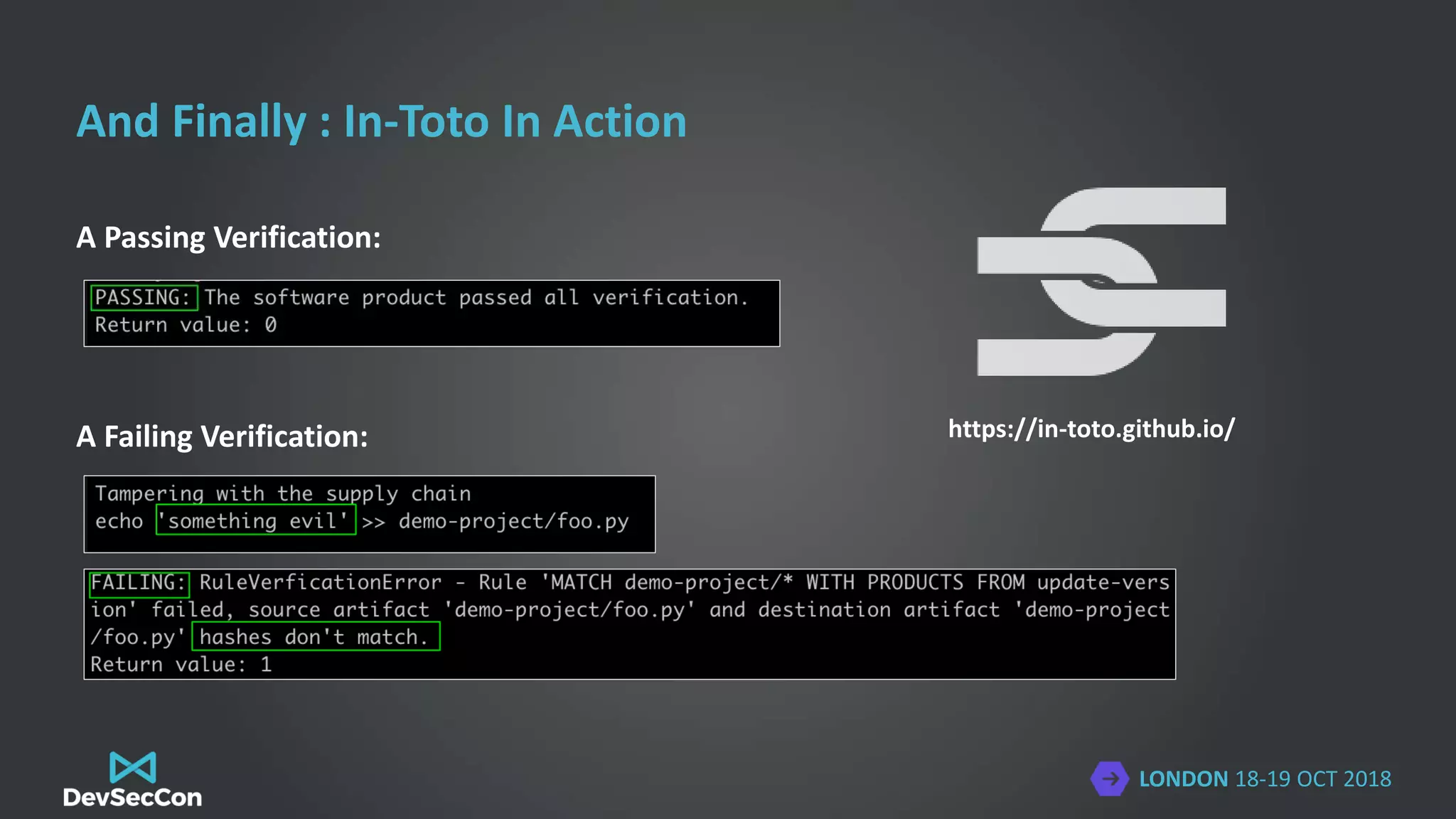
The document discusses the importance of securing software supply chains, highlighting vulnerabilities from third-party components and previous malware incidents like the CCleaner attack. It introduces frameworks like in-toto and TUF for enhancing integrity and security throughout the supply chain, emphasizing practices such as hardening build pipelines and managing dependencies effectively. The presenter, Colin Domoney, shares insights on maintaining rigorous security measures and integrating new technologies within development and operations processes.


































![LONDON 18-19 OCT 2018
In-Toto in a Jenkins Server
stage('Build') {
agent {
docker {
#image name here
}
}
steps {
withCredentials([#any credentials here]) {
in_toto_wrap(['stepName': 'Build',
'keyPath': "${WORKER_KEY}",
'transport': "redis://${REDIS_ENDPOINT}:6379"]){
#your actual step here
}
}
}
}
}](https://image.slidesharecdn.com/isyoursupplychainyourachillesheel-181105114156/75/DevSecCon-London-2018-Is-your-supply-chain-your-achille-s-heel-38-2048.jpg)









![LONDON 18-19 OCT 2018
[Last slide for thank you
message, links, etc]
@colindomoney](https://image.slidesharecdn.com/isyoursupplychainyourachillesheel-181105114156/75/DevSecCon-London-2018-Is-your-supply-chain-your-achille-s-heel-50-2048.jpg)