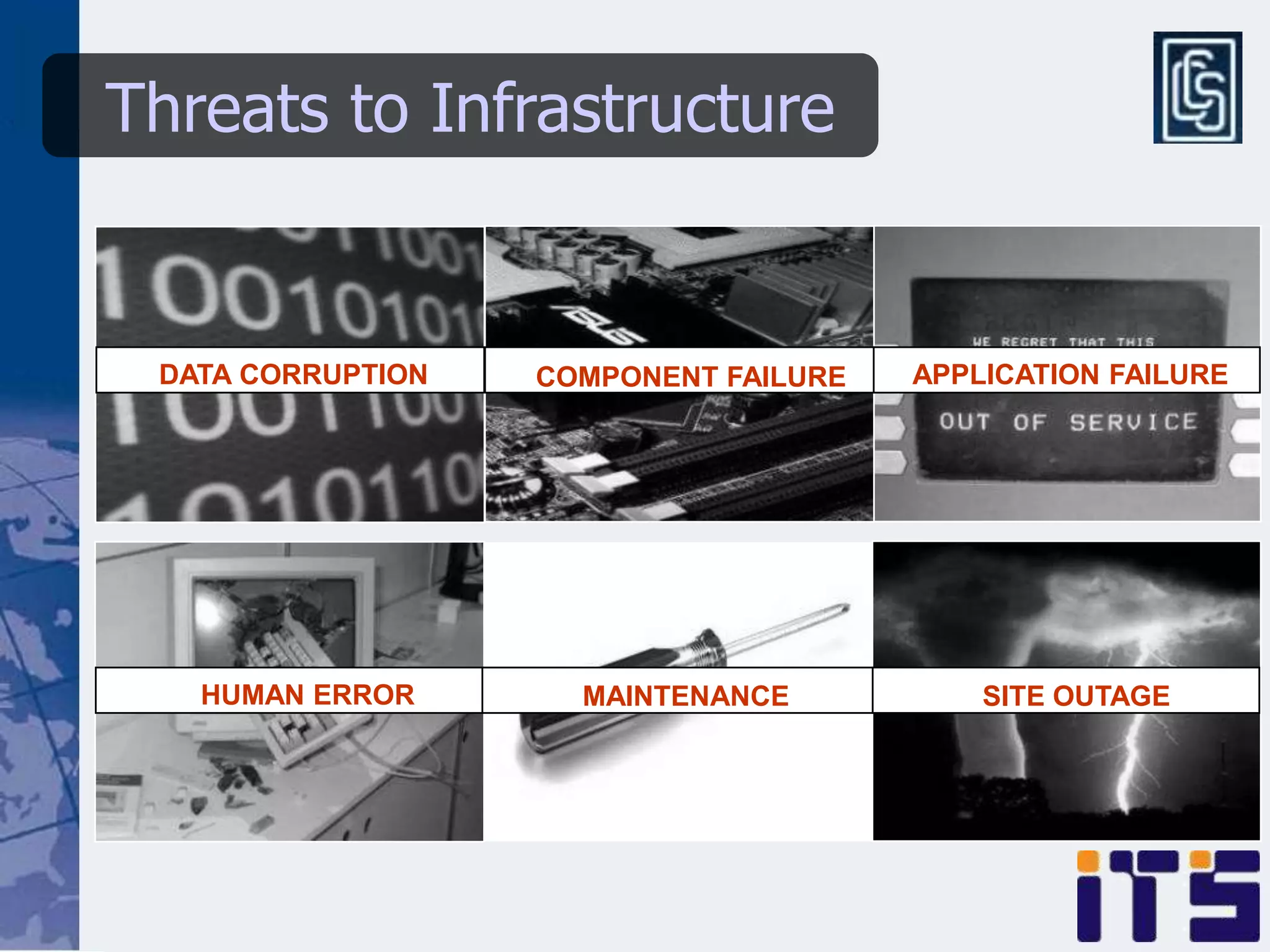
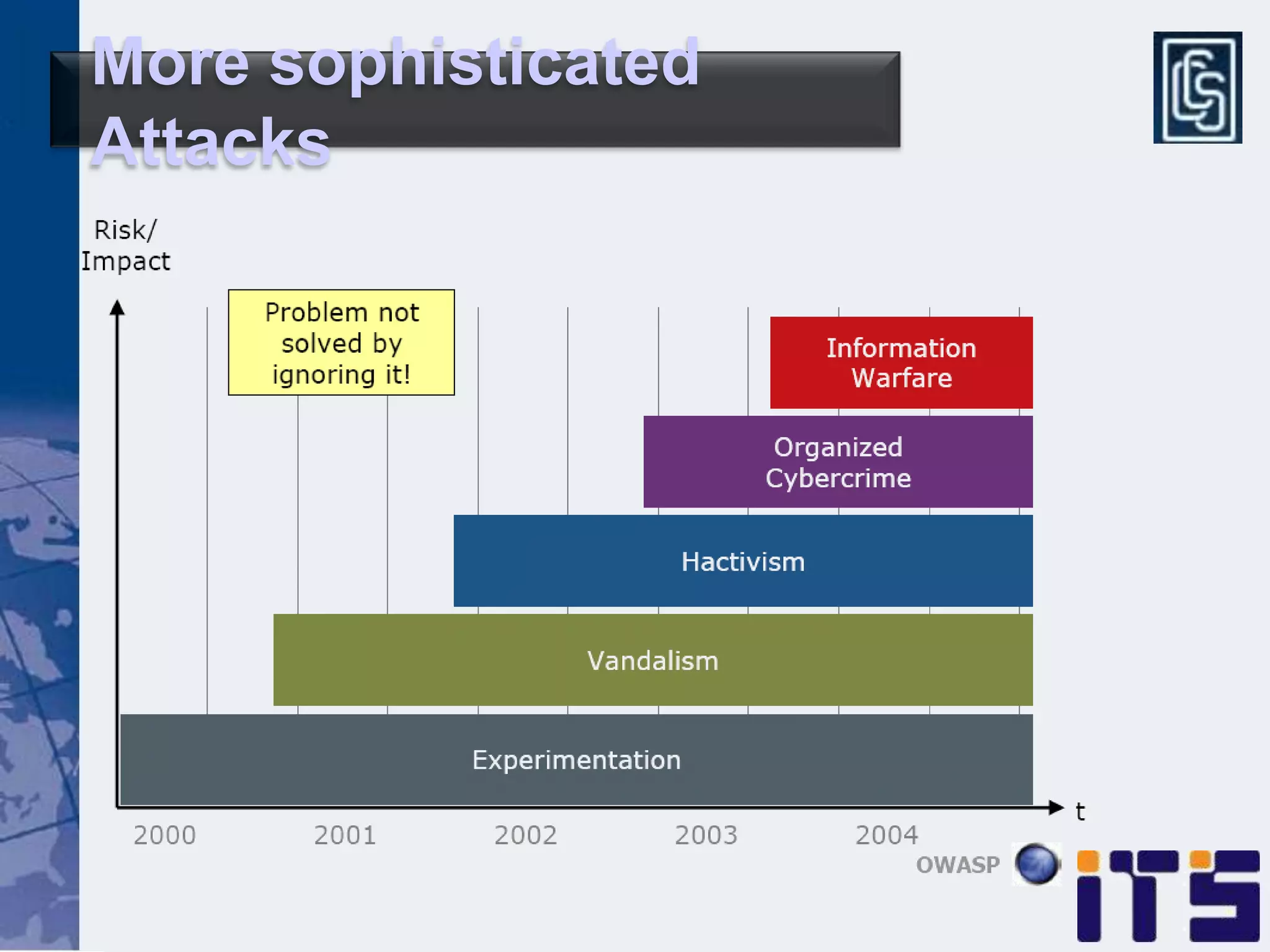
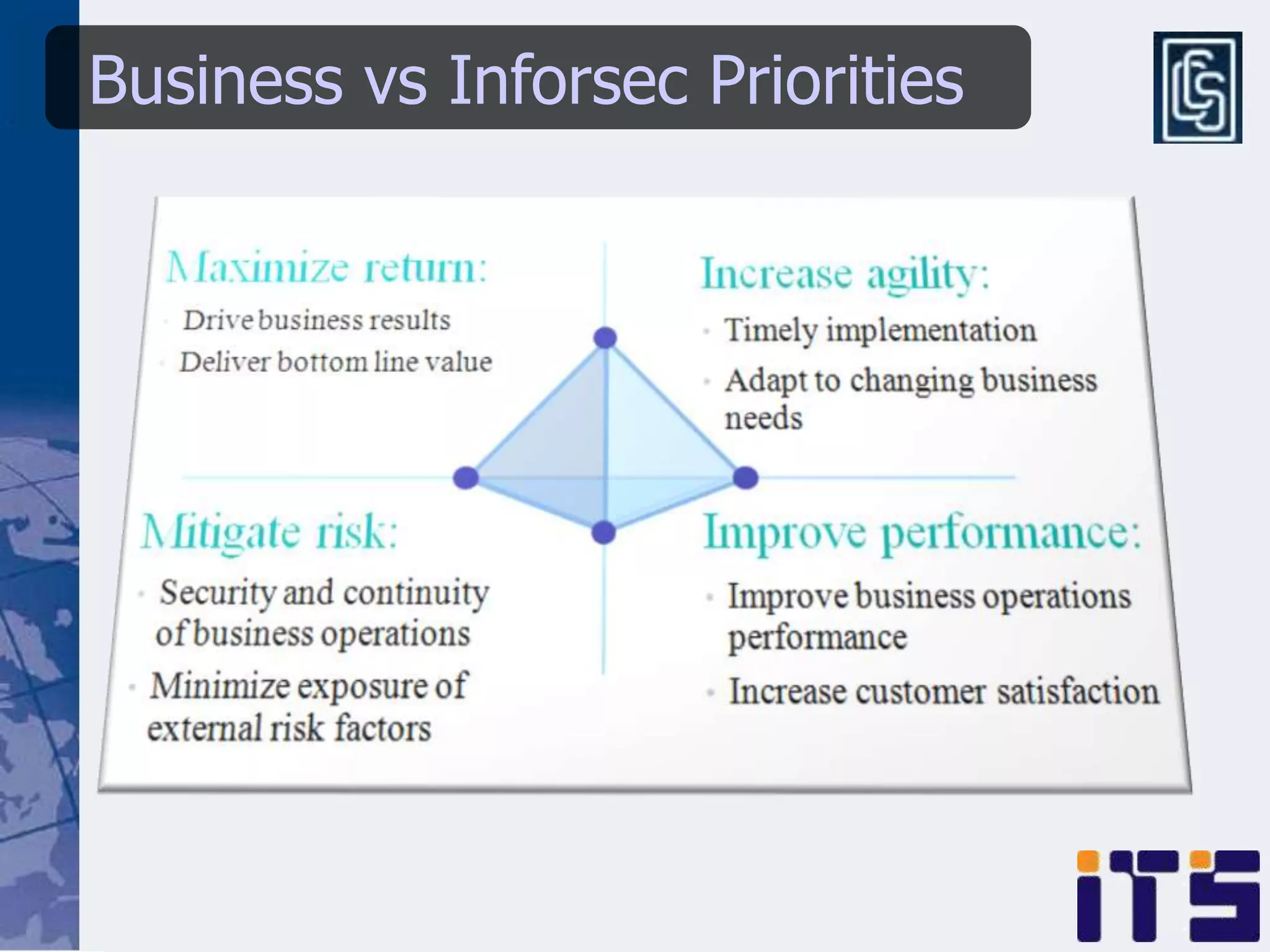
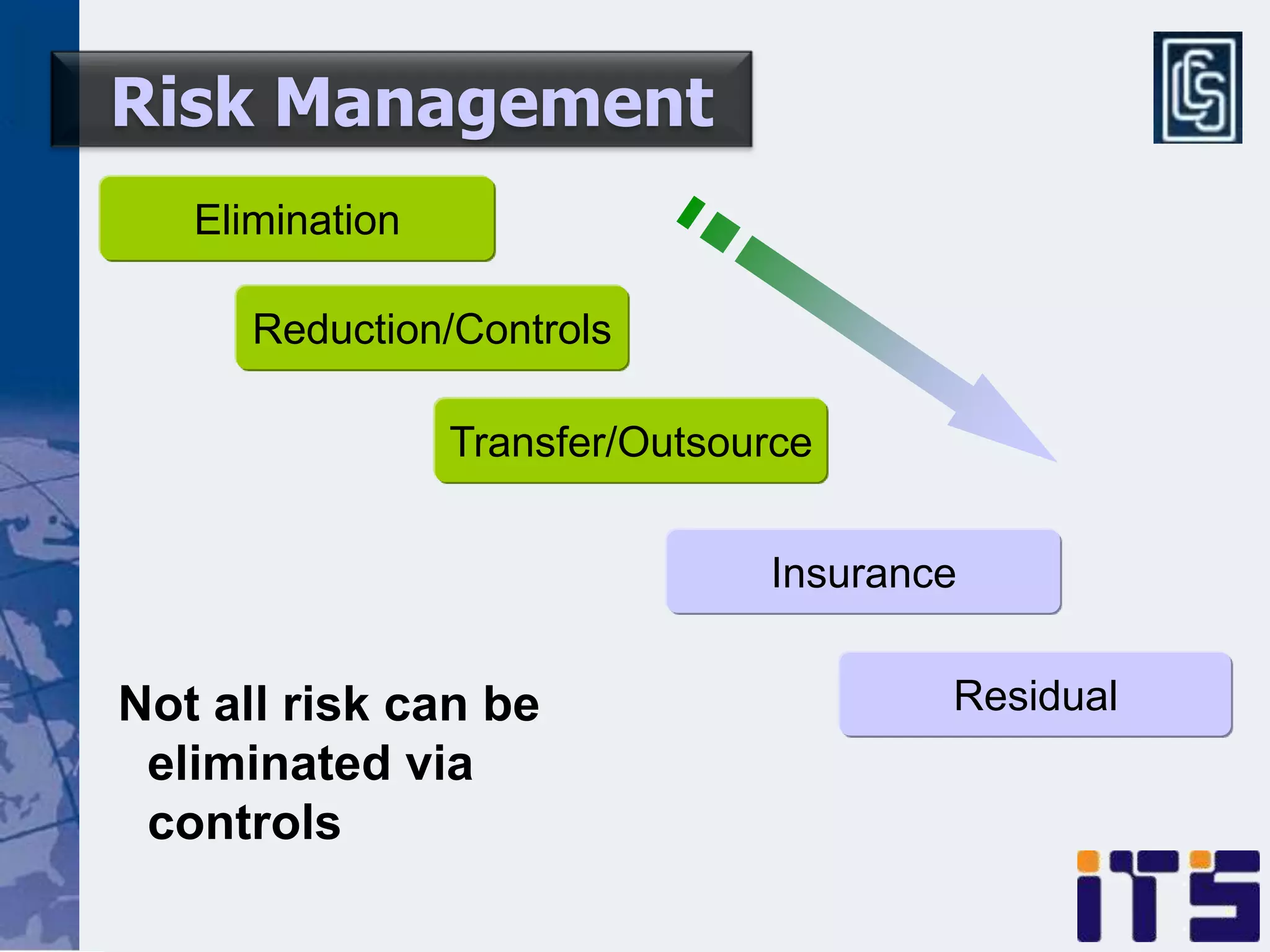
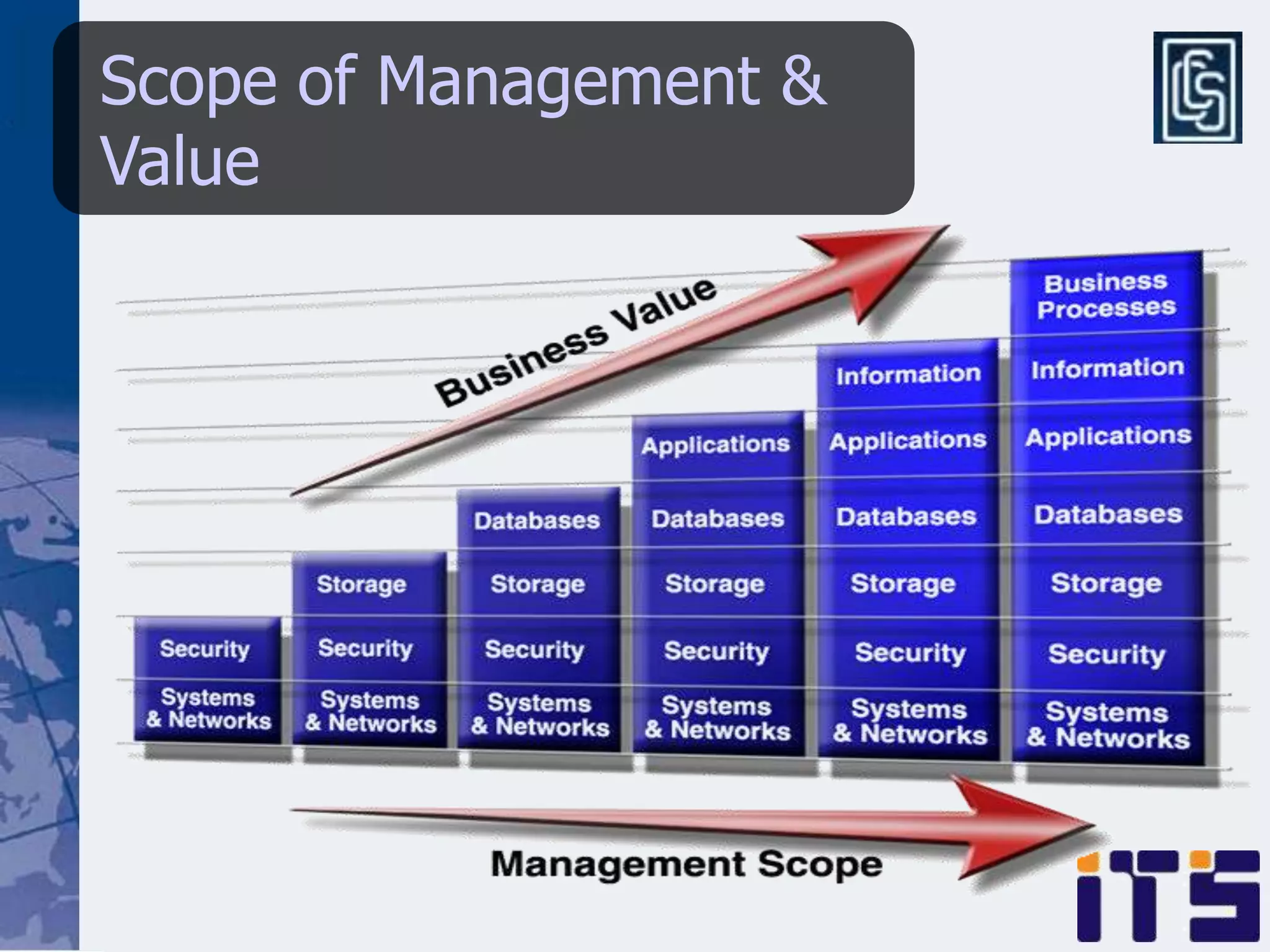
