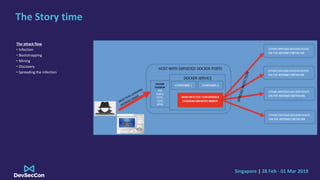
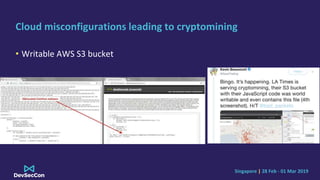
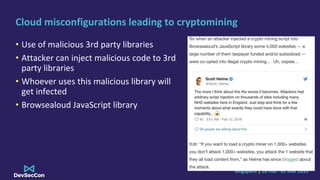
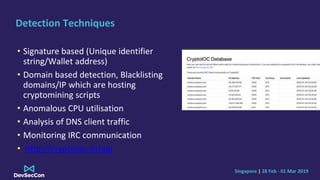
The document discusses cryptojacking, detailing its types such as browser-based and server-based mining, and highlights the attack flow including infection and spreading processes. It addresses cloud misconfigurations that facilitate these attacks, along with detection and evasion techniques used by such malware. Finally, it offers mitigation strategies to secure containerized environments and emphasizes the importance of continuously patching and properly configuring resources.