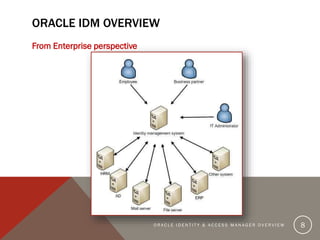
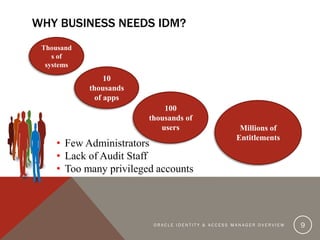
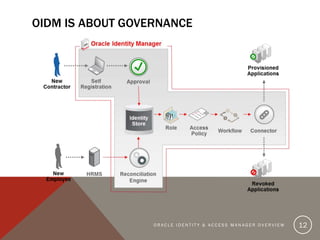
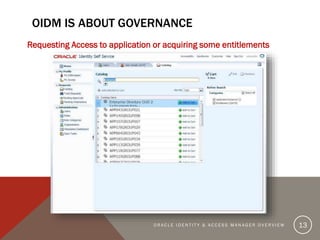
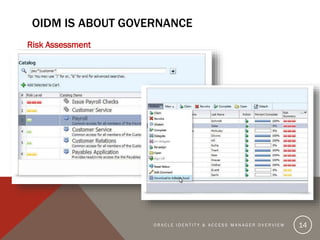
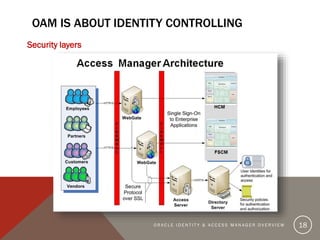
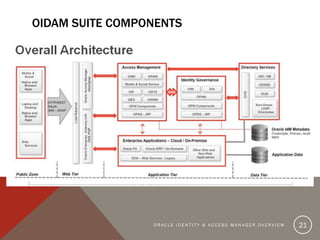
The document provides an overview of Oracle Identity and Access Management (OIDAM) from social, enterprise, and solution perspectives. It discusses Oracle Identity Manager (OIDM) which is about governance, including requesting access, risk assessment, and auditing. It also discusses Oracle Access Manager (OAM) which is about identity controlling by checking for authentication and authorization. The document outlines the overall OIDAM architecture and components and how OIDAM must be integrated as part of an enterprise solution.