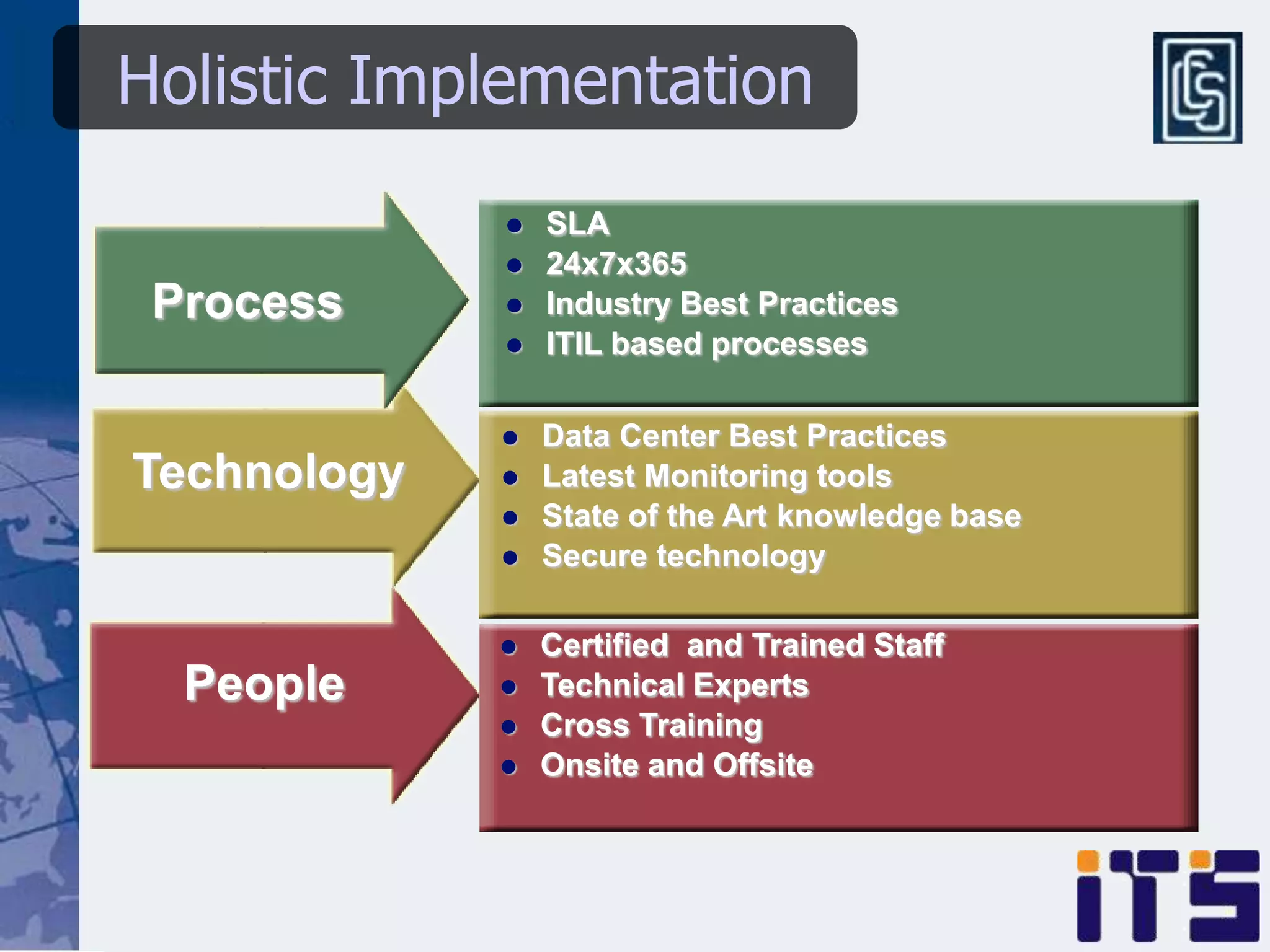
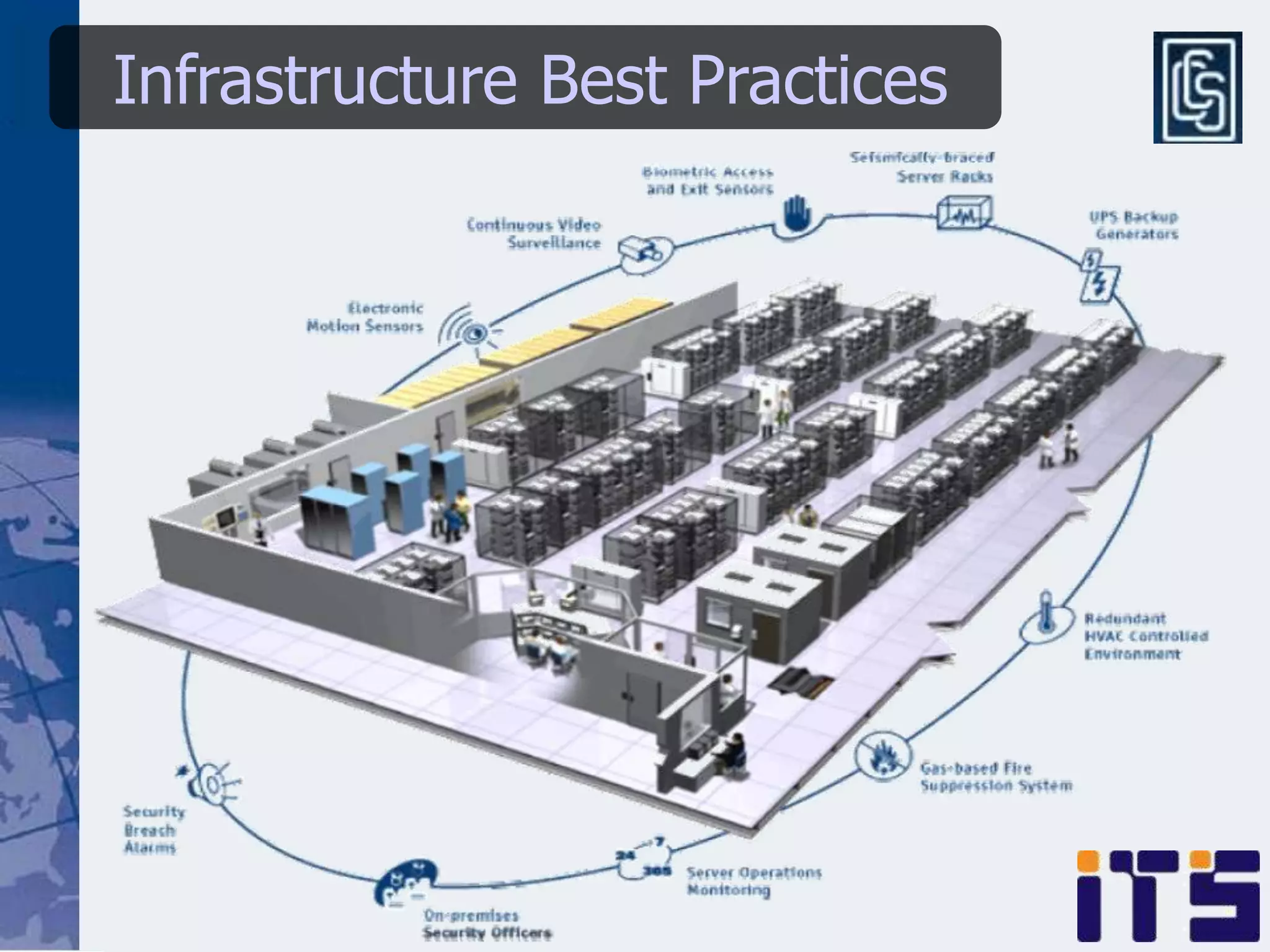
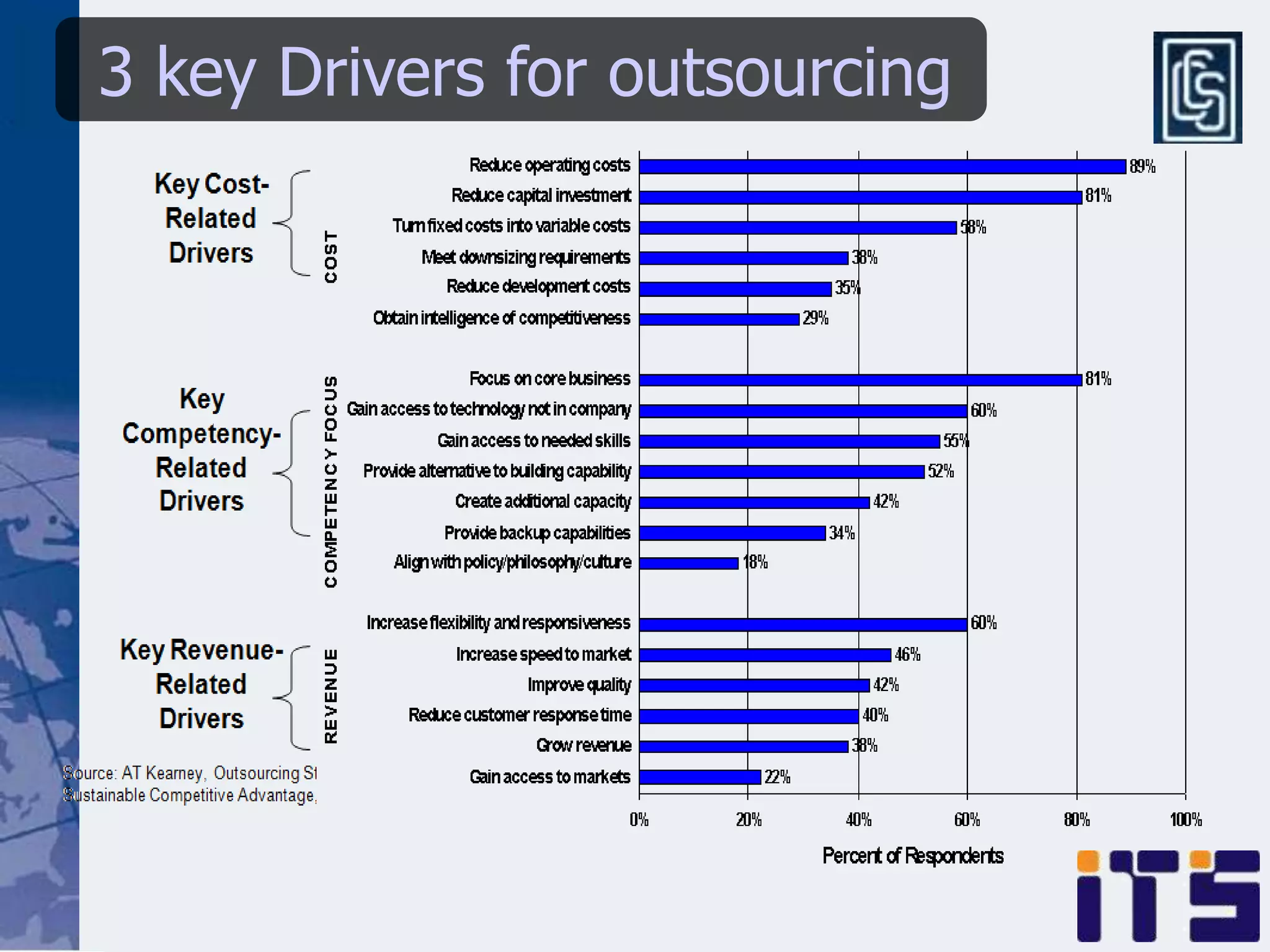
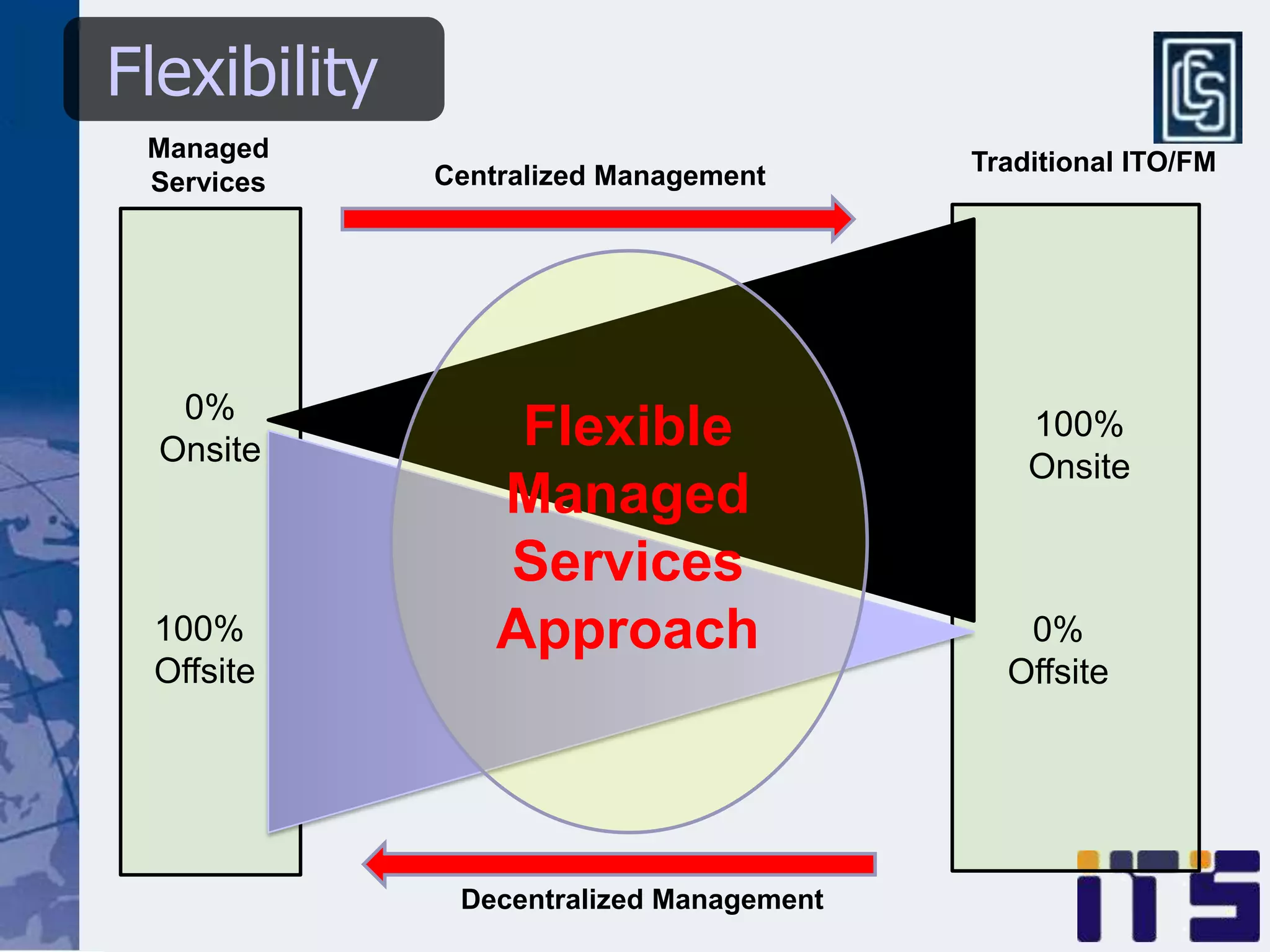
