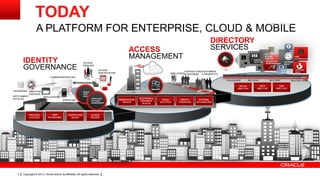
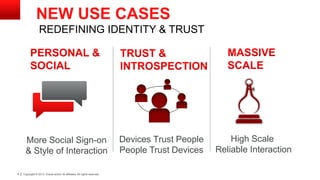
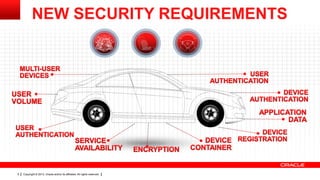
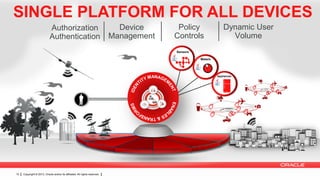
The document discusses the growing number of connected devices and the need for identity management solutions. It outlines Oracle's identity management platform and its ability to handle authentication, authorization, and management at massive scale across various devices. The platform provides a single solution for securing all devices and addresses new security requirements as interactions between people, devices, and applications increase.