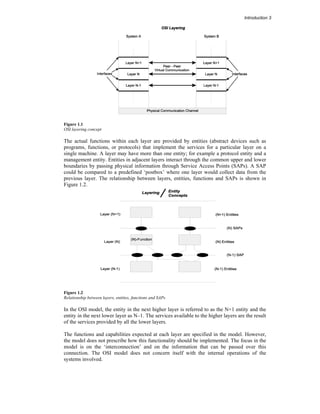
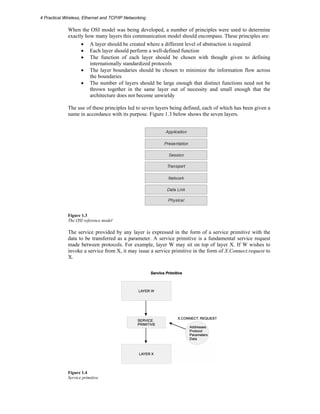
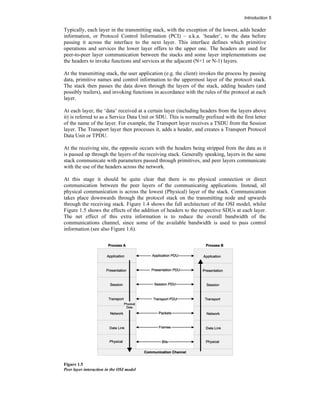
The document discusses the evolution of communication networks, focusing on local area networks (LANs), metropolitan area networks (MANs), wide area networks (WANs), wireless LANs (WLANs), and personal area networks (PANs). It emphasizes the importance of the Open Systems Interconnection (OSI) model, which structures network communication into seven distinct layers, facilitating standardization and interoperability among different network devices and protocols. Additionally, the document elaborates on Ethernet and TCP/IP technologies, highlighting their roles, functionalities, and recent developments in modern networking.