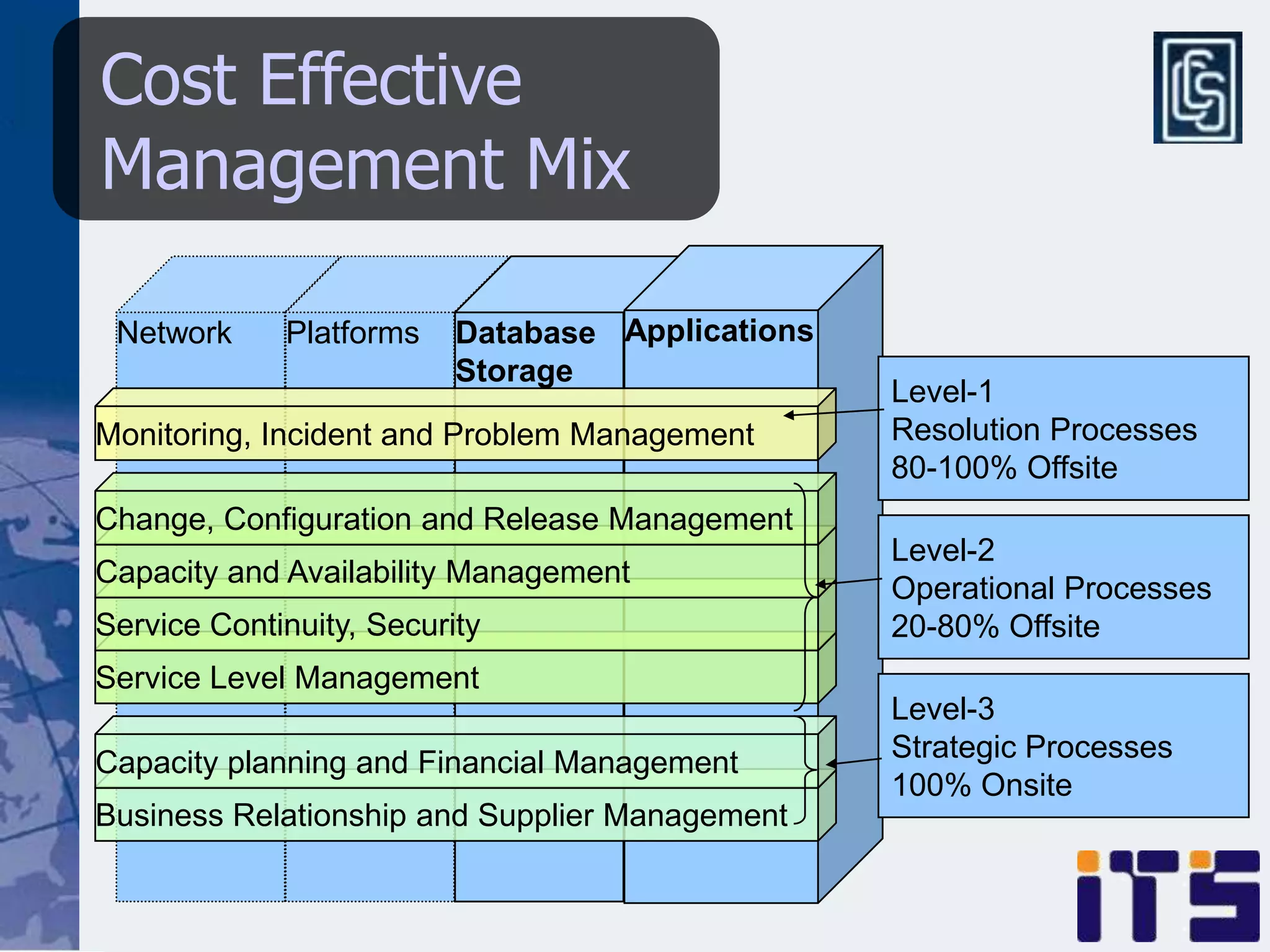
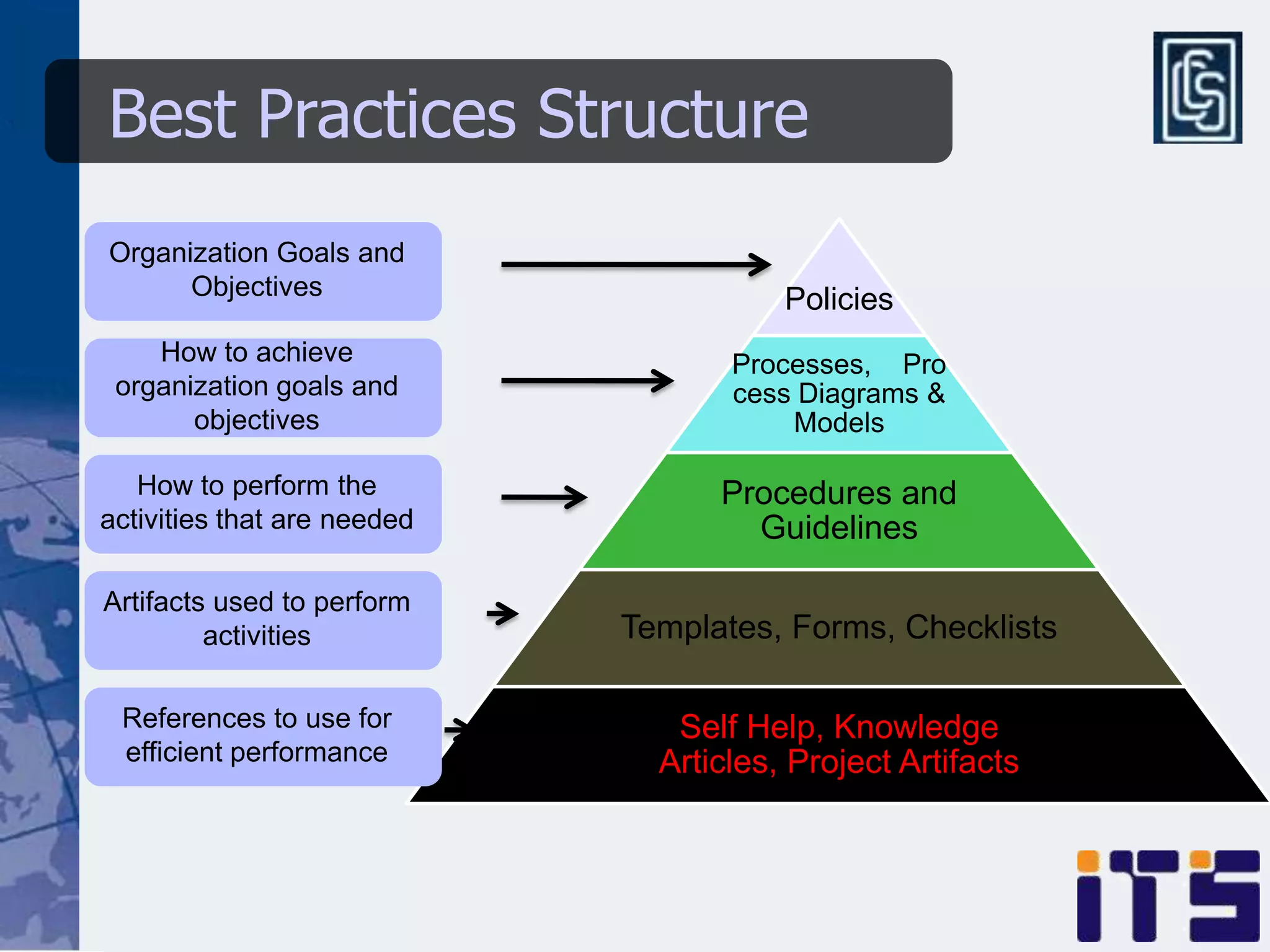
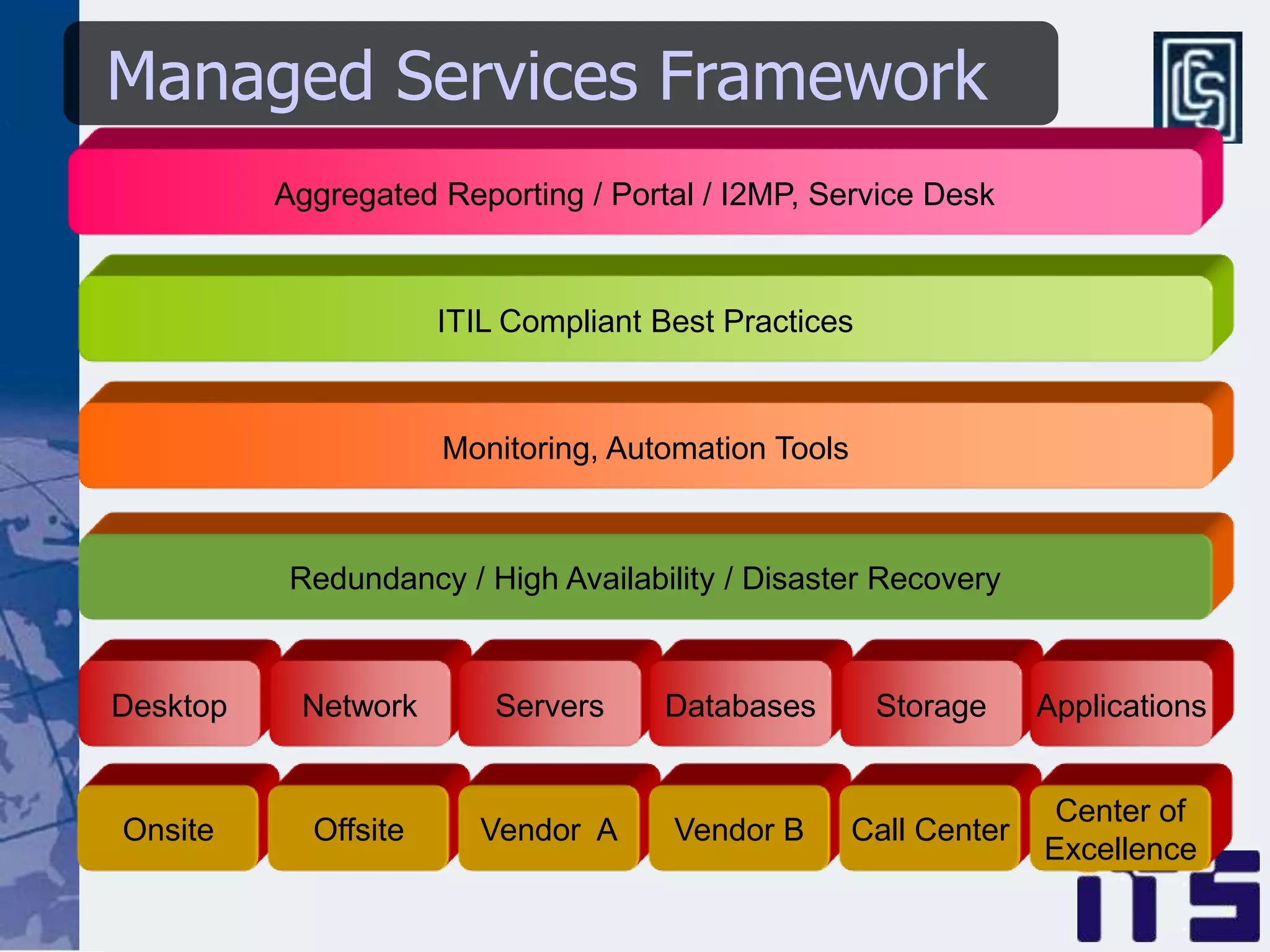
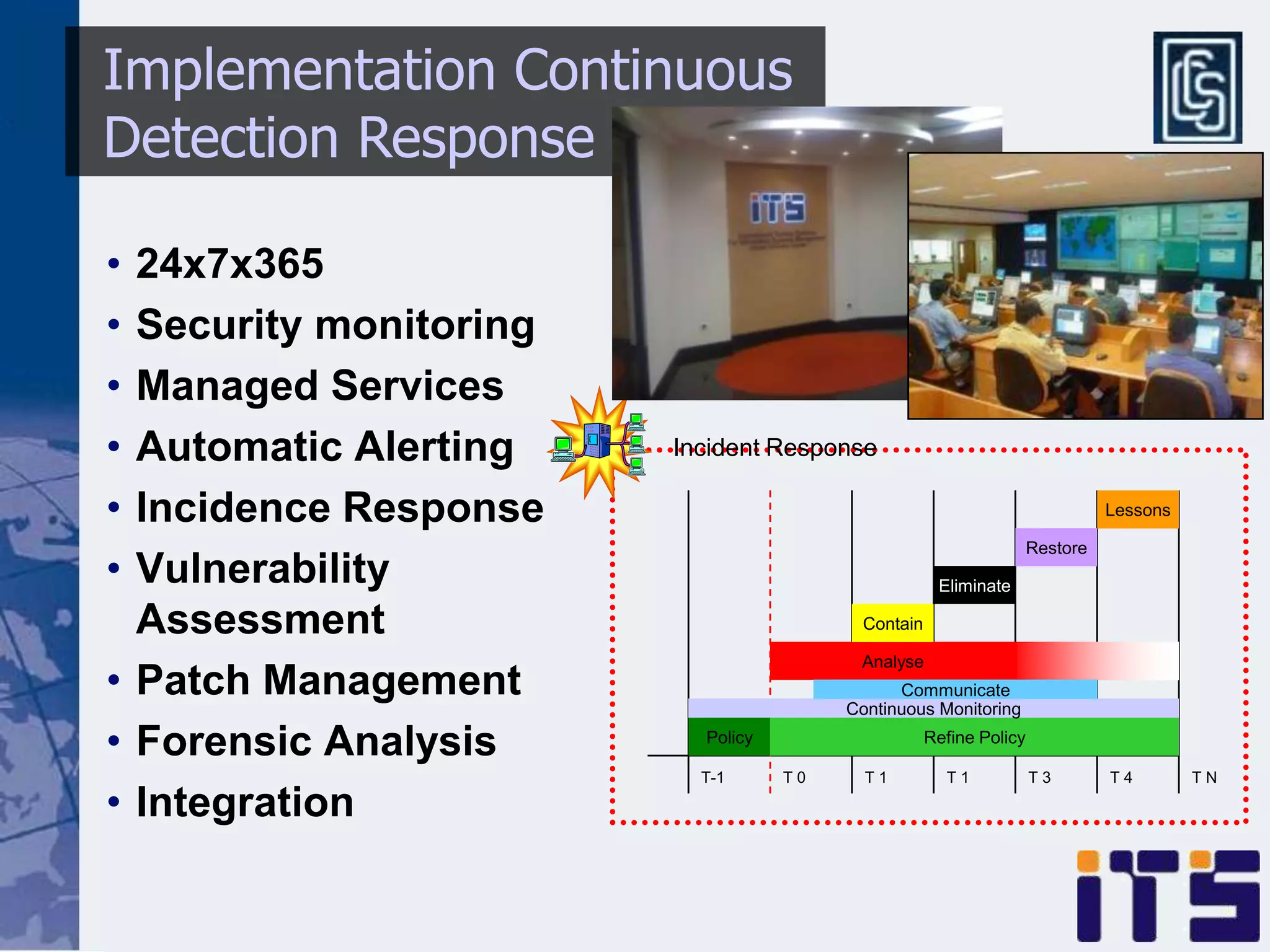
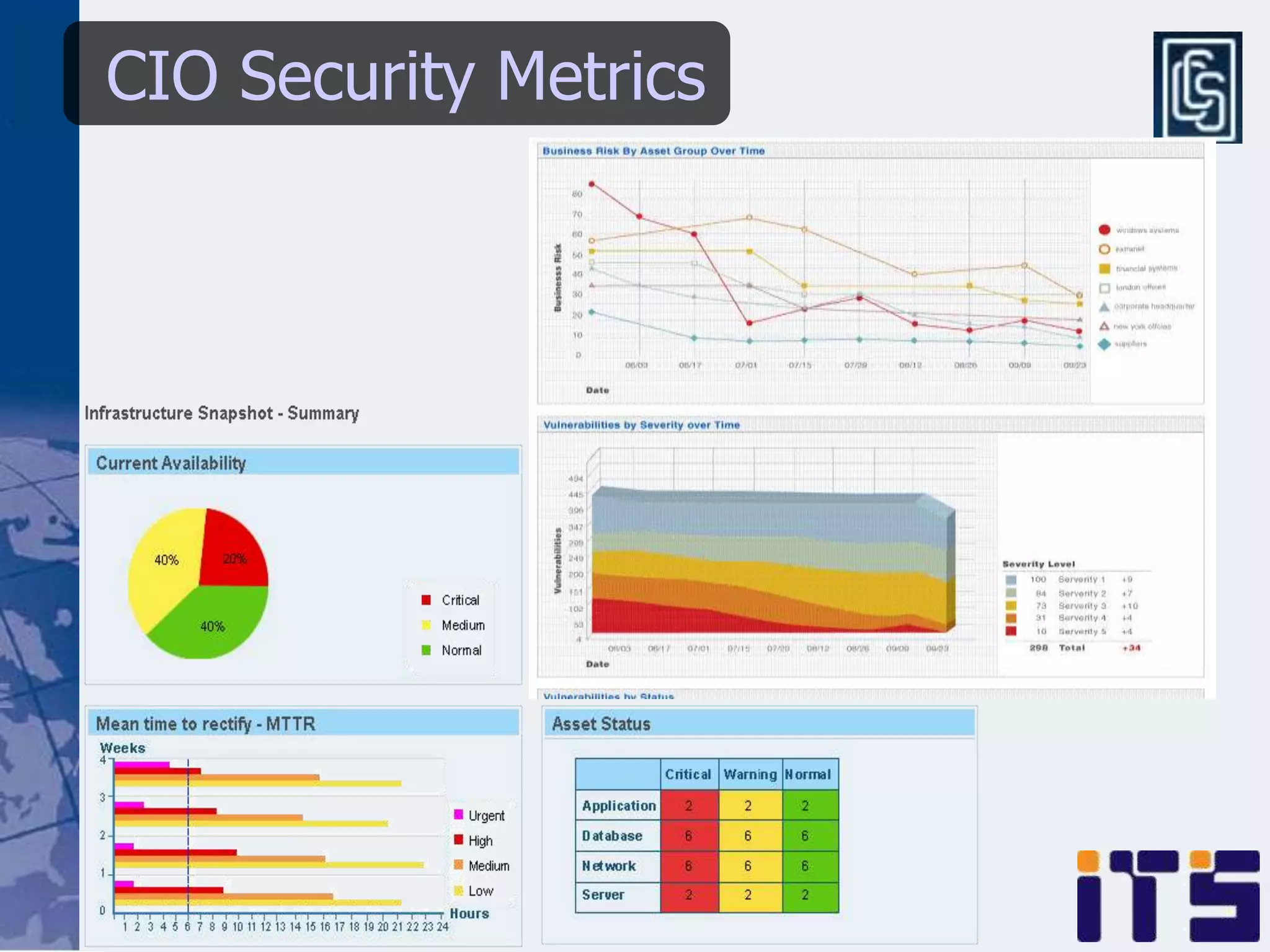
