This document discusses network architecture and design. It covers component architectures, addressing and routing architectures, network management architecture, performance architecture, and security architecture. Some key points include:
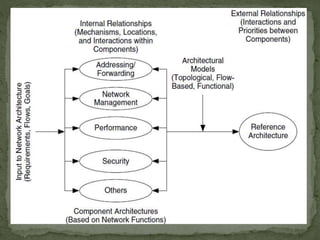
- Component architecture describes how network functions are applied using hardware and software mechanisms.
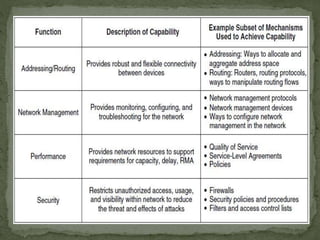
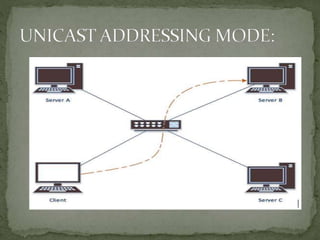
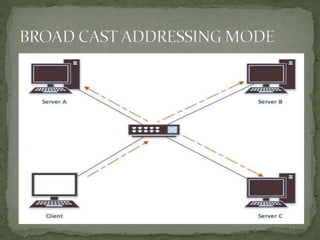
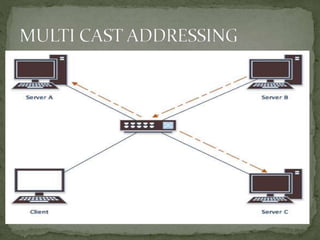
- Addressing involves applying identifiers to network devices, while routing learns connectivity and forwards packets. Common addressing mechanisms include subnetting, super-netting, dynamic addressing, and private/public addressing.
- Network management architecture provides functions for controlling, planning, and monitoring network resources using mechanisms like monitoring, instrumentation, and configuration.
- Performance architecture allocates network resources to users and applications using mechanisms like quality of service, resource control, service level agreements, and policies.