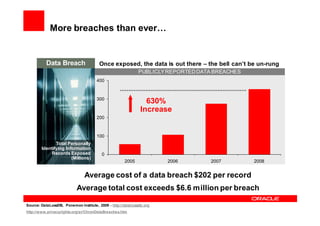
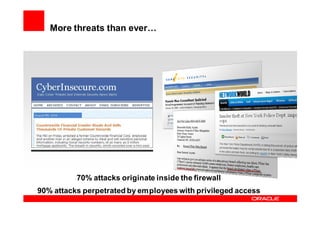
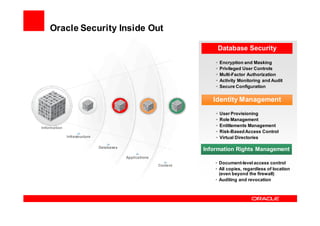
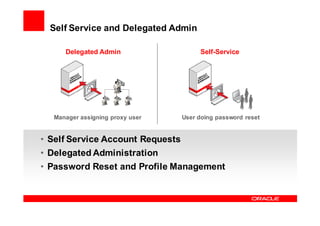
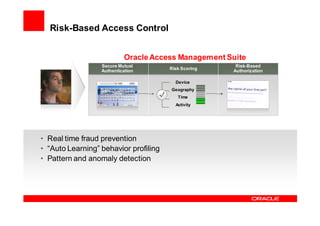
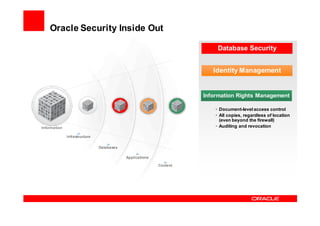
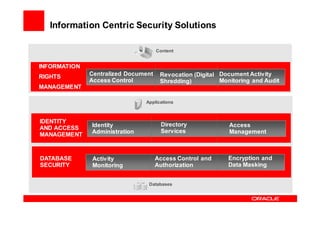
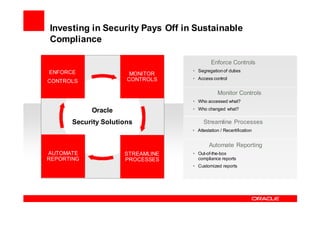
Oracle Identity Management improves security, compliance, and efficiency through centralized user provisioning, access management, and audit reporting. It enforces consistent security policies across systems, automates user provisioning and access based on defined roles, and streamlines compliance reporting to reduce costs.