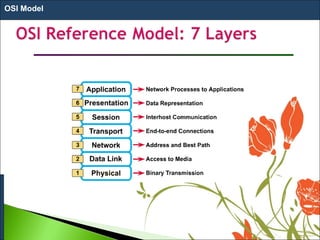
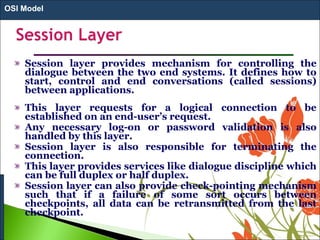
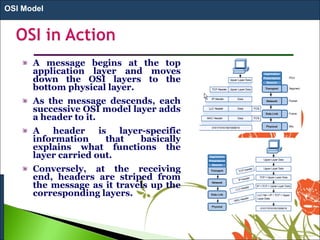
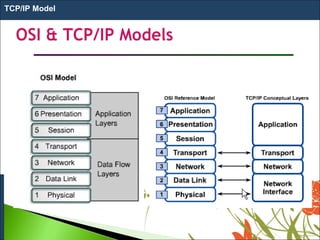
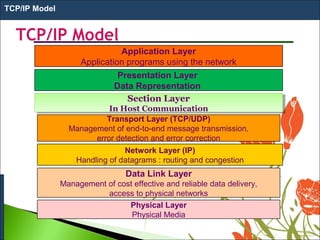
1. The OSI model is a standard reference model that defines the functions of a networking system by separating it into 7 layers.
2. Each layer has a specific role and provides services to the layer above it. Data moves down the layers at the sending device and up at the receiving device.
3. The model was developed in 1984 by ISO to provide a common way of designing and implementing communication between any two systems using a network. It aims to make networks more flexible, efficient and easy to maintain.