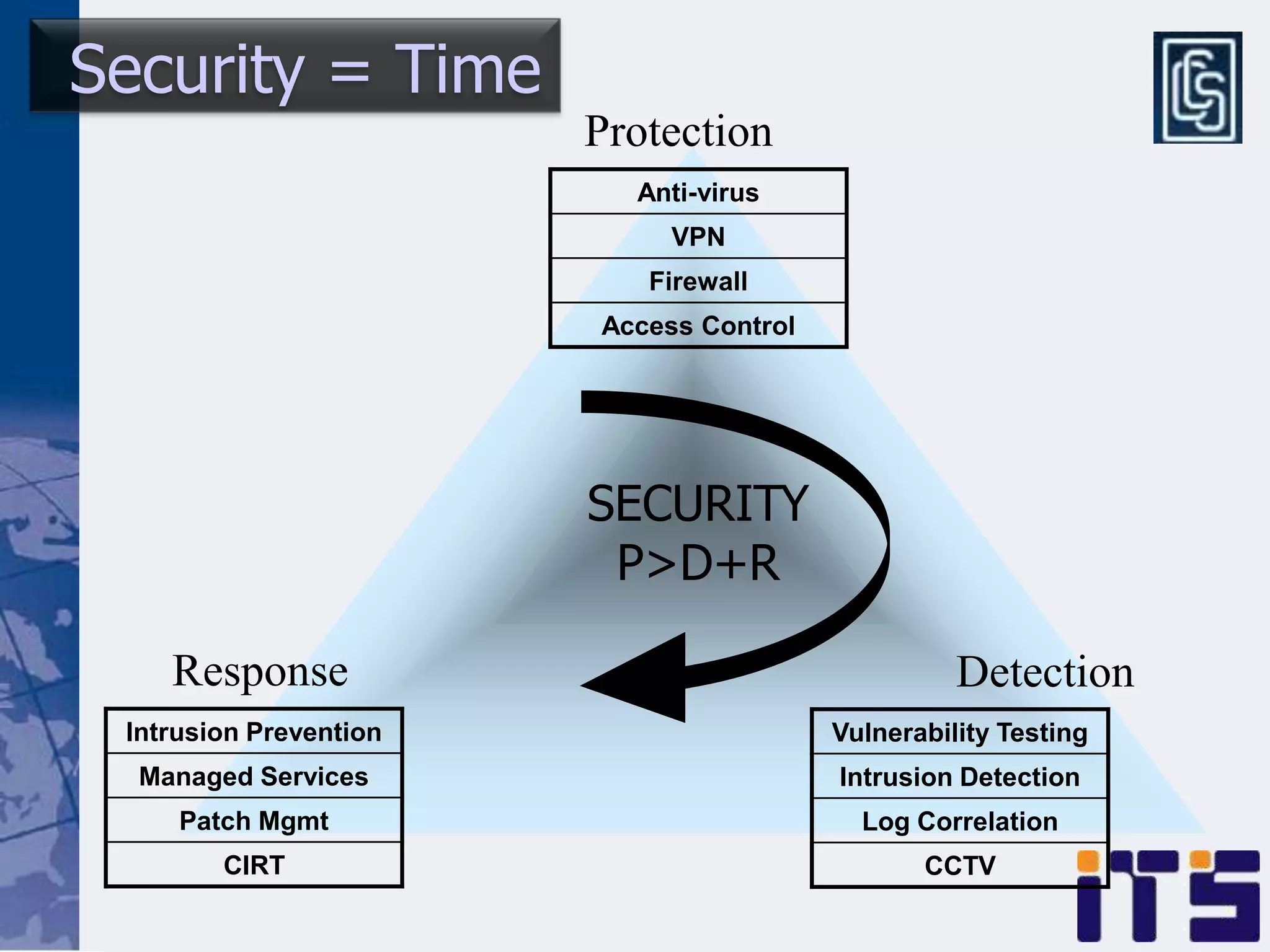
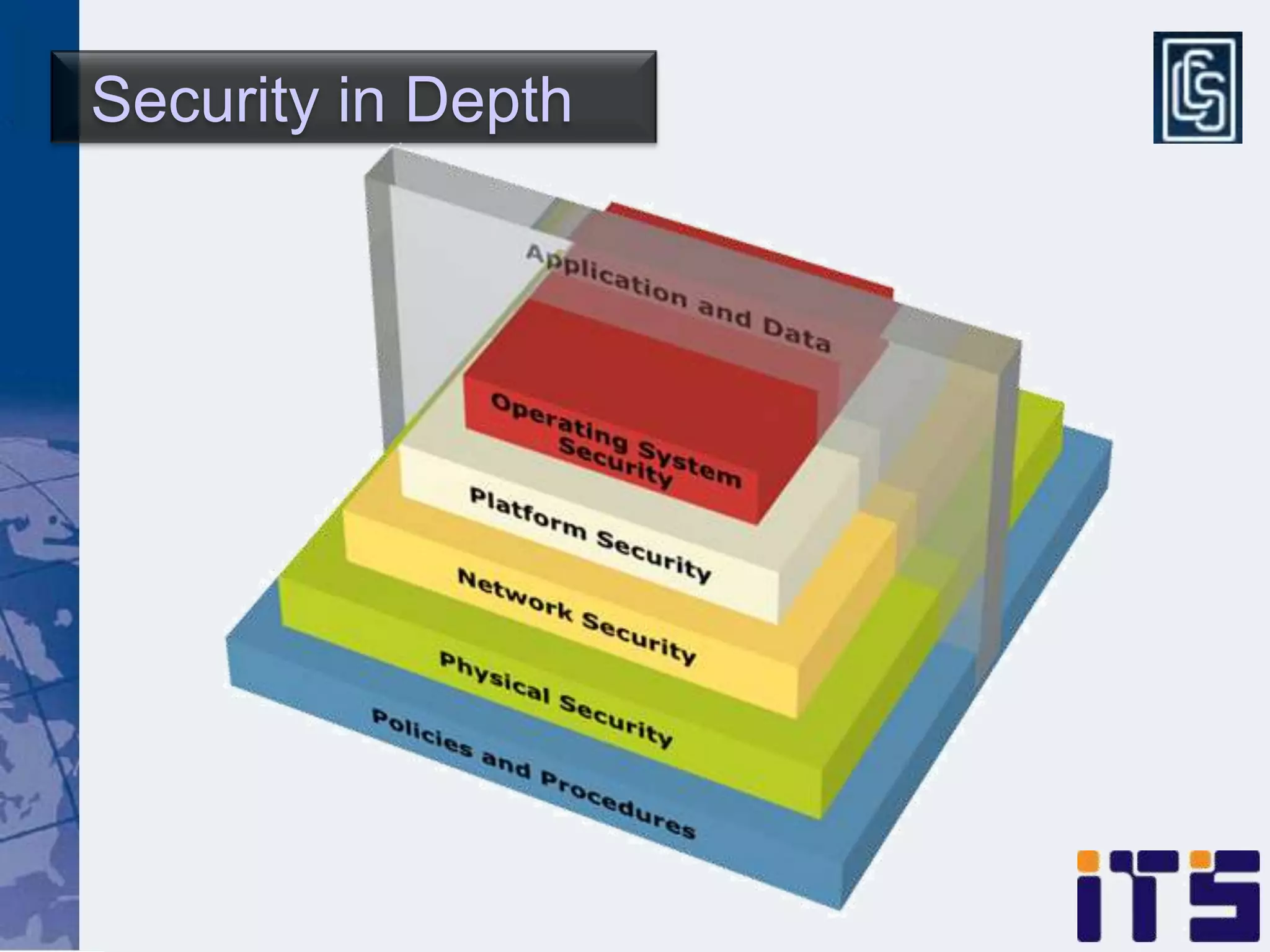
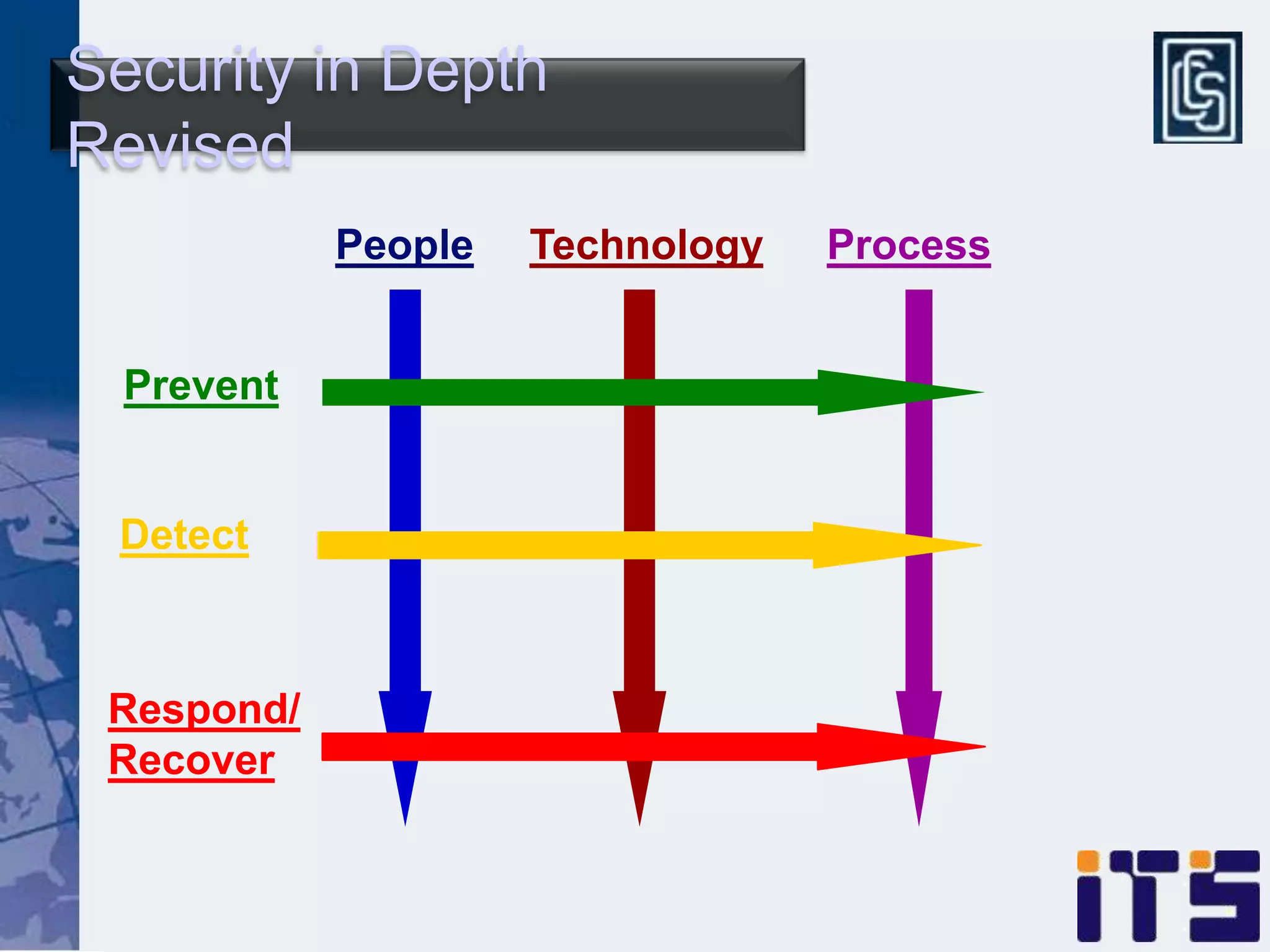
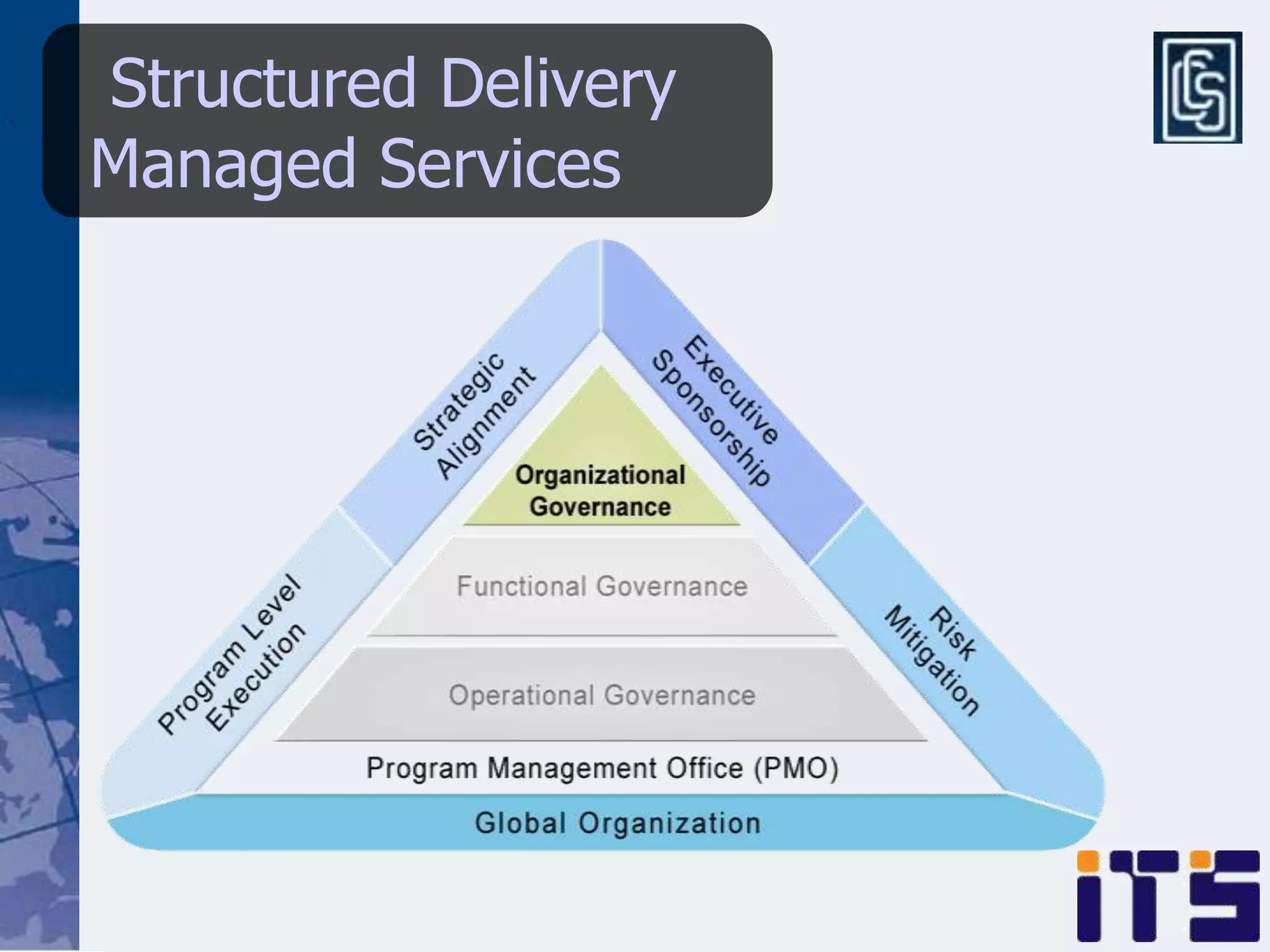
