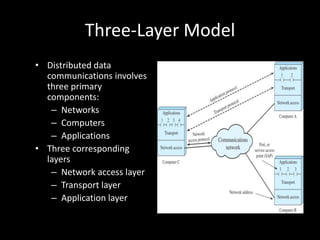
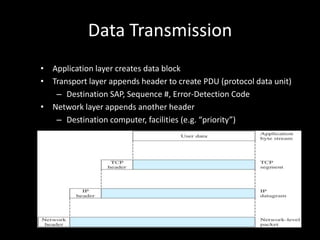
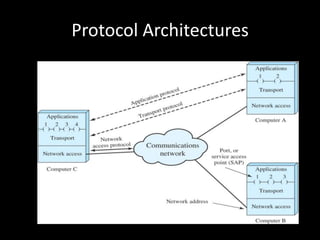
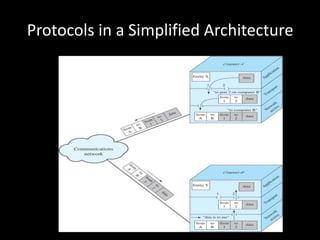
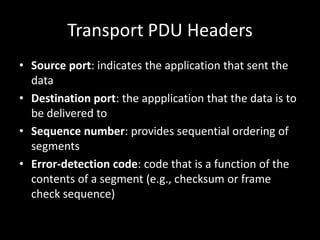
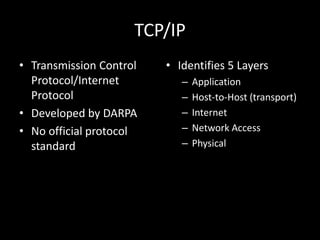
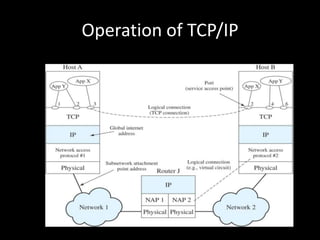
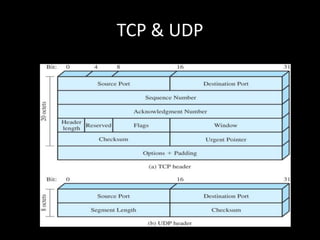
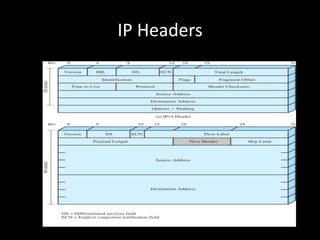
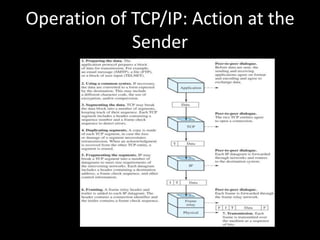
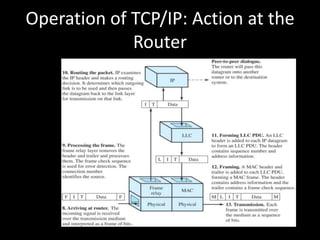
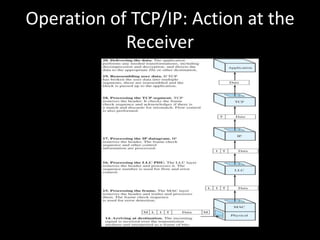
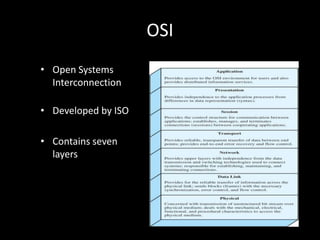
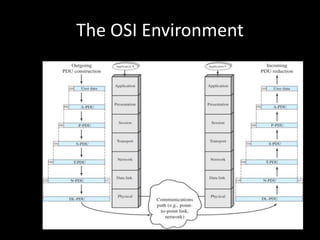
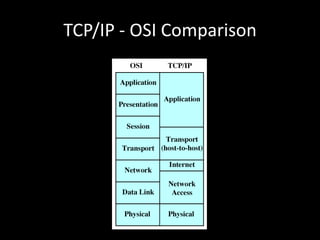
Allows applications on different systems to communicate by defining rules for exchanging data between them. It uses a modular approach that breaks tasks into subtasks handled by separate modules, making applications easier to develop and networks more flexible. The three-layer TCP/IP and seven-layer OSI models both describe a standardized architectural approach to protocol design.