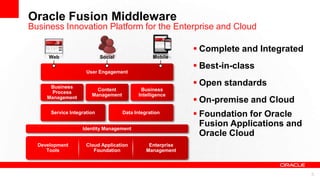
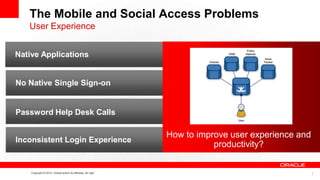
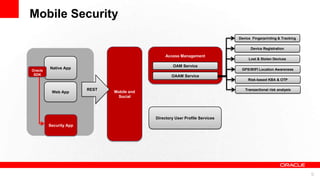
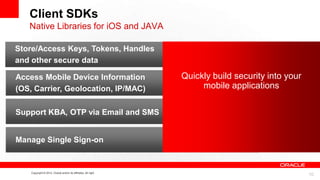
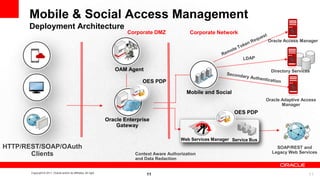
This document discusses developing secure mobile applications. It provides an overview of Oracle Access Management which can be used to centrally manage mobile security. Oracle Access Management includes features for mobile security, social single sign-on, cloud access, and support for standards. It also provides client SDKs to help build security into native mobile apps and manages single sign-on. The document outlines a deployment architecture and is followed by a partner presentation and developer demo of Oracle's mobile security solution.