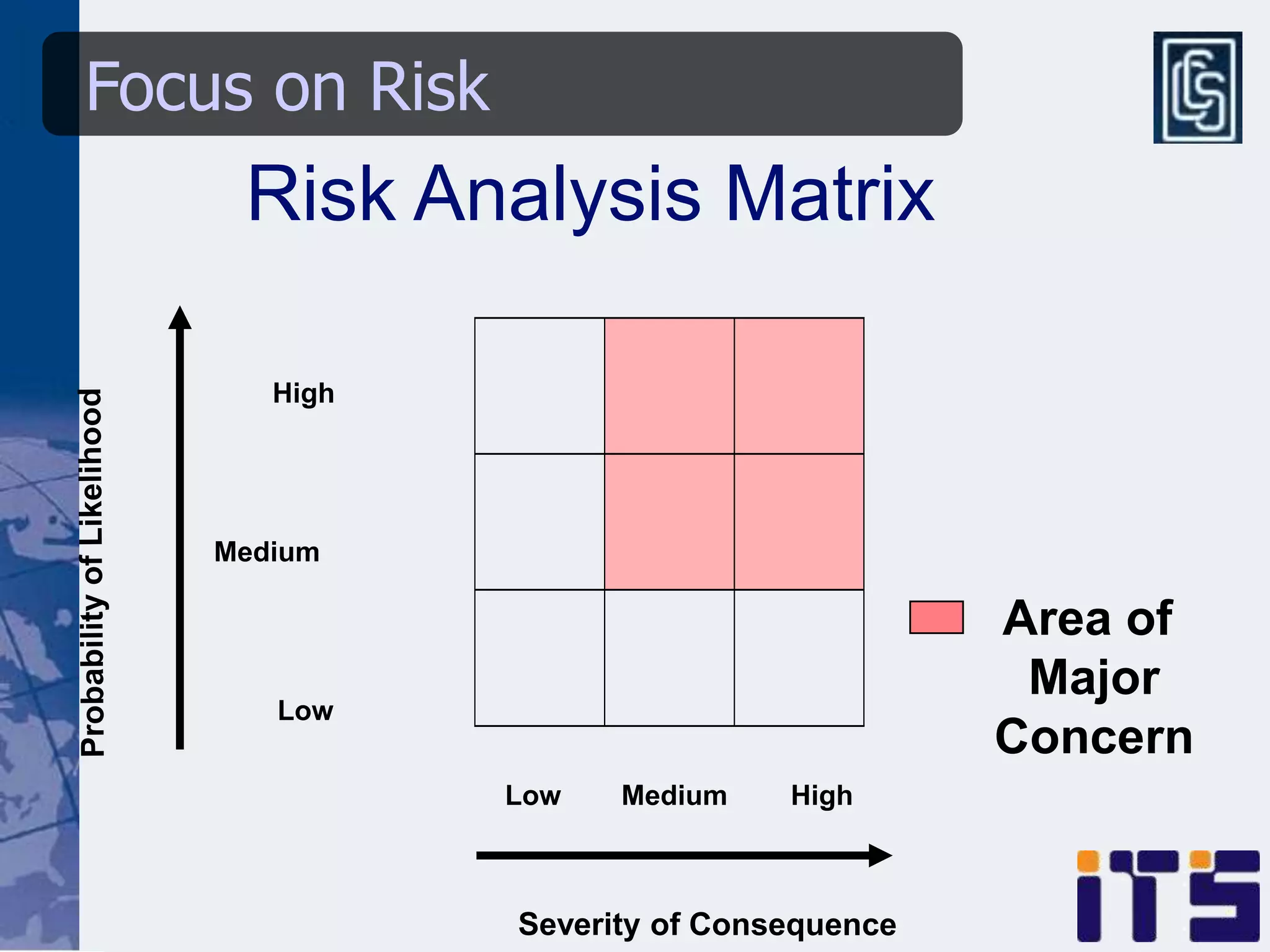
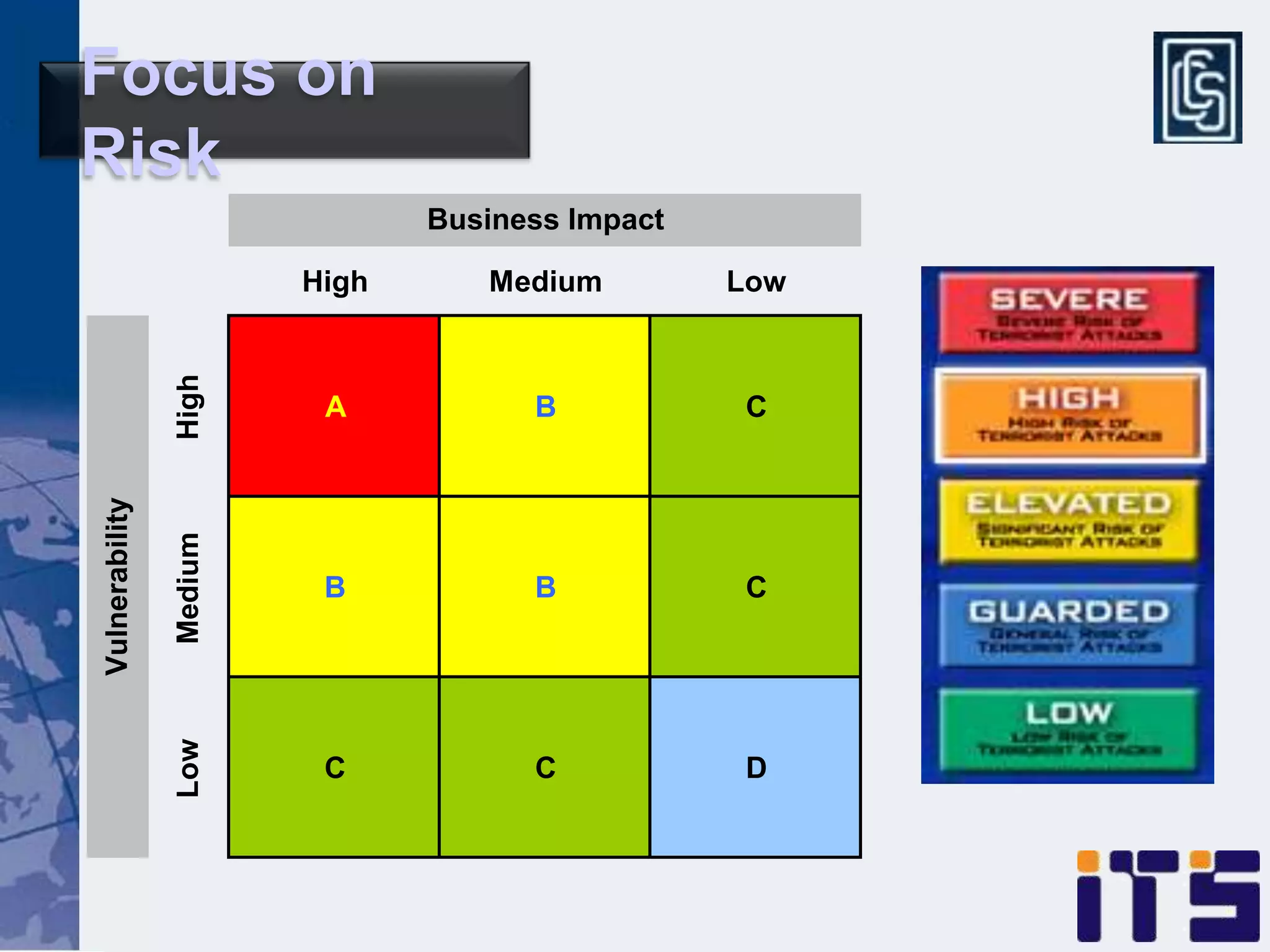
This document discusses leveraging managed security services to provide cost-effective information security operations. It notes that many organizations lack sufficient time and resources to properly address vulnerabilities. It then discusses how outsourcing to managed security services can provide around-the-clock monitoring and response, qualified security resources, infrastructure protection, and adherence to best practices in a predictable cost model. Finally, it outlines some of the key components of a managed security services framework, including monitoring tools, high availability, change management processes, and continuous improvement based on lessons learned from incidents.