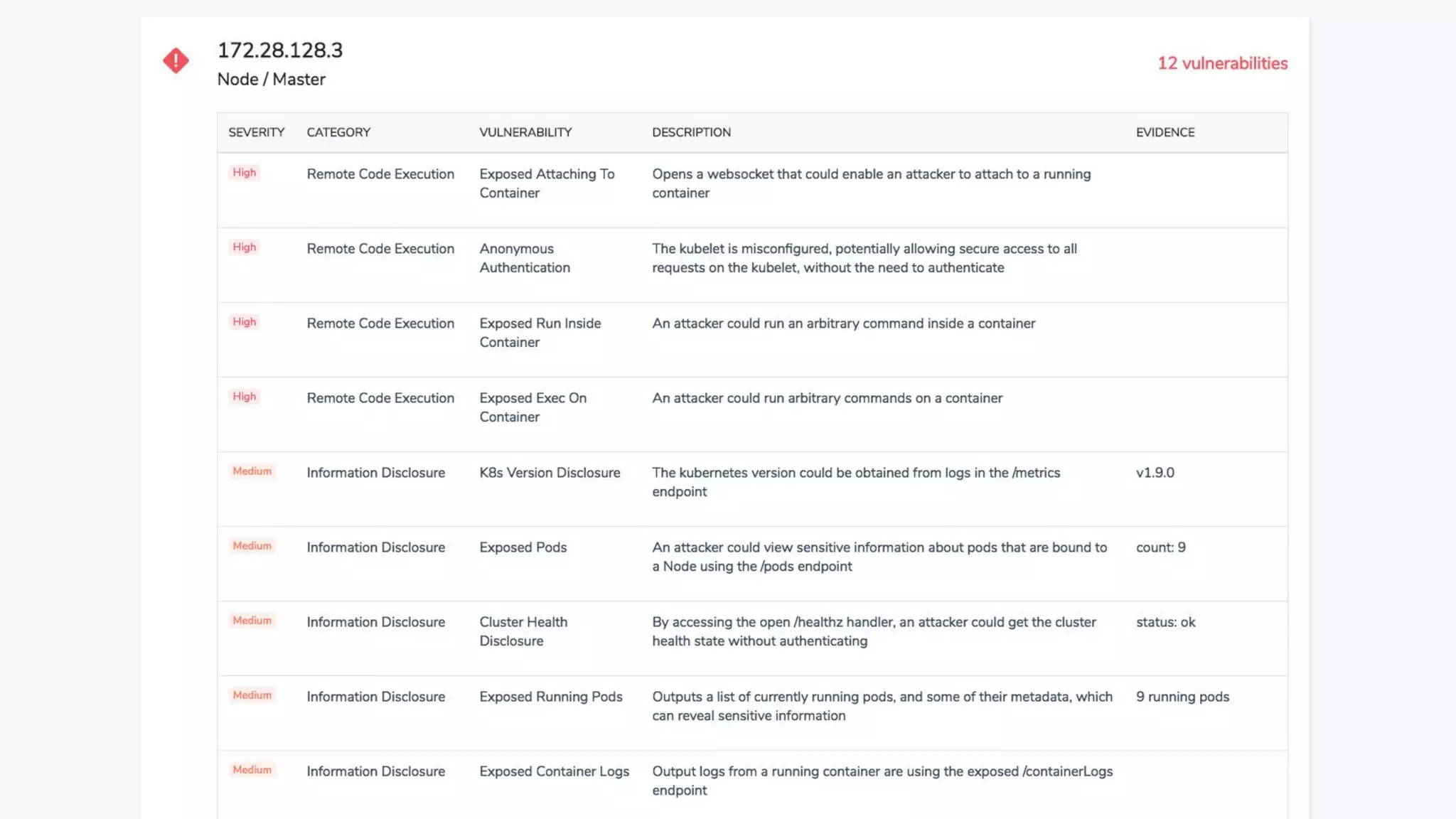
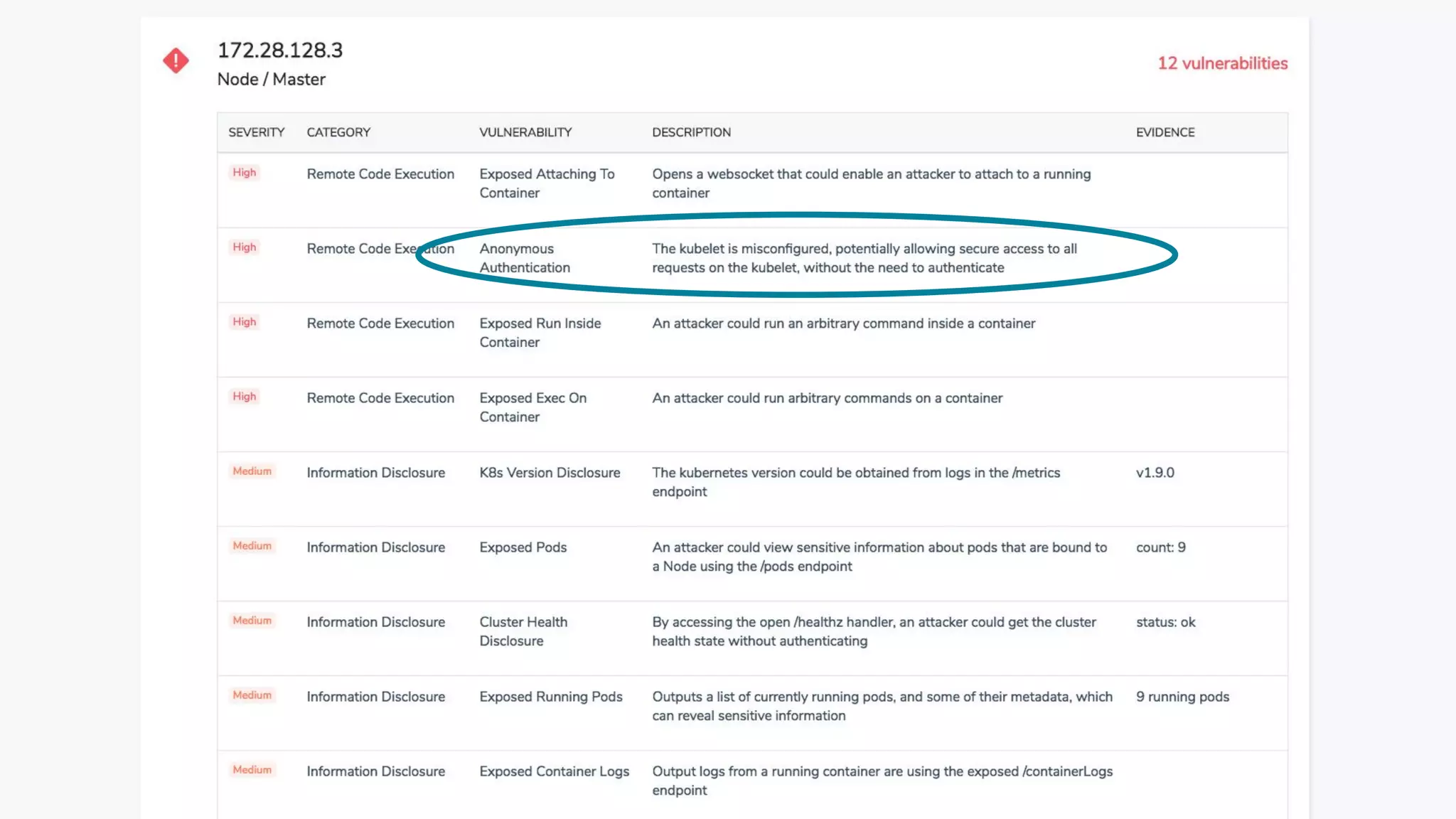
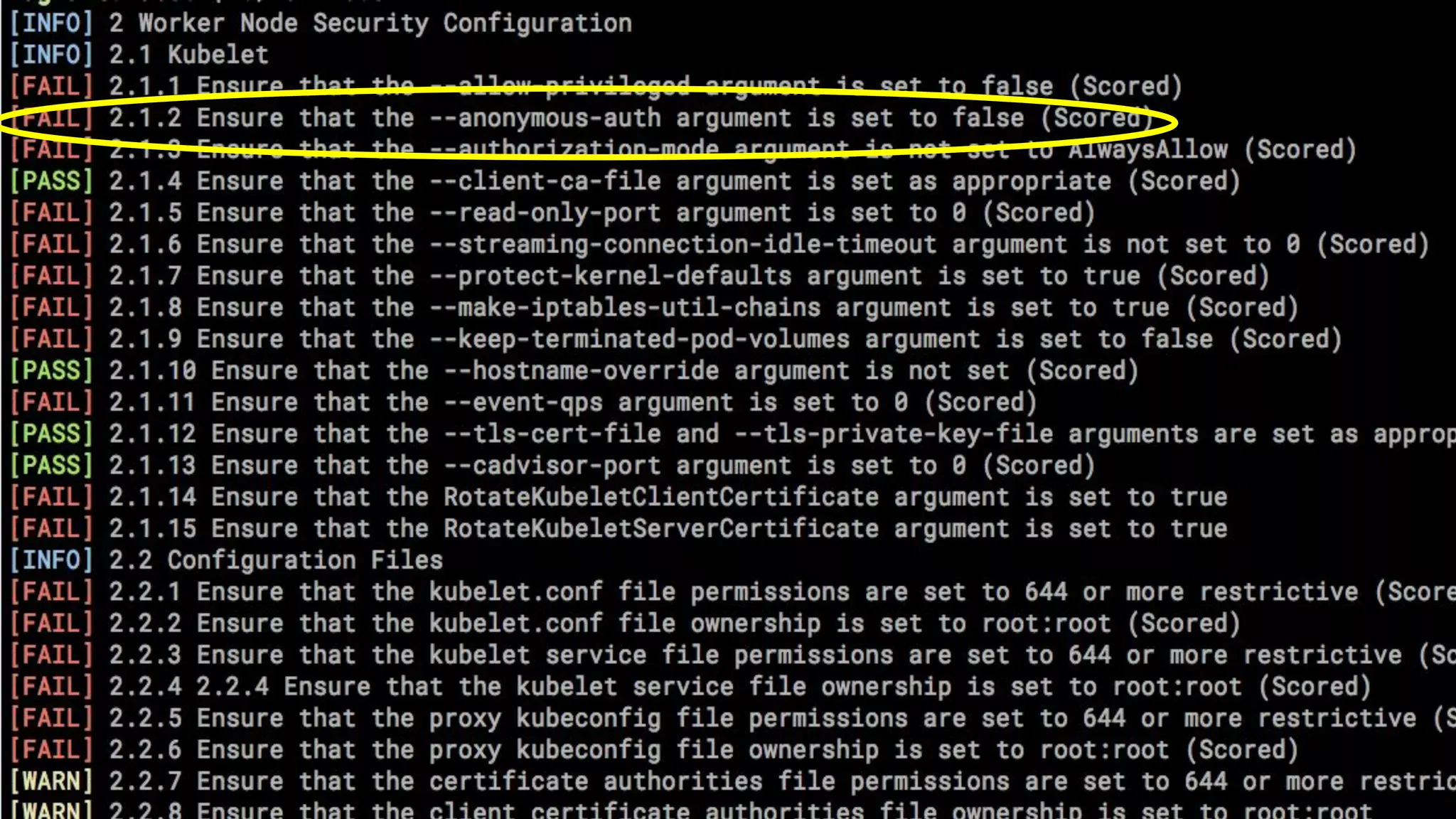
