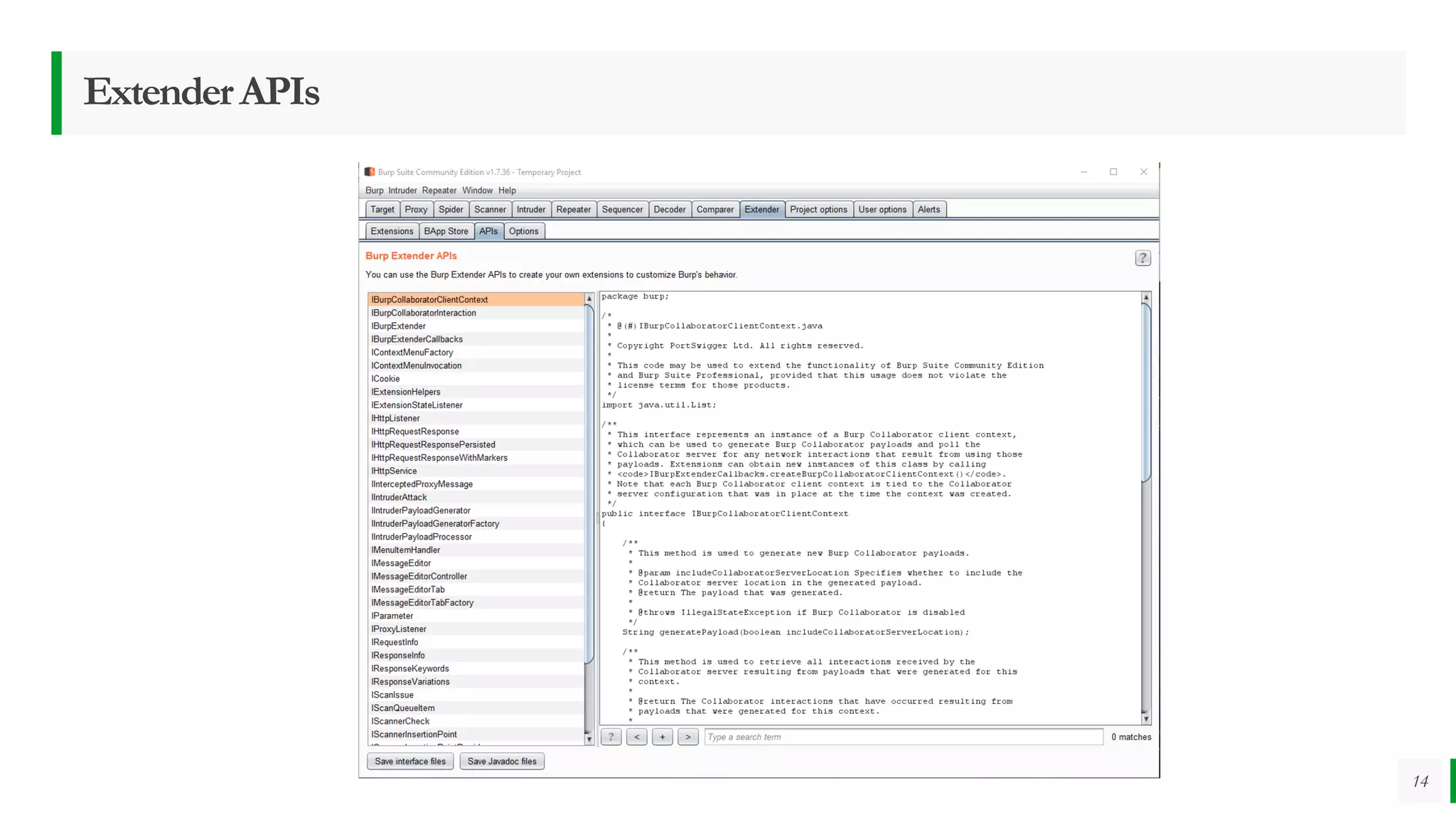
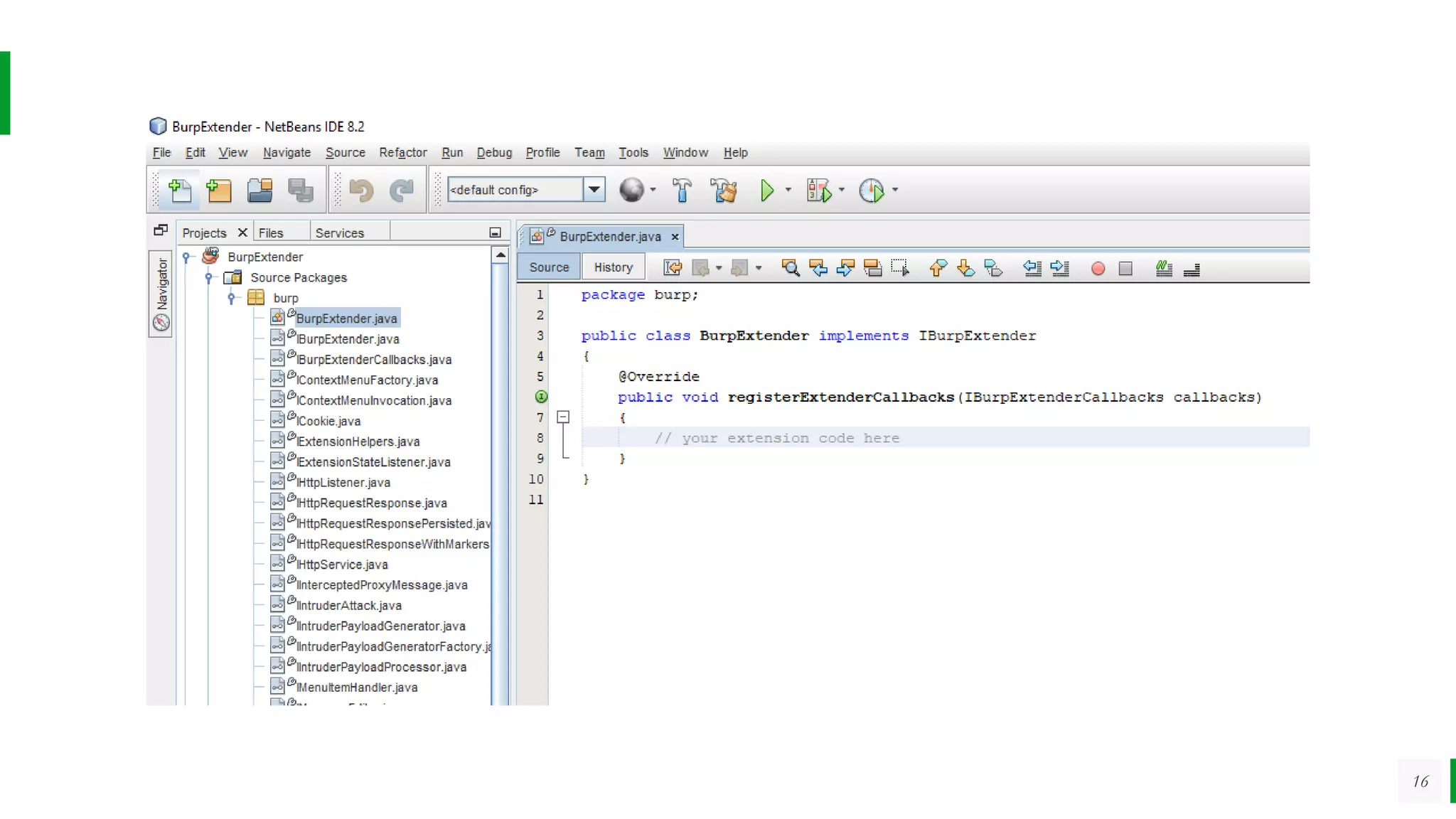
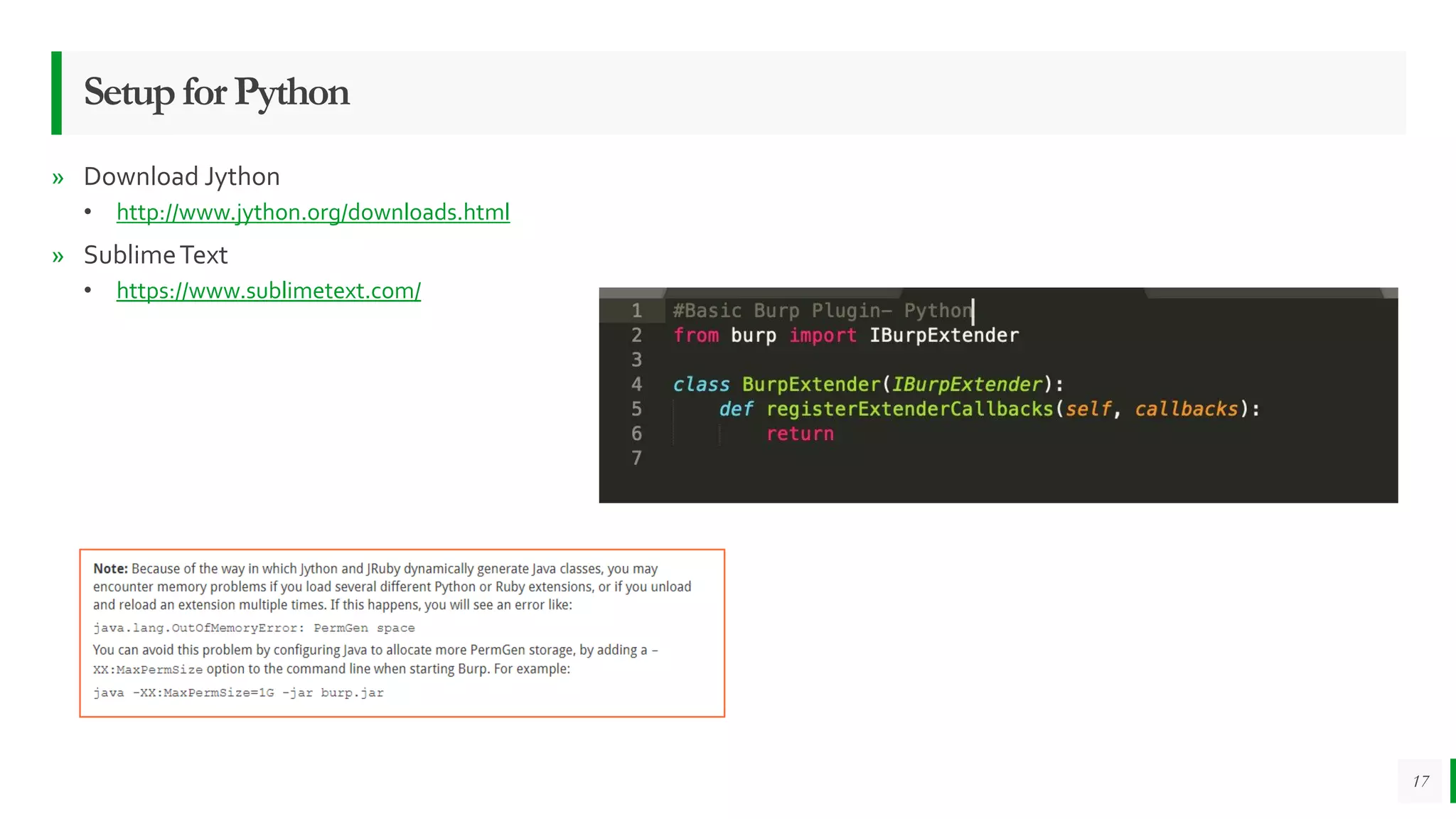
The Burp Suite Extension Writing Workshop conducted by Sanoop Thomas and Samandeep Singh focused on developing extensions for Burp Suite, an essential tool for application security testing. Participants learned about Burp's functionalities, development environment setup, and coding best practices, with hands-on exercises in Java and Python. The workshop aimed to enhance participants' skills in creating custom extensions while encouraging collaborative learning and troubleshooting.




