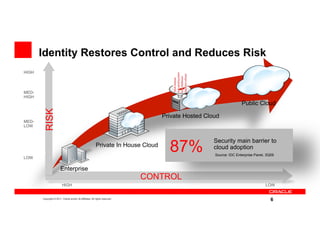
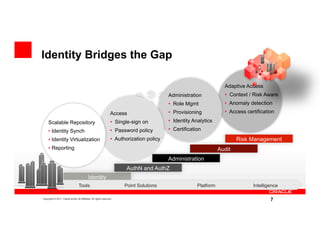
The document discusses key security considerations for cloud computing. It identifies top cloud security concerns such as access from mobile devices and identity management. It evaluates best practices for assessing a cloud provider's security and discusses how identity management can reduce risks and bridge security gaps. The presentation then provides an example of Oracle's identity and authentication cloud service and its features for multi-factor authentication and anti-fraud. It concludes with biographies of the cloud security executive panel speakers.