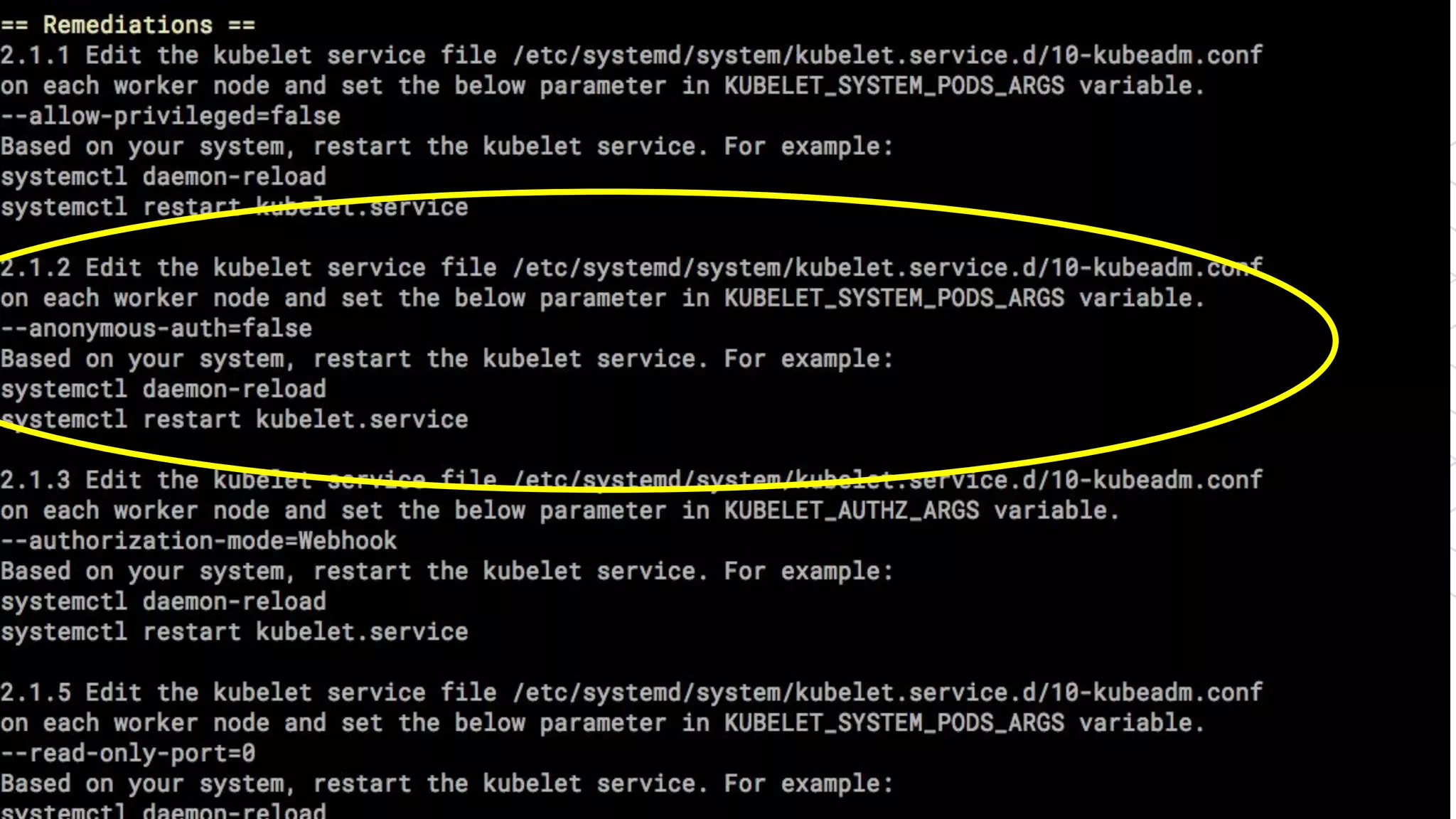
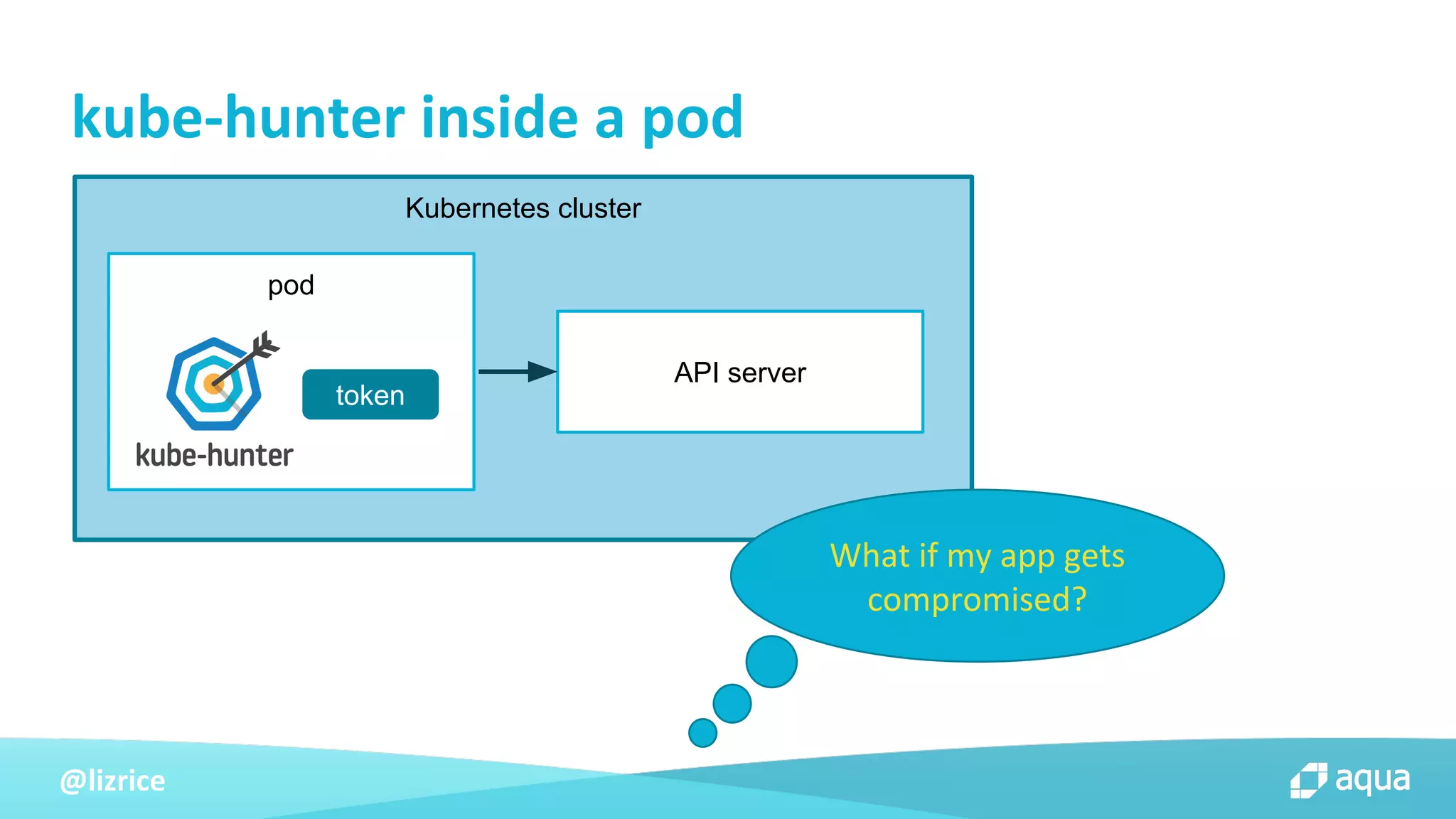
The document outlines security approaches for Kubernetes, including configuration settings, CIS benchmarks for testing, and penetration testing methods. It emphasizes the importance of automating security in the CI/CD pipeline, enforcing immutability, and using tools like kube-bench and kube-hunter for vulnerability assessment. The authors advocate for ongoing security evaluations and adjustments to protect applications across various platforms.