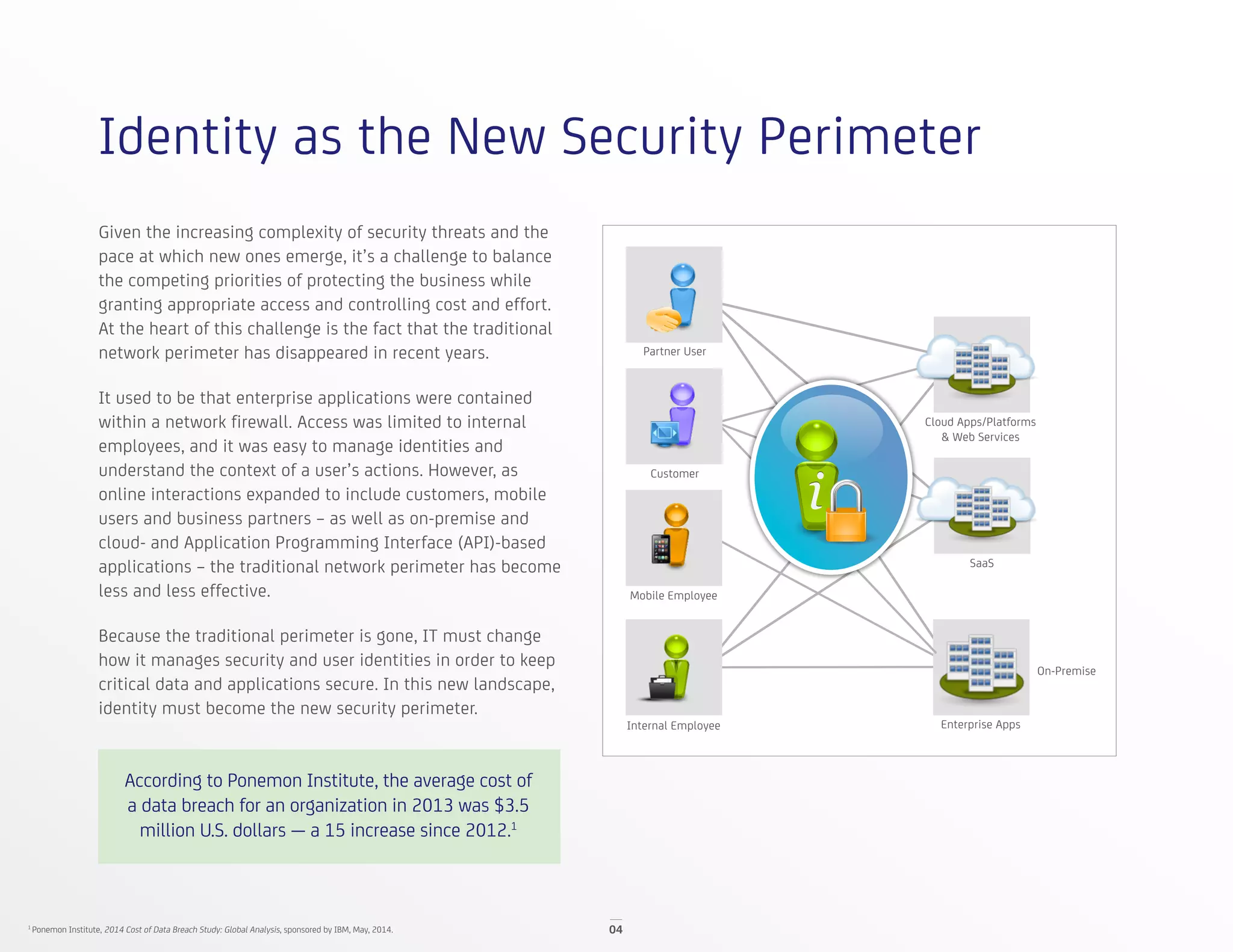
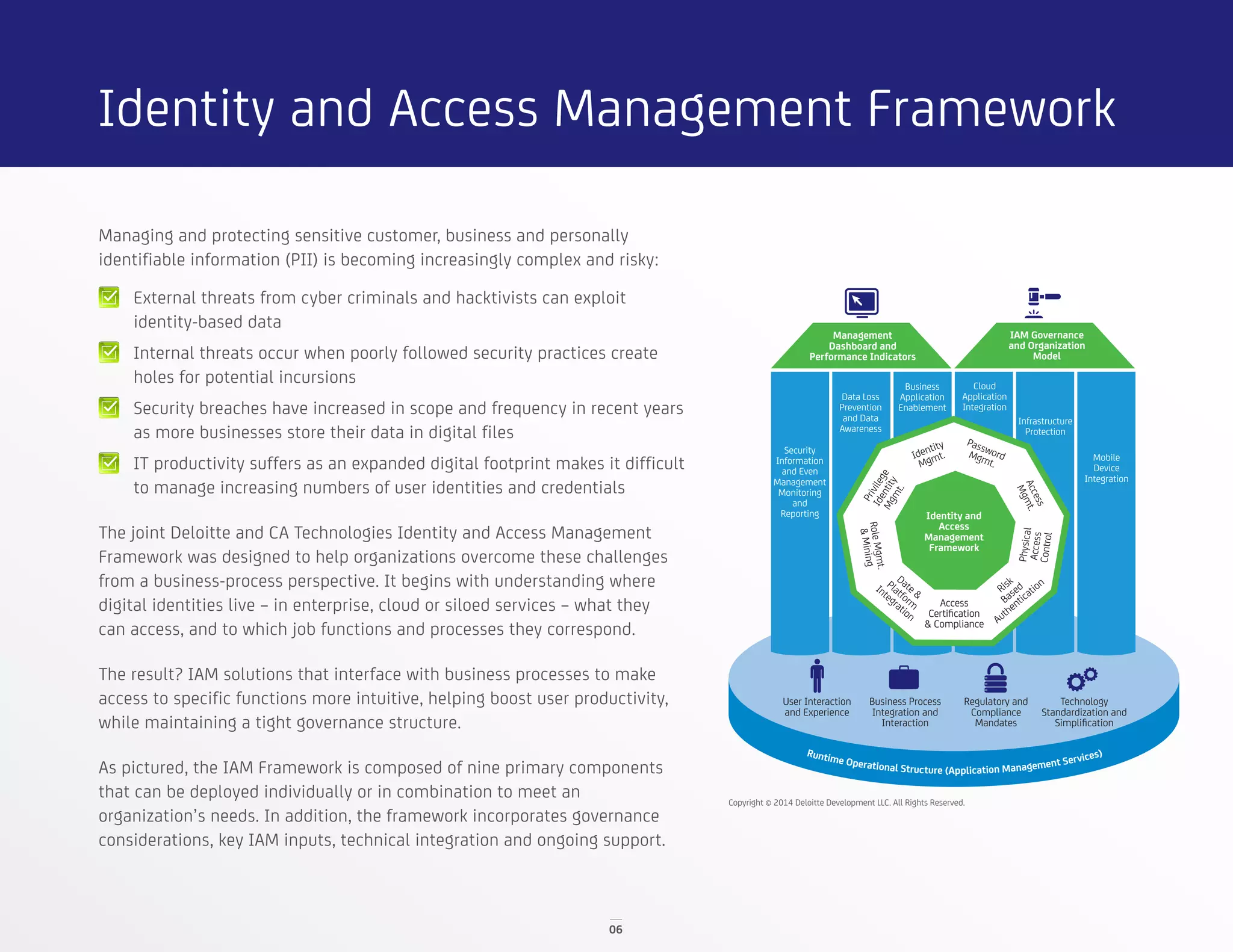
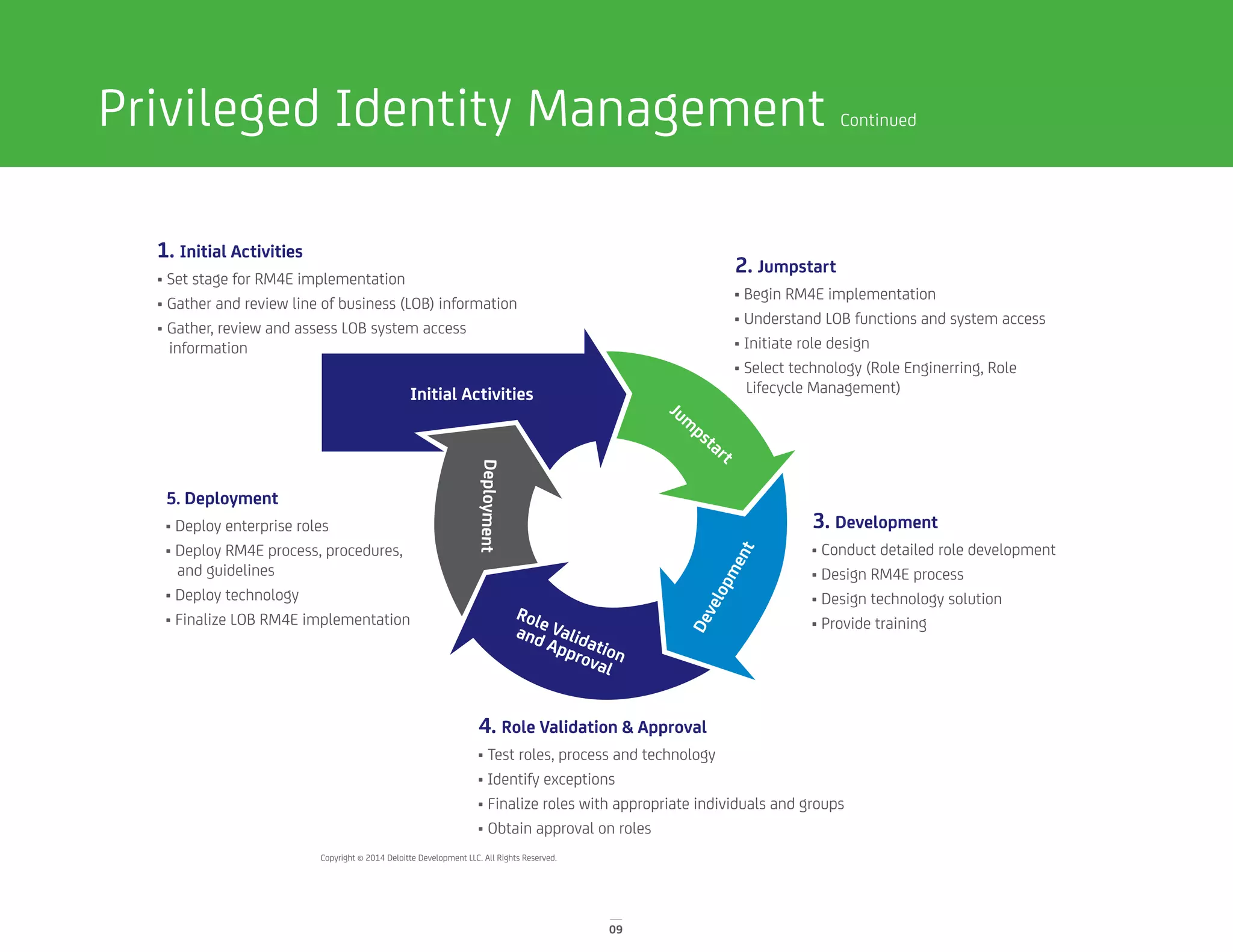
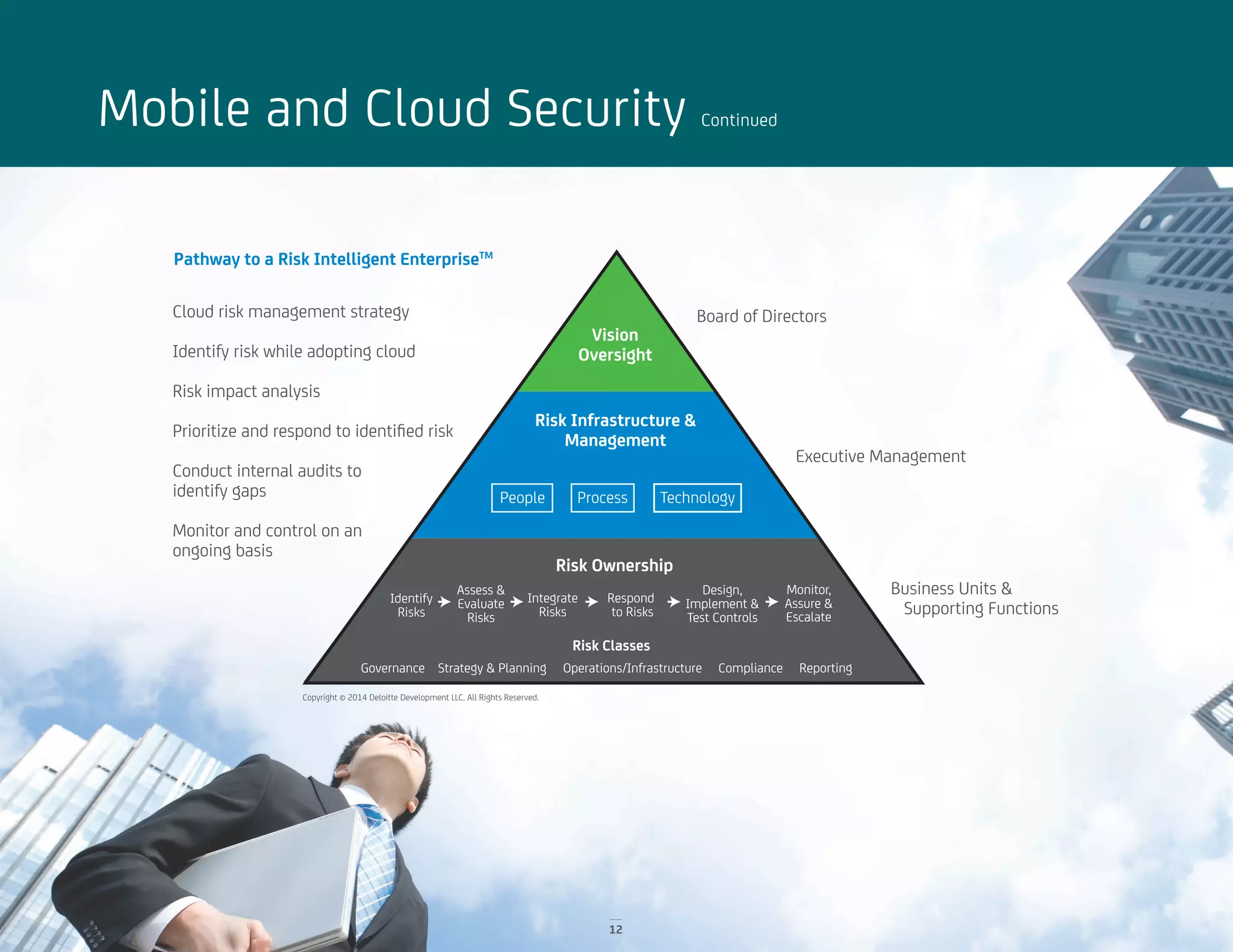
The document discusses identity and access management (IAM) solutions from CA Technologies and Deloitte to help organizations balance business growth and security. It describes the disappearing traditional network perimeter and need for a holistic IAM approach. Key solutions discussed include identity management, privileged identity management, advanced authentication, and mobile/cloud security. Case studies show how these solutions helped a tire company manage user access and a government agency implement a new application securely.