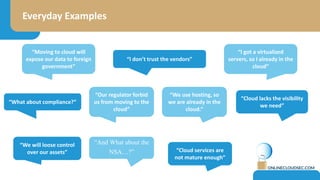
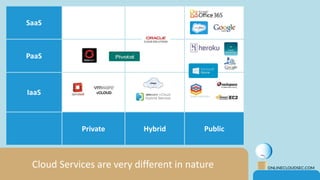
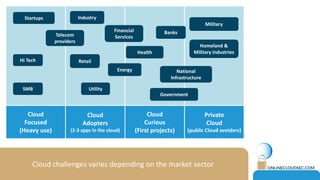
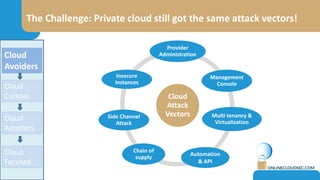
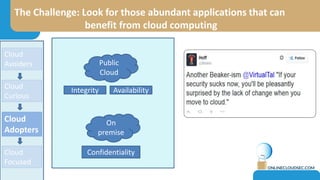
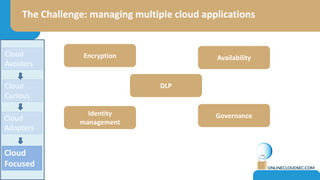
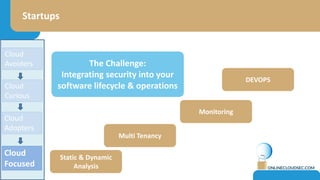
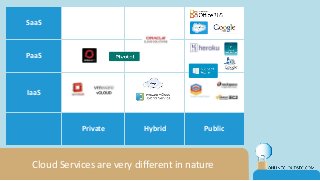
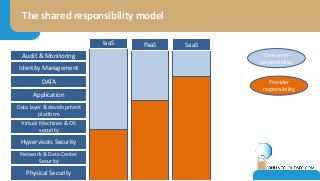
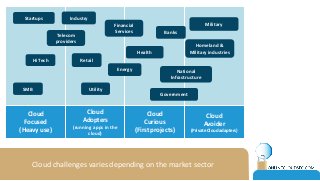
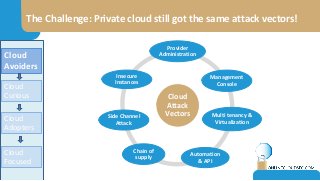
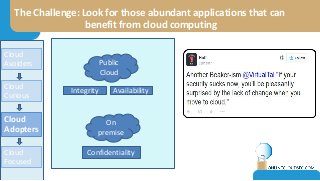
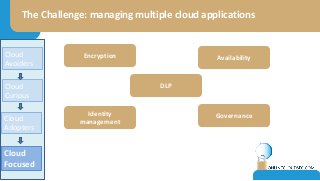
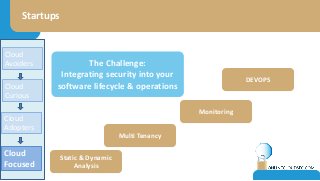
The document discusses the challenges of CISOs in adopting cloud computing, highlighting various perspectives from different stakeholders like CEOs, CFOs, and end-users. It outlines concerns about security, compliance, and vendor trust, while introducing the shared responsibility model between cloud providers and users. Additionally, it emphasizes the importance of building a cloud strategy, evaluating providers, and integrating security into software lifecycles.