![Someusefulmethods
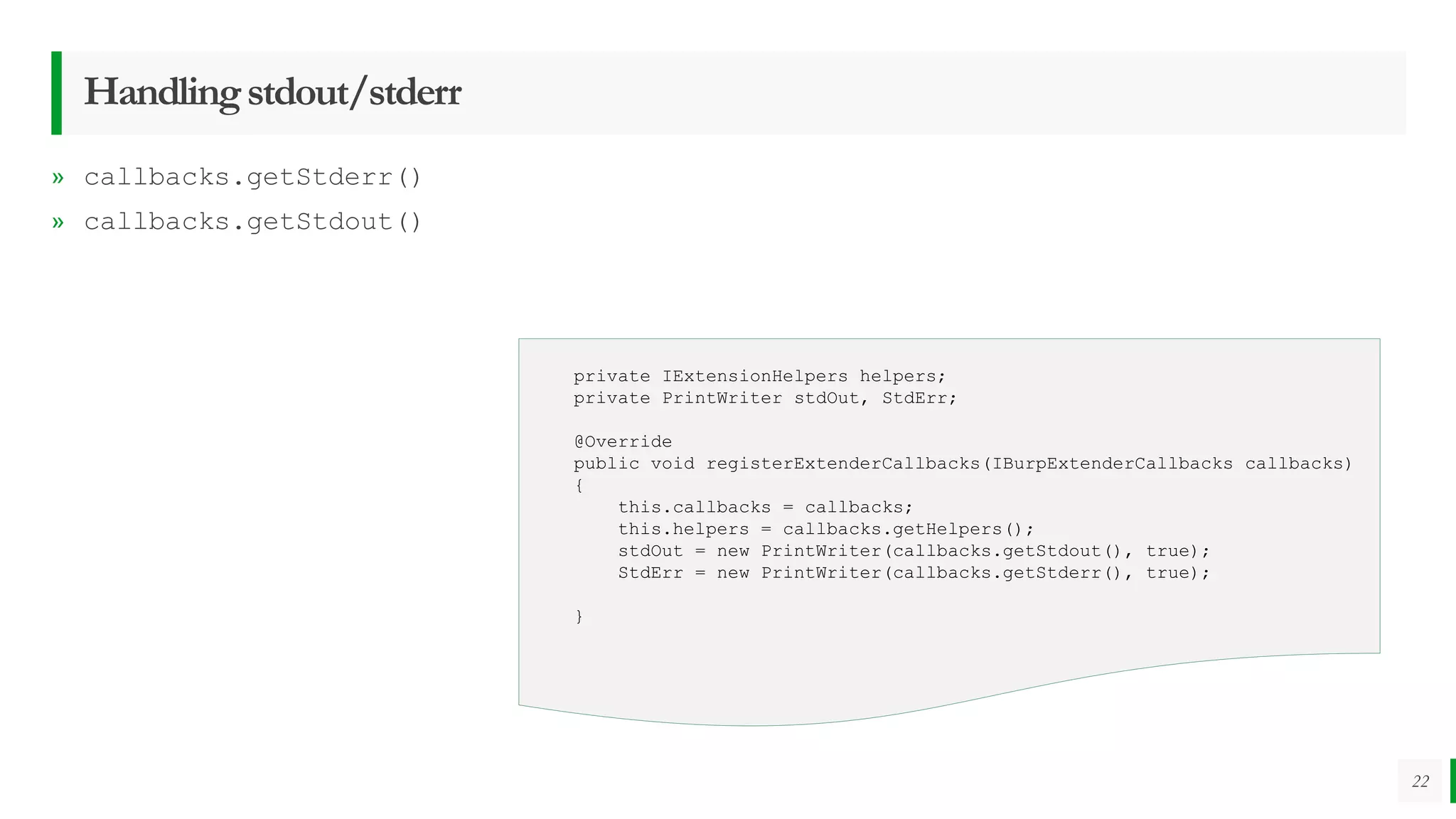
» IBurpExtenderCallbacks
• IHttpRequestResponse makeHttpRequest(IHttpService httpService, byte[] request);
• void registerHttpListener(IHttpListener listener);
• void registerProxyListener(IProxyListener listener);
» IExtensionHelper
• IRequestInfo analyzeRequest(byte[] request);
• IResponseInfo analyzeResponse(byte[] response);
• IParameter getRequestParameter(byte[] request, String parameterName);
• byte[] addParameter(byte[] request, IParameter parameter);
• byte[] toggleRequestMethod(byte[] request);
• byte[] buildHttpMessage(List headers, byte[] body);
» IRequestInfo
• List<String> getHeaders();
• List<IParameter> getParameters();
25](https://image.slidesharecdn.com/sanoopthomasburpextensionwritingworkshop-devsecconsingapore2019-190314123426/75/DevSecCon-Singapore-2019-Workshop-Burp-extension-writing-workshop-25-2048.jpg)